Quines: A self producing syndrome

Presented by Gopika Subramanian

- > Gopika Subramanian (@m0n574)
-> 3rd Year BTech CSE @Amrita School of Engineering
-> CTF Player @teambi0s and @teamshakti6
-> Web Exploitation
-> Organising team @InCTF, @ShaktiCTF
WHO AM I?

- > No. 1 CTF team of India
-> Founded in 2008 by our mentor Vipin Pavithran
-> Members engage actively in security research
-> Conduct International and National CTFs yearly
ABOUT TEAM BI0S

- > No. 1 women-only CTF team of India
-> Founded in 2018 by our mentor Vipin Pavithran
-> Members engage actively in security research
-> Organizers of Shakti CTF (Women-only international CTF)
ABOUT TEAM SHAKTI

Agenda
SQL Injection
Quines
-> What | Why | How
-> Introns
Quine SQL Injection
-> What | How | Where
-> Quine payloads and its breakdown
-> Prevention

SQL Queries
SQL is the standard language for Relational Database System
Programming Language to:
- Store
- Manipulate
- Retrieve
DBMS eg: Oracle, Sybase, Microsoft SQL Server, Access


SQL Injection
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. -owasp
SQL injection exploit can :
- Read sensitive data from the database
- Modify database
- Privilege escalation
- Issue commands to the operating system

SQL Injection
Input: ' union select username, password from users --
select * from users where username=`input` and
password=`input`
select * from users where username= '' union select username, password from users -- and password=''
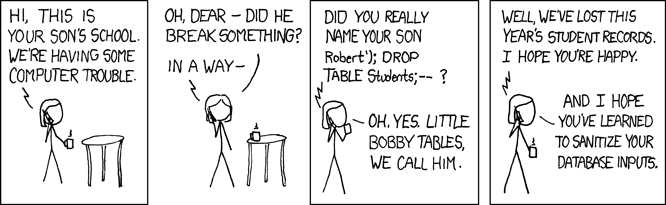

SQL Injection
SELECT * FROM data WHERE username='admin';

SQL Injection
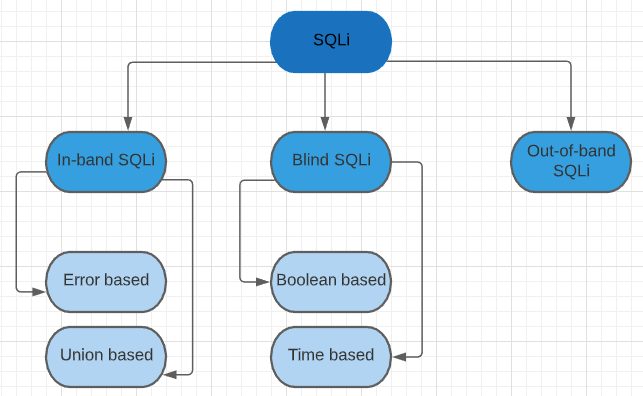

SQL Injection
WAF Bypass
WAF = Web Application Firewall
Security layer which follows a bunch of rules to prevent SQL injection
Sanitize or blacklist the common SQL keywords in the input.

SQL Injection
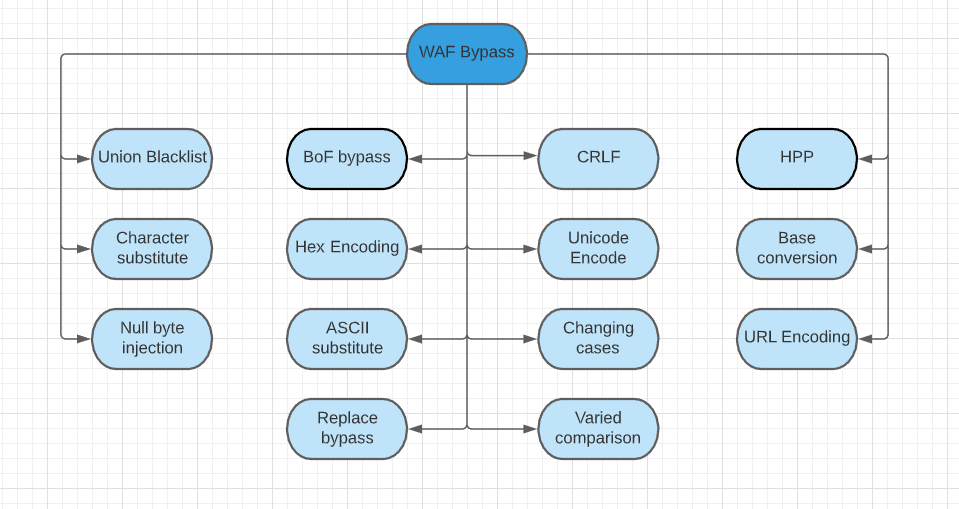

Quines
Program which takes no input and produces a copy of its own source code
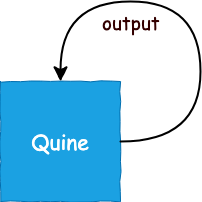
Quines are not allowed to “step outside itself”
self-replicating programs | self-reproducing programs | self-copying programs

Quines
Advantages of Quines:
Does not depend on:
- Being able to read files/program
- Represent quotes in varied ways
- Access to the source files location

Quines

Quine
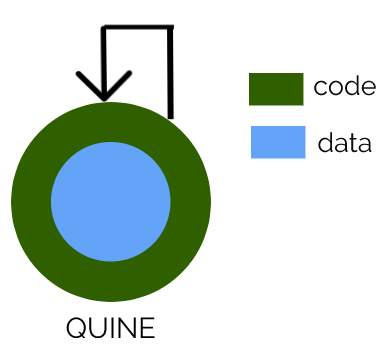
s='s=%r;print(s%%s)';
print(s%s)
Data part: s=%r;print(s%%s)
Code Part: print(s%s)
Python quine program

Quine

Quine
Introns
-> Code that can be injected within a quine
-> Replicates along with the quine's replication
-> Does not contribute directly to function of quine
-> "Non-functional part of Quine"
-> Not used to write the program but gets copied

Quine
Introns

Quines in SQL = Queries that outputs the source query
Quine SQL Injection
- Do not need control over data
- Can be used on Ghost tables

Quine SQL Injection
Where it works
Consider:
$r = mysql_fetch_array(mysql_query("select * from test where pw=$_GET['pw']"));
if($r['pw'] === $_GET['pw'])
auth();
Result of query of password should be equal to Input password

Quine SQL Injection
Possible attacks:
-> Blind SQL Injection
Disadvantages:
- Difficult to attack if rows don't exist
- Difficult if password is hash

Quine SQL Injection
Possible attacks:
-> Union based attack if information_schema.processlist contains currently executing query
union select 1,'admin',database() from information_schema. processlist
The MySQL process list indicates the operations currently being performed by the set of threads executing within the server.

Quine SQL Injection
Disadvantages:
- information_schema.processlist must be accesible
- It can only be used in MySQL

Quine SQL Injection
Quine SQL query
SELECT REPLACE ( REPLACE ( 'SELECT REPLACE(REPLACE("$",CHAR(34),CHAR(39)),CHAR(36),"$") AS Quine' , CHAR ( 34 ), CHAR ( 39 )), CHAR ( 36 ), 'SELECT REPLACE(REPLACE("$", CHAR(34), CHAR(39)), CHAR(36), "$") AS Quine' ) AS Quine;
data
code

Quine SQL Injection
Query Breakdown
INPUT: REPLACE ( 'SELECT REPLACE(REPLACE("$",CHAR(34),CHAR(39)),CHAR(36),"$") AS Quine' , CHAR ( 34 ), CHAR ( 39 ))
OUTPUT: SELECT REPLACE(REPLACE('$',CHAR(34),CHAR(39)),CHAR(36),'$') AS Quine
INPUT: REPLACE ("SELECT REPLACE(REPLACE('$',CHAR(34),CHAR(39)),CHAR(36),'$') AS Quine", CHAR ( 36 ), 'SELECT REPLACE(REPLACE("$", CHAR(34), CHAR(39)), CHAR(36), "$") AS Quine')
OUTPUT: SELECT REPLACE(REPLACE('SELECT REPLACE(REPLACE("$", CHAR(34), CHAR(39)), CHAR(36), "$") AS Quine',CHAR(34),CHAR(39)),CHAR(36),'SELECT REPLACE(REPLACE("$", CHAR(34), CHAR(39)), CHAR(36), "$") AS Quine') AS Quine

Quine SQL Injection

Demo
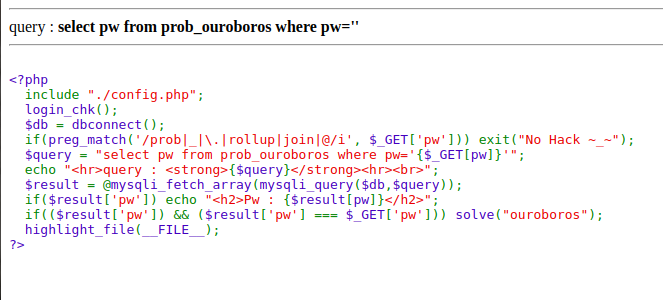
challenge courtesy: los

Demo
Quine SQL Injection

SQL Injection
Prevention
-> Input validation
-> Escaping user inputs
-> Avoiding administrative privileges
-> Parameterized queries
-> Stored procedures

Any Questions ?


Thankyou :)
Copy of deck
By Gopika Subramanian
Copy of deck
- 69



