A Practical Way of Testing Security Patterns

Loukmen REGAINIA, Sébastien SALVA
Nice 15/10/2018


ICSEA 2018
-
Implementing secure software
- expertise, knowledge, time consuming
- Software security is essential and should be considered as early as possible
- Developers are provided with a plethora of documents:
- Vulnerabilities, Attacks, Weaknesses, etc
- Security Principles and best practices
- Security Patterns
Introduction
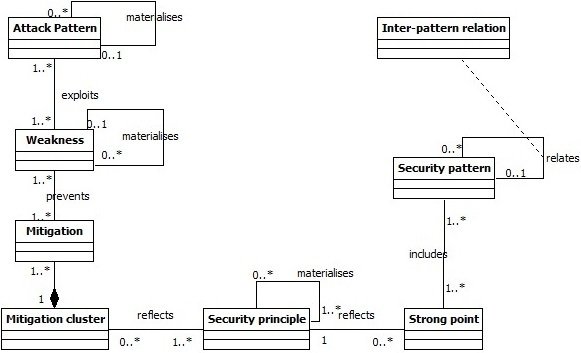
Security patterns
A pattern is a generic solution to a recurrent problem
security
security
SP := (C,P,S)
Security patterns
Context
Problem
Solution
Schumacher et al. 2001
Security patterns
A pattern is generic
Must be integrated
Difficult and error prone task


Security patterns
A security pattern is not an island M. Schumacher et al.

K.Yskout et al.
-
LTL, ADTrees
-
Knowledge base
-
Method steps
-
Conclusions and Perspectives
Outline
Linear Temporal Logic (LTL)
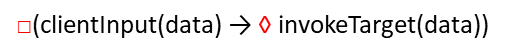
Generic :
Instantiated :

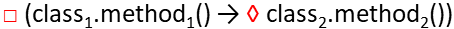
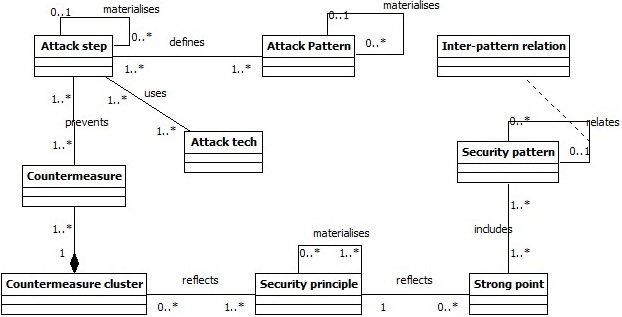
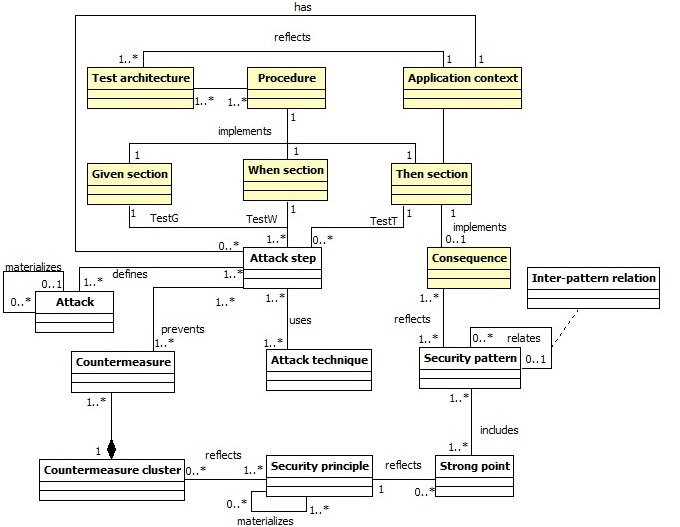
Classification Meta-model
- Objective : Classify patterns w.r.t Attack steps and techniques
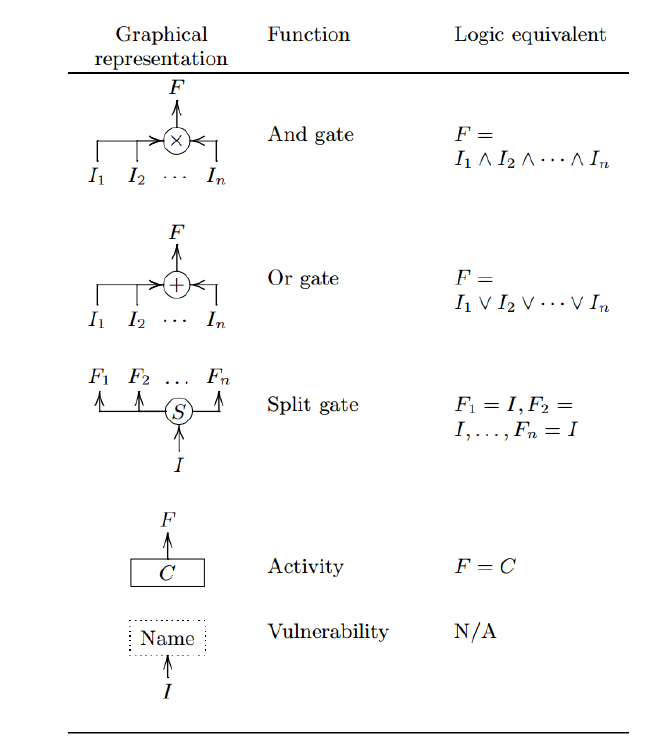
Attack Defense Trees
An ADTree can be expressed with :
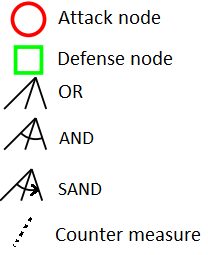
Opponent "o"
Proponent"p"
Algebra (ADTerms):
Graphical:
B.Kordy et al. 2014
ADTree generation
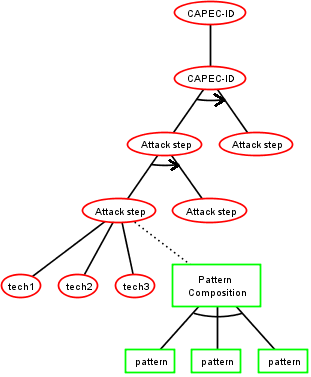
Meta-model
Method steps
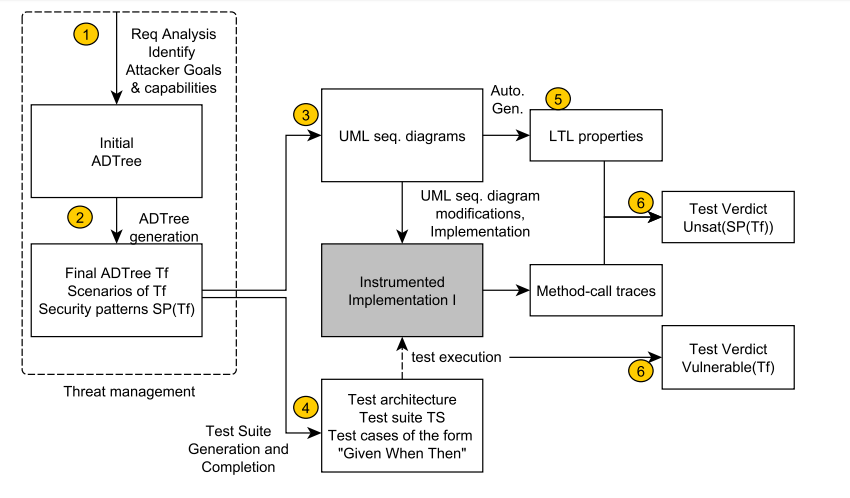
Step 1: Initial ADTree T
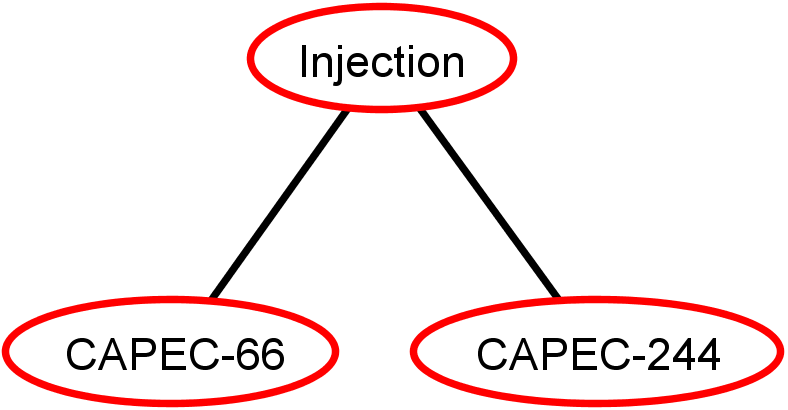
- CAPEC-66: SQL Injection
- CAPEC-244: XSS Targeting URI Placeholders
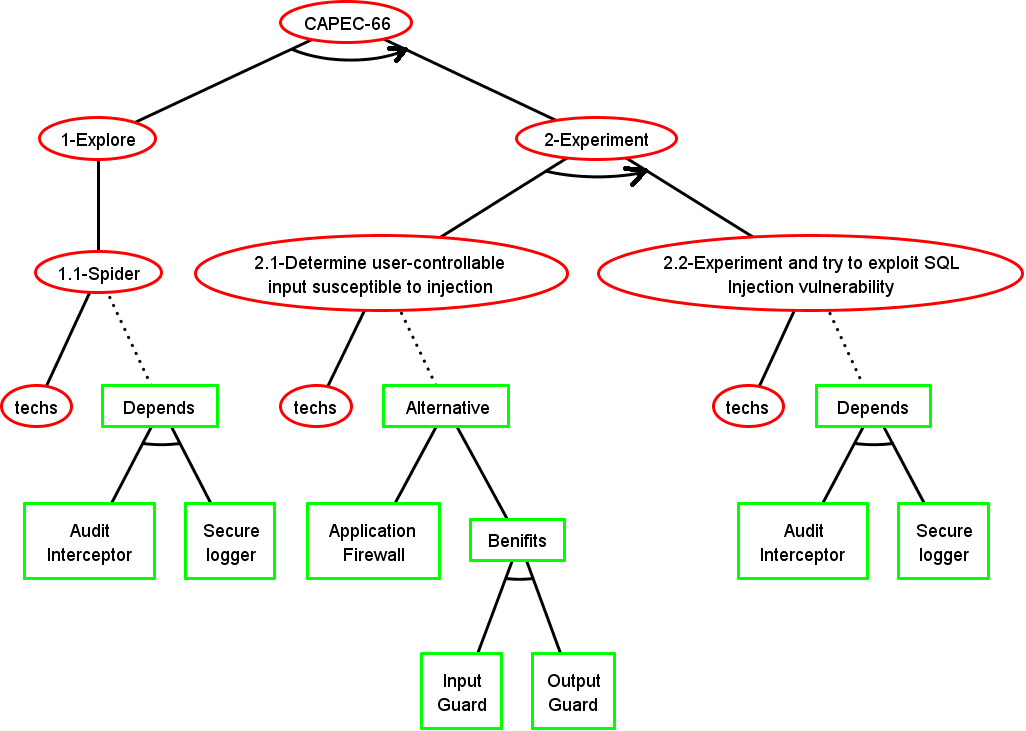
Step 2: ADTree Generation
The form of the tree depends on the Knowledge base
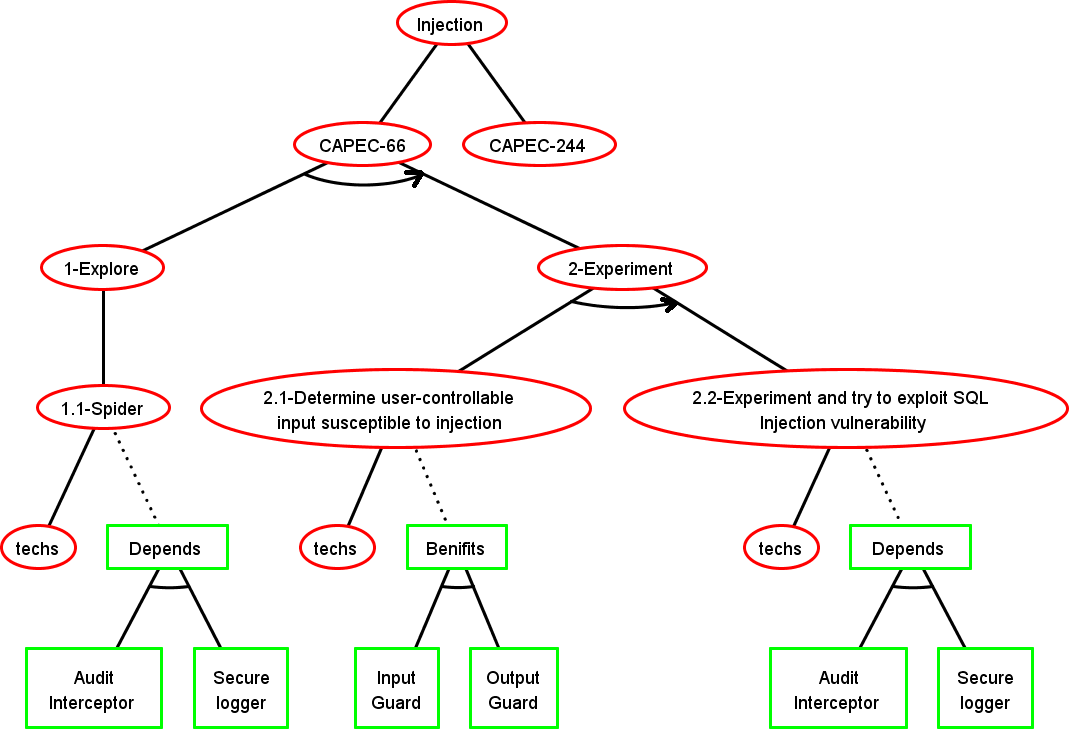
Step 2: Final ADTree
Basic Attack Defence Step (BADStep)
st
sp
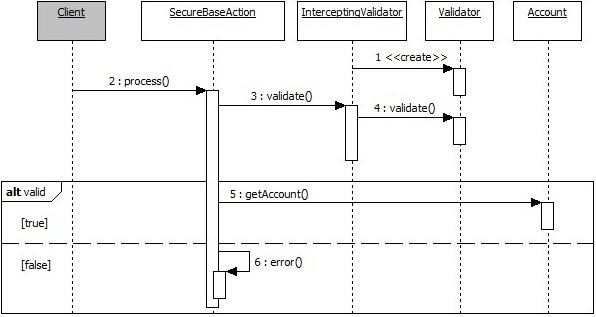
Given, When, Then (GWT) Test Case (TC)
Step 4: Test Suite Generation
Attack Scenario
Test Suite
Test Suite Execution
Final test verdicts
Step 3: Sequence Diagrams
Step 5: LTL Properties Generation
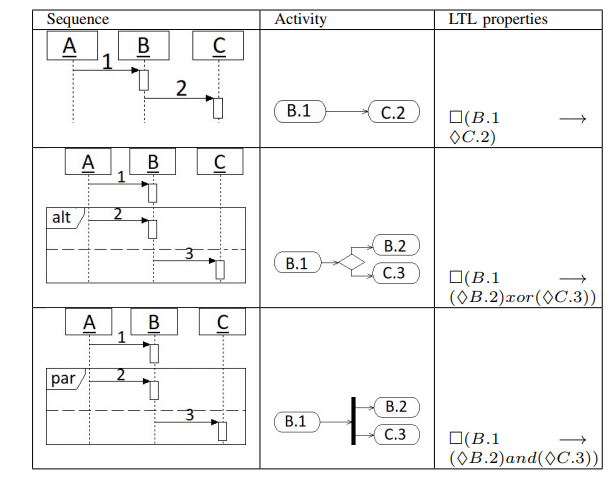
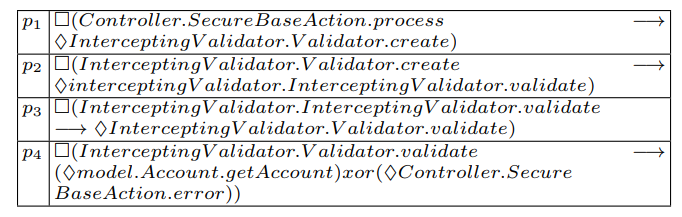
Step 5: LTL Properties Generation
Step 6: Test Verdicts
Traces
Declare2LTL
LTL Properties
Verdicts (Unsat(Sp))
Instrumented Application
Generated TCs
Verdicts (Fail/Pass(St))
TCs Execution
Conclusions
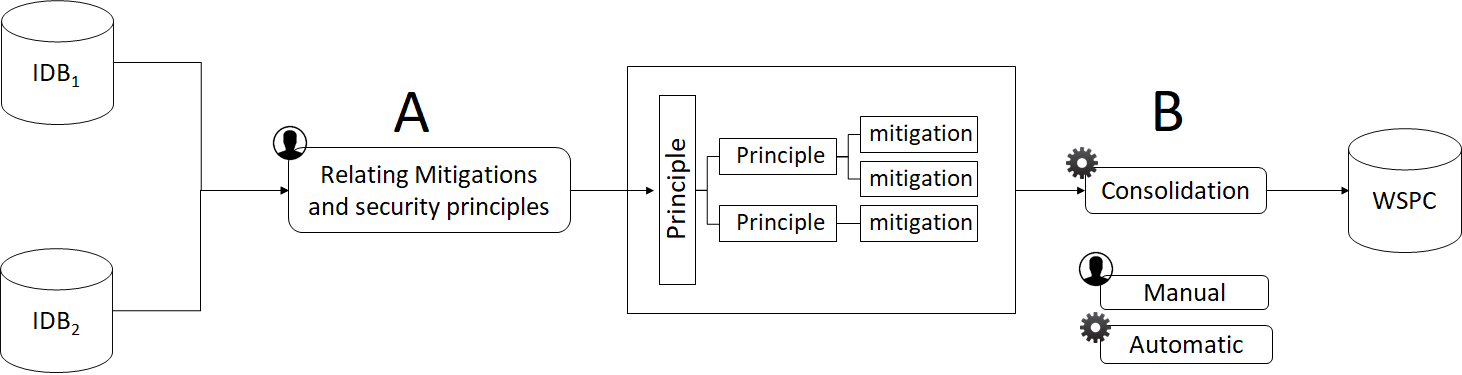
- A knowledge base associating weaknesses, attacks, security principles, ...
- Security test cases generation and execution
- Security patterns behavioral properties (LTL) generation and verification
- Test Verdicts about vulnerability to attacks and satisfiability of patterns properties
Work In Progress
- Address Inter patterns relationships
- Text mining instantiate patterns
Thank you for your attention

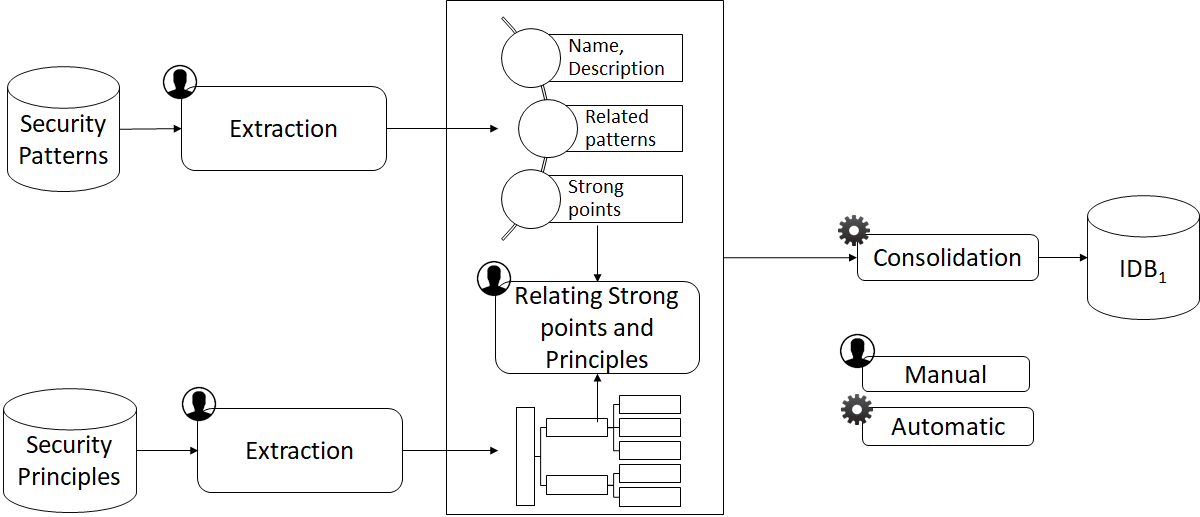
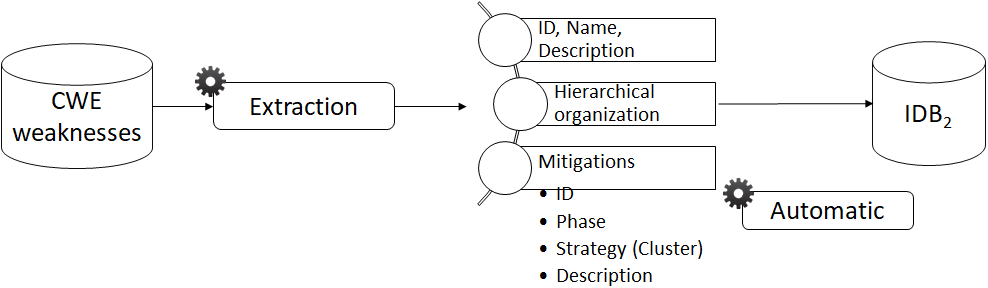
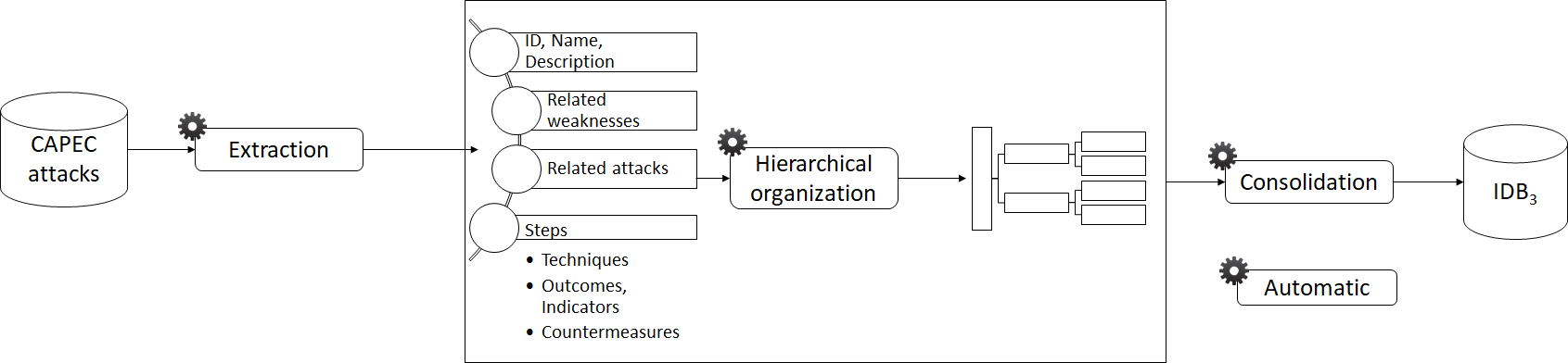
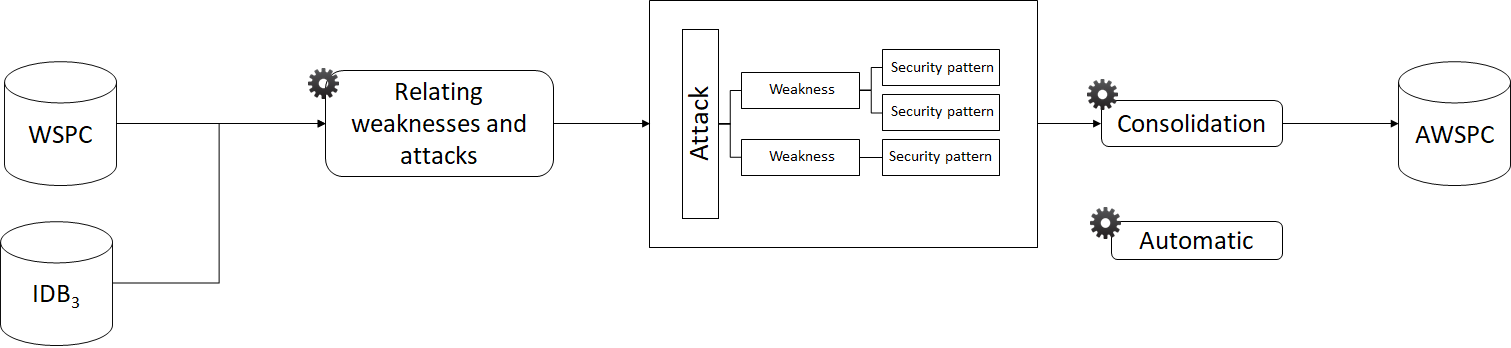
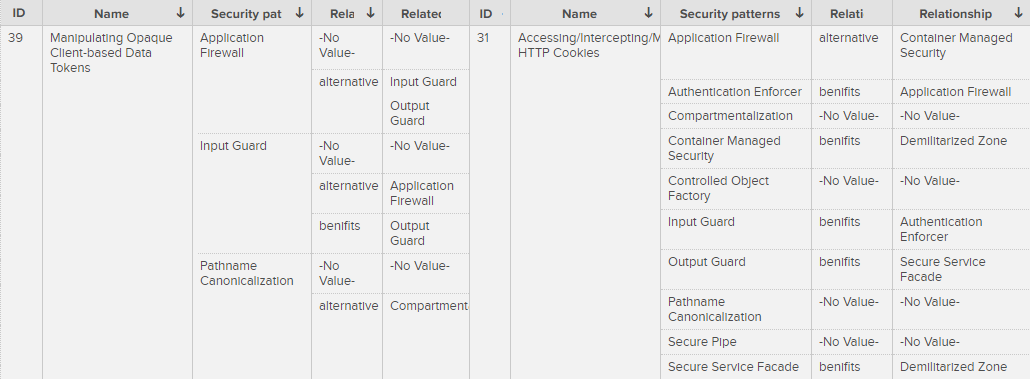
ADTree generation method 1
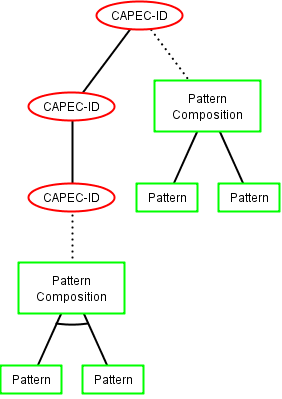
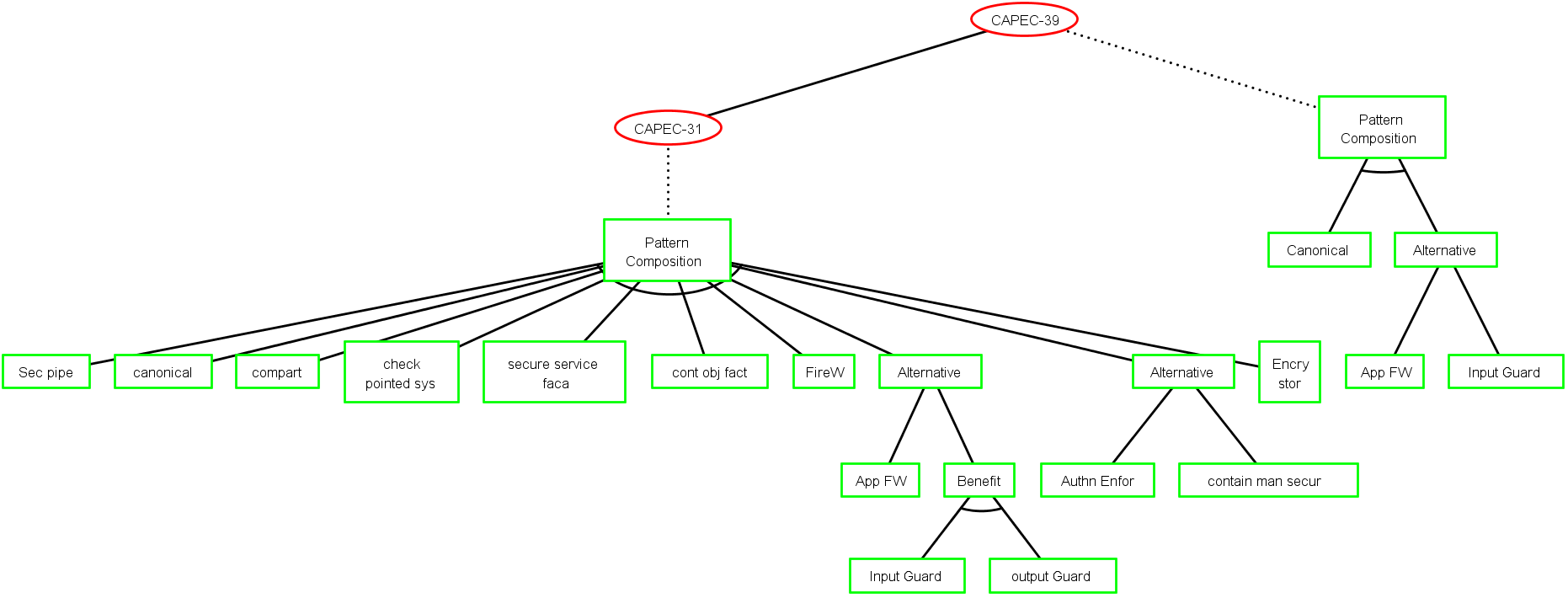
ADTree generation method 1
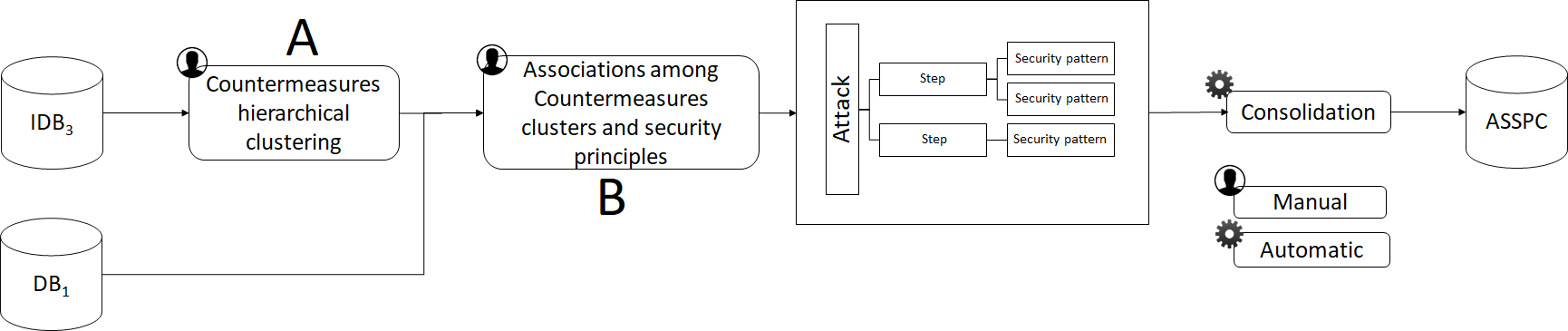
- POS Tagger and stop words definition
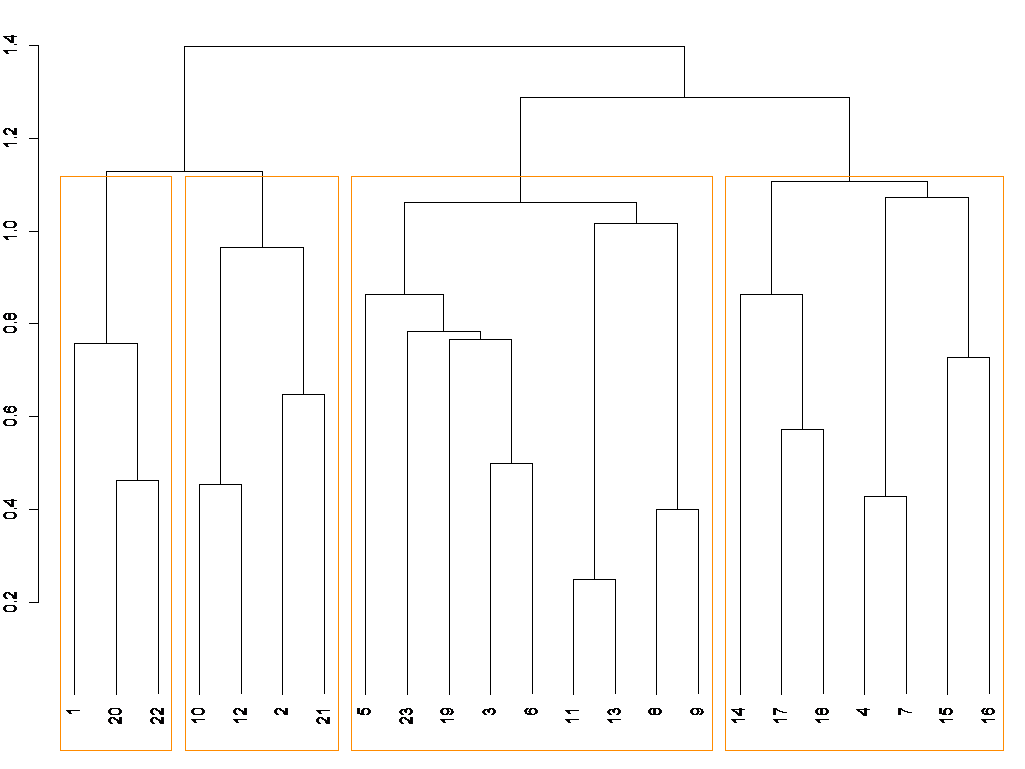
- Distance matrix with “Jaccard”
- Hierarchical clustering with “Ward”
ASSPC
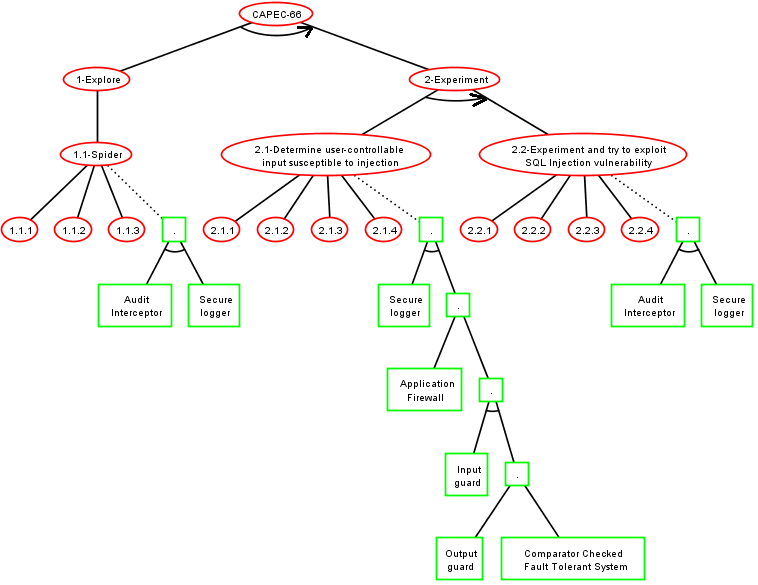
ADTree generation method 2
Step 3: Security pattern choice
Basic Attack Defence Step (BADStep)
Keep security pattern conjunctions
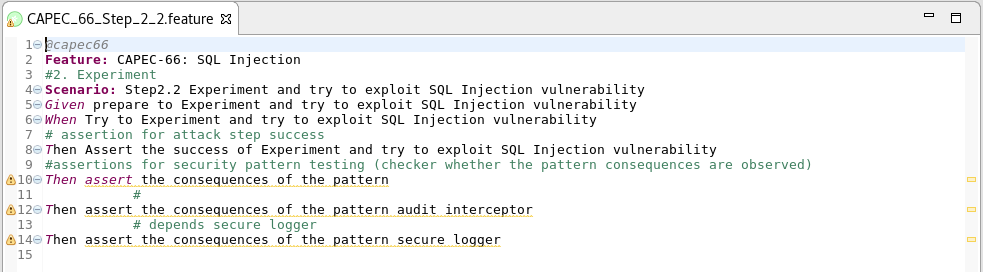
Step 5: Test suite generation
Test case (TC) example :
Step 5: Test suite generation
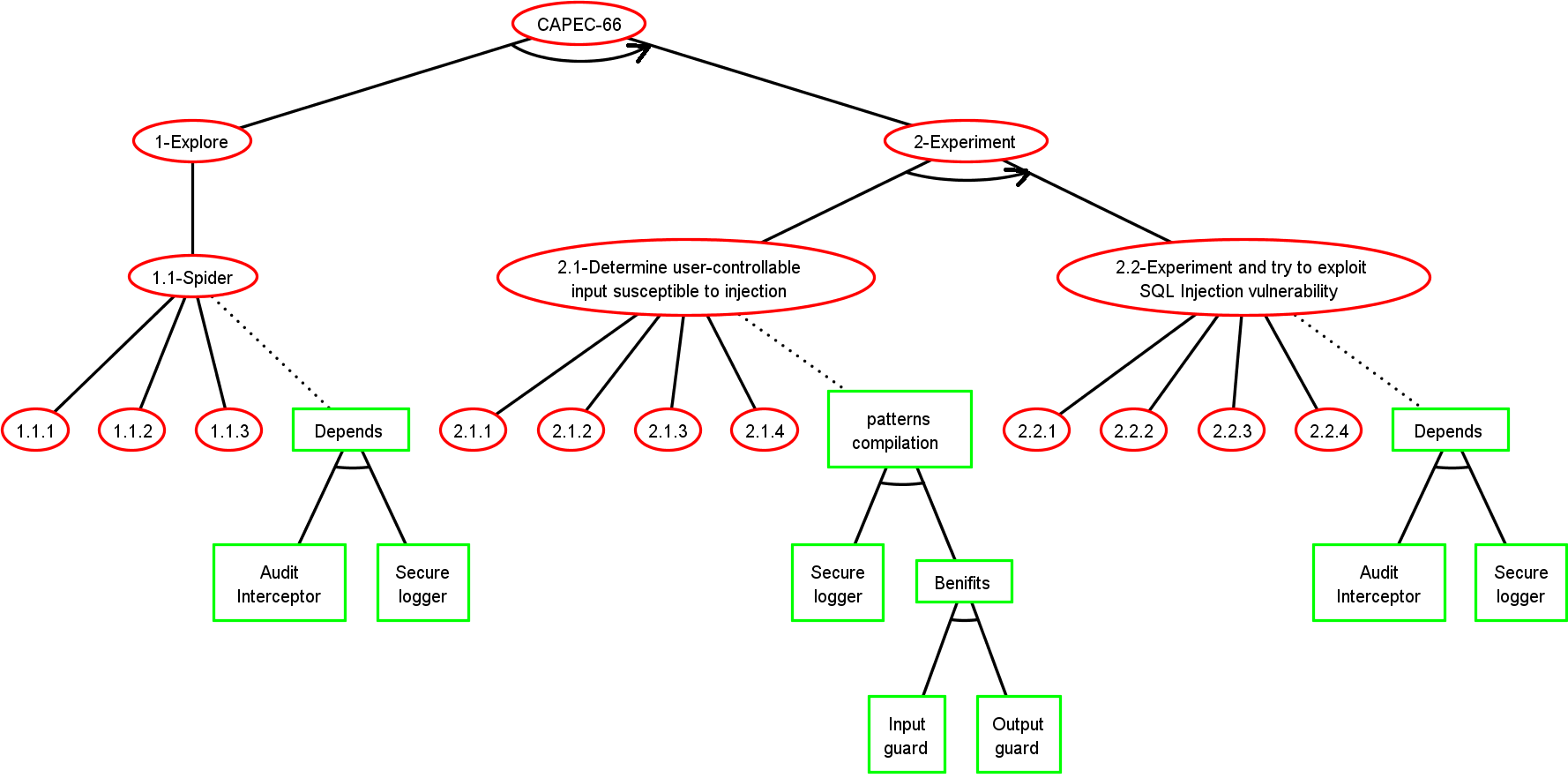
BADStep
Test scenario extraction from ADTree using ADTerms
Step 5: Test suite generation
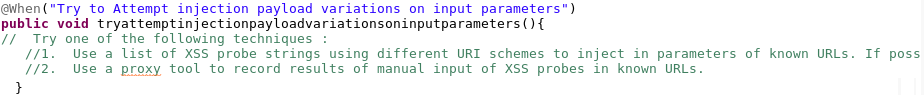
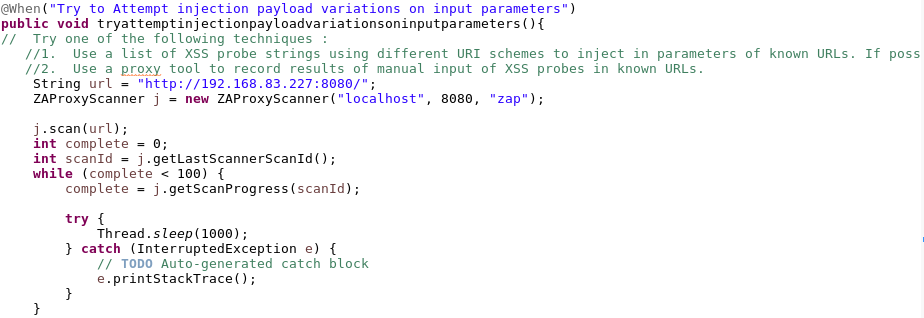
Step 6: Test case completion


Methodology Evaluation results
- C1: Comprehensibility
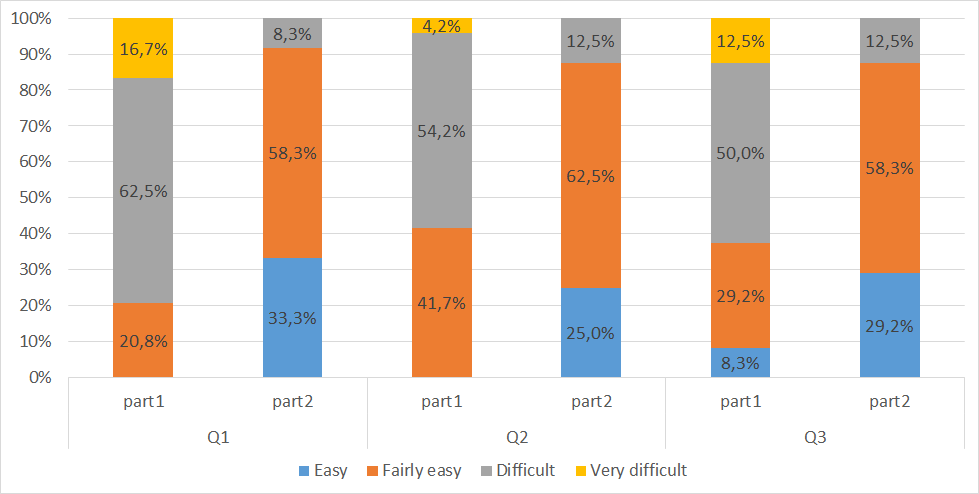
Methodology Evaluation results
- C2: Effectiveness
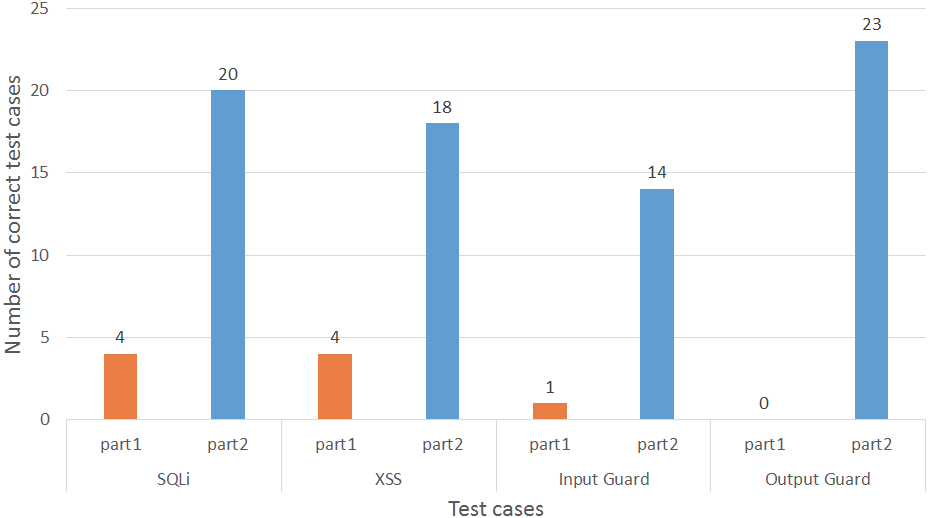
Methodology Evaluation results
- C2: Effectiveness
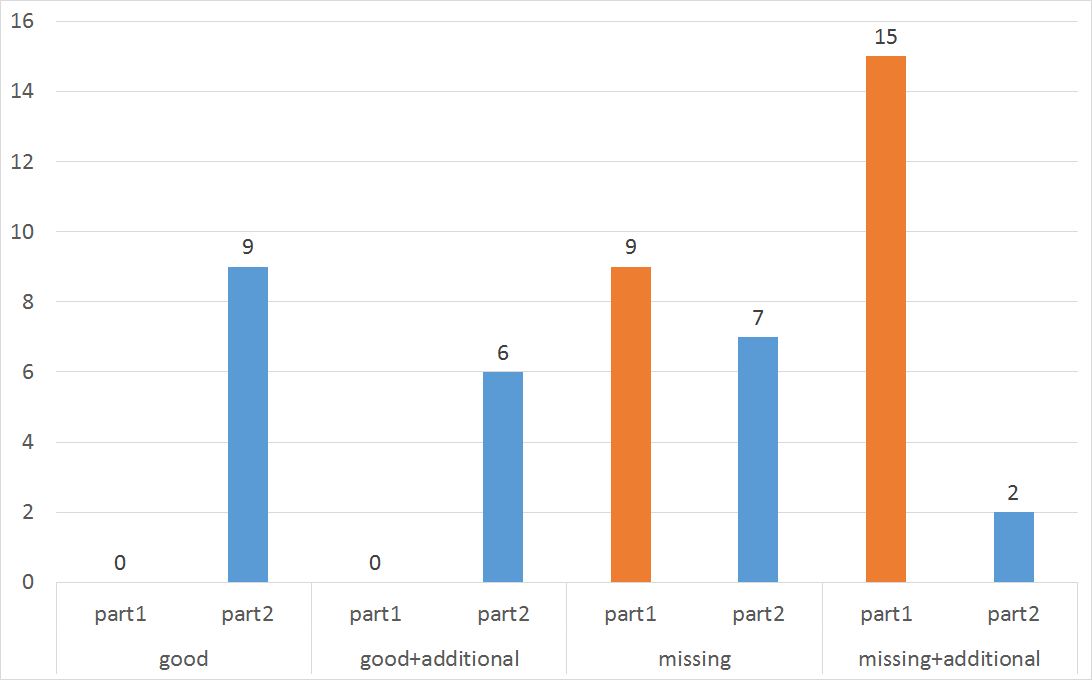
Methodology Evaluation results
- C3: Efficiency
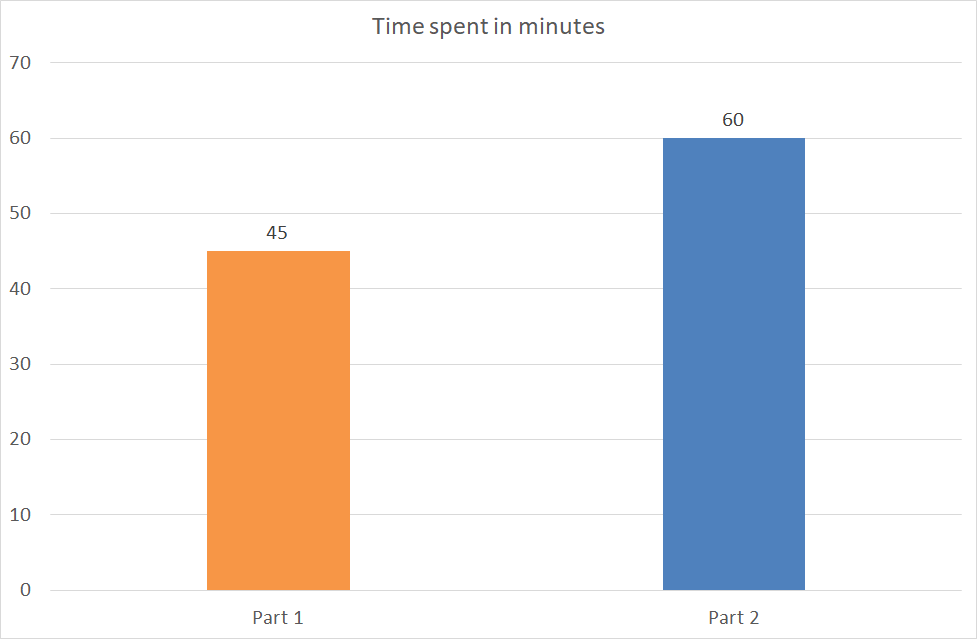
Copy of Soutenance
By Loukmen Regainia
Copy of Soutenance
- 218


