Applications of Cryptography in the Web
What we will cover
- Hashing (+salting)
- Enrypting (Symmetric & Asymmetric)
- Signing
- Comprehensive example
- General Advice
Hashing
- Hashing turns a string of data into some giberish.
- Also called 1-way encryption
- Used for storing passwords
hash("This is an arbitrary string") => aad348cc30efef7876a61e6214536f82bc3bd68d
Bad: store in plain text
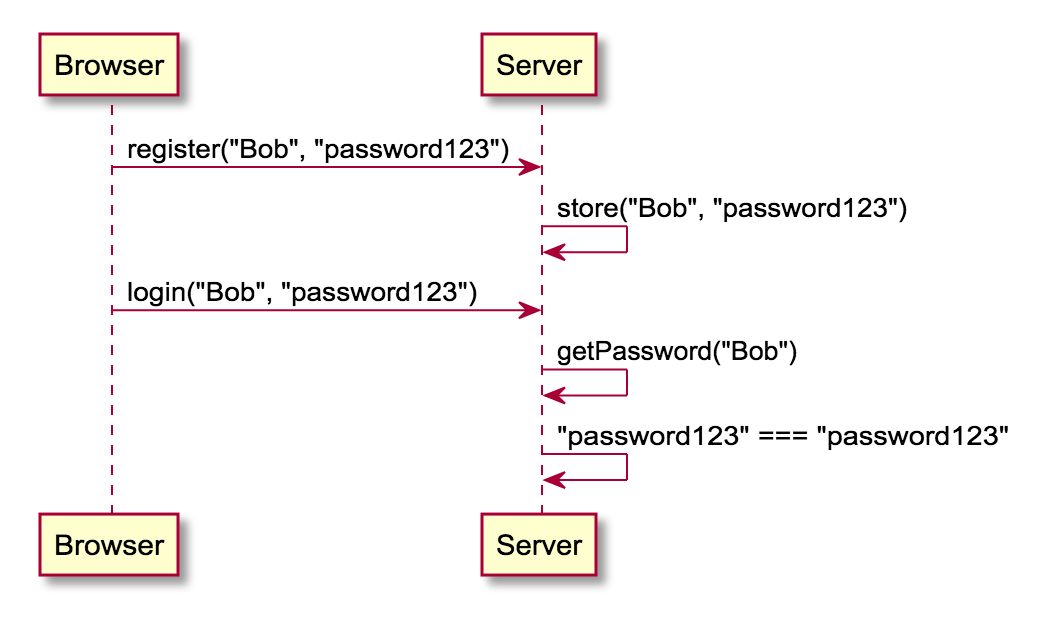
| Username | Password |
|---|---|
| Bob | password123 |
Better: store a hash
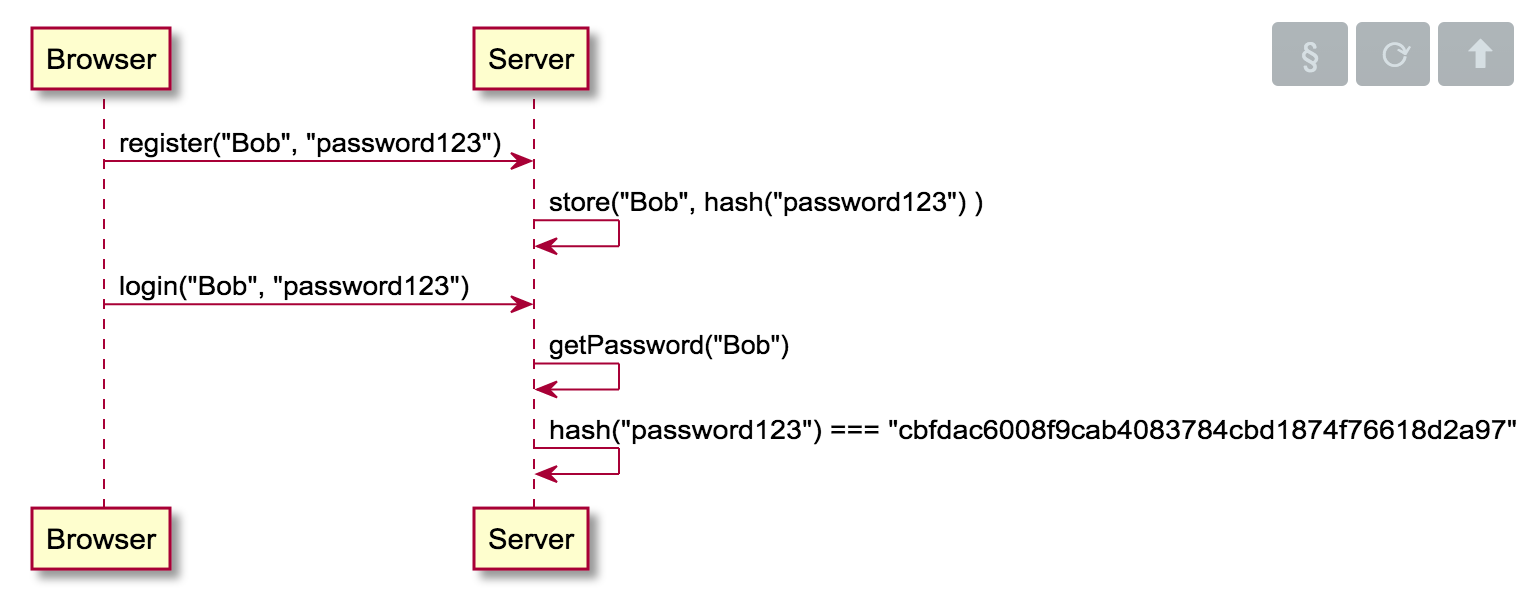
| Username | Password |
|---|---|
| Bob | cbfdac6008f9cab4083784cbd1874f76618d2a97 |
The problem with hashing...
| Username | Password |
|---|---|
| Bob | cbfdac6008f9cab4083784cbd1874f76618d2a97 |
| Alice | cbfdac6008f9cab4083784cbd1874f76618d2a97 |
| Joe | 96d712a79f47055aebcfed0a58092ef7d12da37f |
Best: Store a hash + salt
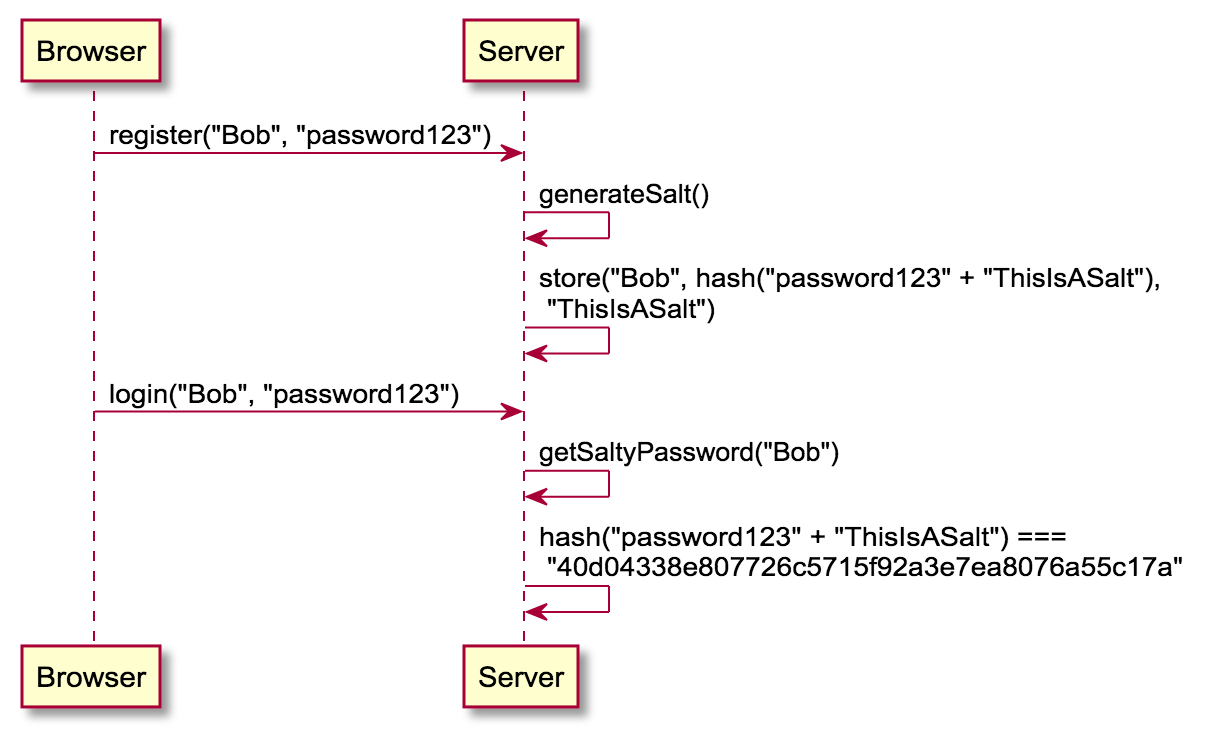
| Username | Password | Salt |
|---|---|---|
| Bob | 40d04338e807.... | ThisIsASalt |
Encrypting
- There are two kinds of encryption that we will use.
- Symmetric Encryption
- Asymmetric Encryption

What we can take for granted
function encrypt(message, key)
function decrypt(message, key)
- Let's not worry about the implementation of these functions right now.
- Encrypting and decrypting requires a "key", which is just some seemingly random string you keep in a text file.
Symmetric Encryption
- Both parties use the same key.
- This key is often referred to as the shared key or shared secret.
- Keep this key secret or it loses its value.

Problems with Symmetric
- Both parties need to have copies of the same key ahead of transmitting encrypted messages but how do they send the key to one another?
- Depending on your use case, it can be really cumbersome to manage which key to use for which peer. You definitely don't want to use the same key for each peer.
Asymmetric Encryption
- Now we have a public and a private key
- These keys are distinct but related.
- You can encrypt with one key and decrypt with the other.
- Analogy: Bob provides Alice with a lockbox only he can open so that she can send him a message.



Problems with Asymmetric
- It's really slow.
- The encrypted message is much larger.
Signing
- The data is not encrypted.
- Proves identity of originator*
- Ensures integrity of original data. If the data is modified, the signature will be invalidated.
*: Actually, it only proves the originator has a particular secret key.
How To Sign Something
There are two parts to a signed message.
- The raw, unencrypted message for all to see.
- The signature.
- To make the signature, start by hashing the message.
- Next, encrypt that hash using your private key.
Anyone with the associated public key can decrypt the encrypted hash and validate that it's correct by hashing the message and seeing if it matches.
Example
Logging in over SSL with username/password
Example: Signature Verification
- The browser downloads the site's SSL certificate.
- The browser knows the public keys of all of the trusted authorities that sites are likely to use, like Geotrust.
- The browser will verify the certificate's signature using the public key for the authority that supposedly signed it.



Example: SSL Handshake
- The browser verifies the SSL certificate
- The browser dynamically generates a new secret key. This is a symmetric key. There is no associated public key for this one.
- The browser needs to send this secret key to the server. It can't send the key in plain sight or it could be intercepted.


Example: SSL Handshake
- When the server sent its certificate, it also sent its public key.
- The browser encrypts its newly generated secret key with the server's public key.
- It can now send the encrypted secret key to the server.
- Now the server and browser can exchange messages encrypted with the same secret key.


Example: Password Verification
- The server receives a request with the user's password.
- The server gets the hashed password and the salt from its database.
- The server adds the salt to the provided password and hashes that concatenated string.
- The server hashes that string, using the same hashing algorithm it used when it stored the password's hash.
hash("password123"+"ThisIsASalt") === 40d04338e807726c5715f92a3e7ea8076a55c17a
General Advice
- Use tried and true libraries. Don't implement yourself.
- Salt your passwords.
- Avoid giving encrypted data to the client.
- Generally speaking, private keys should only be stored in one place.
Applications of Cryptography in the Web
By mustack
Applications of Cryptography in the Web
- 979



