Introduction To Reverse Engineering and Assembler
Levels Of Programming Languages
Descriptive/Declaretive Structures
Low
High
HTML, XML, JSON
Scripting Interpreters
Python, Perl, Lua, JS, PHP
VM/Drivers/Executables
C, C++, C#, Java, Pascal
CPU Instructions
Assembler, Machinecode
Computer System Architecture
CPU
RAM
Data
Address
RAM (Random Access Memory)
| Address | Data |
|---|---|
| 0 | 01100010110010111100011000011011 |
| 1 | 11111100111001110110000001110101 |
| 2 | 10001100111001110110000001110100 |
32 Bit
| Address | Data |
|---|---|
| 0 | 1000001011100101110101001011101100000000011000101010111111111100 |
| 1 | 1000101011100101110101001011101100001110011000101010111111111100 |
| 2 | 0010101011100101110101001011101110000000110001010101111111111001 |
64 Bit
CPU (Central Processing Unit)
Registers
EAX
EBX
ECX
EDX
ESP
STATUS FLAGS
...
...
...
Arithmetic Logic Unit
(ALU)
+,-, *,/
PROGRAM COUNTER
INPUT/OUTPU
Registers
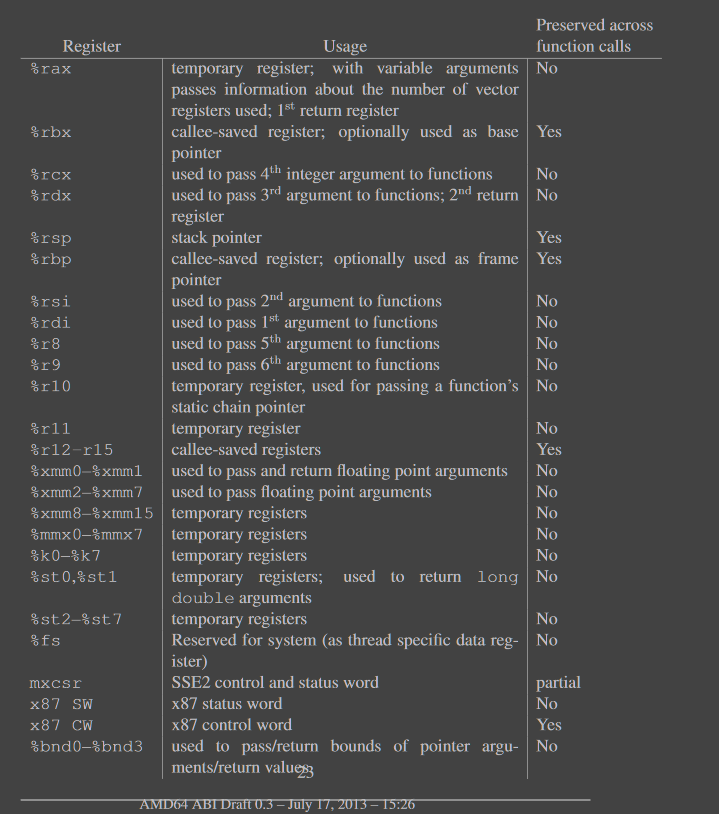
Assembler
Function (Argument #0, Argument #1)
Opcode (Oprand #0, Oprand #1)
Register
Memory
Address
Constant
Assembler
Example:
{ADDRESS/LINE} {OPCODE} {OPRAND} {OPRAND}
0 MOVE EAX [2]
1 MOVE EBX [5]
2 MOVE ECX [6]
3 MOVE EDX 0
4 ADD EDX EAX
5 ADD EDX EBX
6 SUB EDX ECX
-----------------------------------------------------------------
Enough low-level
for now
What is reverse engineering
- Simply put, a way to understand the inner workings of software or hardware without proprietary documentation.
- A process of taking software or hardware and analyzing its functions in order to understand its functionality.
It's not only C and ASM
- Reverse engineering is not related to C programs and it's not always reading ASM.
- We have MSI files -> pseudo C# code.
- We have .pyc and .pyo files -> Python code.
- We have Bash scripts.
- We have hardware components.
What to do
- Gather info about the target file (file, strings).
- Gather info about the architecture.
- Gather metadata.
- Start decompiling.
- Reconstruct pseudocode.
- Patch/reproduce (if needed).
Now some practice
Copy of Introduction to
By Ivan Zlatanov
Copy of Introduction to
- 70



