SQLi: Dead until bypassed
Agenda
SQL Queries
SQL Injection
- what
- why
- how
SQLi Bypasses
Q&A
SQL Queries
SQL is the standard language for Relational Database System
Programming Language to:
- Store
- Manipulate
- Retrieve
DBMS eg: Oracle, Sybase, Microsoft SQL Server, Access

SQL Injection
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. -owasp
SQL injection exploit can :
- Read sensitive data from the database
- Modify database
- Privilege escalation
- Issue commands to the operating system
SQL Injection
Input: ' union select username, password from users --
select * from users where username=`input` and
password=`input`
select * from users where username= '' union select username, password from users -- and password=''
SQL Injection
SELECT * FROM data WHERE username='admin';
SQL Injection
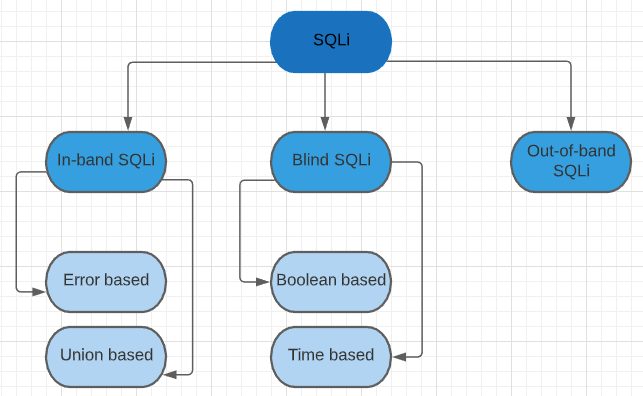
SQL Injection
WAF Bypass
WAF = Web Application Firewall
Security layer which follows a bunch of rules to prevent SQL injection
Sanitize or blacklist the common SQL keywords in the input.
SQL Injection
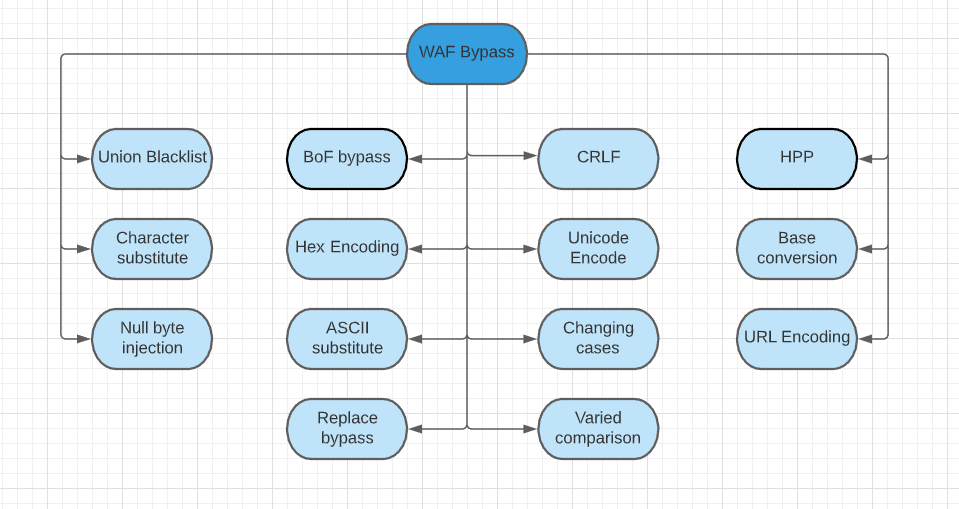
SQL Injection
Prevention
-> Input validation
-> Escaping user inputs
-> Avoiding administrative privileges
-> Parameterized queries
-> Stored procedures
Any Questions ?

Thankyou :)
sqli
By Gopika Subramanian
sqli
- 142



