Cryptoparty for CUNY students
Text
Your Perspective
Importance of security/privacy
- Herd Immunity
- Secure today, pwned tomorrow (data breach)
- Threats students (and peers) may face?
- Cyber harassment (doxxing)
- Potential employers (googleable)
- law enforcement (&ICE

Example: ICE
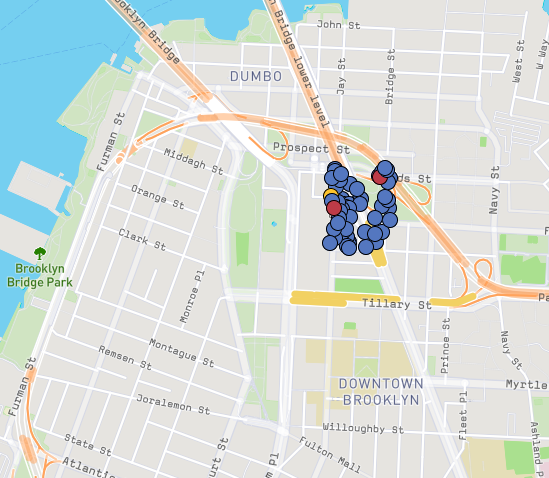
https://raidsmap.immdefense.org/
- Students can be undocumented
- Students may have undocumented family
- Your peers may be undocumented
Online collaboration and ...ICE?
Example:
ICE builds profiles by surveilling social media
ICE has active contracts with major tech companies to aid in surveillance






http://fortune.com/2018/10/23/tech-companies-surveillance-ice-immigrants/
https://www.eff.org/deeplinks/2018/06/hart-homeland-securitys-massive-new-database-will-include-face-recognition-dna-and
Just one example, other police surveillance included in HART
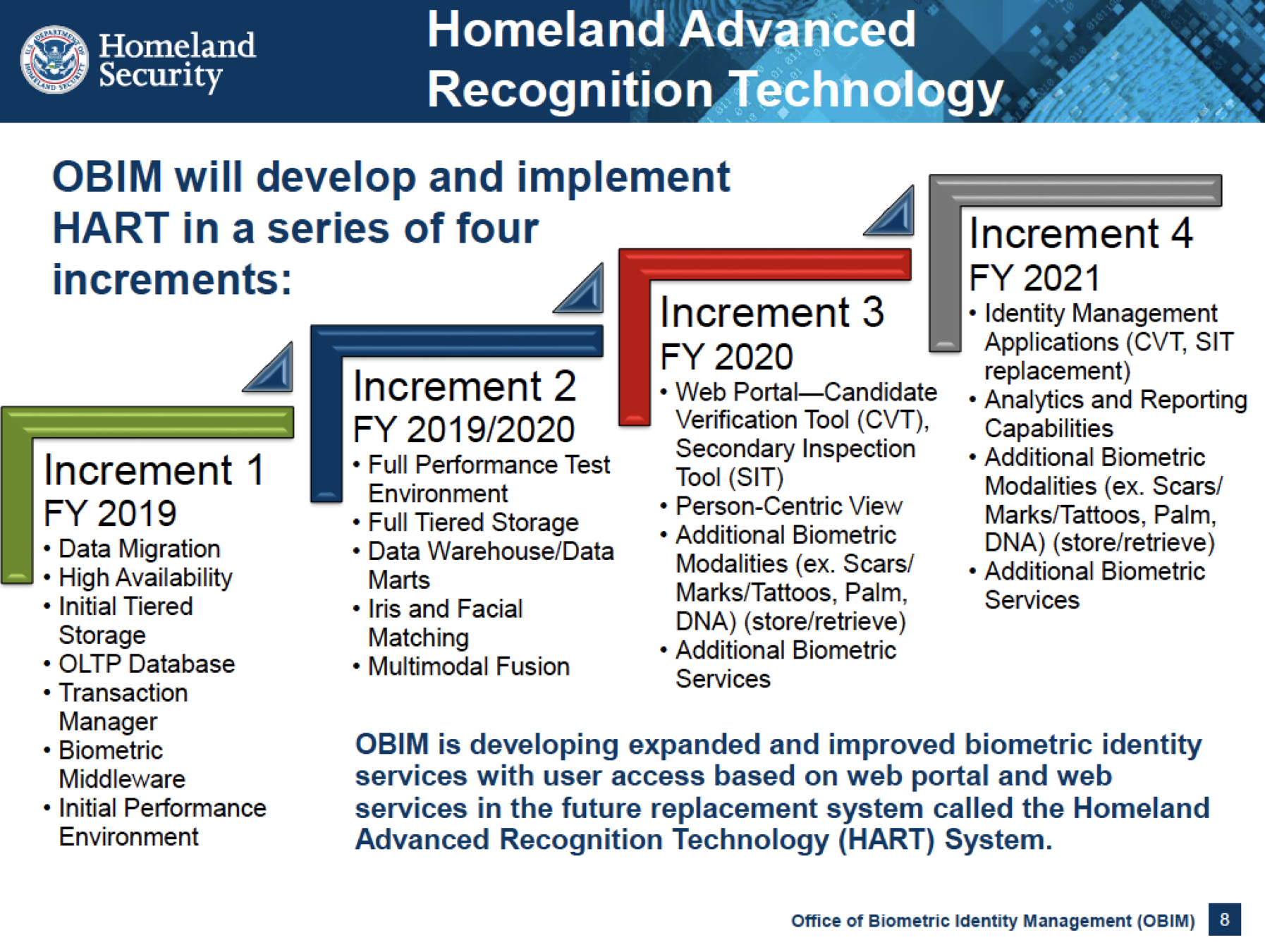
Holistic Approach


Holistic Approach

- Balance, not purity
- Improving, not finishing
Threat Modeling
- What do I want to protect?
- Who am I protecting it from?
- How likely is this threat?
- What are the consequences if I fail?
- How much trouble am I willing to go through to prevent the consequences?
- Implement change && return to (1)

Actor Mapping
- Improves understanding of threats
- Reveals new threats/allies
- Helps prioritize threats
Threat Modeling CUNY
A Simple Actor Map
Student
IT Dept
CUNY
NYS Gov
Fed Gov
City Tech
Federal
- 4th amendment
- No unwarranted search
- 14th amendment
- Penumbra- right by implication
- due process --> Marital privacy (same sex marriage 2015)
- Privacy Act 1974
- Restricts federal surveillance to foreign entities
- Restricts federal disclosure of records
- Patriot Act 2001
- Lowers barriers to surveillance
- Freedom of Information Act (FOIA) 1967

New York State
- Freedom of Information law (FOIL)
- Agencies responsible for responsible discolure of databases
- Personal Privacy Protection Law
- Only collect necessary info
- Must disclose to law enforcement, and inform user (unless it "impedes" investigation)
- Internet Security and Privacy Act
- State agency cannot collect/share info without user consent (includes implied consent)

- CUNY Computer User Policy
- Computers are for CUNY duties and (limited) socializing
- IT may monitor individual e-mails, websites, other communications as part of
- routine security monitoring
- to diagnose tech issue
- When failure to do so may harm individuals or make CUNY vulnerable to liability
- Reasonable belief of a law being violated
- Unusual account activity

Instructors & Peers
Instructors
- Responsible for student records (FERPA, federal)
- May assign work outside of CUNY infrastructure (e.g. googledocs)
When should(n't) we use an .edu email?
Workshops
- Better Passwords
- Intro to Mobile Security
Mobile Security
How do we communicate?
How does tech communicate?
Carrier/ISP
Internet/cell infastructure
Applications
Operating system
Phone Hardware







You




Friend



You

Server

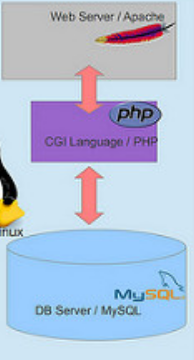

Hardware
What can my phone do?




- Feature & Smart Phones:
- Dial pad, touch screen, camera, mic, GPS,battery, bluetooth, cellular data,Call/SMS, antenna
- Smart Phones:
- Accelerator, biometric scanner, NPC, Wifi
Software




- iPhone v. Android
- Determine what apps can do?
- App questions:
- What permissions does it ask for? required?
- What info does it ask for?
- Who owns the app? (FOSS?)
- How does the mobile browser site compare?
Browser v. Facebook




- Pros of the FB app
- Convenience
- Notifications
- Offline access
- Pros of the FB website via browser
- FB has less access to your device
- Fewer updates
- More control of data
Providers and Infastructure




- Infrastructure
- Who has access?
- Their policies/legal requirements?
- What can they see?
- Providers
- What laws apply?
Net Neutrality - What is their business model?
- What laws apply?


Easiest steps
- Phone settings
- Lock screen/ phone encryption
- Turn off what you don't use
- Browser
- Firefox
- Brave
- Tor (Android)
- Communication
- Signal
- Riot
- Social media
- Browser or FOSS app (F-Droid)
Setting up a phone
Cryptoparty for CUNY Students
By cypurr
Cryptoparty for CUNY Students
- 386



