Post-Quantum Cryptography Hardware
Neil Koul
Post-Quantum Crypto
Hardware
Performance
Post-Quantum Cryptography (PQC)
What is Post Quantum Cryptography?
The cryptography needed after quantum computers reach a certain degree of both feasibility and usability.
Why should we care about PQC?
- Undermine cryptographic algorithms
- RSA
- Shor's and Grover's algorithm
PQC Algorithms
- Public-key and Key-establishment Algorithms
- Classic McEilece, CRYSTALS-KYBER, NTRU, and SABER
- Digital Signature Algorithms
Current Hardware
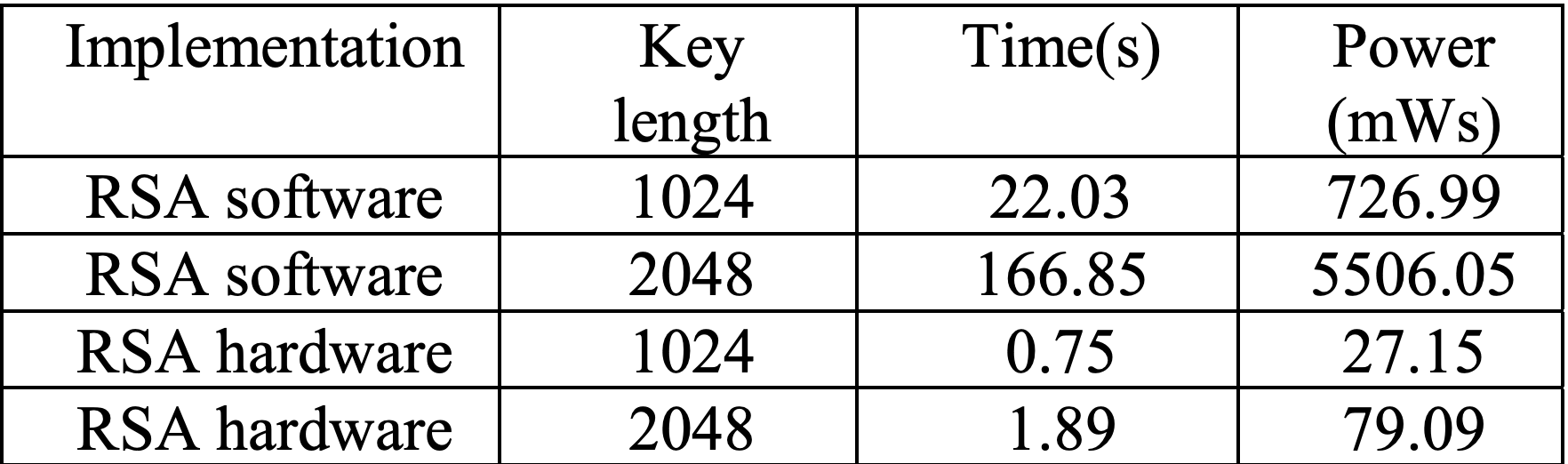
RSA
- Current Hardware
- Performance During Usage
- Performance to Break

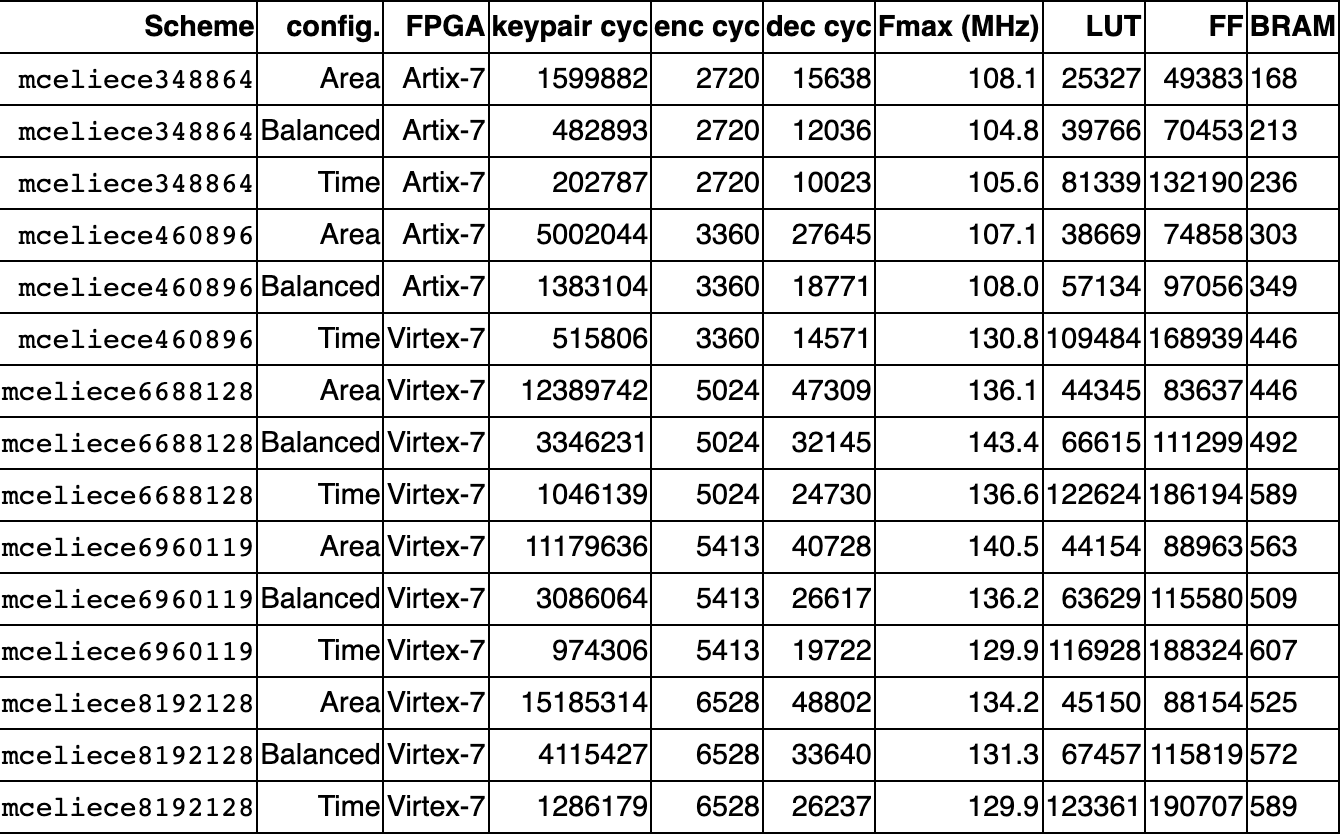
Classic McEliece
- Algorithm Information
- Lattice Based Cryptography
- Performance
Text
MCELIECE PERFORMANCE
CRYSTALS-KYBER
- Algorithm Information
- Hardware
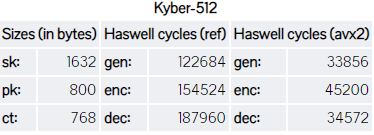
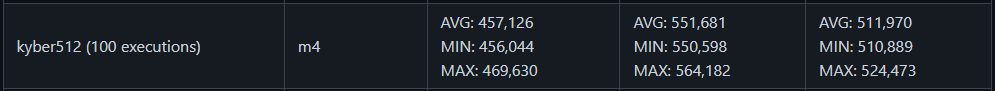
CRYSTALS-KYBER PERFORMANCE
NTRU
- Algorithm Information
- Encryption
- Performance
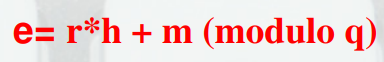
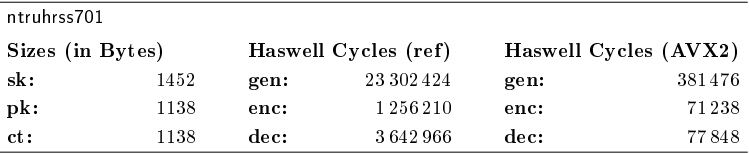
NTRU PERFORMANCE
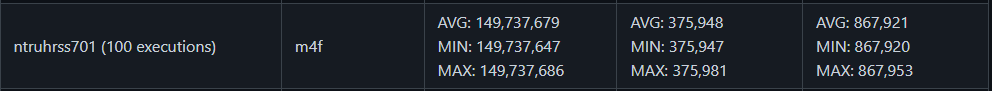
SABER
- Algorithm Information
- LWR and Mod scheme
- Performance
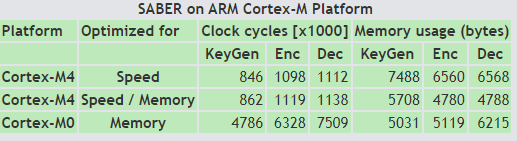
SABER PERFORMANCE

Conclusion
Algorithms
Out of the four PQC compared algorithms, it's found that SABER is the fastest algorithm. Since embedded devices will most likely have higher standards of security after quantum computers have become fully realized, these algorithms will continue to develop
Sources
[1] T. M. Fernández-Caramès and P. Fraga-Lamas, “Towards Post-Quantum Blockchain: A Review on Blockchain Cryptography Resistant to Quantum Computing Attacks,” IEEE Access, vol. 8, pp. 21091–21116, 2020, doi: 10.1109/ACCESS.2020.2968985.
[2] J.-P. D’Anvers et al., “SABER: LWR-based KEM.” https://www.esat.kuleuven.be/cosic/pqcrypto/saber/performance.html (accessed Aug. 08, 2021).
[3] NIST, “Round 3 Submissions - Post-Quantum Cryptography | CSRC | CSRC,” CSRC | NIST, Jan. 03, 2017. https://csrc.nist.gov/Projects/post-quantum-cryptography/round-3-submissions (accessed Aug. 04, 2021).
[4] L. Chen et al., “Report on Post-Quantum Cryptography,” National Institute of Standards and Technology, NIST IR 8105, Apr. 2016. doi: 10.6028/NIST.IR.8105.
[5] C. Chen et al., “NTRU.” https://ntru.org/index.shtml (accessed Aug. 08, 2021).
[6] P. Schwabe, “Kyber.” https://pq-crystals.org/kyber/index.shtml (accessed Aug. 08, 2021).
[7] M. Andrzejczak, F. Farahmand, and K. Gaj, “Full hardware implementation of the Post-Quantum Public-Key Cryptography Scheme Round5,” in 2019 International Conference on ReConFigurable Computing and FPGAs (ReConFig), Dec. 2019, pp. 1–2. doi: 10.1109/ReConFig48160.2019.8994765.
Sources Continued
[8] T. M. Fernández-Caramés, “From Pre-Quantum to Post-Quantum IoT Security: A Survey on Quantum-Resistant Cryptosystems for the Internet of Things,” IEEE Internet of Things Journal, vol. 7, no. 7, pp. 6457–6480, Jul. 2020, doi: 10.1109/JIOT.2019.2958788.
[9] M. Giles, “Explainer: What is post-quantum cryptography?,” MIT Technology Review. https://www.technologyreview.com/2019/07/12/134211/explainer-what-is-post-quantum-cryptography/ (accessed Aug. 03, 2021).
[10] D. Zoni, A. Galimberti, and W. Fornaciari, “Efficient and Scalable FPGA-Oriented Design of QC-LDPC Bit-Flipping Decoders for Post-Quantum Cryptography,” IEEE Access, vol. 8, pp. 163419–163433, 2020, doi: 10.1109/ACCESS.2020.3020262.
[11] Abdullah Said Alkalbani, T. Mantoro, and A. O. M. Tap, “Comparison between RSA hardware and software implementation for WSNs security schemes,” in Proceeding of the 3rd International Conference on Information and Communication Technology for the Moslem World (ICT4M) 2010, Jakarta, Indonesia, Dec. 2010, pp. E84–E89. doi: 10.1109/ICT4M.2010.5971920.
[12] M. R. Albrecht et al., “Classic McEliece: Intro.” https://classic.mceliece.org/index.html (accessed Aug. 08, 2021).
[13] C. Chen et al., “Algorithm Speci cations And Supporting Documentation,” p. 41.
Further Reading
Digital signature algorithms:
https://csrc.nist.gov/Projects/post-quantum-cryptography/round-3-submissions
quantumCryptoProject
By Neil Koul
quantumCryptoProject
- 114



