Hardware Hacking For Beginners
Why should you care about hardware?
Things To Consider
- Cost of tools;
- Logic analysers;
- USB to <PROTOCOL> (UART, JTAG, etc) dongles;
- Bus Pirate;
- Soldering Iron stations;
- More...
- Cost of tested device (at least 2);
- 1 just for "dismembering".
- Prior research;
- Previous vulnerabilities, etc.
- Legal aspect;
- Company with/without Bug Bounty program;
- Warranty.
- Importance
- Fun or impact.
Steps: Reconnaissance
- Open-Source Intelligence;
- Leaked blueprints;
- Publicly available information;
- FCC website for patent data;
- Forums and online-available firmware;
- Etc...
- Disassembly of the device/s;
- Documents and papers in the box! :D
Steps: Discovery (Poking around)
- Locating common debug Interfaces;
- UART (3-4 pins);
- JTAG (6+ pins).
- Checking network side (if one);
- NMAP-ing;
- Locating web application or other network-exposed services;
- Fuzzing.
- Locating memory chips;
- Checking permissions - web, network, and debug interfaces.
Steps: Reversing & Exploitation?
- Connecting to hardware debug interfaces;
- USB to UART connections soldering;
- USB to JTAG connection coupling.
- Accessing network/web interfaces;
- Extracting firmware (or downloading, if available);
- Extraction through debug interface;
- Extraction through direct memory chip access clamp (flash reader);
- Extraction through download from public repository.
- Reverse engineering firmware;
- Exploring and fuzzing potentially vulnerable endpoints;
- Trying hardware exploits and fault injections.
Case Study: TP-Link C200
Source of photos and some data from: https://drmnsamoliu.github.io/hardware.html
All rights are his.
The Target
- TP-Link C200 - a home surveillance camera;
- WiFi connectable, exposed to the global internet, if configured;
- Accessible via TP-Link proprietary mobile application;

The Hardware
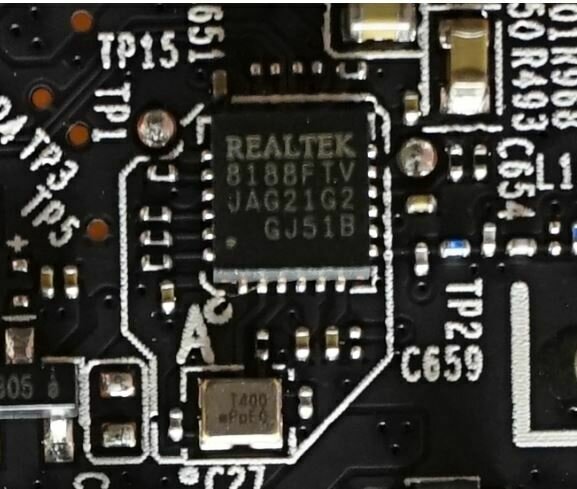


The processor: Realtek RTS3903 SoC
The network chip: Realtek 8188FTV
The memory: XMC XM25QH64A NOR Flash
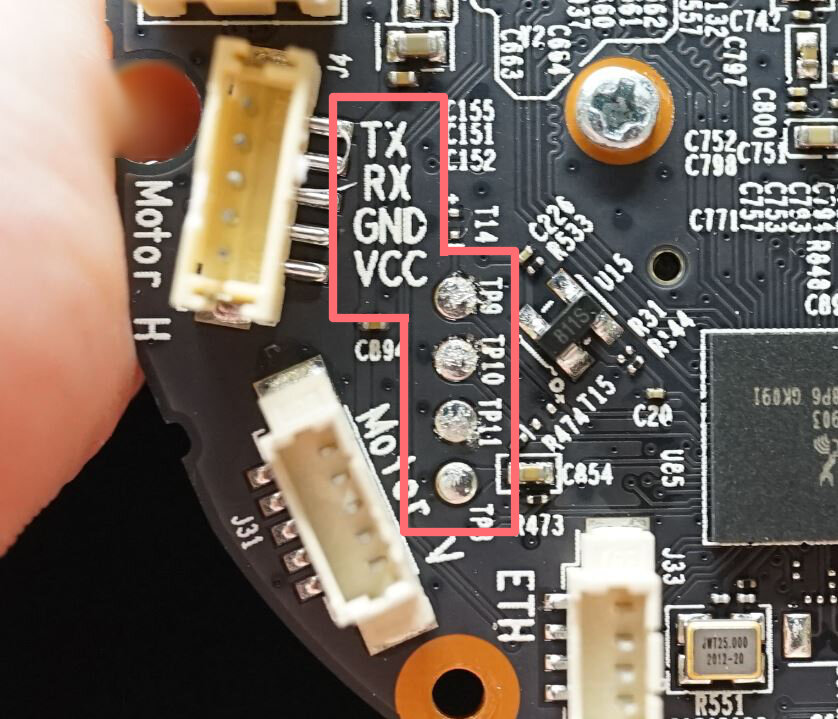
The debug interface: UART
The Endpoints
- UART access on circuit board;
- NMAP shows multiple network endpoints (and ports);
- HTTP endpoint (443) - API;
- RTSP endpoint (554) - video feed access;
- xinupageserver (2020) - motion detector access?;
- sunwebadmin (8800) - config/update?.
nmap -p- -sV 172.0.0.168
Nmap scan report for
TEST-CAM-C200 (172.0.0.168)
Host is up (0.153s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
443/tcp open https
554/tcp open rtsp
2020/tcp open xinupageserver
8800/tcp open sunwebadminGetting a Shell


Getting a Shell: The Bootl0g

On local PC:
$ sudo su
$ screen /dev/ttyUSB0 57600 Getting a Shell: The Password
<Firmware>/squashfs-root/etc/passwd
/squashfs/etc/passwd
0: $1$kX3zxwZJ$oalW3az6H3F/au8T0CB96.
After some brute forcing (curtesy to @kubik369):
slprealtekLooking at the firmware

Looking at the firmware

/bin/uhttpd

Let's see it in real life!
Hardware Hacking
By Ivan Zlatanov
Hardware Hacking
- 66



