Assistance au développement et au test d’applications sécurisées

Soutenance de thèse
Présentée par : Loukmen REGAINIA
12 Juin 2018


Sous la direction de :
- Pr. Sébastien SALVA
- Dr. Cédric BOUHOURS
-
Implementing secure software
- expertise, knowledge, time consuming
- Software security is essential and should be considered as early as possible
- Developers are provided with a plethora of documents:
- Vulnerabilities, Attacks, Weaknesses, etc
- Security Principles and best practices
- Security Patterns
Introduction
2
- Weakness
- Vulnerability
- Attack
- Threat
- Security Principle


Introduction

CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')
CVE-2018-8045 (Joomla 3.5.0 - 3.8.5)
CAPEC-66: SQL Injection
In depth defense
Relying on user input

3
Security patterns
A pattern is a generic solution to a recurrent problem

4
Security patterns
A pattern is a generic solution to a recurrent problem
security
security

4
SP := (C,P,S)
Security patterns
Context
Problem
Solution
Schumacher et al. 2001

5
Security patterns
A pattern is generic
Must be integrated
Difficult and error prone task

6


Security patterns




7
Pattern
Application model
Pattern Integration
Security patterns


8
Security patterns

8
Security patterns
A security pattern is not an island M. Schumacher et al.


9
K.Yskout et al.
Contributions
- Measure Security Pattern integration quality
- Measure Security Pattern effectiveness against vulnerabilities
- Knowledge Base design and fulfillment
- Security Pattern classifications
- Security and Pattern testing

10
-
Security Pattern integration
-
Security Pattern classification
-
Security and Pattern testing
-
Conclusions and Perspectives
Outline
11
1 :Security Pattern integration
12
Introduction
Where:
- M the UML model of the application
- V = {V1,..,Vn} a set of Vulnerabilities
- SP = {Sp1,..,Spk} a set of Security Patterns
- Pvi , Pspj sets of Vulnerability i, and Security Pattern j LTL (Linear Temporal Logic) generic properties
M
V
SP
Wants to protect
Against
Using
Dev
13
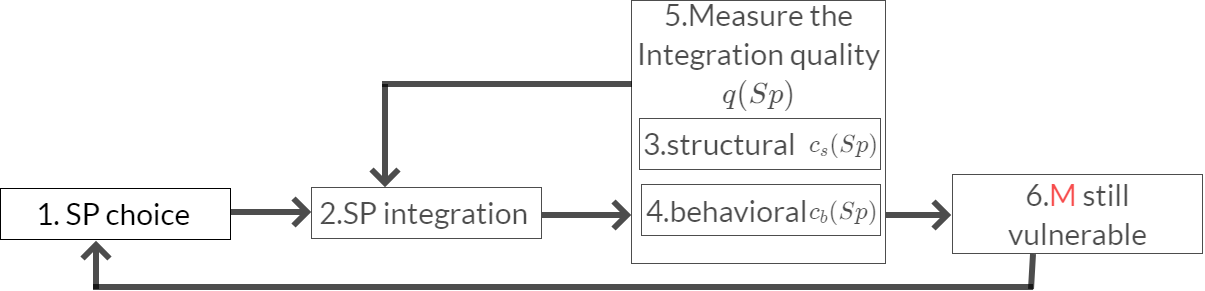
Big picture
1. SP choice
2.SP integration
3.structural
4.behavioral
5.Measure the Integration quality
6.M still vulnerable
Vulnerability coefficient
Vulnerabilities V

14
2. Pattern integration (Structural)


15
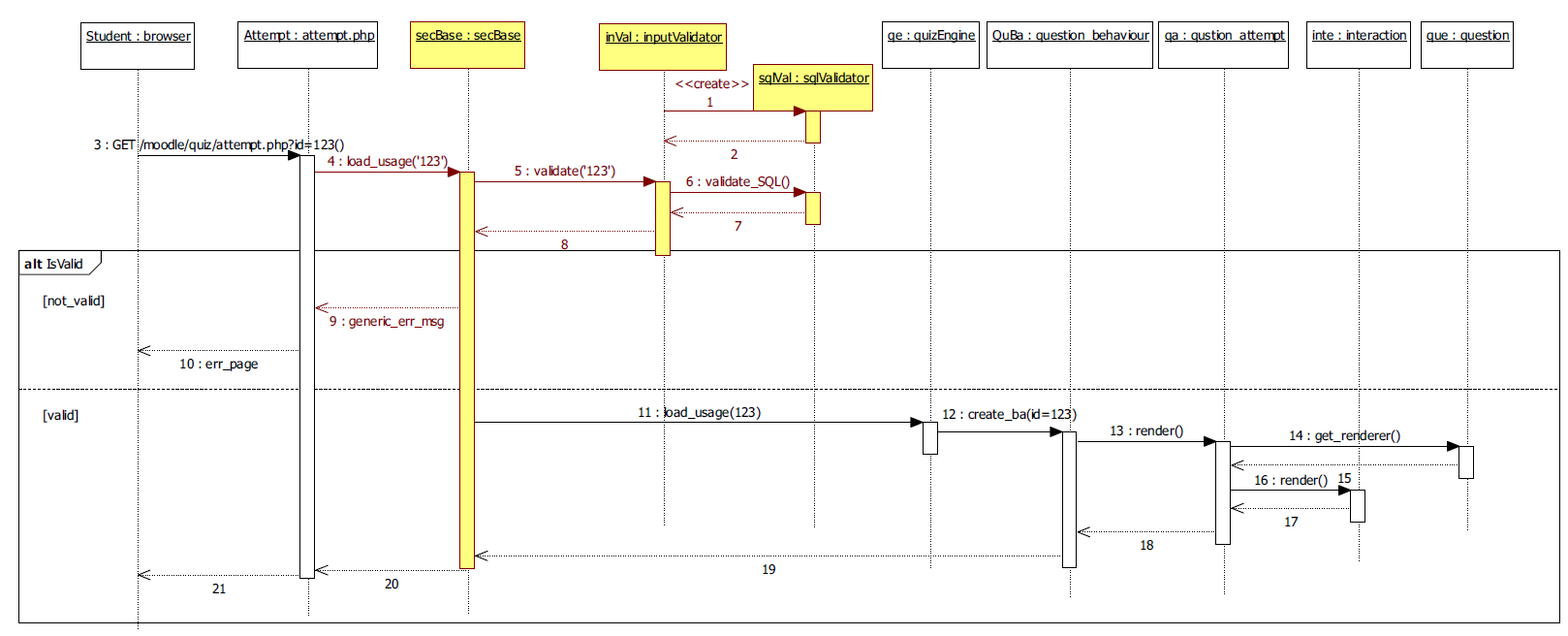
2. Pattern integration (Behavioral)


16
3. Structural integration quality
With the Disclosure Coefficient of the Pattern i


17
4. Behavioral integration quality
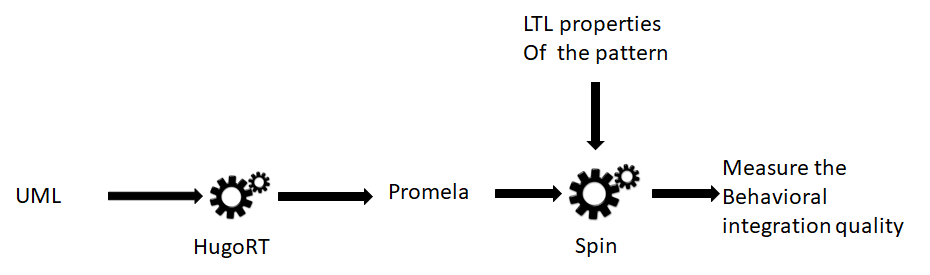


18
4. Linear Temporal Logic (LTL)
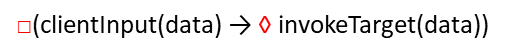
Generic :
Instantiated :



19
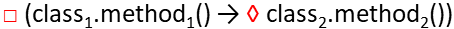
4. Behavioral integration quality
where:


20
K. Yoon 1995
Simple Additive Weighting
5. Overall integration quality
A Pattern Sp
The set SP
where


21
6. Pattern effectiveness
Overall vulnerability coefficient
- We check whether M is still vulnerable

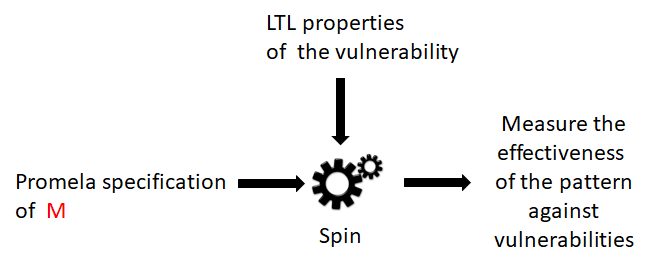

22
Chapter Conclusions
Open issues :
- A Pattern cannot be the silver bullet against a vulnerability
- Need to use other patterns Difficult to choose patterns
M
V
SP
Wants to protect
Against
Using
Dev

23
Published in :
- CIEL 2015
- Softeng 2016
- TSI 2016
2 : Security Pattern classification
24
Open problems
- Many Security Patterns difficult choice
- One Security Pattern cannot protect an application
- Directly associating a Pattern and an Attack or a Weakness is awkward
- Security Patterns are inter-related
25
Big Picture
3 Security Patterns classifications WRT:
- Weaknesses
- Attacks and Weaknesses
- Attack steps and techniques

26
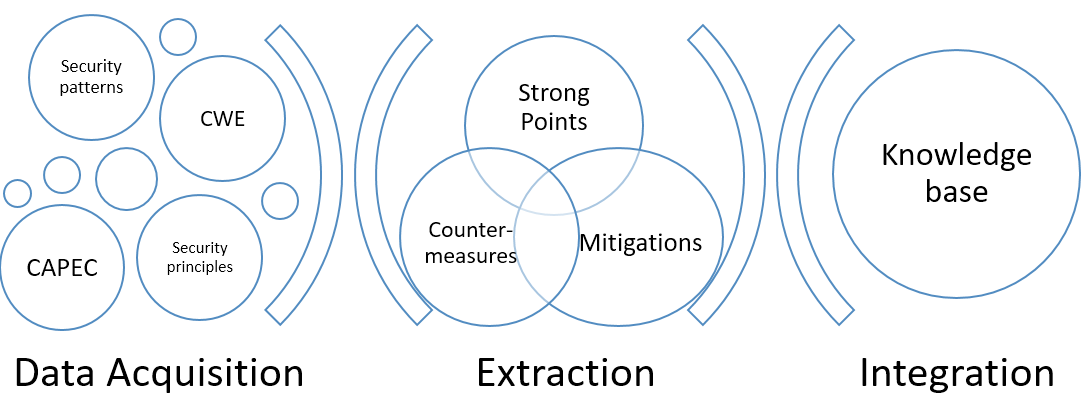
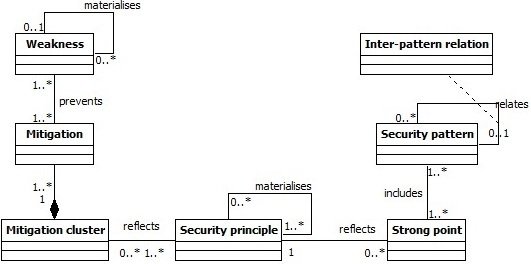
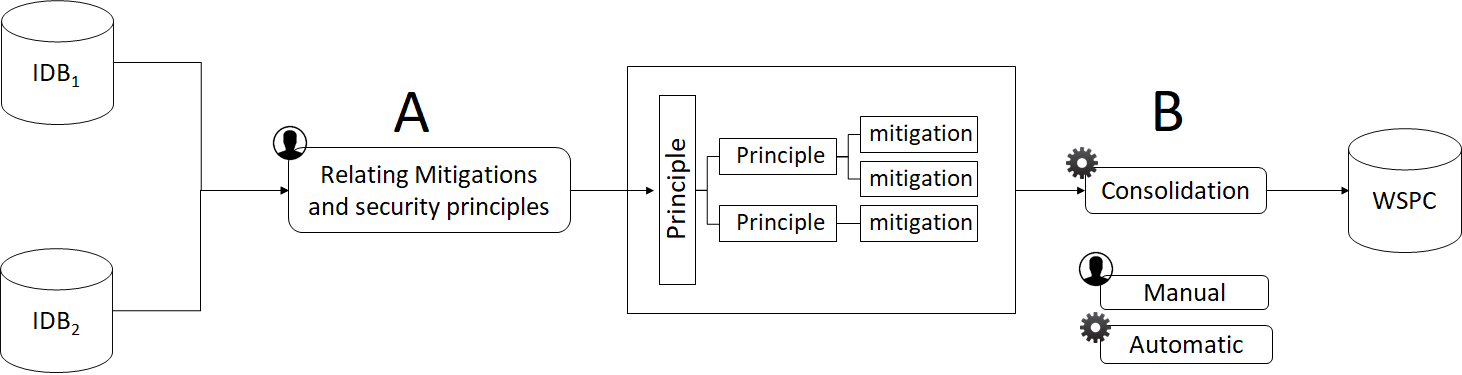
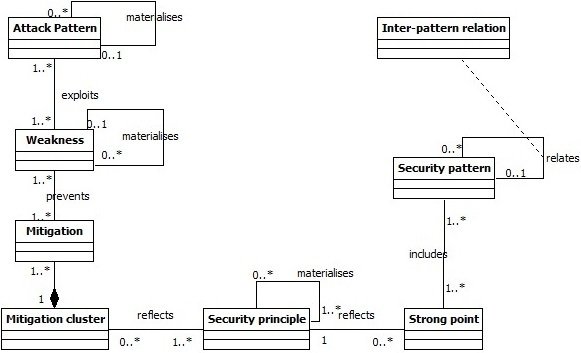
Classification Meta-model
- Objective : Classify patterns w.r.t weaknesses

27
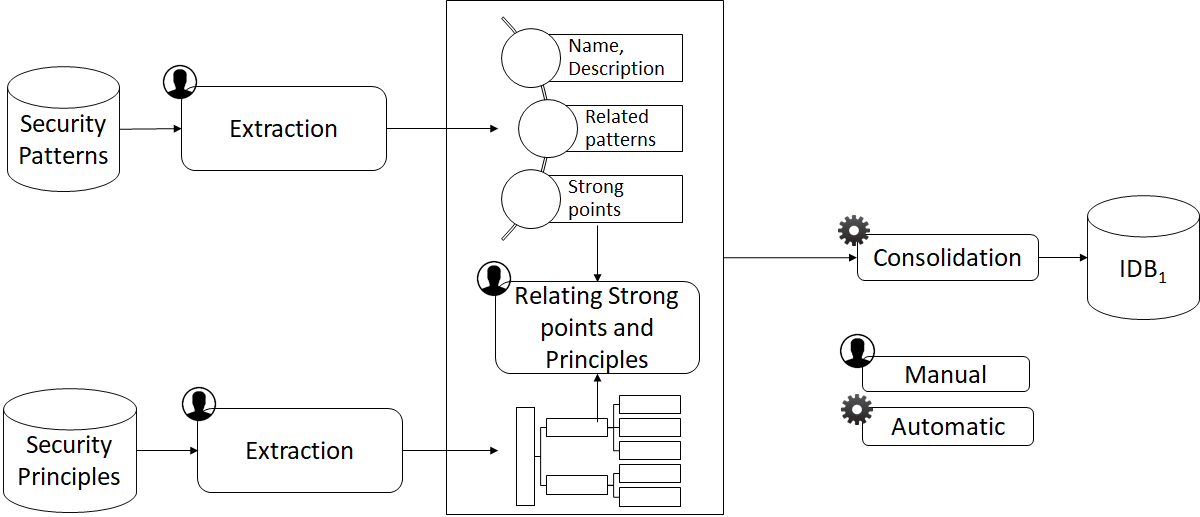
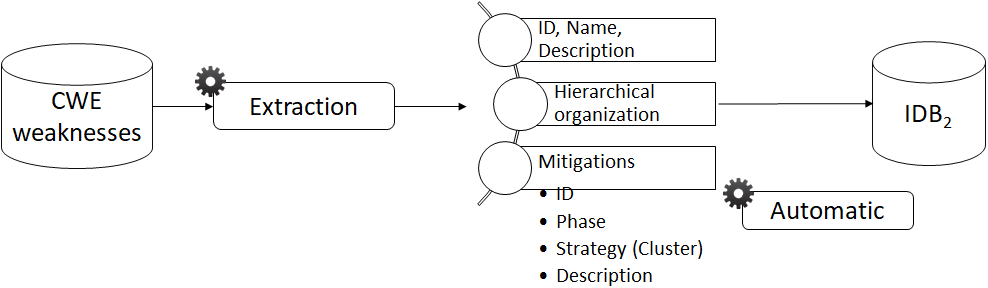
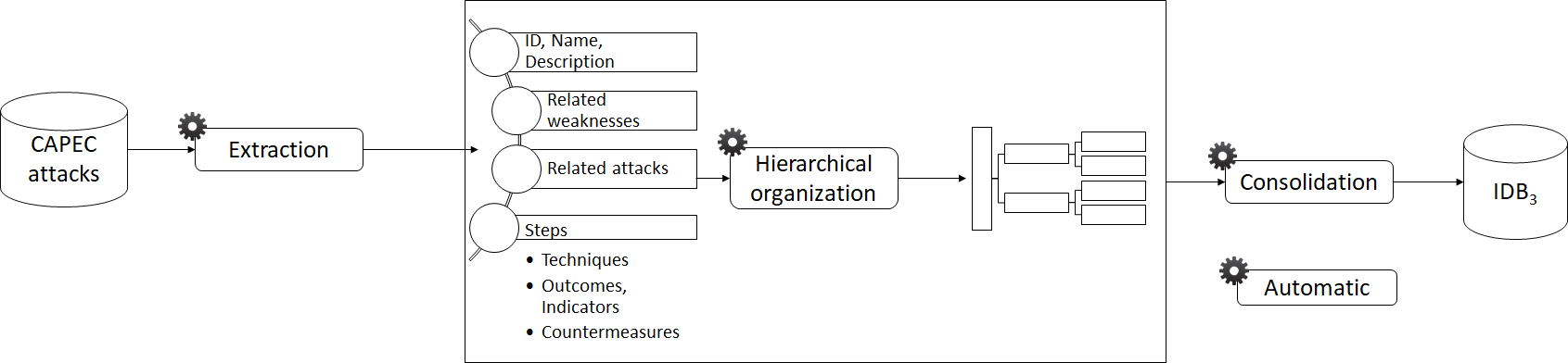
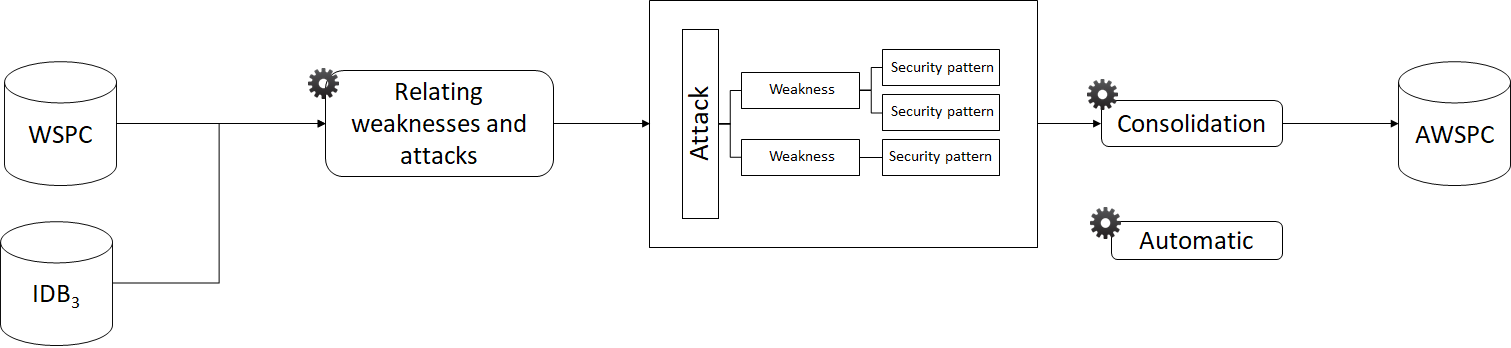
Classification Extraction
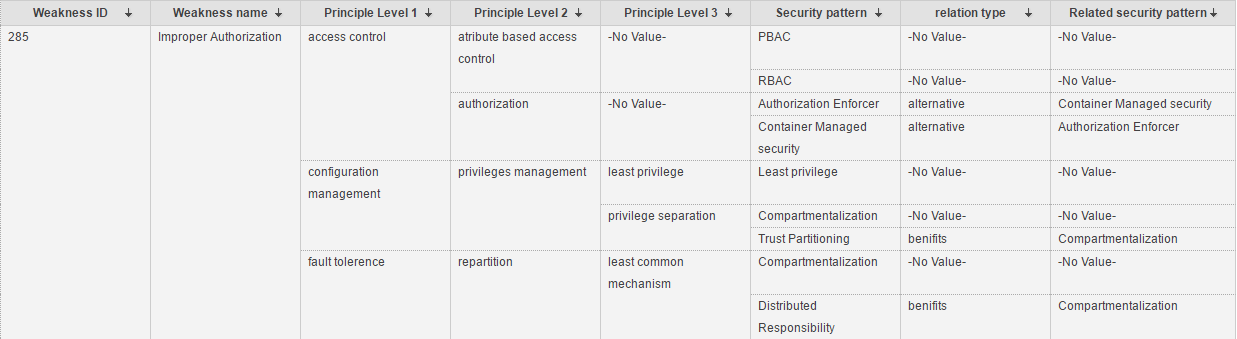

28
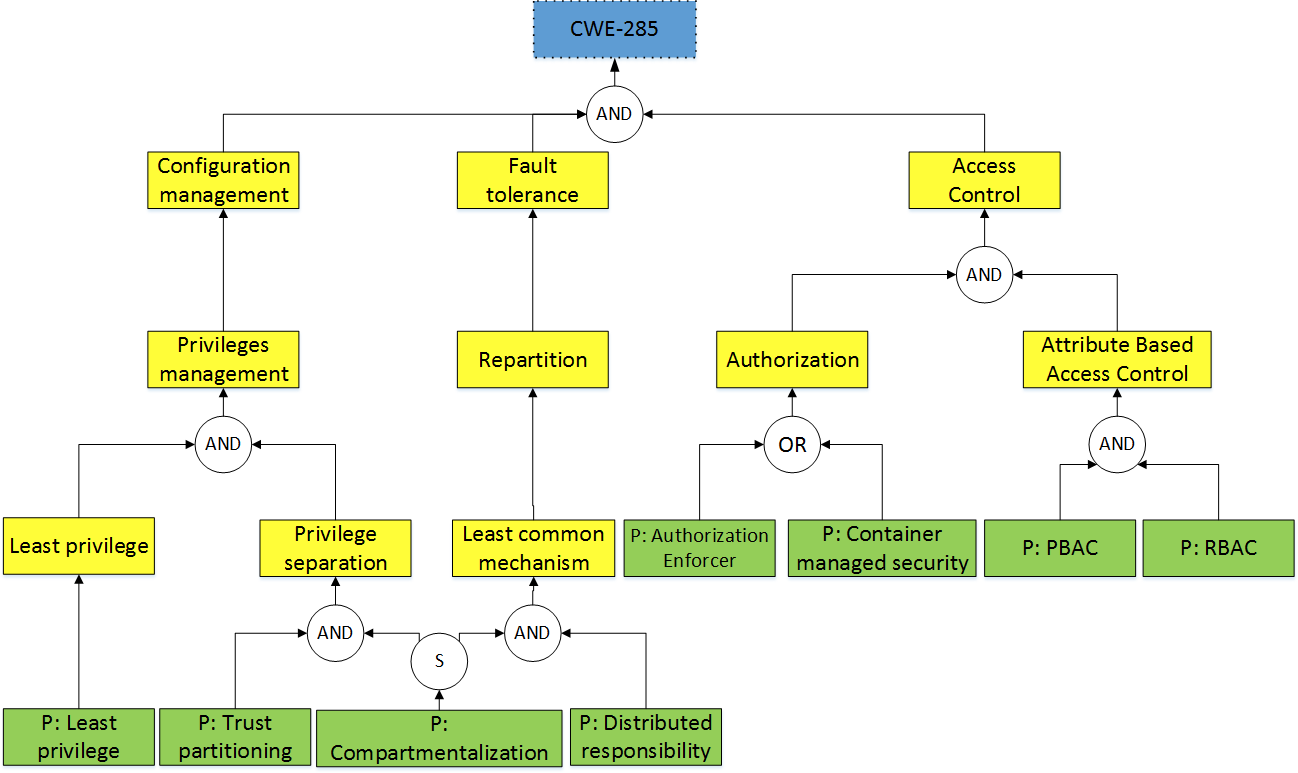
Security Activity Graphs generation

29
Weakness
Principle
Pattern
S
Split
S.Ardi et al. 2006
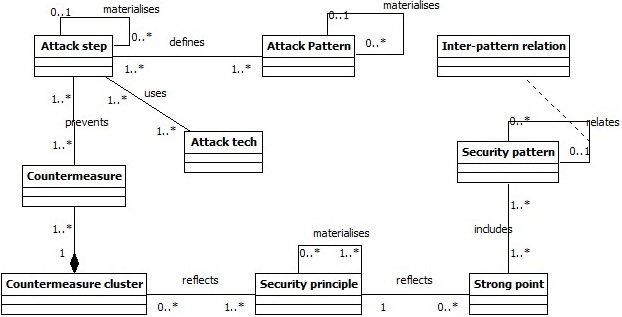
Classification Meta-model

30
- Objective : Classify patterns w.r.t Attack steps and techniques
Classification Extraction
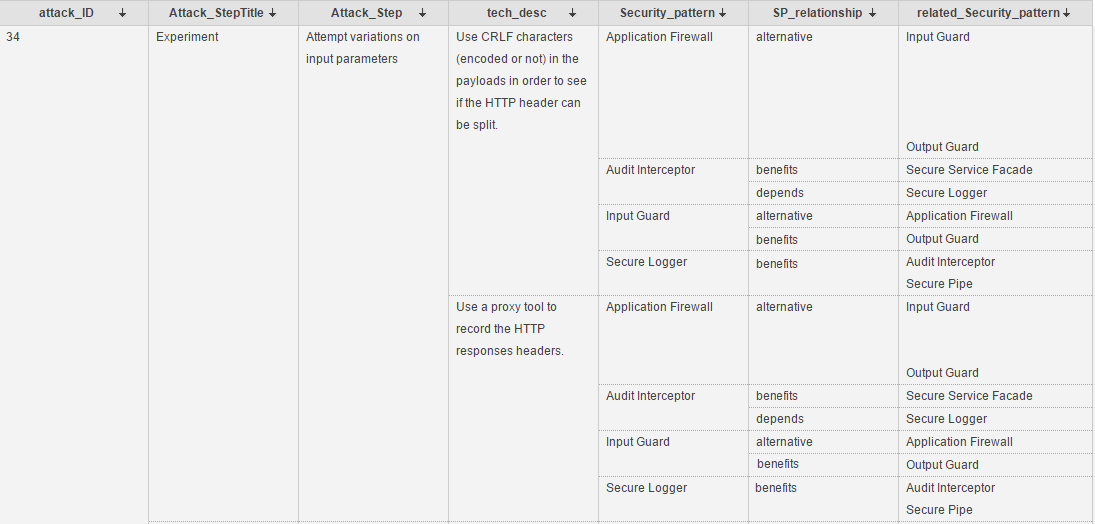

31
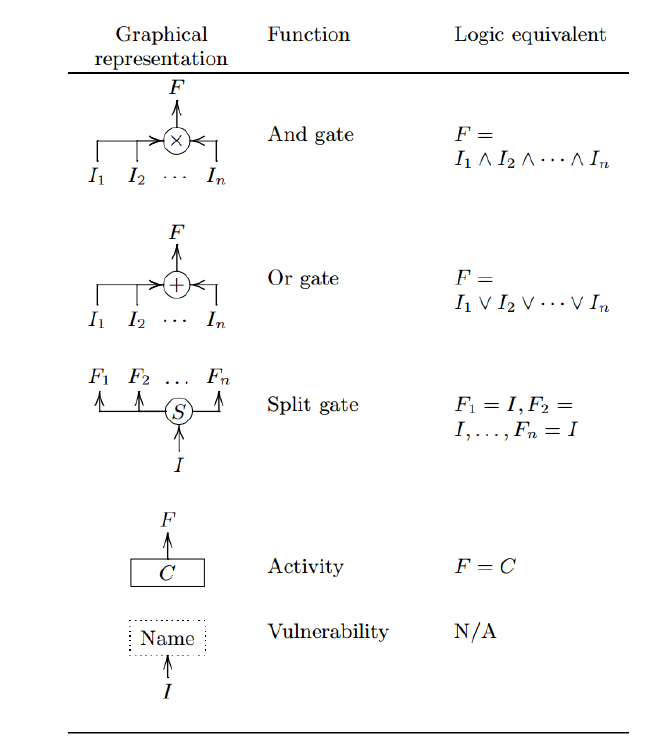
Attack Defense Trees
An ADTree can be expressed with :
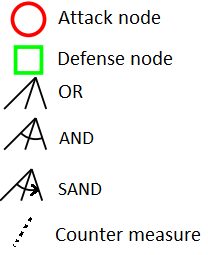
Opponent "o"
Proponent"p"
Algebra (ADTerms):
Graphical:

32
B.Kordy et al. 2014
ADTree generation
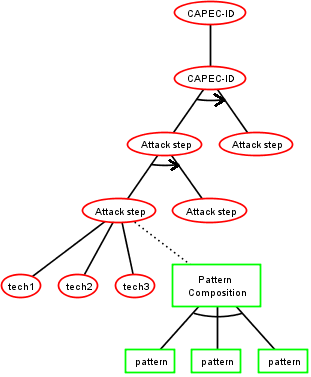

33
Chapter Conclusions
We presented :
- Data Integration methods
- 3 classifications comply with
- Navigability
- Unambiguity
- Usefulness
- Automatic generation of :
- Security Activity Graphs
- Attack Defense Trees
Perspectives:
- Generate tests from ADTrees to test attacks and security patterns
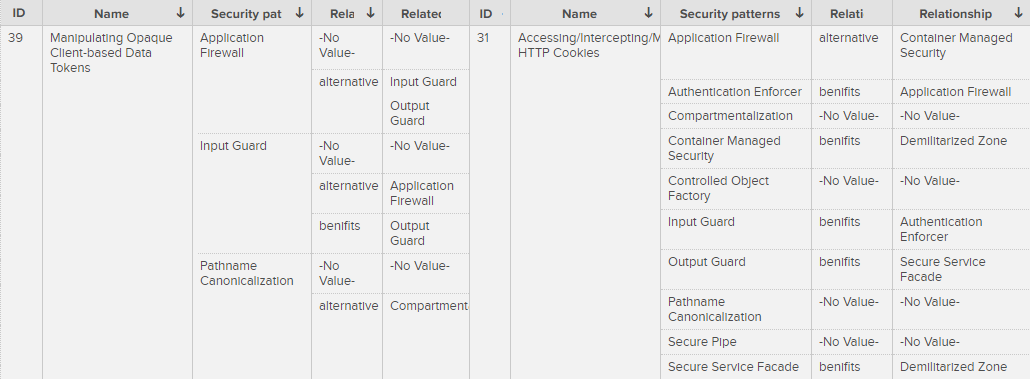
Knowledge base

34
Published in :
- AICSSA 2016
- ICISSP 2017
- CRISIS 2017
- RSIS 2018
3 : Security and Pattern testing
35
We propose:
- Pragmatic approach to guide developers in choosing security solutions and writing concrete test cases for :
- Checking whether the application is vulnerable
- Checking whether pattern observable consequences are absent
- Writing concrete security tests is long and difficult
- Testing security patterns (Generic) is difficult
Open Problems
36
37
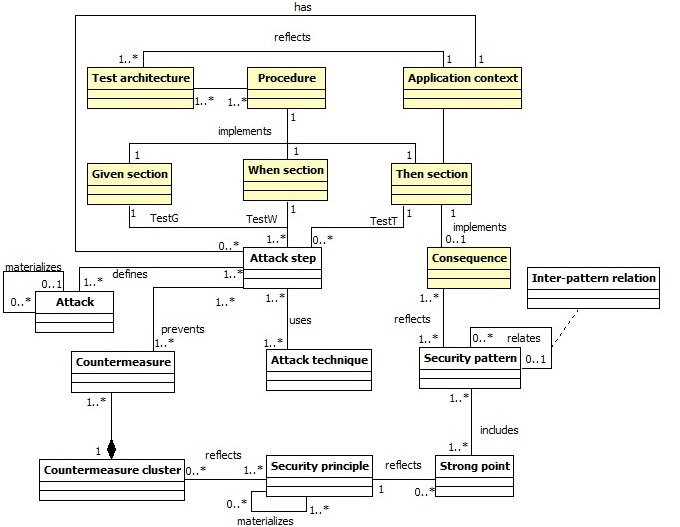
Meta-model
Method steps

38
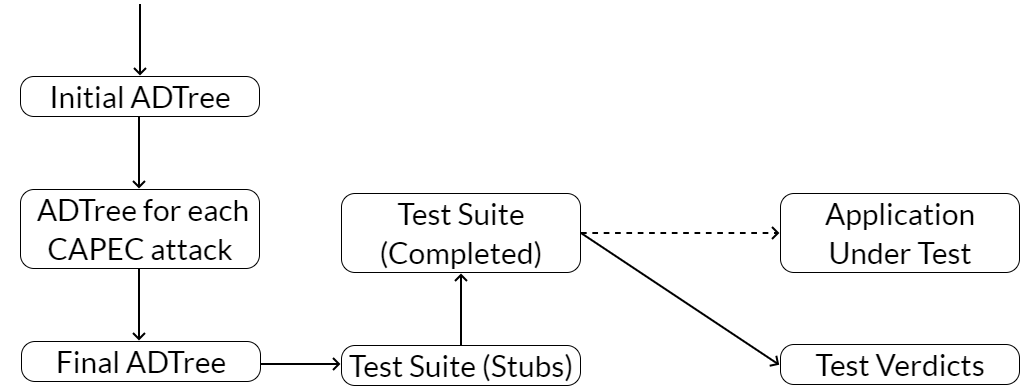
Initial ADTree
ADTree for each CAPEC attack
step 1
step 2
step 3-4
Final ADTree
Test Suite (Stubs)
step 5
Test Suite (Completed)
Application Under Test
Test Verdicts
step 6
step 7
Step 1: Initial ADTree T
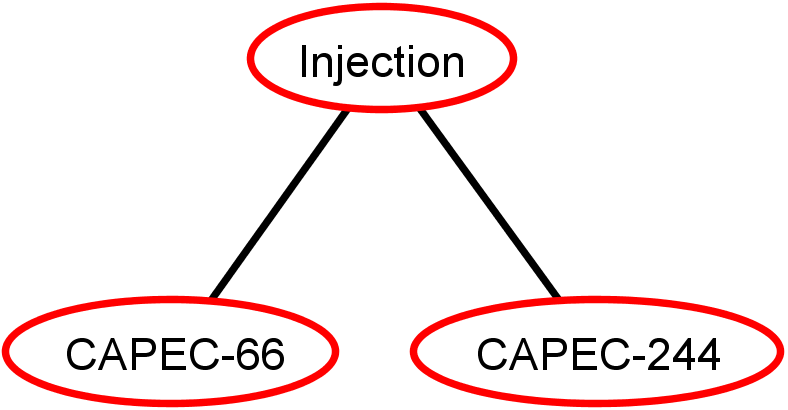
- CAPEC-66: SQL Injection
- CAPEC-244: XSS Targeting URI Placeholders

39
Step 2: ADTree Generation
The form of the tree depends on the Knowledge base

40

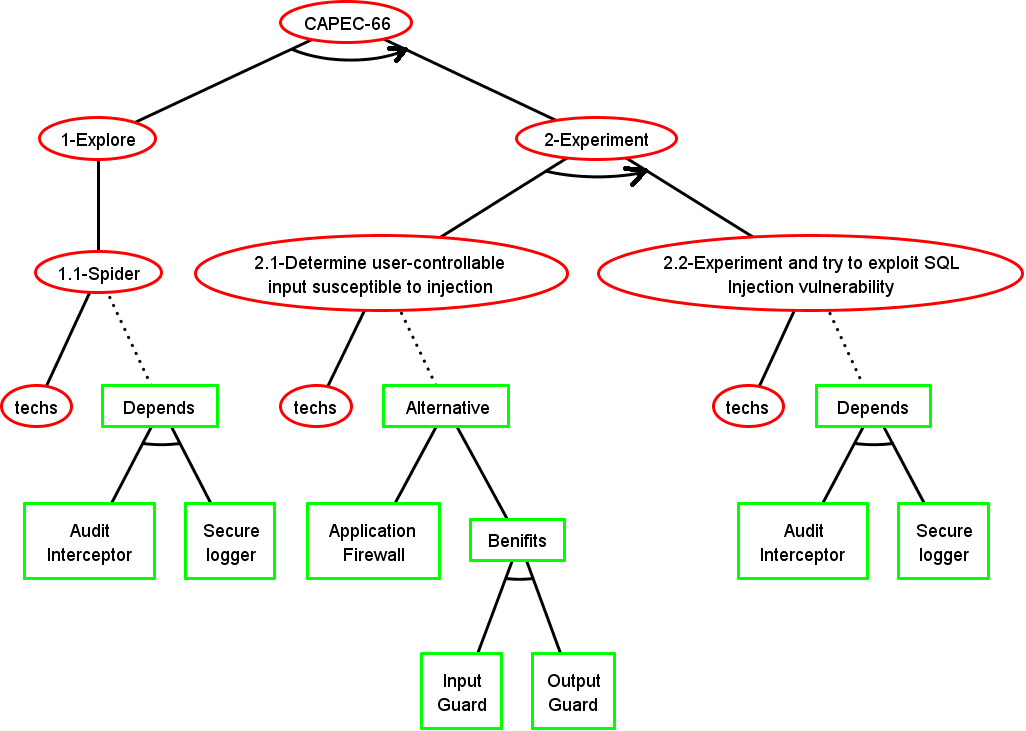
Step 3-4: Final ADTree
Basic Attack Defence Step (BADStep)
st
sp

41

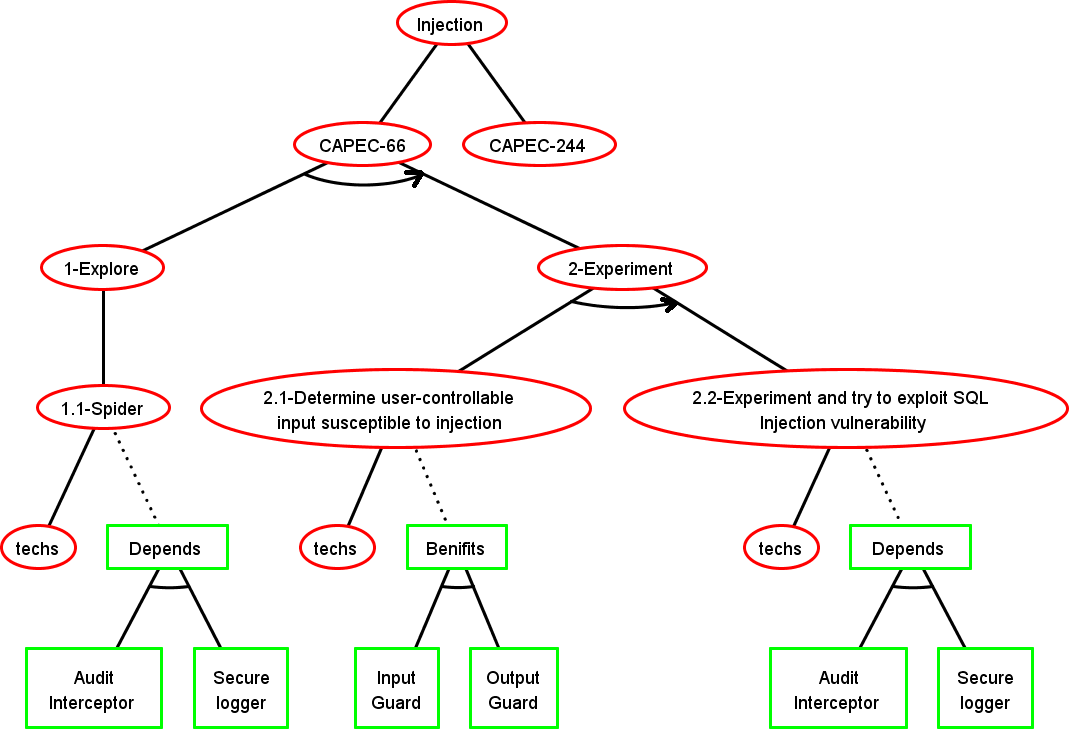
Step 5: Test Suite Generation
Attack Scenario
Test Suite

42

Step 6: Test Suite Completion

43
Given
When
Then
Procedure
Completed using pentesting tools
A procedure is generic if reusable in a context

Step 7: Test Suite Execution
Local test verdicts

44

Step 7: Test Suite Execution
Final test verdicts
45
Method Evaluation
- 24 participants to evaluate :
- Comprehensibility
- Accuracy
- Efficiency
- Security pattern choice w.r.t :
- SQL Injection
- Cross site scripting
- Writing test cases

46
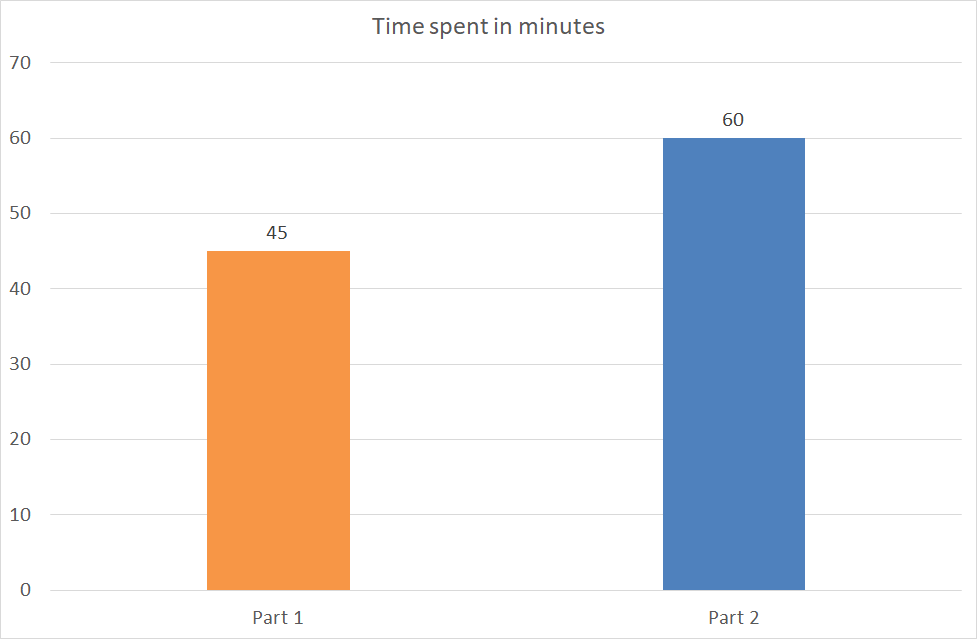
Part 1 (1h30):
- Basic documents
Part 2(1h30):
- Basic documents
- ADTrees
- GWT test cases
Method Evaluation
| Comprehensibility | Part 1 | Part 2 |
|---|---|---|
| Pattern choice | 00.0% | 33% |
| Understanding Attacks | 41.7% | 87.5% |
| Understanding Patterns | 37.5% | 87.5% |
| Writing test cases | 33.3% | 58.3% |

47
Method Evaluation
| Accuracy | Part 1 | Part 2 |
|---|---|---|
| Pattern choice (correct) | 00.0% | 62.5% |
| Writing test cases (correct) | 0.1% | 78.1% |

48
Method Evaluation
| Efficiency | Part 1 | Part 2 |
|---|---|---|
| Pattern choice | 32 m | 14 m |
| Writing test cases | 46 m | 60 m |

49
Chapter conclusions

50
We proposed :
- Knowledge base for test case generation
- Test case generation and execution
- Check vulnerability
- Check observable pattern consequences
- Evaluation with 24 participants
Issues :
- Checking pattern consequences (not enough)
- Knowledge base not exhaustive
Published in :
- AFADL 2017
- ICTSS 2017
We presented approaches and tools to assist developers :
-
Security Pattern integration
-
Security pattern classification
-
Security and Pattern testing
Conclusions
51
Perspectives
- Knowledge base completion
- Check patterns behavioral properties w.r.t execution traces
- Associate patterns with well known threat management methodologies
- Security Reference Architecture (patterns + Knowledge base)
52
Thank you for your attention
ADTree generation method 1
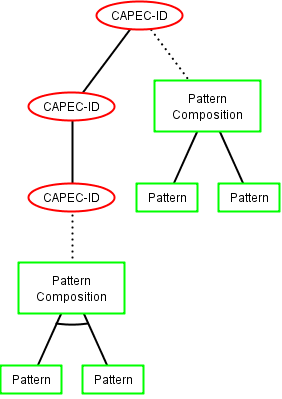
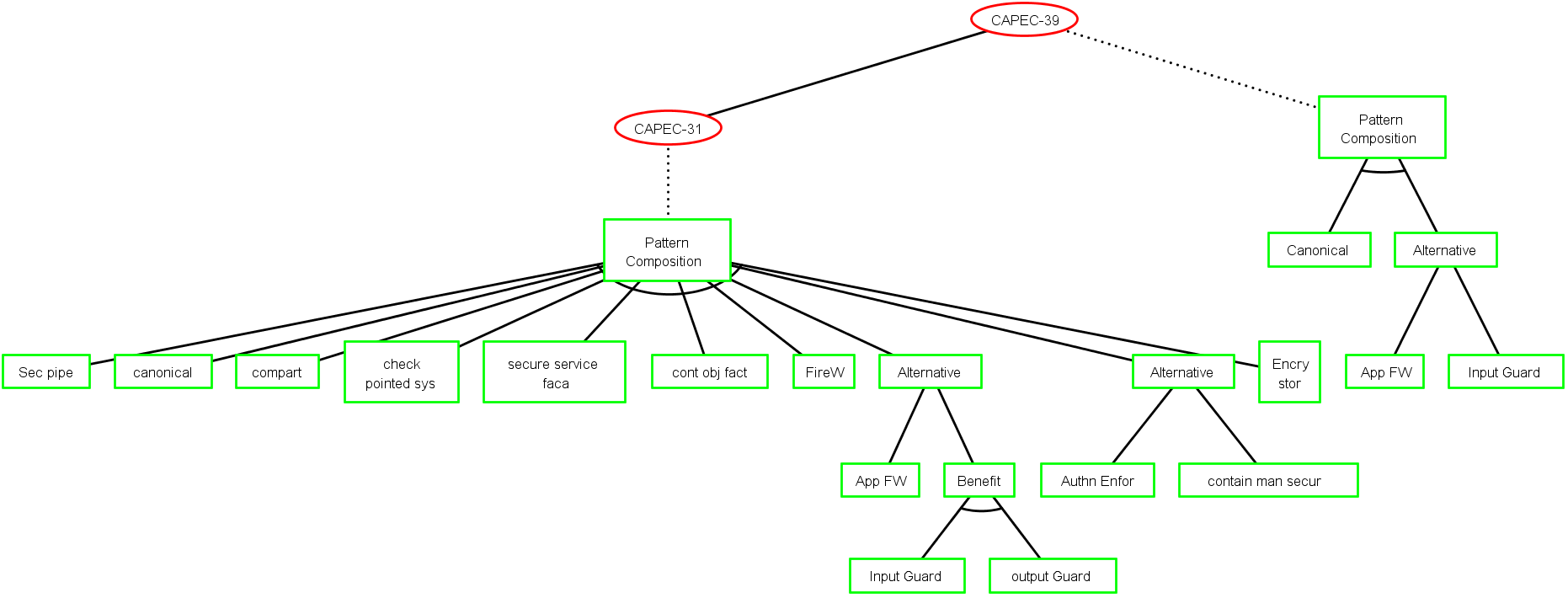
ADTree generation method 1
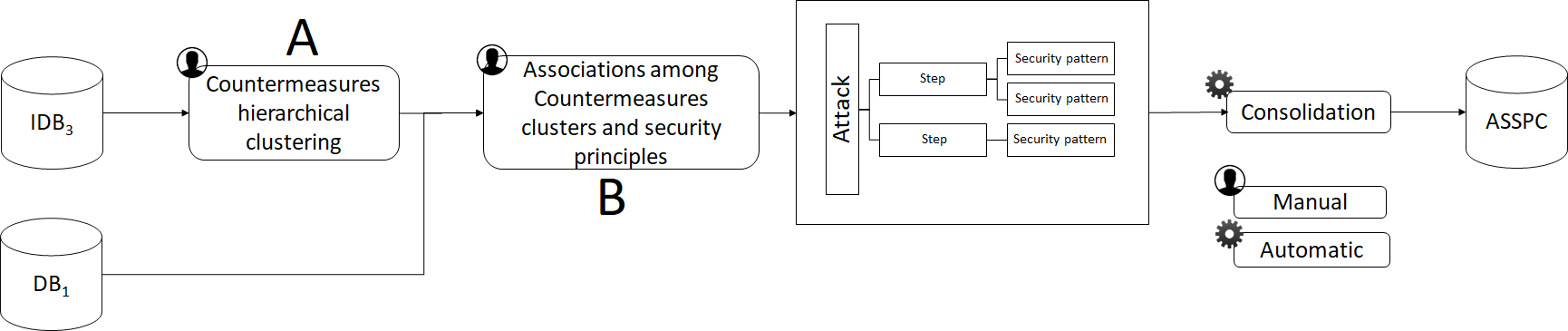
- POS Tagger and stop words definition
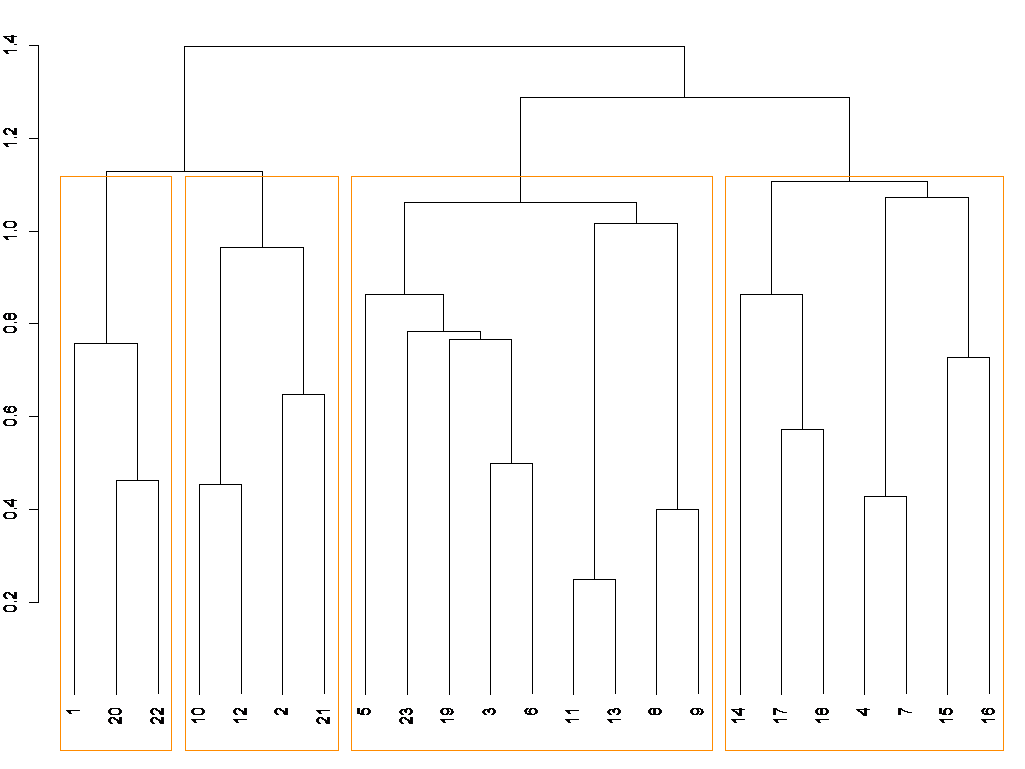
- Distance matrix with “Jaccard”
- Hierarchical clustering with “Ward”
ASSPC
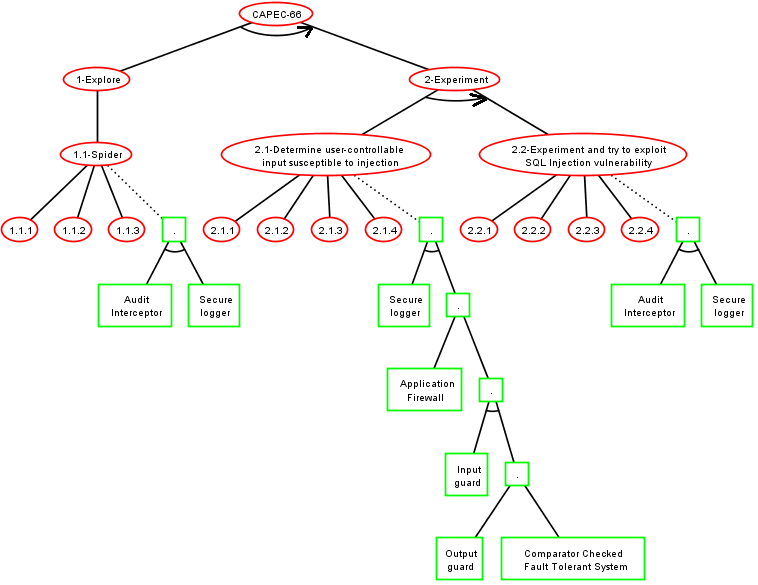
ADTree generation method 2
Step 3: Security pattern choice
Basic Attack Defence Step (BADStep)
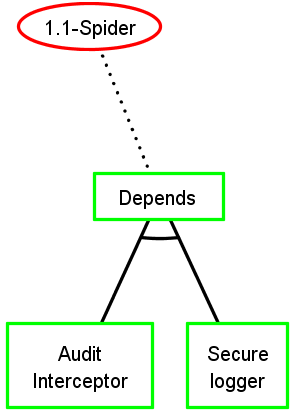
Keep security pattern conjunctions
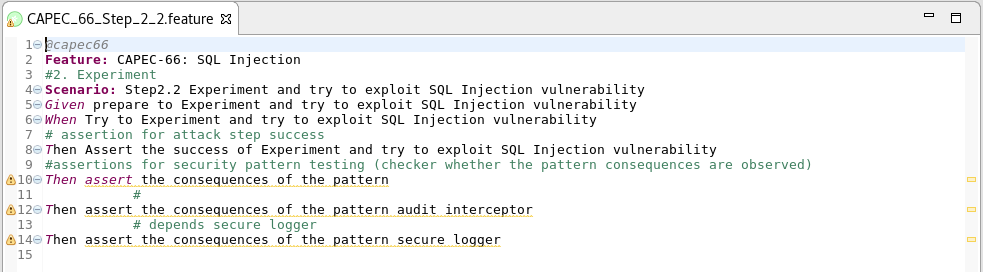
Step 5: Test suite generation
Test case (TC) example :
Step 5: Test suite generation
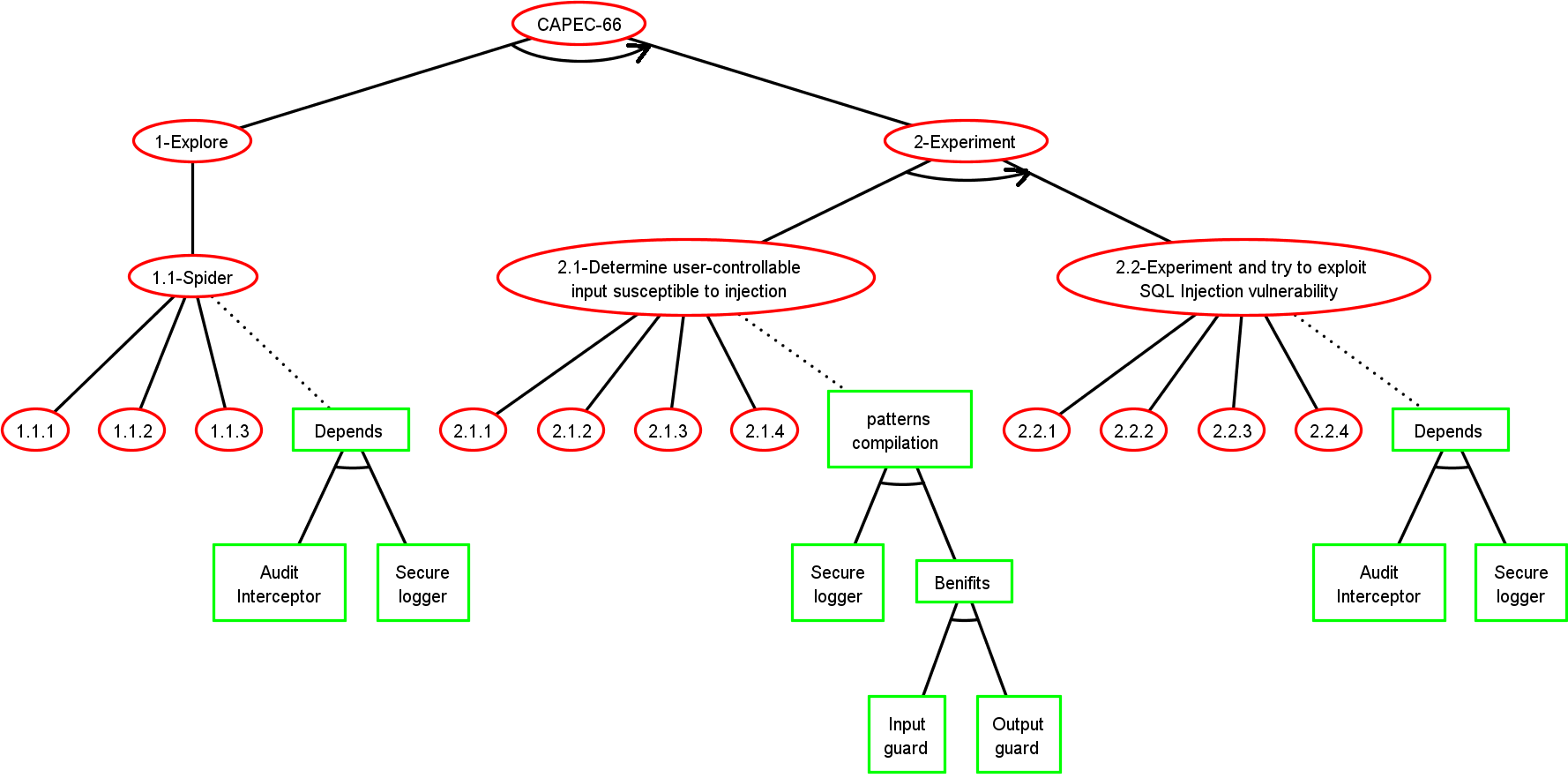
BADStep
Test scenario extraction from ADTree using ADTerms
Step 5: Test suite generation
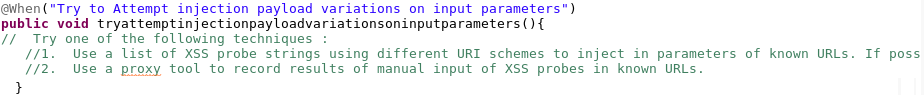
Step 6: Test case completion
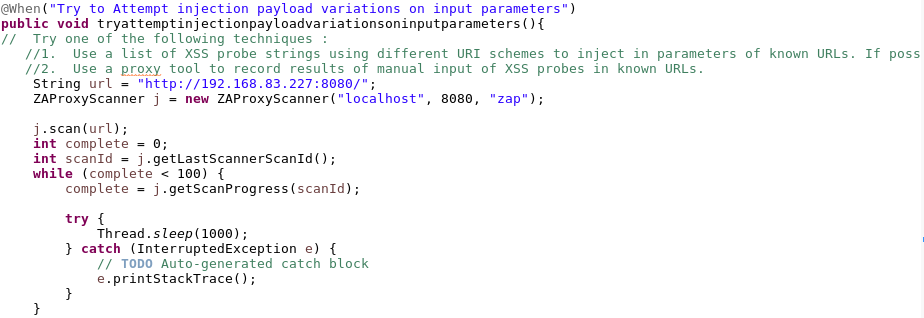


Methodology Evaluation results
- C1: Comprehensibility
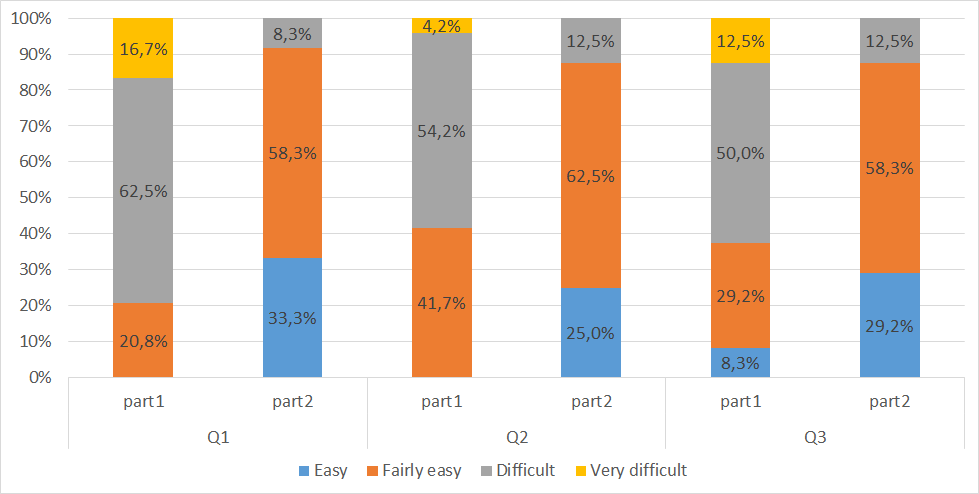
Methodology Evaluation results
- C2: Effectiveness
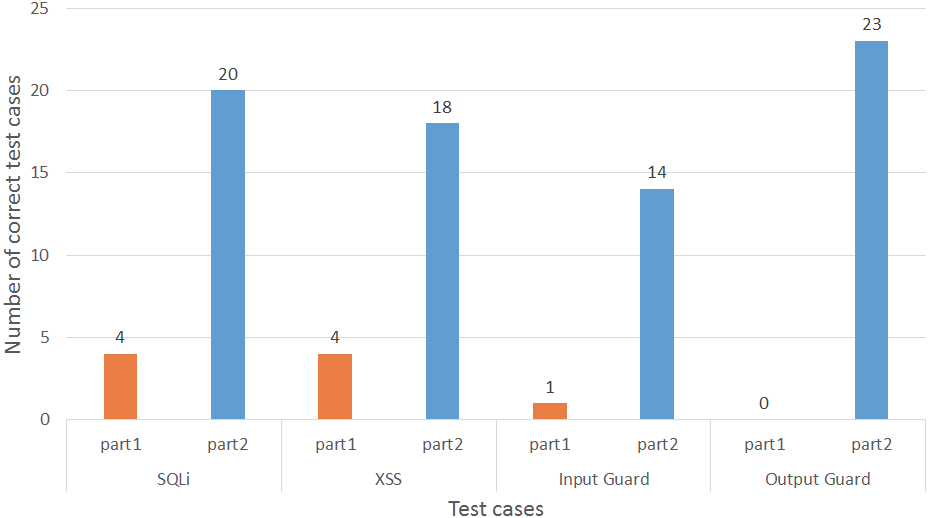
Methodology Evaluation results
- C2: Effectiveness
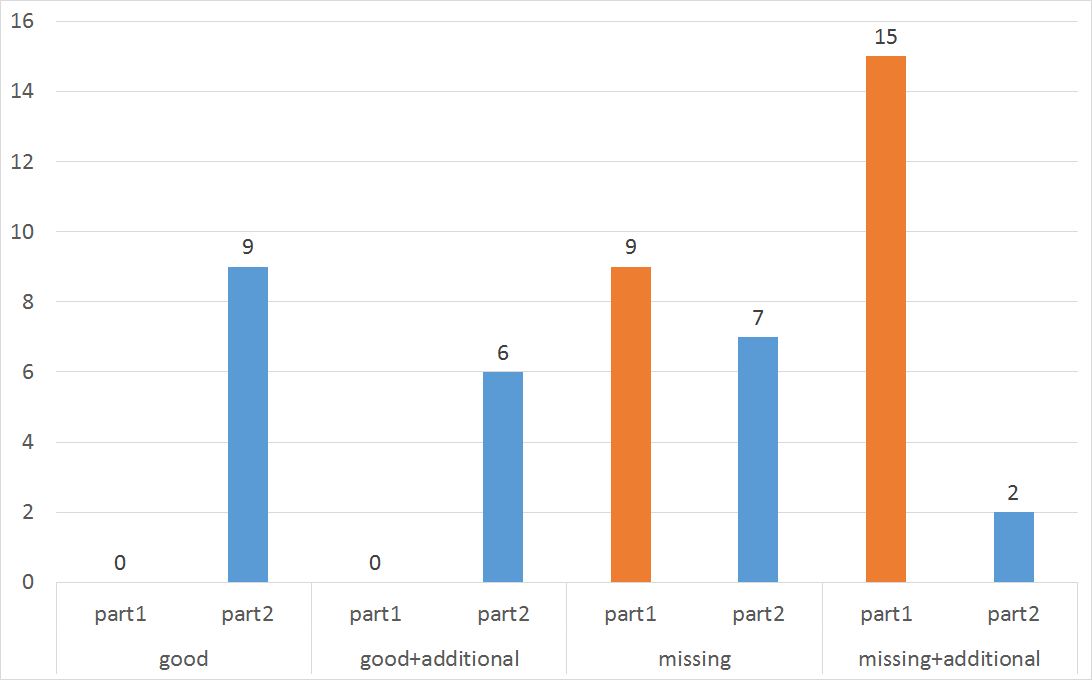
Methodology Evaluation results
- C3: Efficiency
Soutenance
By Loukmen Regainia
Soutenance
- 316


