A classification methodology for security patterns to help fix software weaknesses
AICCSA 2016
Authors : Loukmen REGAINIA, Sébastien SALVA, Cédric BOUHOURS
Presented by : Loukmen REGAINIA
LIMOS, Auvergne Clermont University, Clermont-Ferrand, France


Introduction

Web applications are usually badly designed, or not at all !!!
Most of badly designed applications are Vulnerable
Secure design skills are not common in all the members of a development team
Security patterns are abstract, generic and reusable solutions to recurrent security problems
Security patterns

A security pattern has:
- an intent : The main aim of the pattern
- a problem : In which the pattern is advised
- forces : why this pattern and not an other
- a solution :
- a structure and a behavior
- consequences : how the application will
be with the use of the pattern
- a set of related patterns:
depend, benifit, impair, alternative,
conflictual
Security patterns
The strong points of a pattern:
The security properties contributed by the use of the security patterns
Manually extracted from :
- forces : why this pattern and not an other
- consequences : how the application will
be with the use of the pattern
Security patterns

Limited view pattern
Full view with errors
Security patterns

Security patterns
- A pattern P1 may (Depend, benefit, impair, alternative, conflict) a pattern P2.
- The abstract presentation of patterns
- Growing number of patterns
Why using security patterns stills difficult ?


A security pattern cannot completely cover a weakness
The combination of patterns to mitigate a weakness, OR not !
Two patterns can be conflictual when used together
What is the best combination of patterns against a weakness ?


Exemple : access control security principles





Data consolidation with


Online database
http://regainia.com/research/database.html
Text
Example
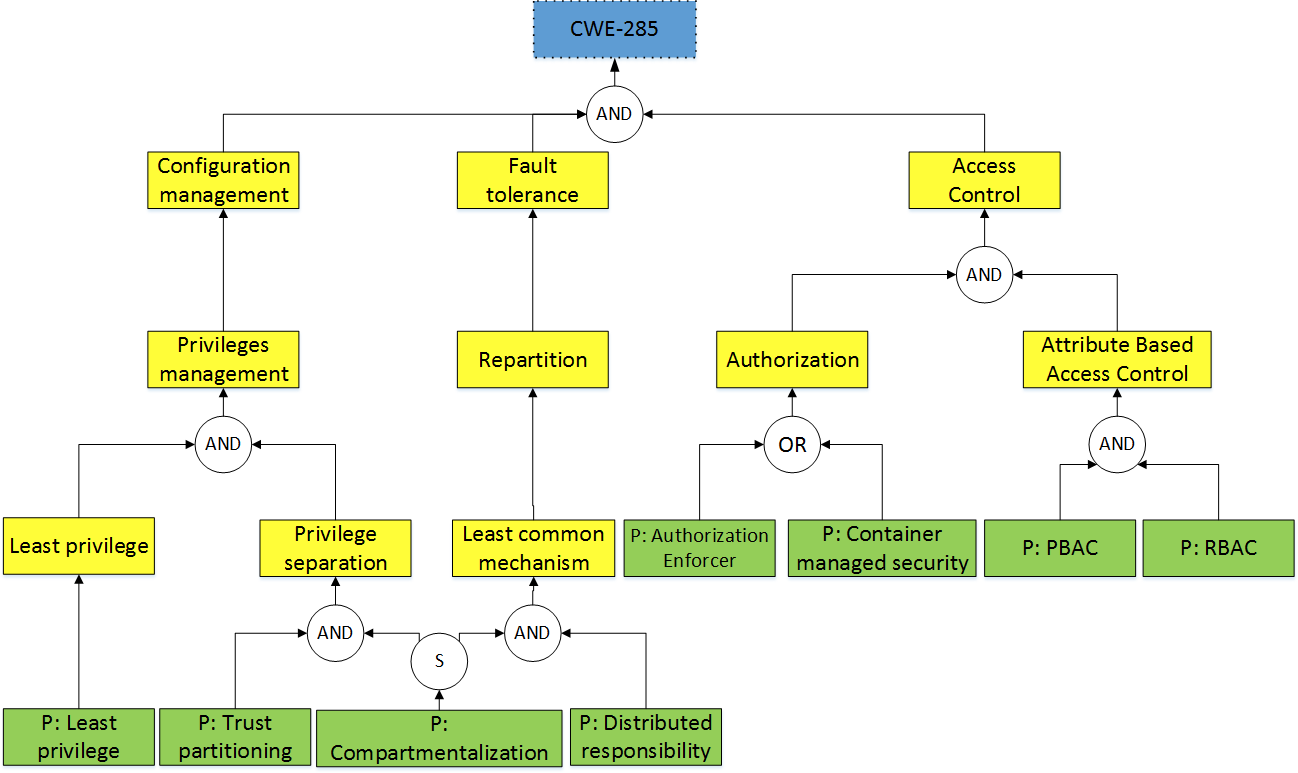
conclusion
A data base of :
185 CWE weaknesses
26 security patterns
66 elemental security principles
An accurate classification of patterns and weaknesses
The presentation of the classification methodology
The generation of SAG (security activity graphs) to get the best combination of patterns against a weakness
work in progress

thank you for your attention
Copy of Copy of UI Team
By Loukmen Regainia
Copy of Copy of UI Team
- 298


