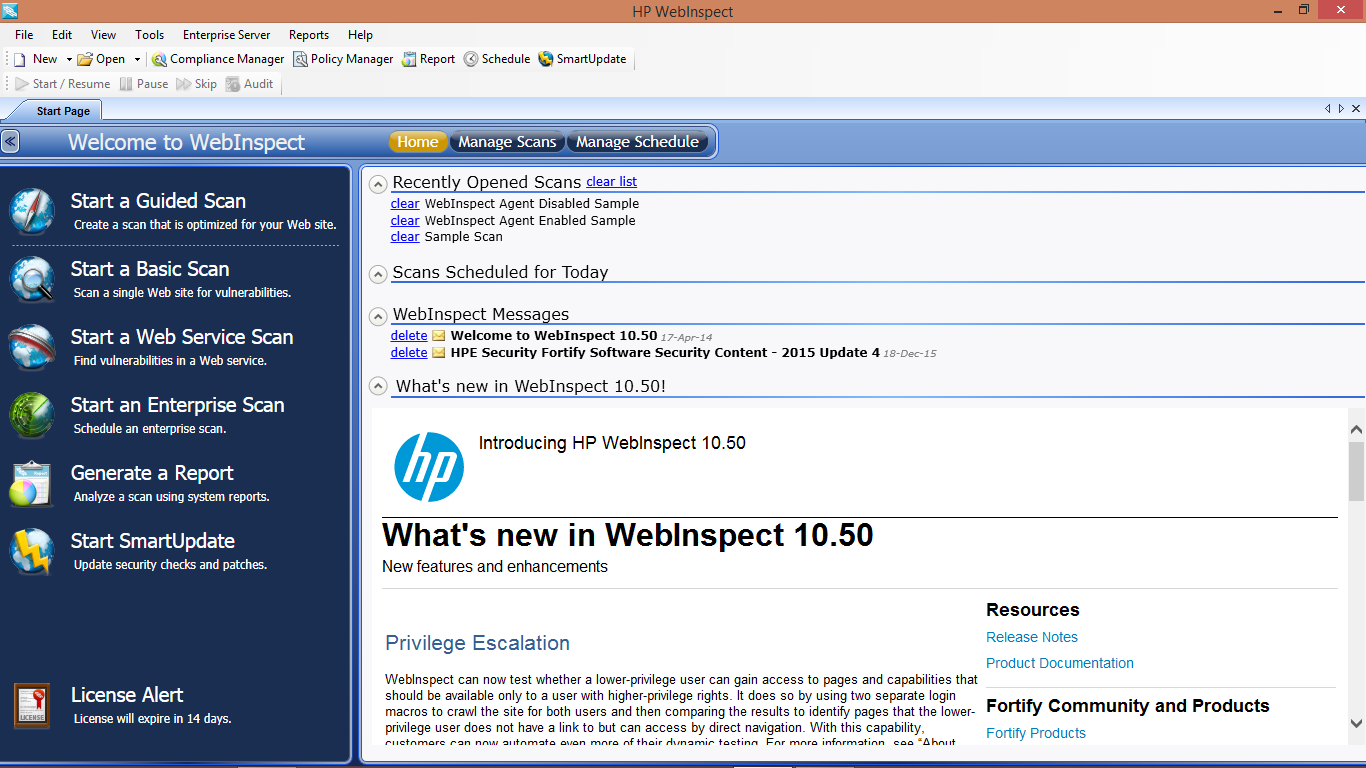
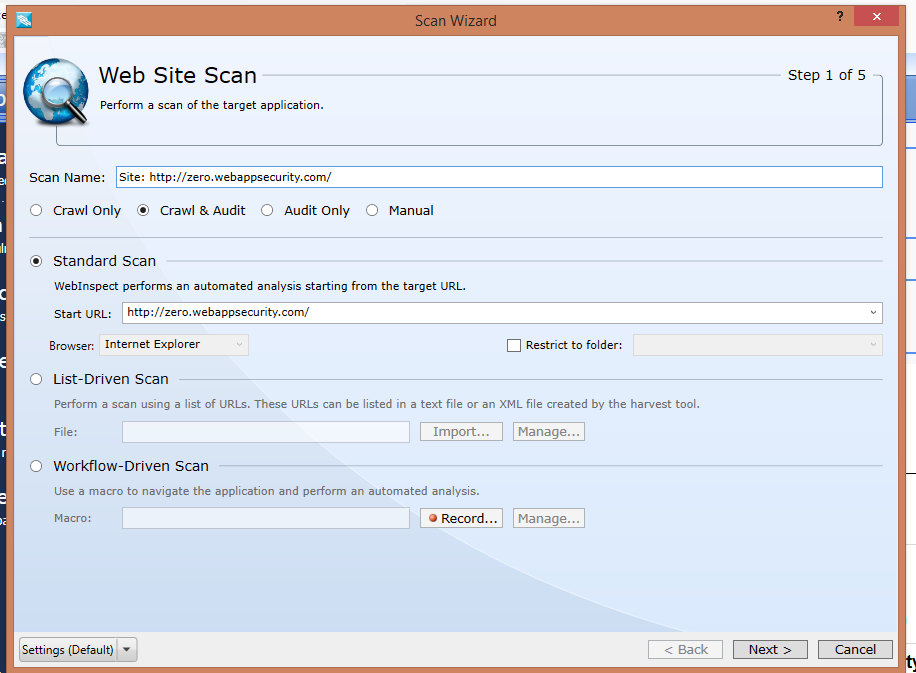
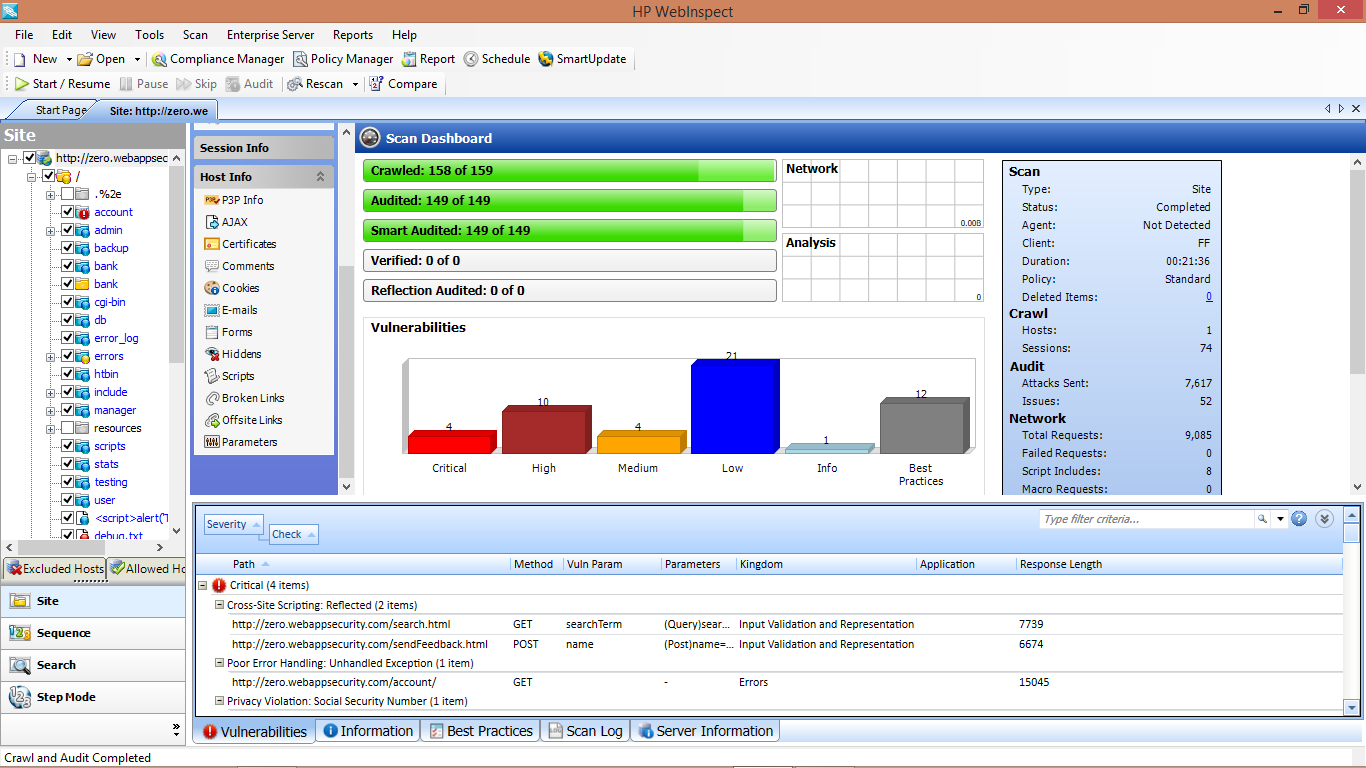
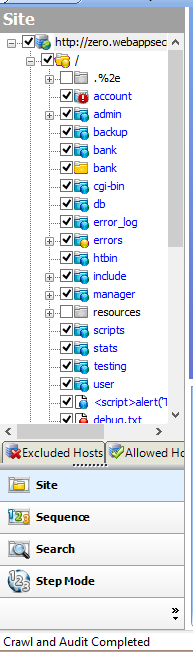
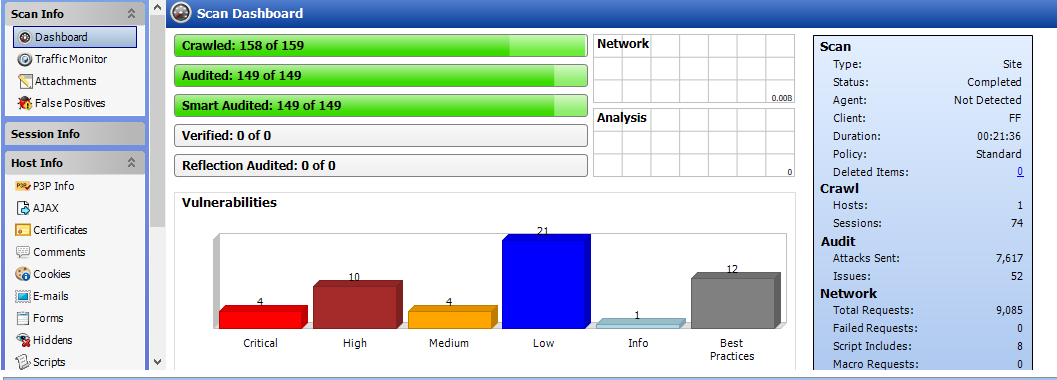
1. Presents you with tree structure: By crawling the entire application WebInspect presents you
with the hierarchical tree structure of the web application by listing all the available URLS.
2. Customizable Views: While viewing the results of the scan WebInspect offers you sortable views as per your requirement.
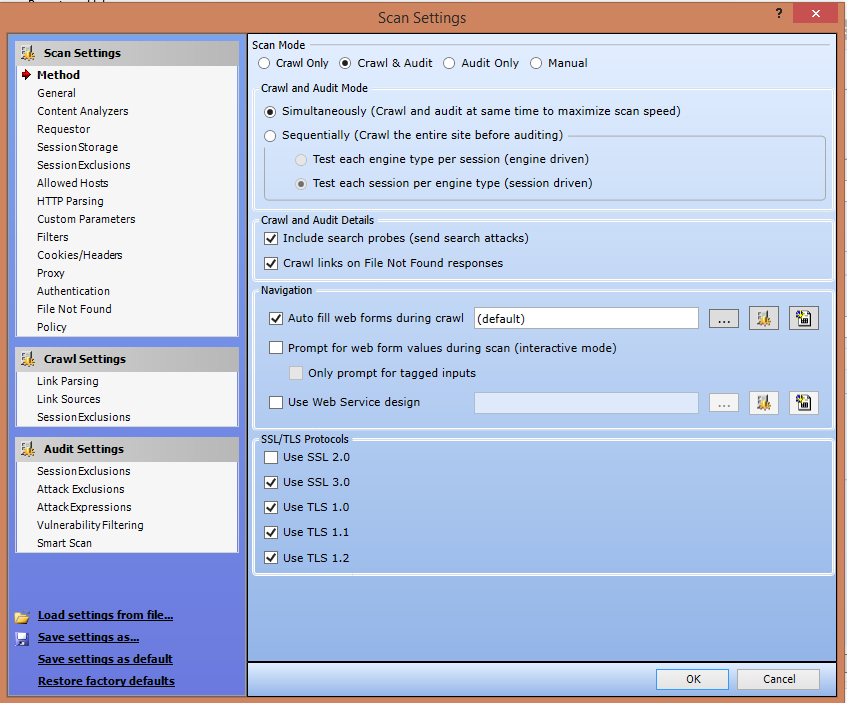
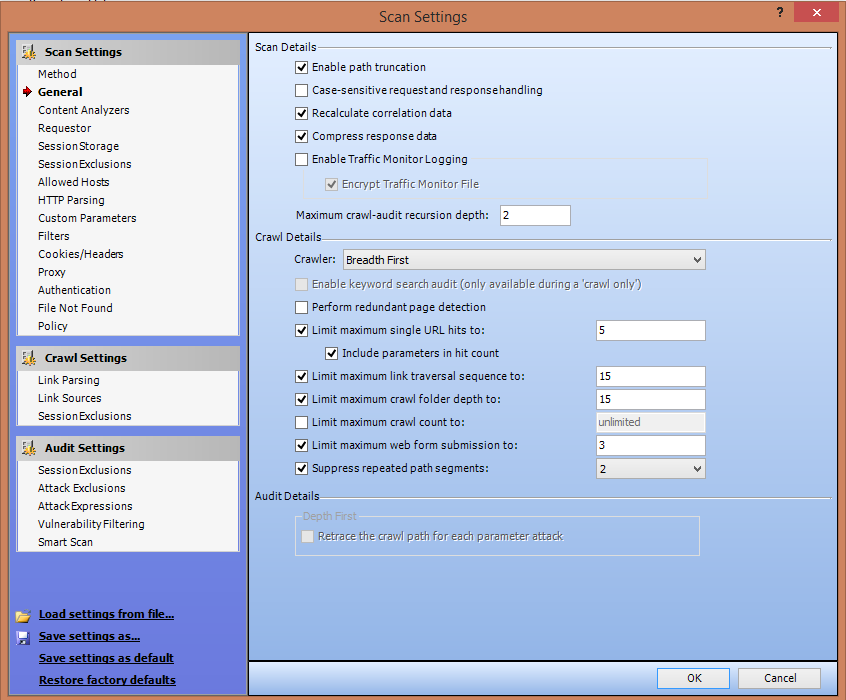
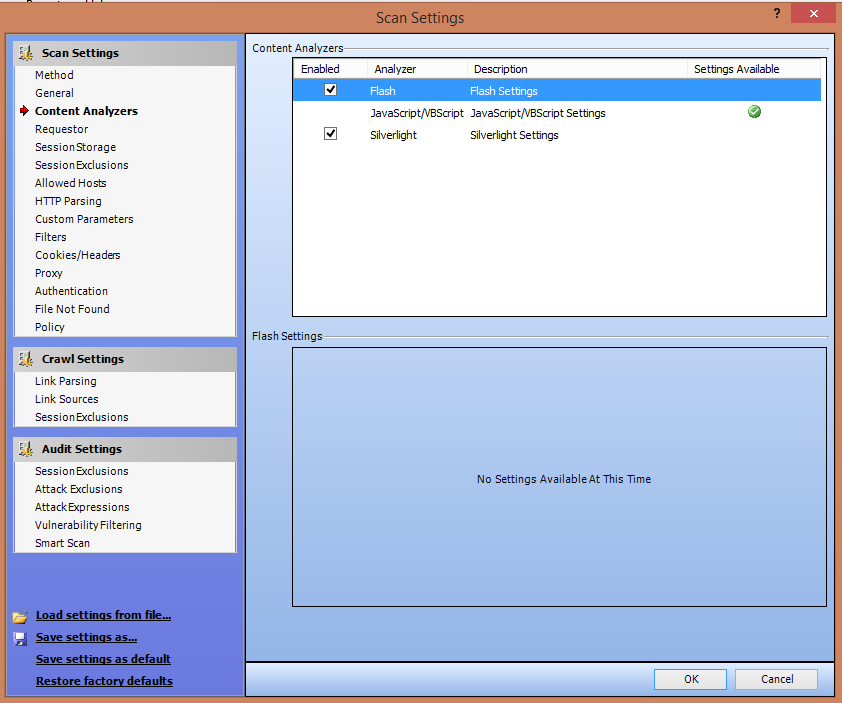
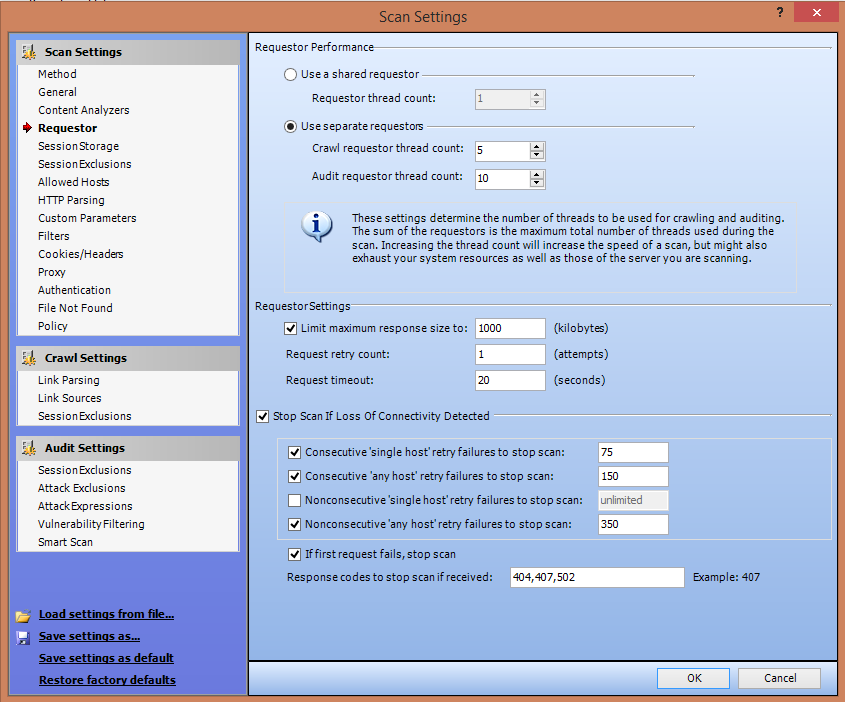
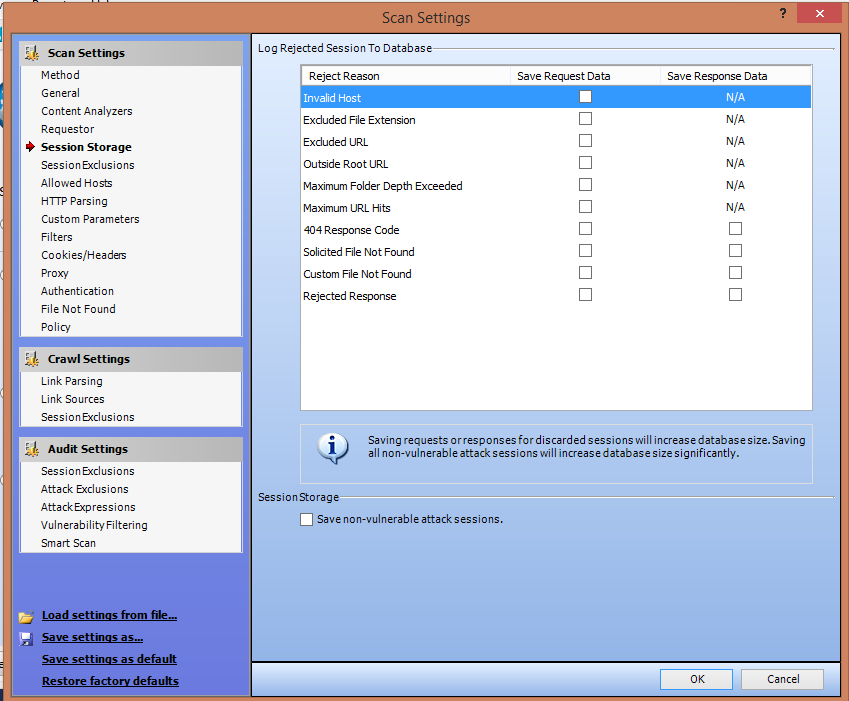
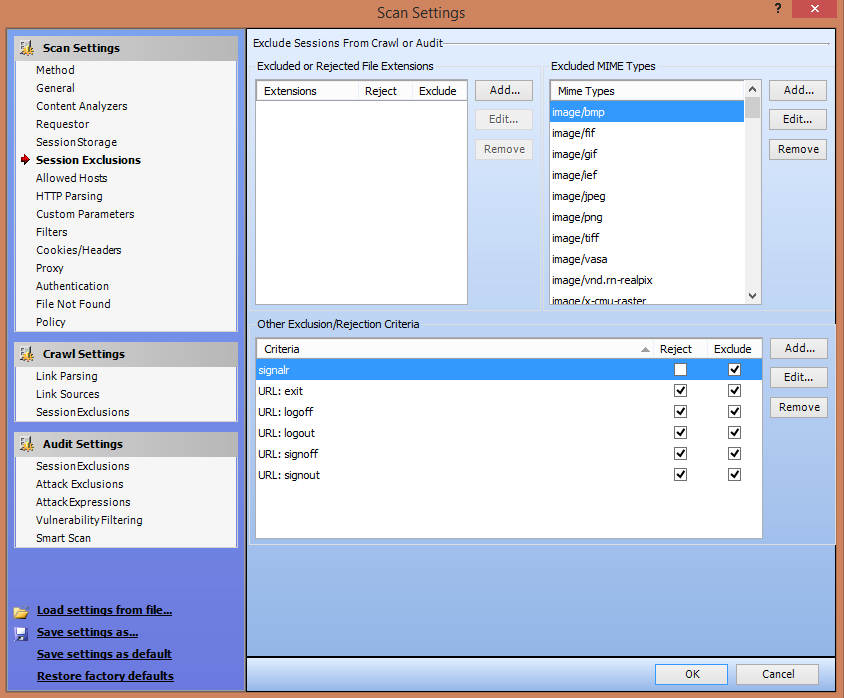
3. Scanning Policies: WebInspect gives you the freedom to edit and customize the scanning policies to suit your requirements and thus gives great flexibility.
4. Manual Hacking Control: With this option you can actually simulate a true attack environment
and see what’s really happening for a particular attack.
5. Report Generation: You can generate customizable reports by including desired sections and indesired format.
6.Remediation: WebInspect would provide a summary and the necessary fixes required to fix the
vulnerabilities detected during a particular scan.
7. Web Services Scan: Web services usage is growing at a rapid pace. You can assess web service
vulnerabilities by using WebInspect.
8. Tools: There are lot many tools that come with WebInspect like web proxy, SQL Injector, web
fuzzer, web macro recorder etc