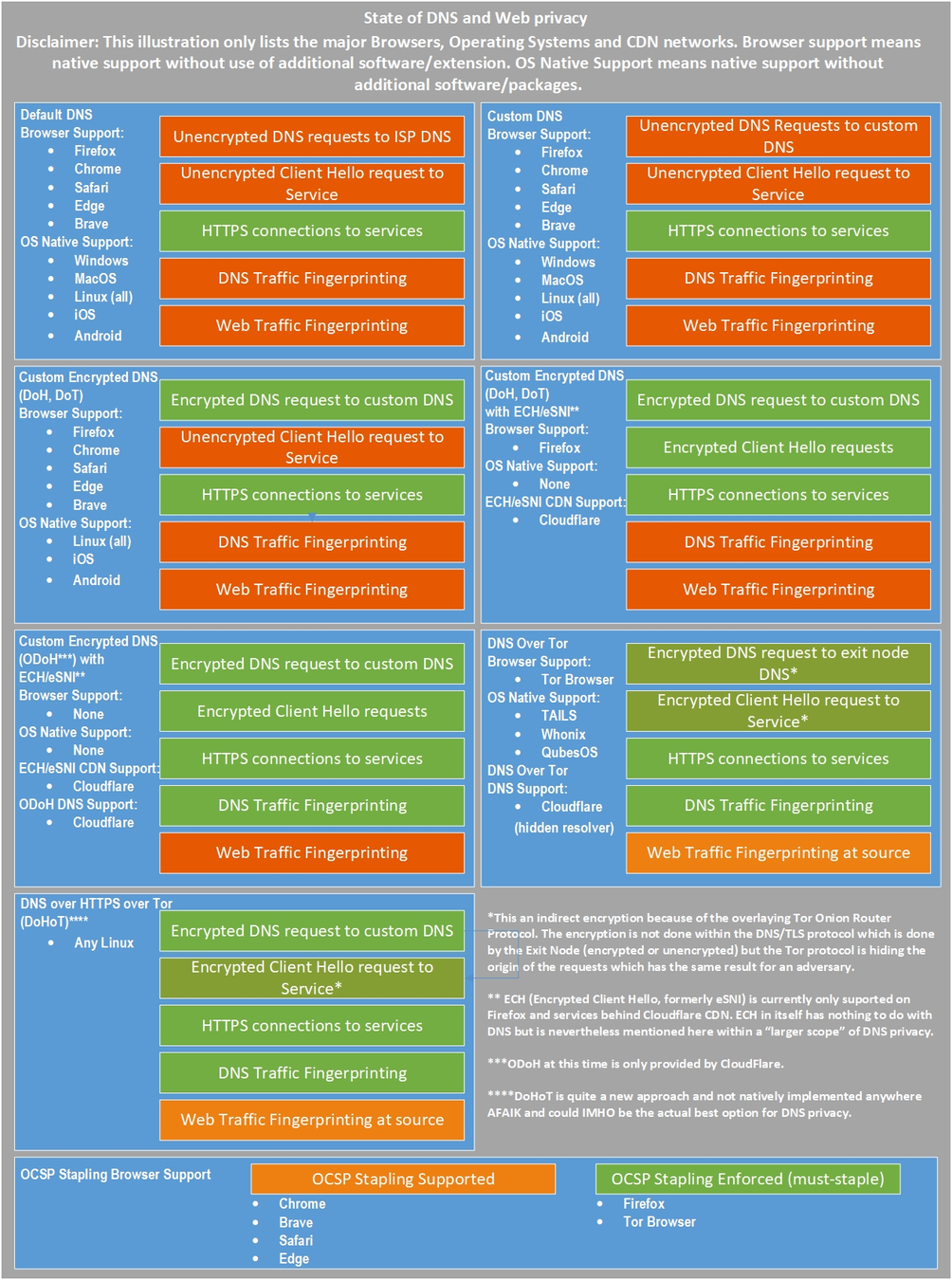
DIGITAL SECURITY
WITH RACCOONS
WITH RACCOONS
DIGITAL SECURITY
PROGRAMME
PROGRAMME
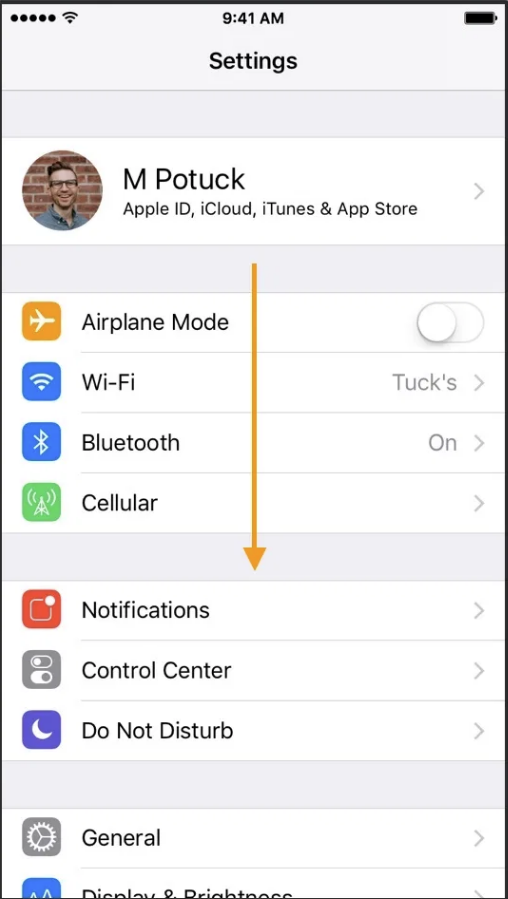
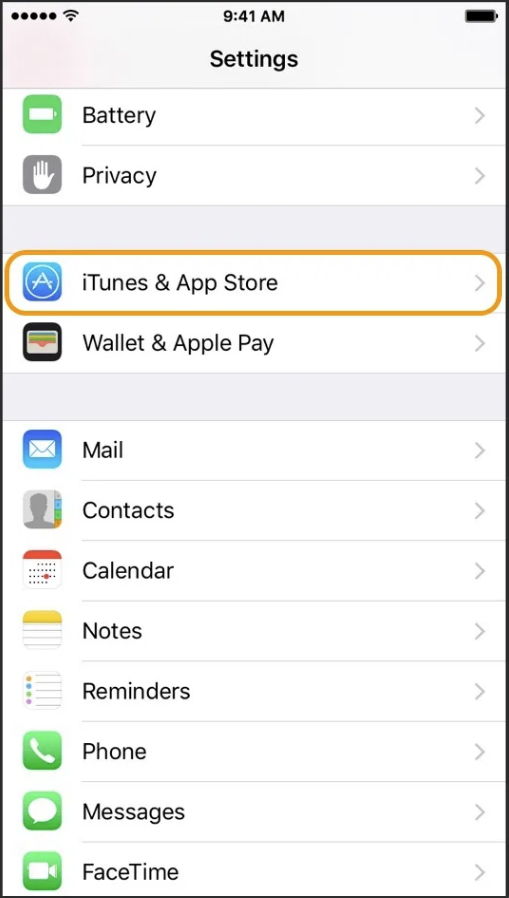
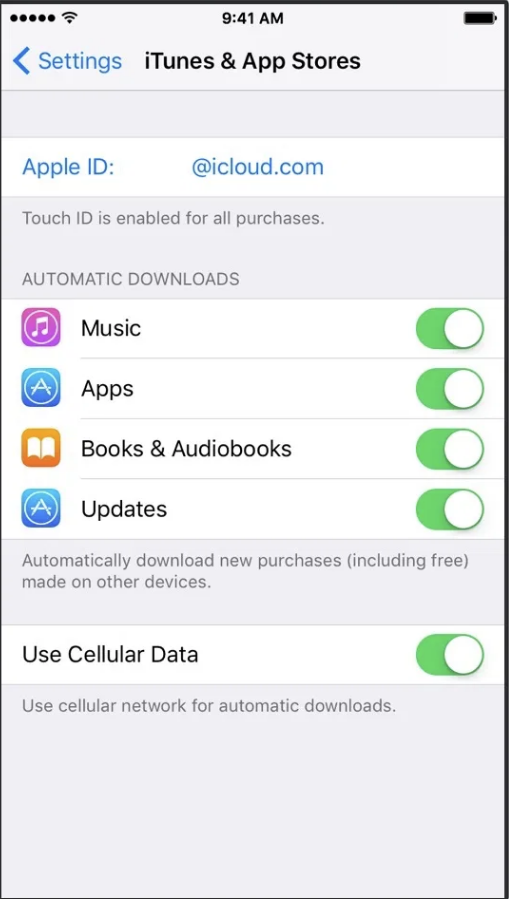
Confirm device setup
Check in
1
2
3
FIDO U2F Keys
4
Good practices for you

CONFIRM SETUP
CONFIRM SETUP
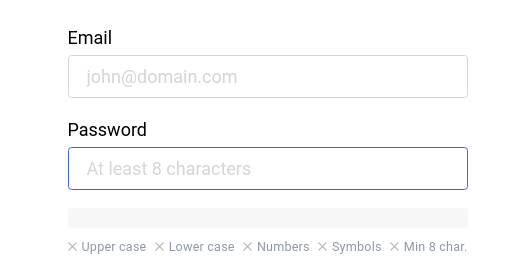
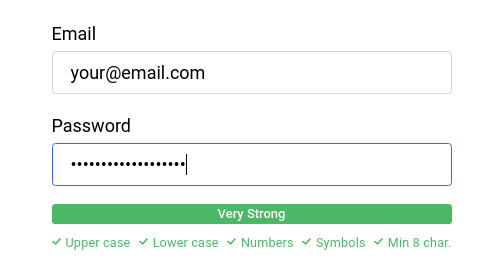
Password Manager
Device Password
1
2
3
Accounts Settings

CHECK IN,
RACCOSMONAUTS!
CHECK IN, RACCOSMONAUTS!
AGENDA

TODAY
NEXT
smartphones
computers
password mgmt
security
apps
storage
photos
security
storage
apps
communication
AGENDA

PREVIOUS
TODAY
smartphones
computers
password mgmt
security
apps
storage
photos
security
storage
apps
communication
WHAT IS (YOUR)
DIGITAL SECURITY?
WHAT IS (YOUR)
DIGITAL SECURITY?
YOUR BIG STROKES HAVE A BIG IMPACT
YOUR BIG
STROKES
HAVE A
BIG IMPACT
BUT YOU NEED MANY SMALL STROKES TO COVER ALL THE DETAILS
BUT YOU NEED MANY SMALL STROKES TO COVER ALL THE DETAILS
ONLY YOU CAN DECIDE WHAT IS DETAILED ENOUGH FOR YOU
WHEN IS IT DONE?
ONLY YOU CAN DECIDE WHAT IS DETAILED ENOUGH FOR YOU
WHEN IS IT DONE?
HOW TO PREPARE
YOUR SIM CARD
2
SECURE
PIN CODE
1
PURCHASE
ANONYMOUS
GROUP BUY
[instructions]
PRE PAID


AUTHENTICATION
you... who are you?
you ... and only you
you ... are unique!

4321
p@$$w!rD
FastBulkCat
local
remote server
PIN
vs
PASSWORD
vs
PASSPHRASE
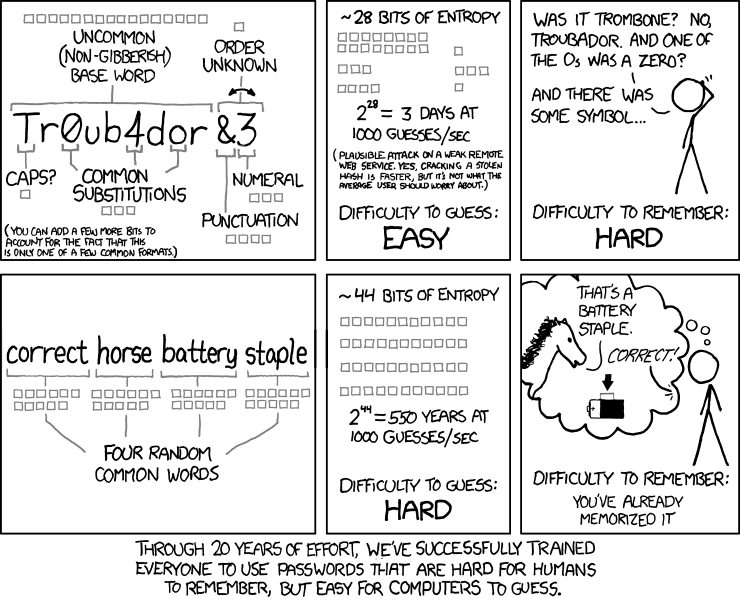
HOW TO LOCK YOUR
SMART DEVICES?
1
USE PINS
NOT PATTERNS

2
TURN OFF
BIOMETRICS
NO REFERENCES
UNIQUE
NO PATTERNS
FACE UNLOCK
FINGERPRINT
3
AUTOLOCK & UNLOCK
SHORT TIMEOUT
MIND THE CCTV
HOW TO LOCK YOUR
SMART DEVICES?
4
LOCK SCREEN NOTIFICATIONS

5
EMERGENCY
DETAILS
REMOVE or
HIDE CONTENT
EMERGENCY CONTACT
YOUR INFO
5
EMERGENCY
DETAILS
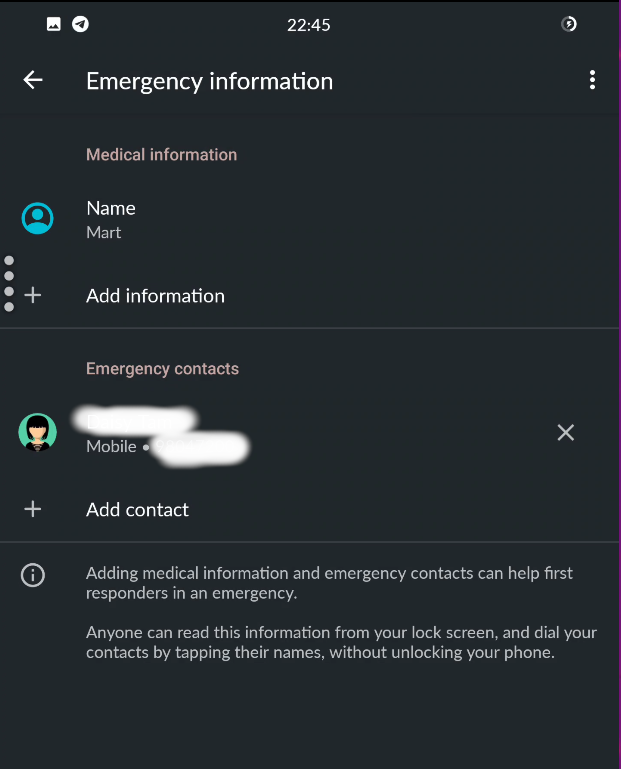

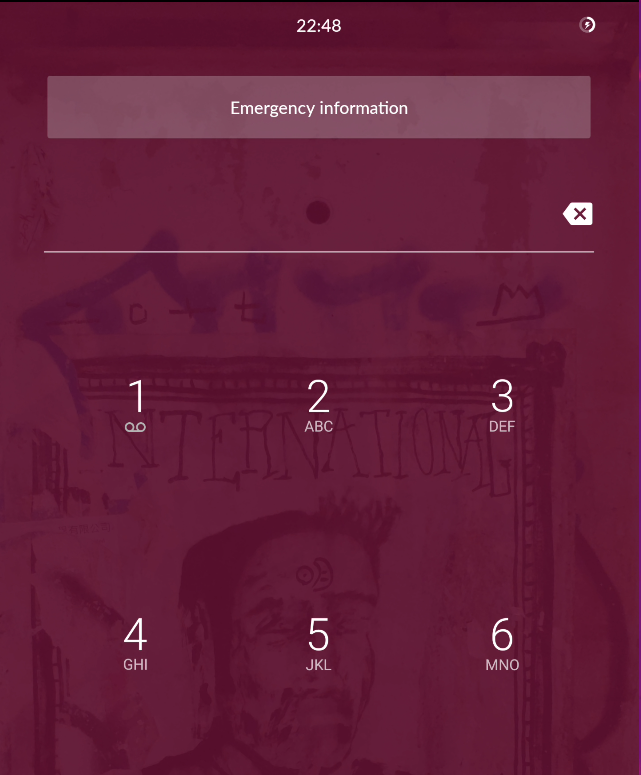
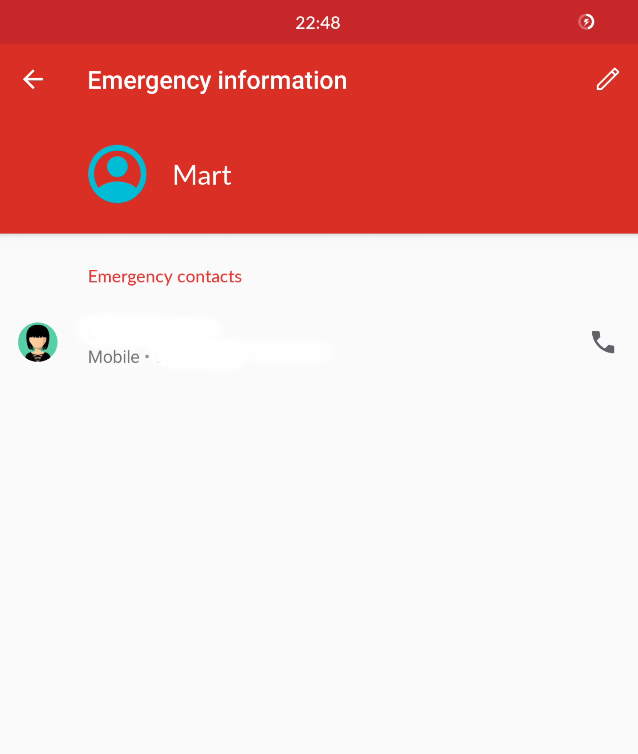
setup
lock screen
emergency
contacts


see next slide
EMERGENCY
DETAILS
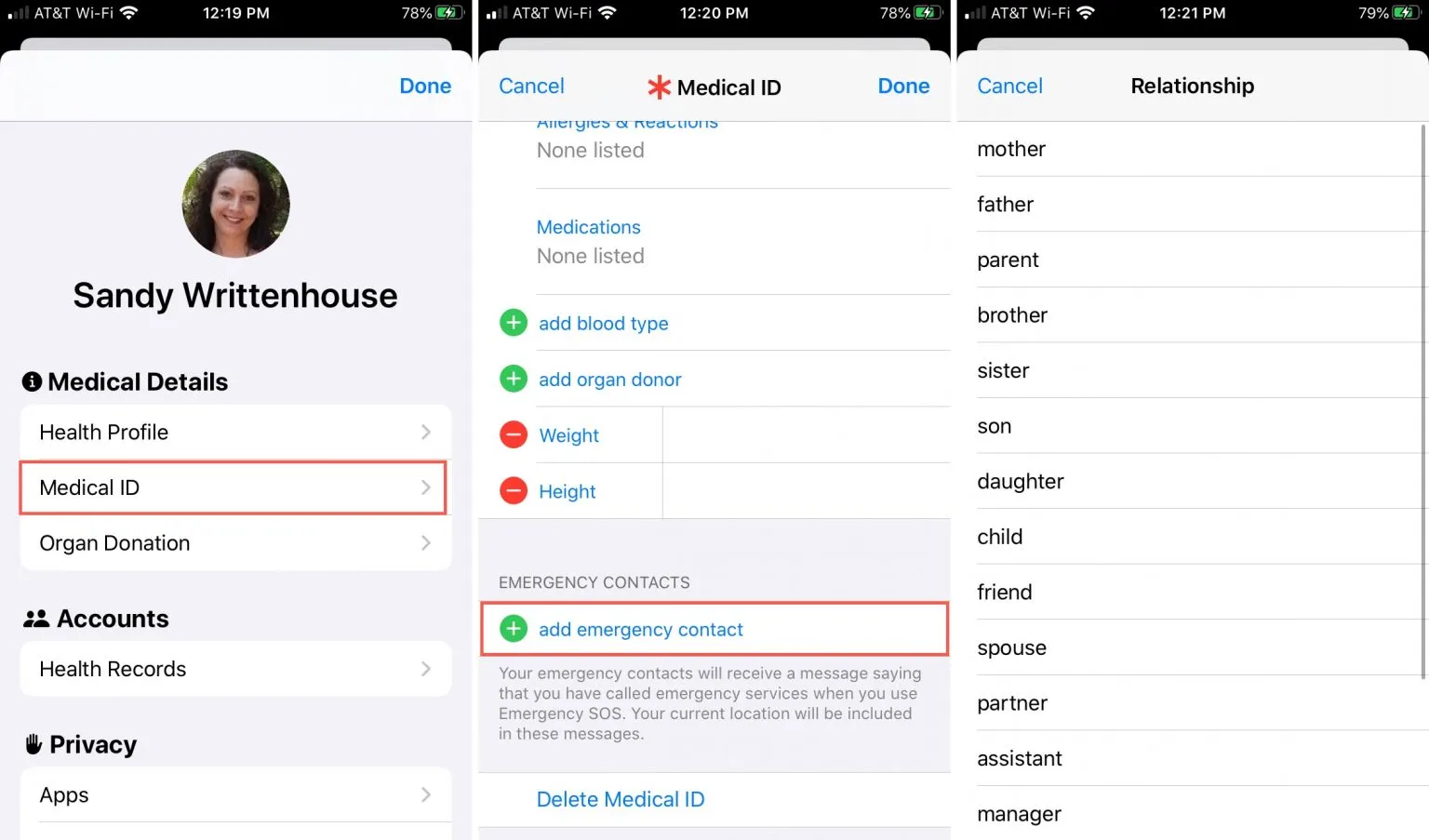
5

HOW TO SAFELY
INSTALL APPS?
1
ONLY USE OFFICIAL APP STORE
2
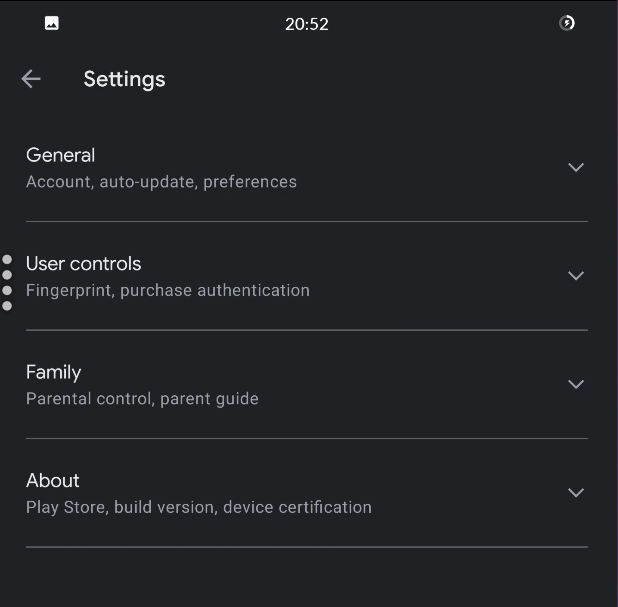
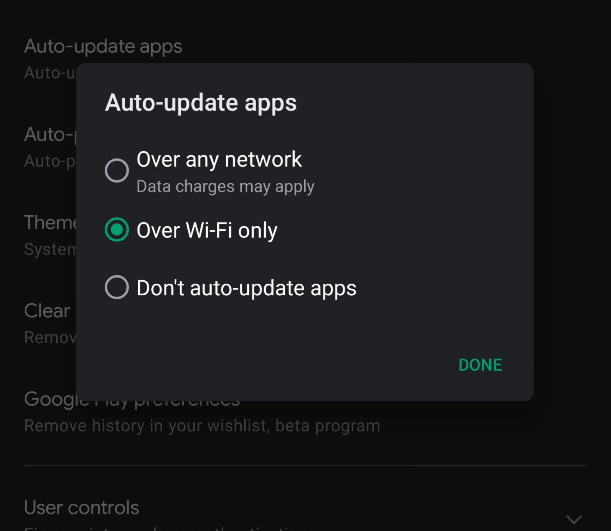
AUTO UPDATE
ALL APPS
TRUSTED SOURCE
UPDATES
NO MALWARE
FACE UNLOCK
SECURITY FIXES

1
DISABLE UNKNOWN APPS


2

3
AUTO UPDATE

PLAY PROTECT


2
3
AUTO UPDATE
APP PROTECT

1
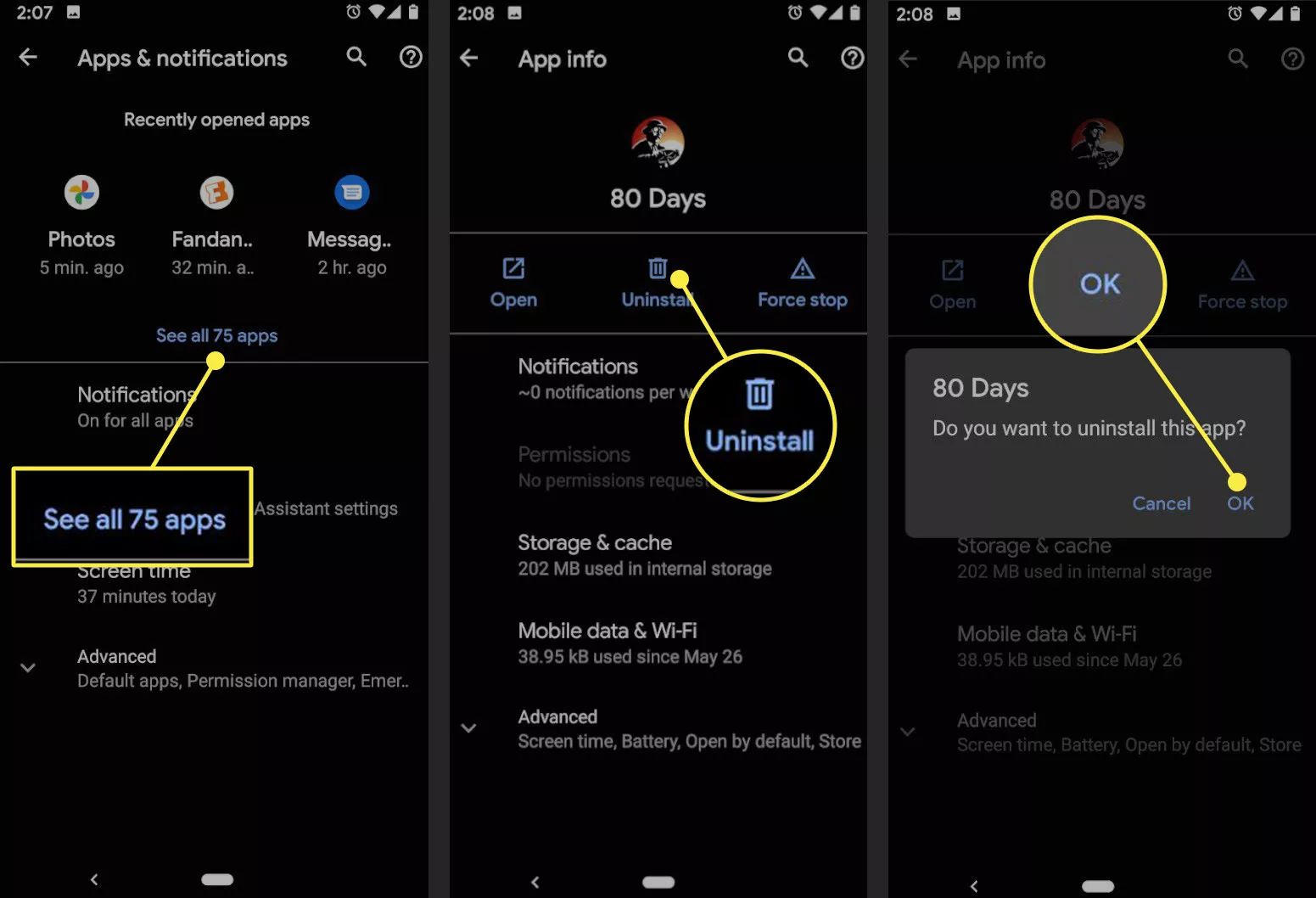
DISABLE UNKNOWN APPS


unless your iDevice is jailbroken
4
UNINSTALL APPS YOU DO NOT REALLY NEED




HOW TO SAFELY
USE APPS?
1
APP PERMISSIONS
2
CREATE APP DECOYS
GRANULAR PERMISSIONS
HIDE CLONES
MULTIPLE COPIES

REVIEW & LIMIT
ACCESS
1
REVIEW APP PERMISSIONS
Settings > Apps > ⚙ icon > App permissions.


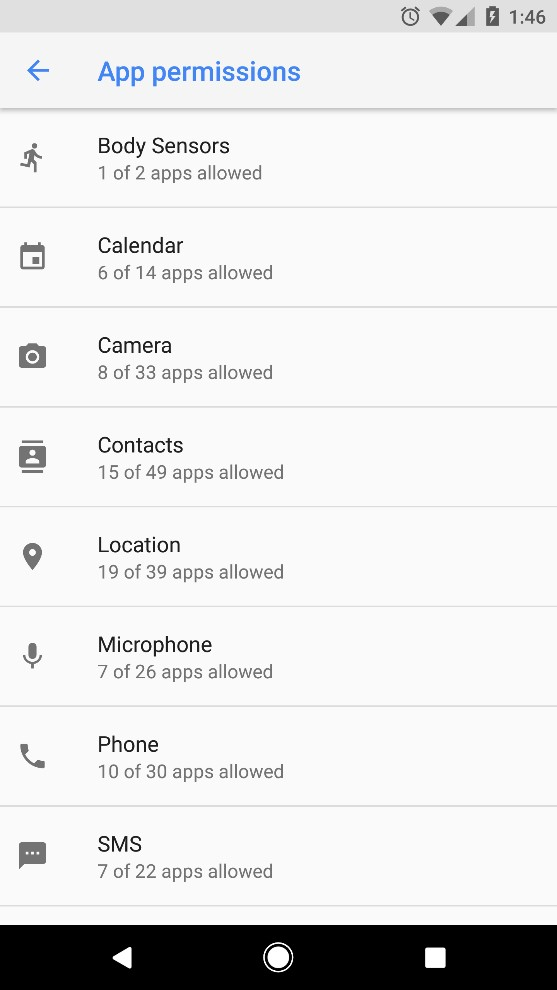
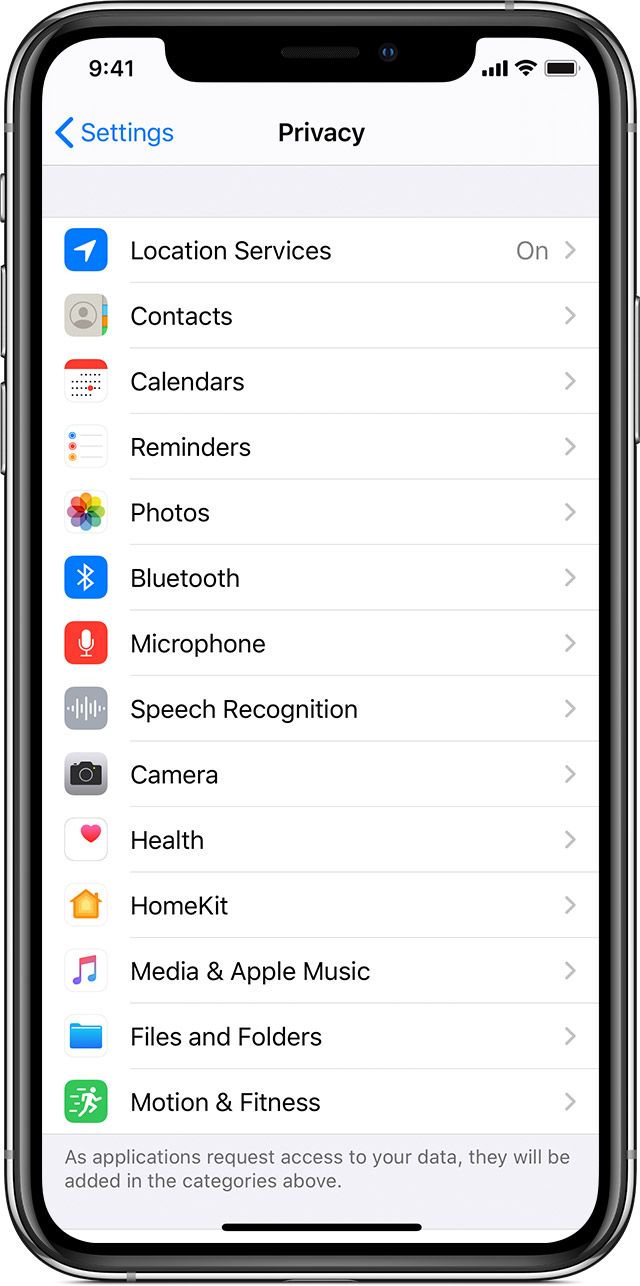
Settings > Privacy
camera
microphone
location
[special attention]
DECOY APPS

2
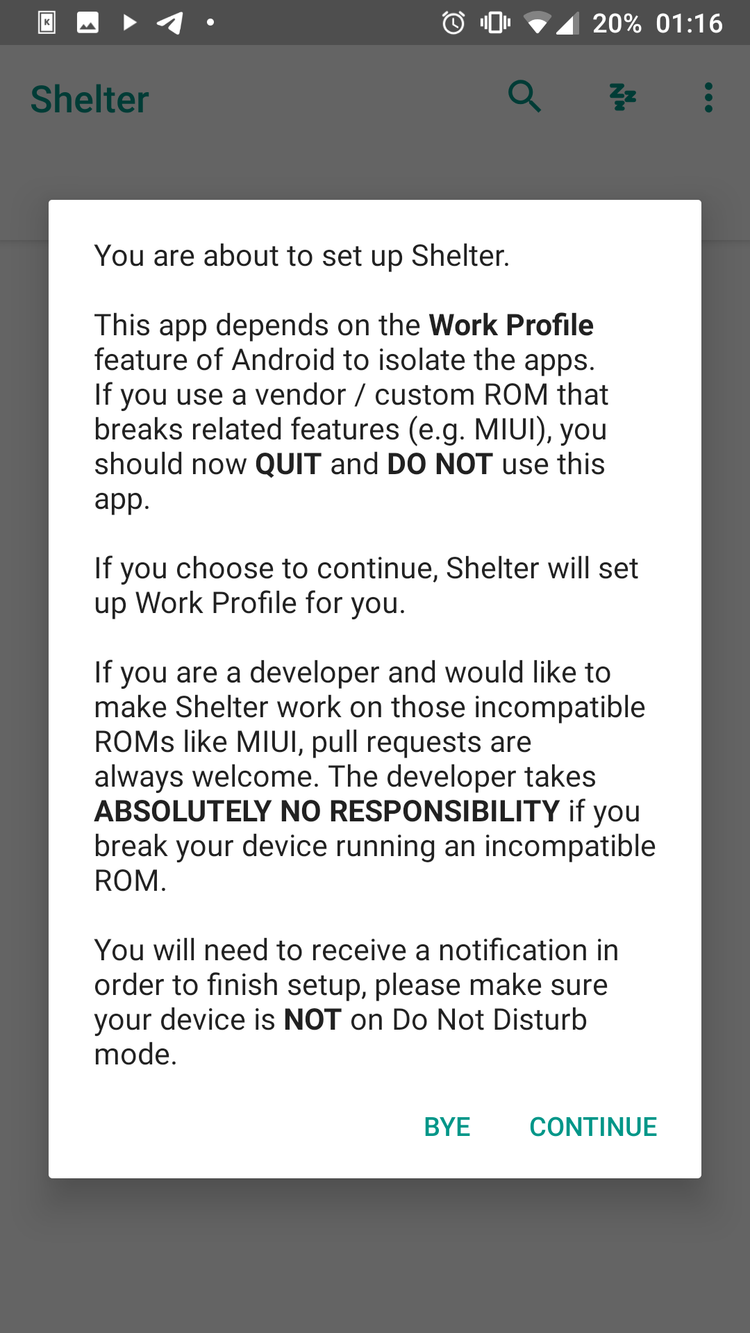
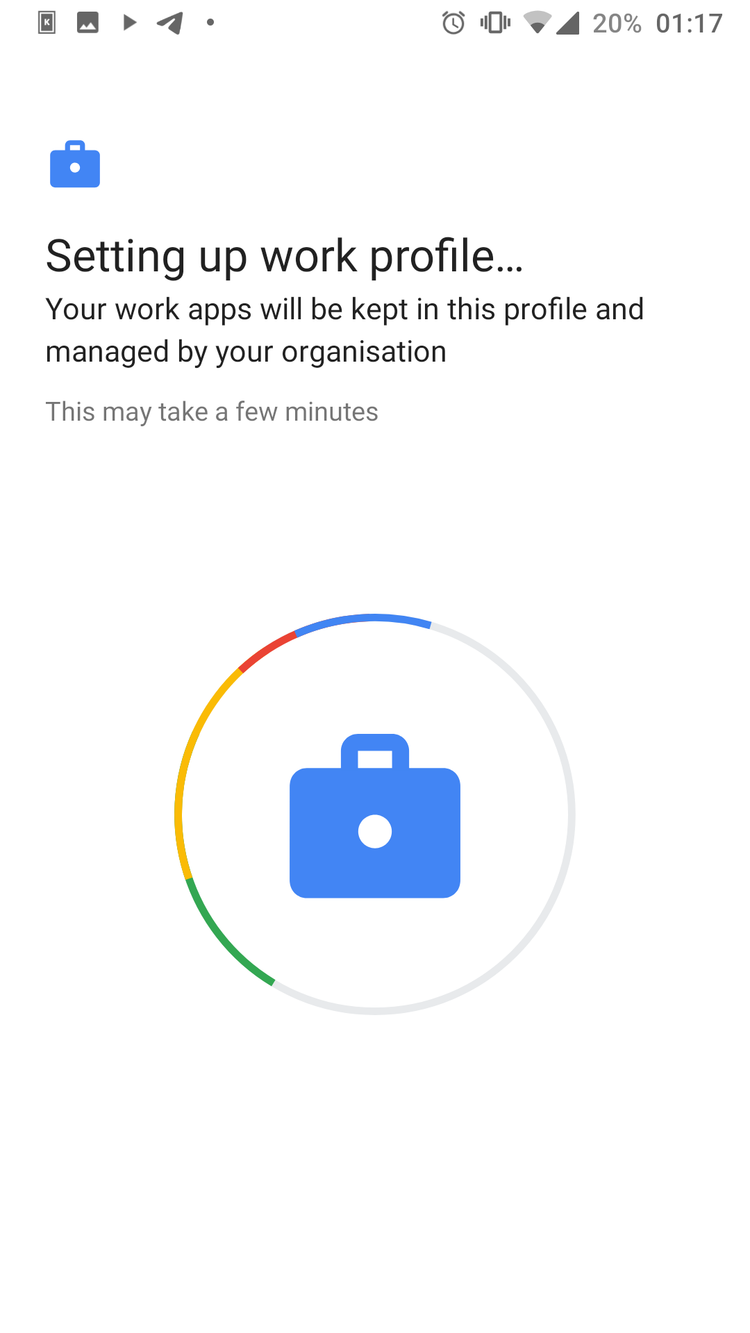
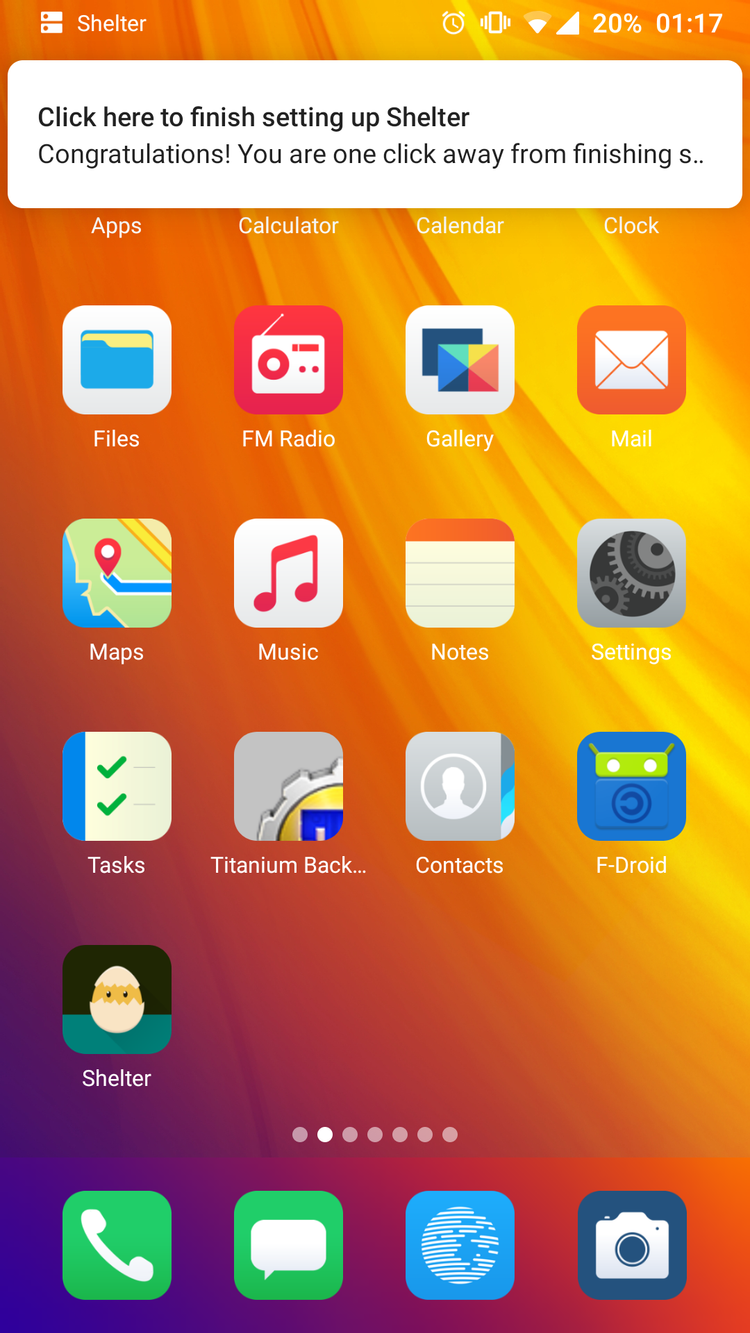
SETUP SHELTER
DECOY APPS

2



SETUP SHELTER
DECOY APPS

2
CLONE APP TO SHELTER

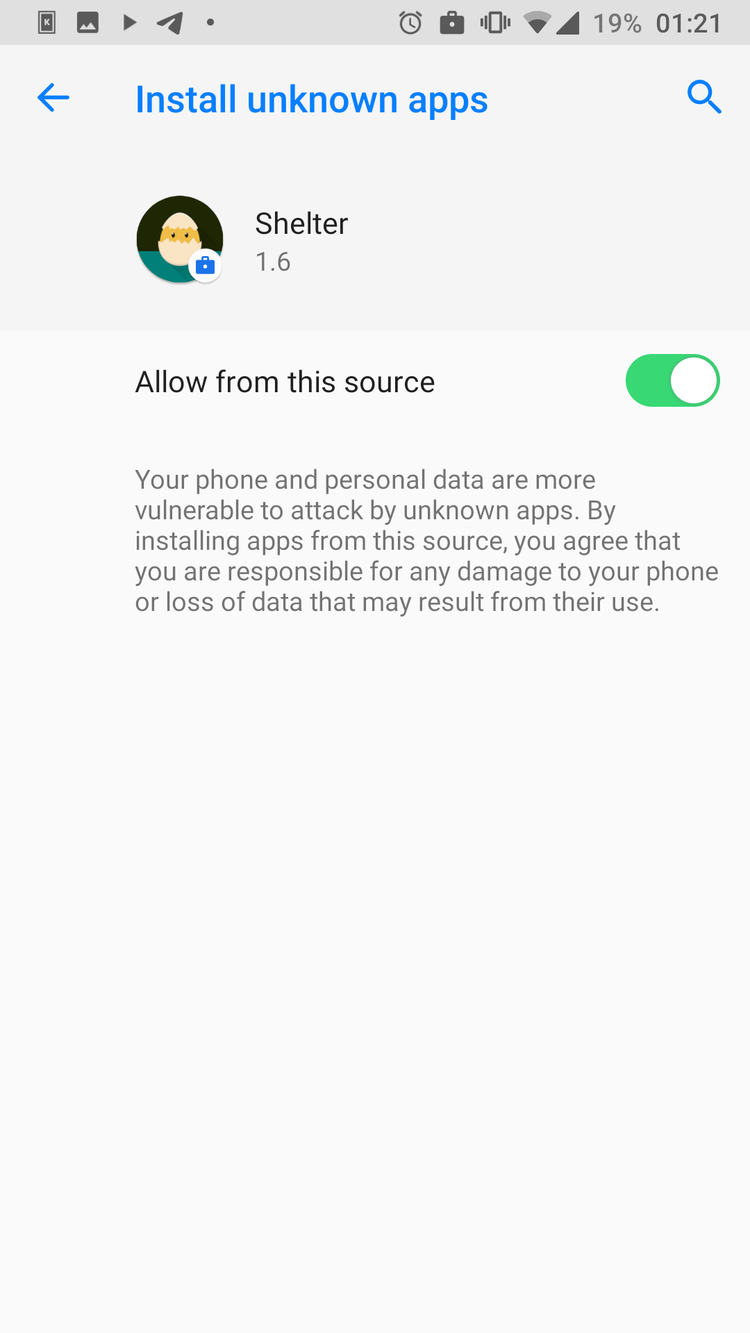
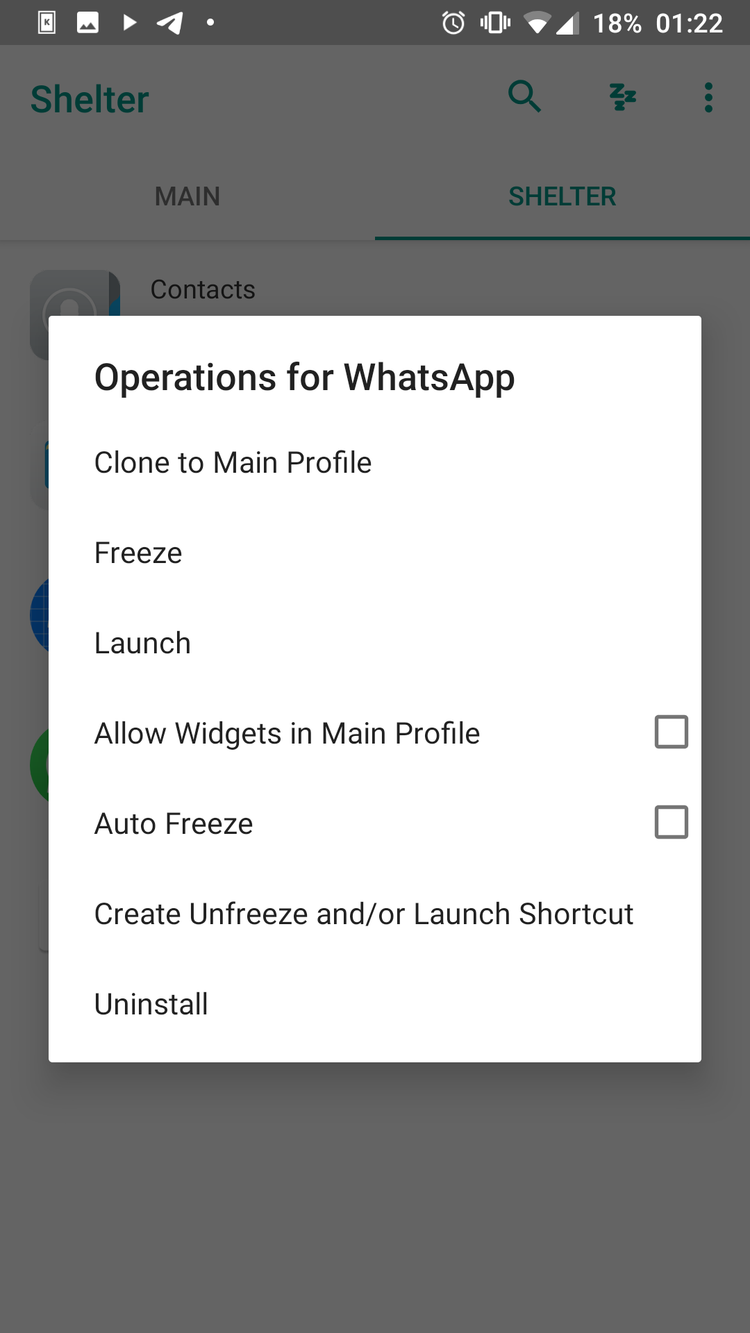
DECOY APPS

2
PROFILE TOGGLE / NO NOTIFICATIONS
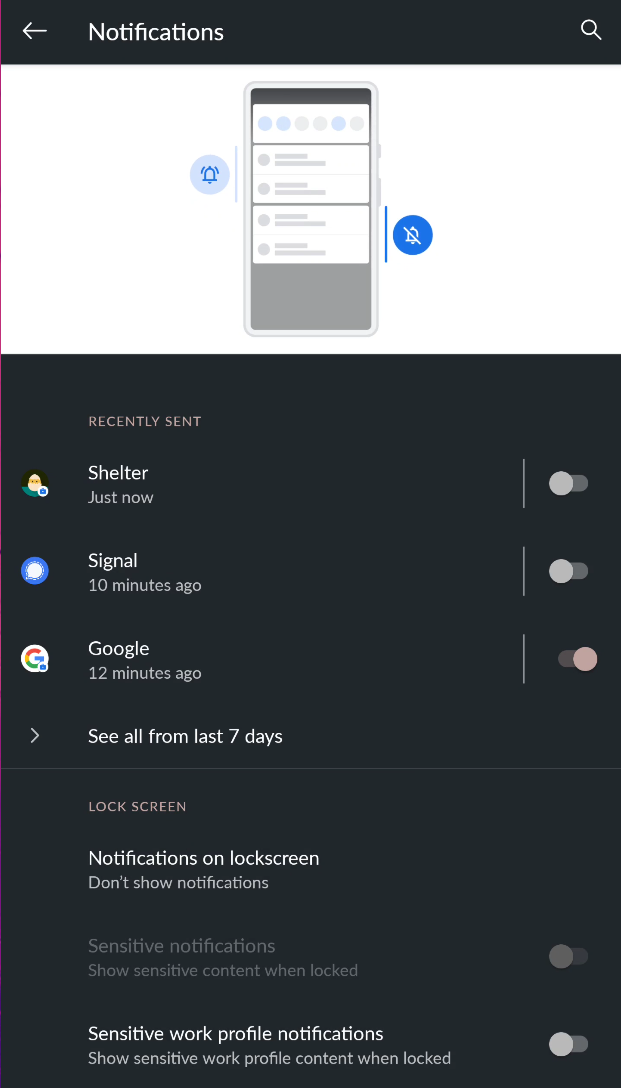
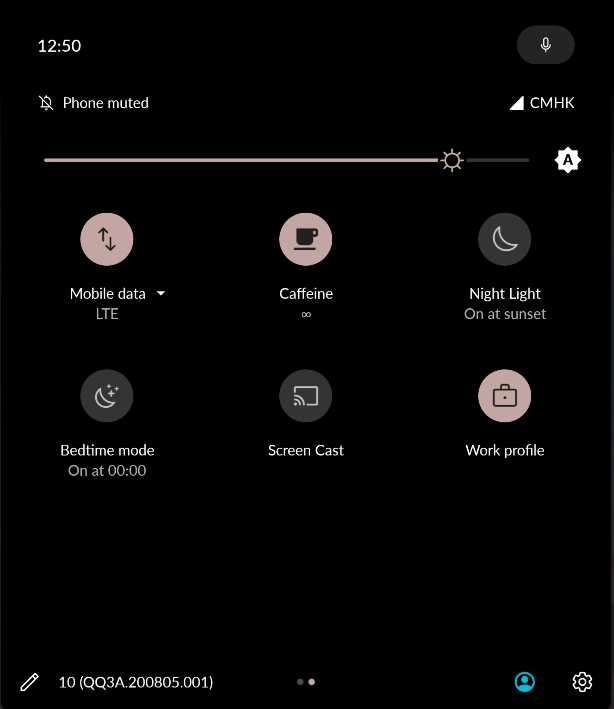


DECOY APPS

2
WORK PROFILE ON / OFF


DECOY APPS

2
HIDE ICONS




DECOY APPS

2
... HIDE ICONS
DECOY APPS
2
DUPLICATE APPS
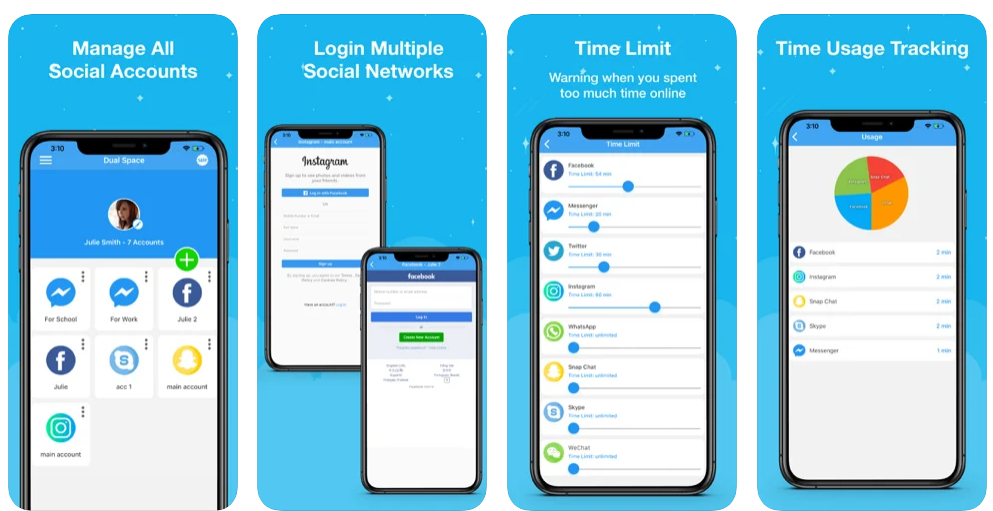

Dual Space: Social Manager
DECOY APPS
2
MOVE APPS to APP LIBRARY


HOW TO SAFELY COMMUNICATE?
1
AVOID OLD METHODS
2
E2EE APPS
(e.g. SIGNAL)
NO "MOBILE" CALLS
CALLS
MESSAGES
NO SMS

2
SCREEN LOCK
and timeout, prevent screenshot, incognito keyboard


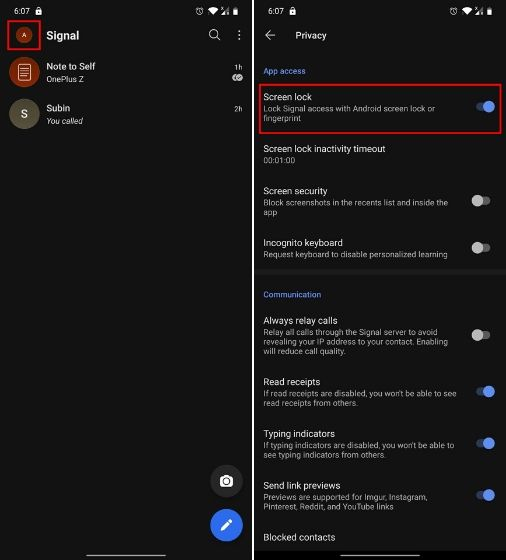
2
SET PIN
for backups, restore, and identify verification



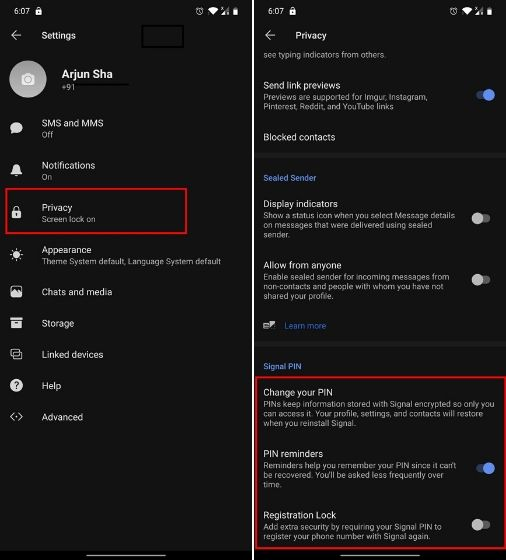
2
<PING>
turn off notifications, or hide the message



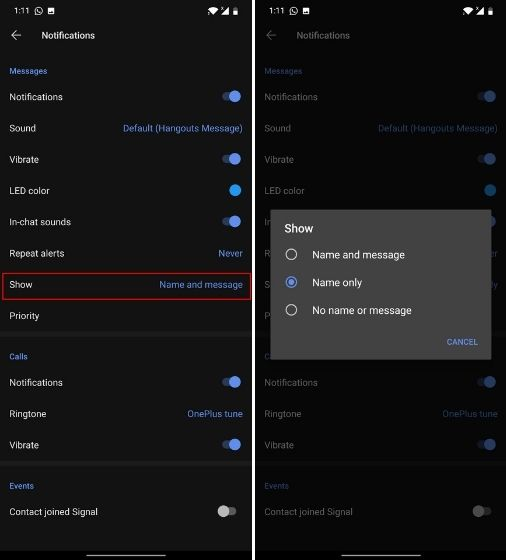
2
BYE, BYE, MSG
auto delete messages after a delay



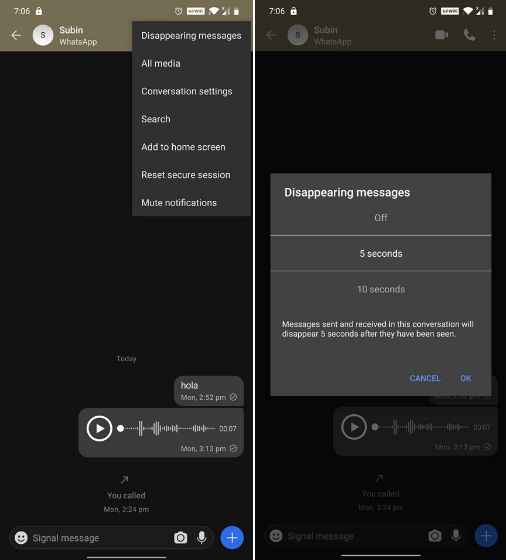
2
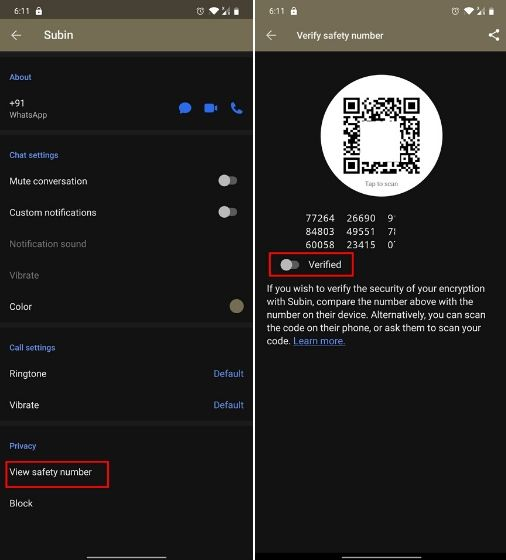
Don't trust. Verify.
verify your critical contacts



HOW TO SAFELY
STORE FILES
1
ENCRYPTED DRIVE

2
ENCRYPTED
VAULT
3
SELECTIVE CLOUD SYNC
4
ONLY CARRY WITH YOU WHAT YOU REALLY NEED
HOW TO SAFELY
STORE FILES
ONLY CARRY WITH YOU WHAT YOU REALLY NEED
BACKUP OR DELETE EVERYTHING ELSE
5
2
ENCRYPTED VAULT

[play store link]
Calculator Photo Vault
1. install app
2. secret button
3. setup security
4. select photos to hide in vault
5. new folder
6. encryption mode : encryption
2
ENCRYPTED VAULT

1
STORE ANY FILE
TYPE
2
LIMIT TO 1000
FILES PER FOLDER
3
DO NOT TOUCH
/.privacy_safe
4
REGULAR BACK UPS OFF DEVICE
5
LIMIT TO 1000
FILES PER FOLDER
6
CONSIDER PREMIUM

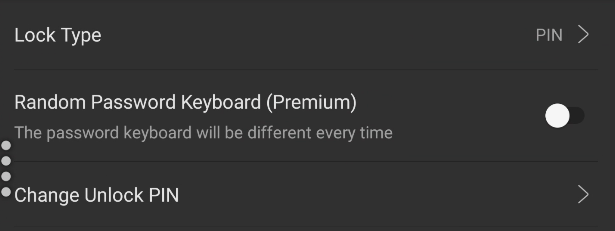
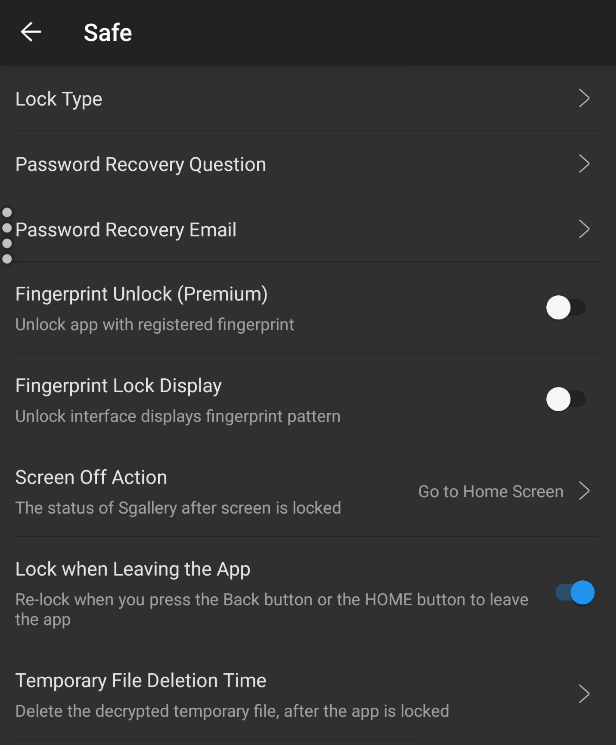
Settings > Safe
Lock Type = PIN
Lock Type = PIN
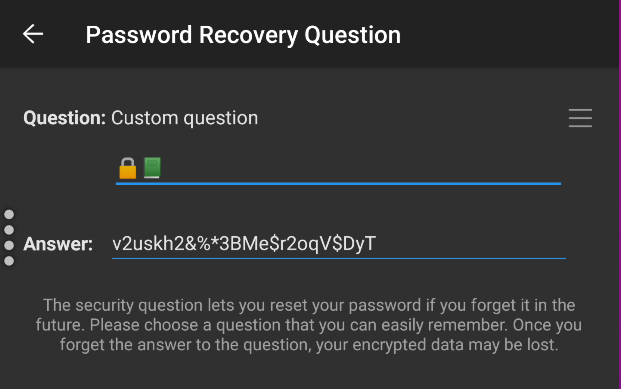
Recovery Question should just point to your password manager
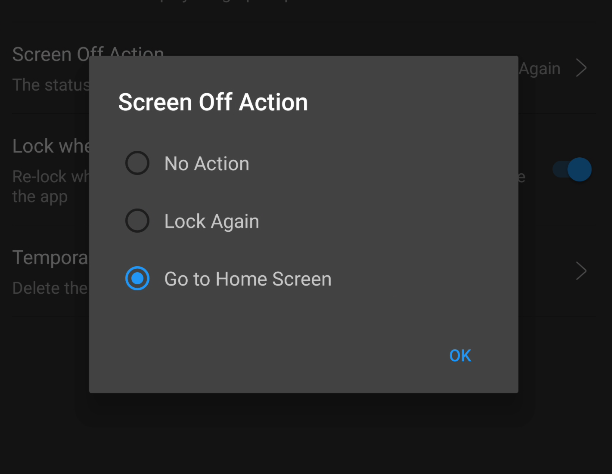
Screen off = Go to Home Screen

Settings > Disguise Icon

[ADVANCED] Hide App Icon
Change Calculator Icon
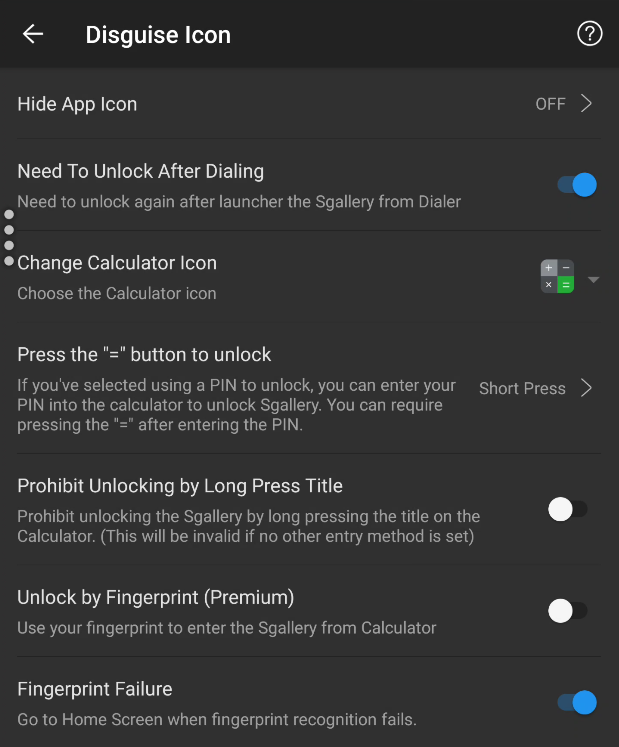
OPTIONAL DISGUISES
Fake Password
PREMIUM OPTIONS
Prohibit Screenshots
Shake Close
1
2
Photo Vault Lock Photos Album

FREE / PRO USD 4
Similar Features
3
4
Decoy Password
Backup Support
[app store link]
HOW TO SAFELY
USE THE WEB
1
PRIVACY BROWSER
2
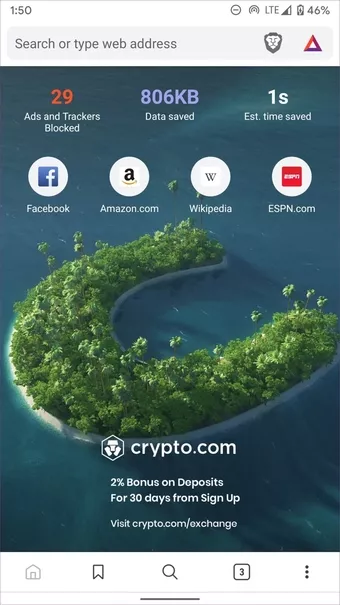
DISABLE SEARCH HISTORY
3
SECURE
DNS

4
USE A
VPN
PRIVACY BROWSER
1
2
DISABLE
SEARCH
HISTORY
... and everything Google is tracking about you that you can live without


3
SECURE DNS

[play store link]



3
SECURE DNS
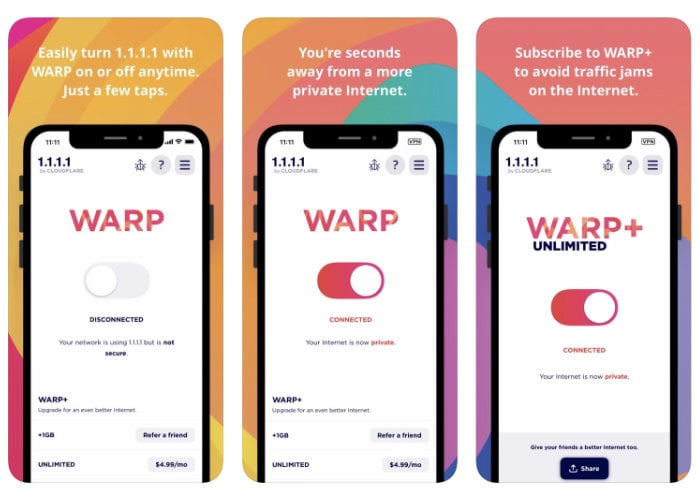

[app store link]
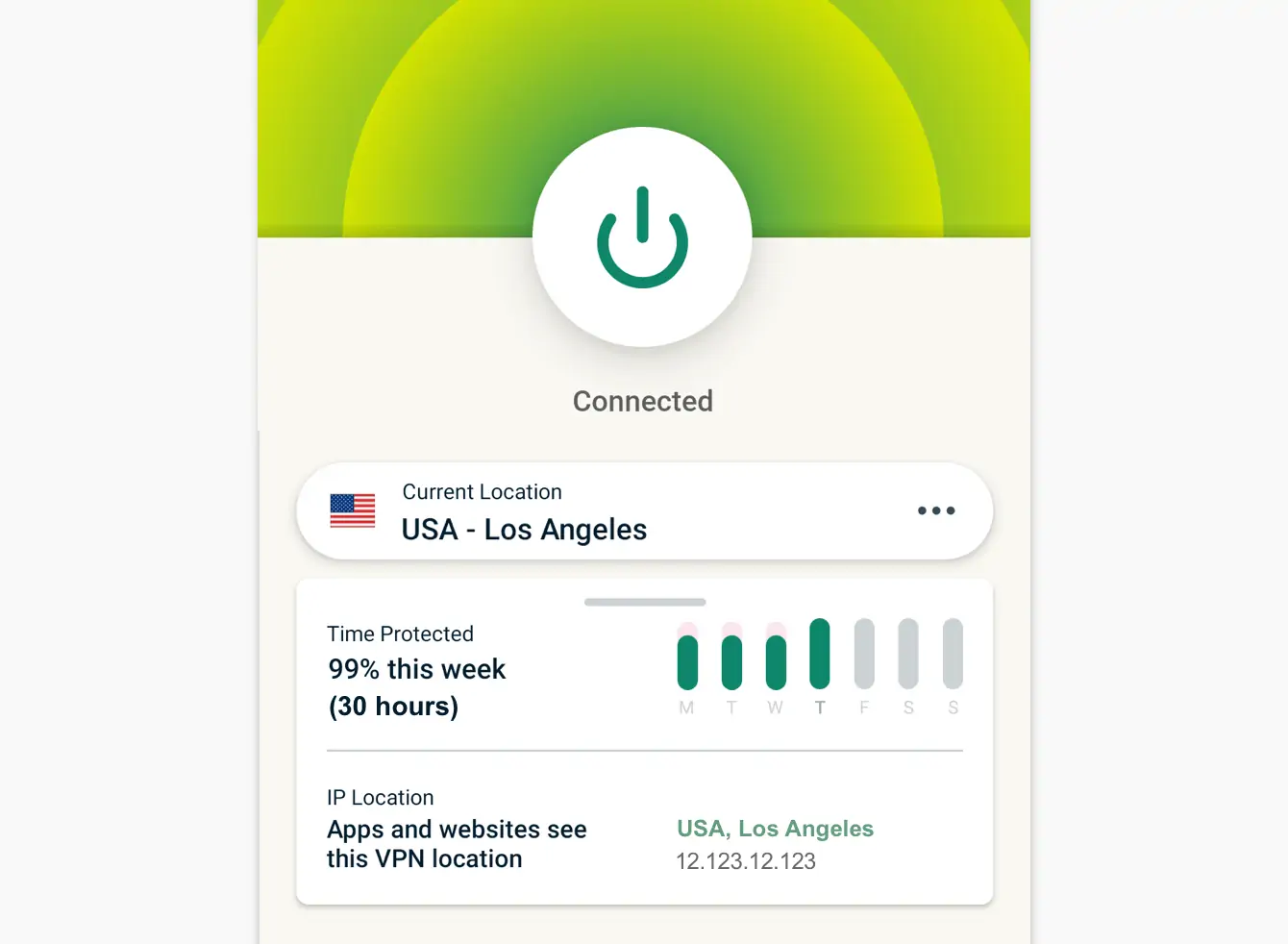
4
VIRTUAL PRIVATE NETWORK
HOW TO SAFELY
TAKE PICTURES
2
SAFE STORAGE
ENCRYPTED
VAULT

1
META DATA
GEOTAGS
1
META DATA
GEOTAGS
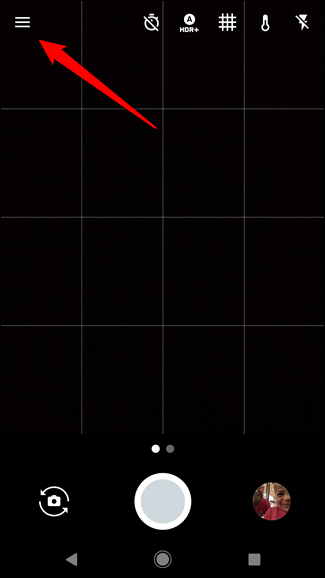
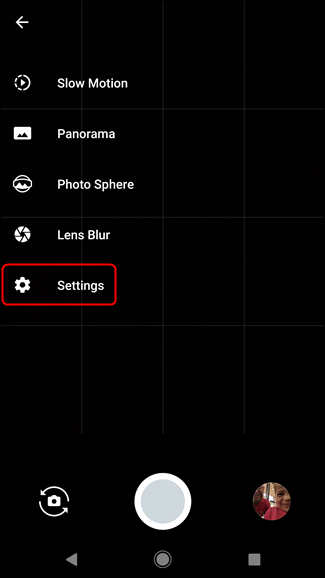
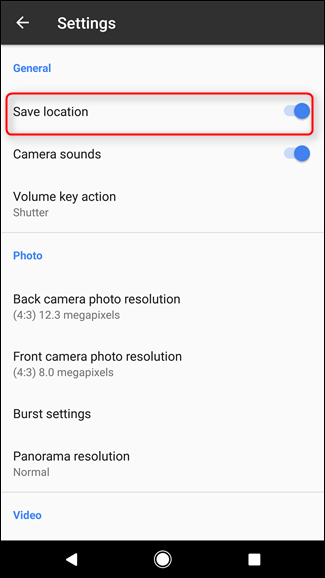

1
META DATA
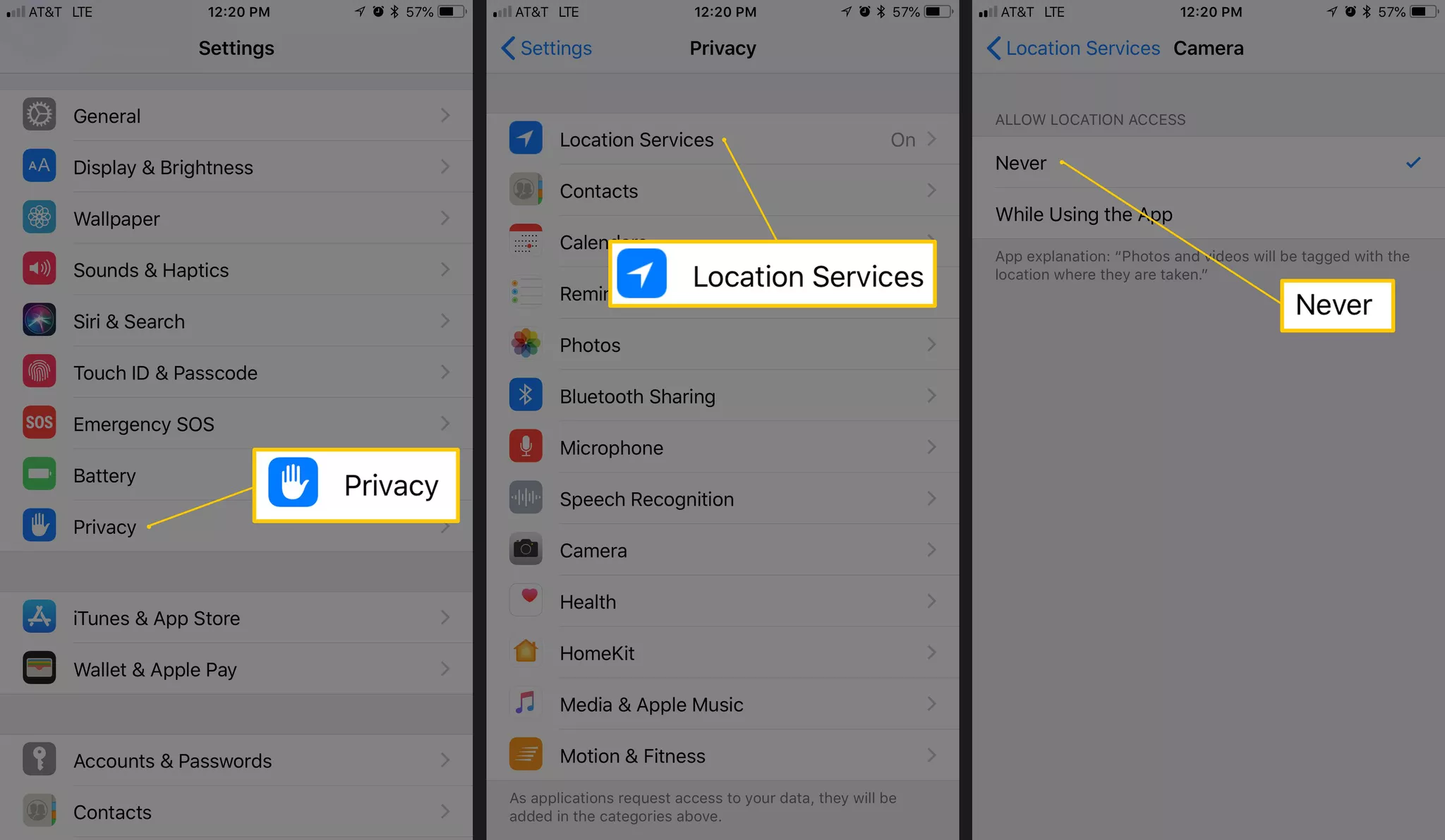

2
SAFE
STORAGE
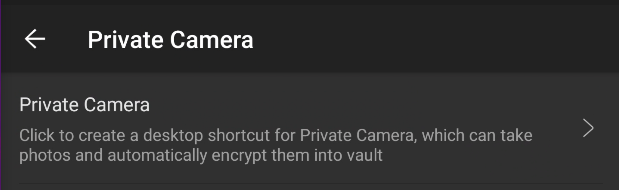
Settings > Private Camera

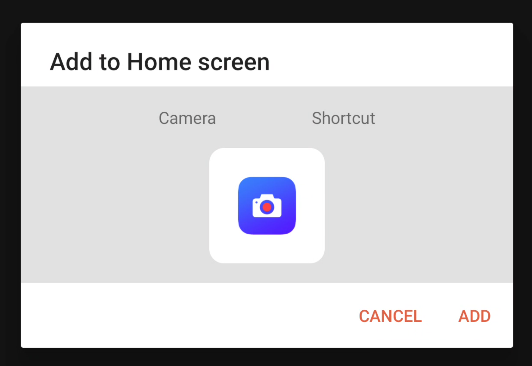

1
2
3
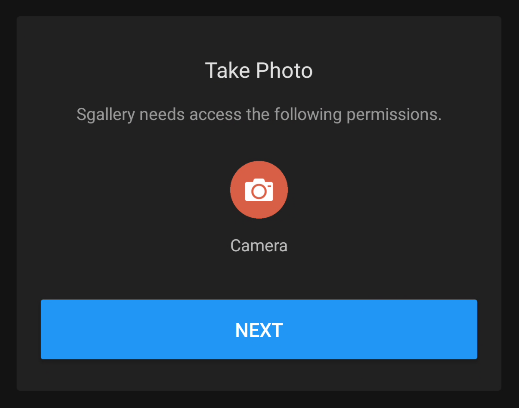
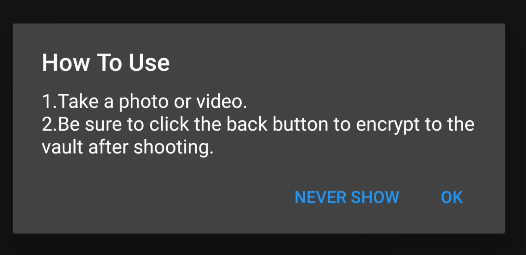
4
5
6

2
SAFE STORAGE
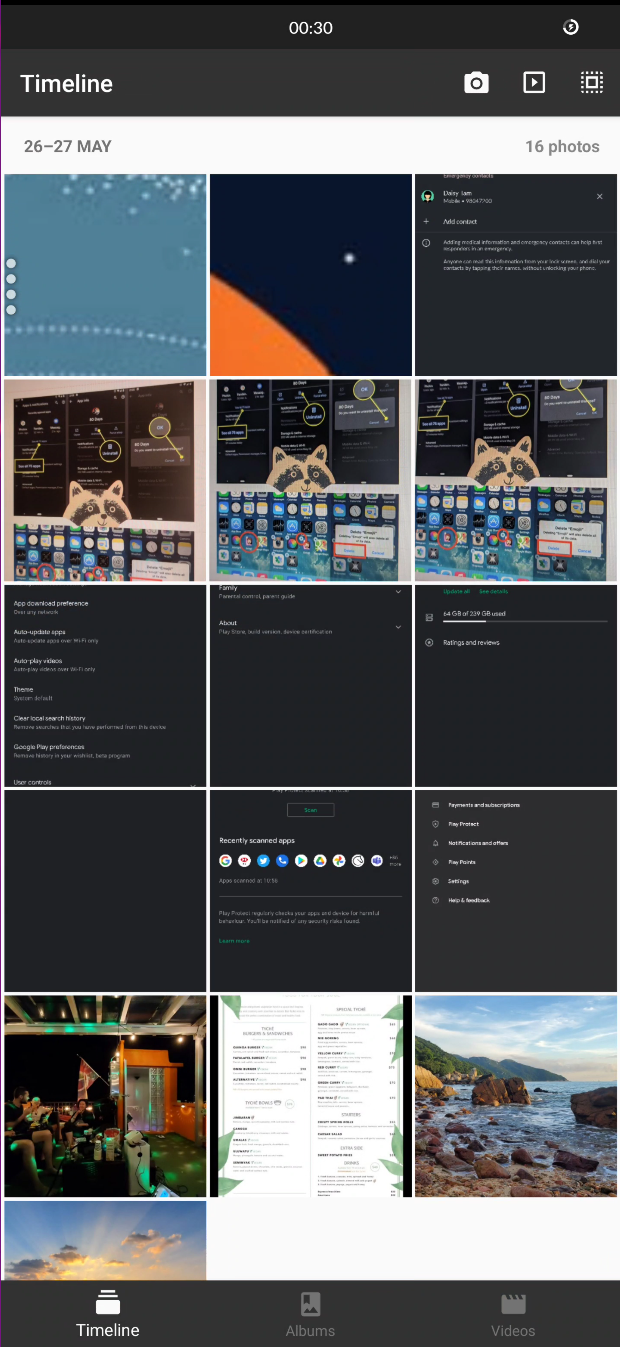
< taking a photo with the "encrypted" camera
doesn't show >
up in gallery

1
2
Photo Vault Lock Photos Album

FREE / PRO USD 4
Similar Features
3
4
Decoy Password
Backup Support
[app store link]
QUESTIONS?!
QUESTIONS?!

1
Set solid
passcode
2
Verify iCloud setting
(off where possible)
3
No/limited lock screen notifications
6
PIN code
on your SIM
5
Turn-off Auto-Join WiFi networks
4
Optional : Add SOS Emergency Contact


4321
p@$$w!rD
FastBulkCat
local
remote server
PIN
vs
PASSWORD
vs
PASSPHRASE
vs

HOW MANY PASSPHRASES DO YOU NEED?
PASSWORD MANAGER
1
MICROSOFT / iCLOUD
2
GENERATE YOUR PASSPHRASES
1
PICK NUMBER
OF WORDS

2
3
LOOKUP RESULT
ON WORDLIST
4
5
6
GENERATE STRONG PASSWORDS
1
ONLY REMEMBER
ONE PASSPHRASE
2
UNIQUE
PASSWORDS
3
SECURE
SHARING
4
PORTABILITY
& SYNC
5
WHY USE A PASSWORD MANAGER?

BETTER
UX
6
Shall we use
iCloud Keychain?

Apple Only
Proprietary
Individual focus
Targeted
SOURCE : "Censorship, Surveillance and Profits:
A Hard Bargain for Apple in China"
New York Times, 17 May 2021
AUTHENTICATION
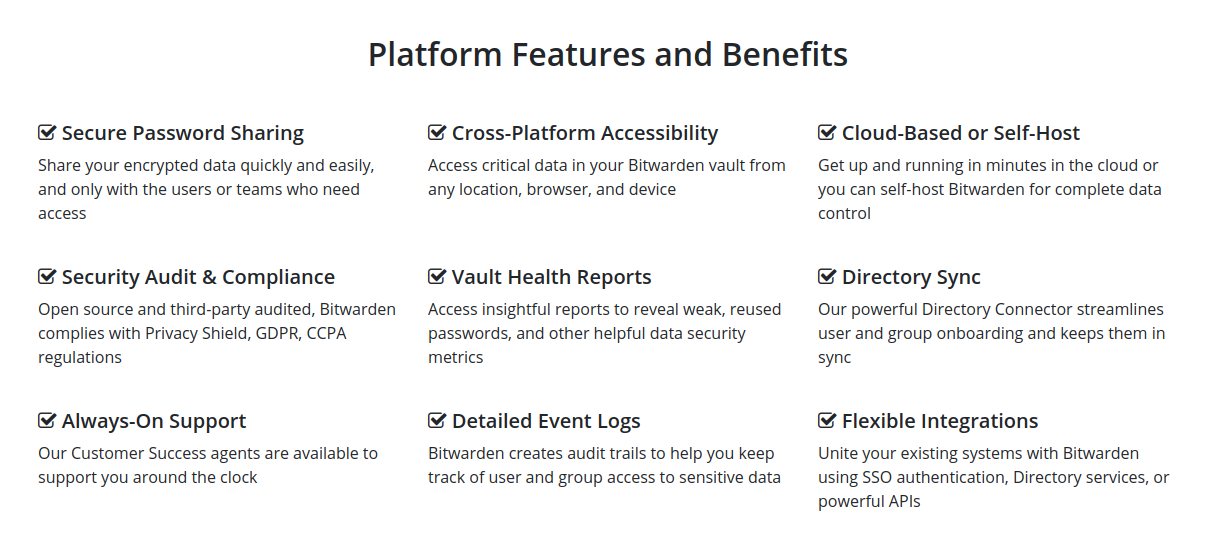
BASIC FEATURES
1
Open Source Security
2
End-to-End
Encryption
3
Cross Platform
Apps & Sync
6
Support for 2FA, FIDO, and T-OTP
5
Password Capture & Auto-Fill
4
Support for all Popular Browsers
ADVANCED FEATURES
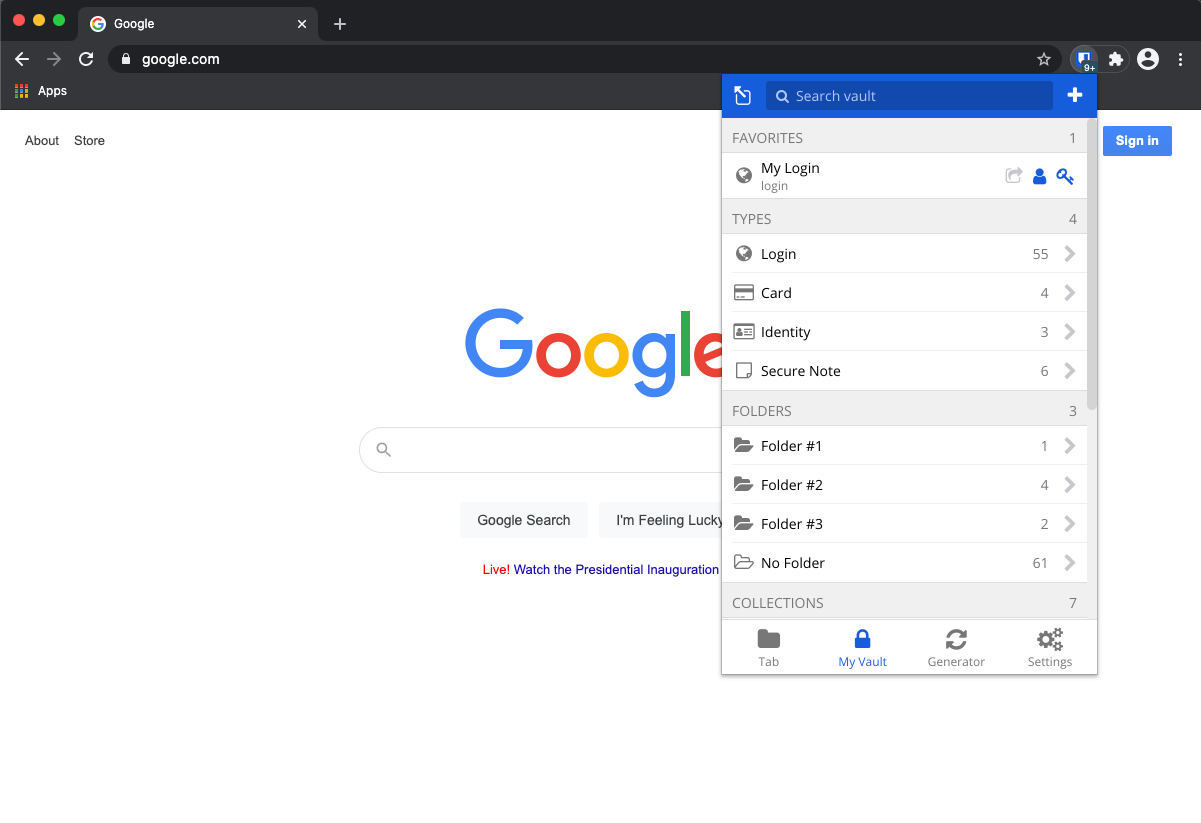
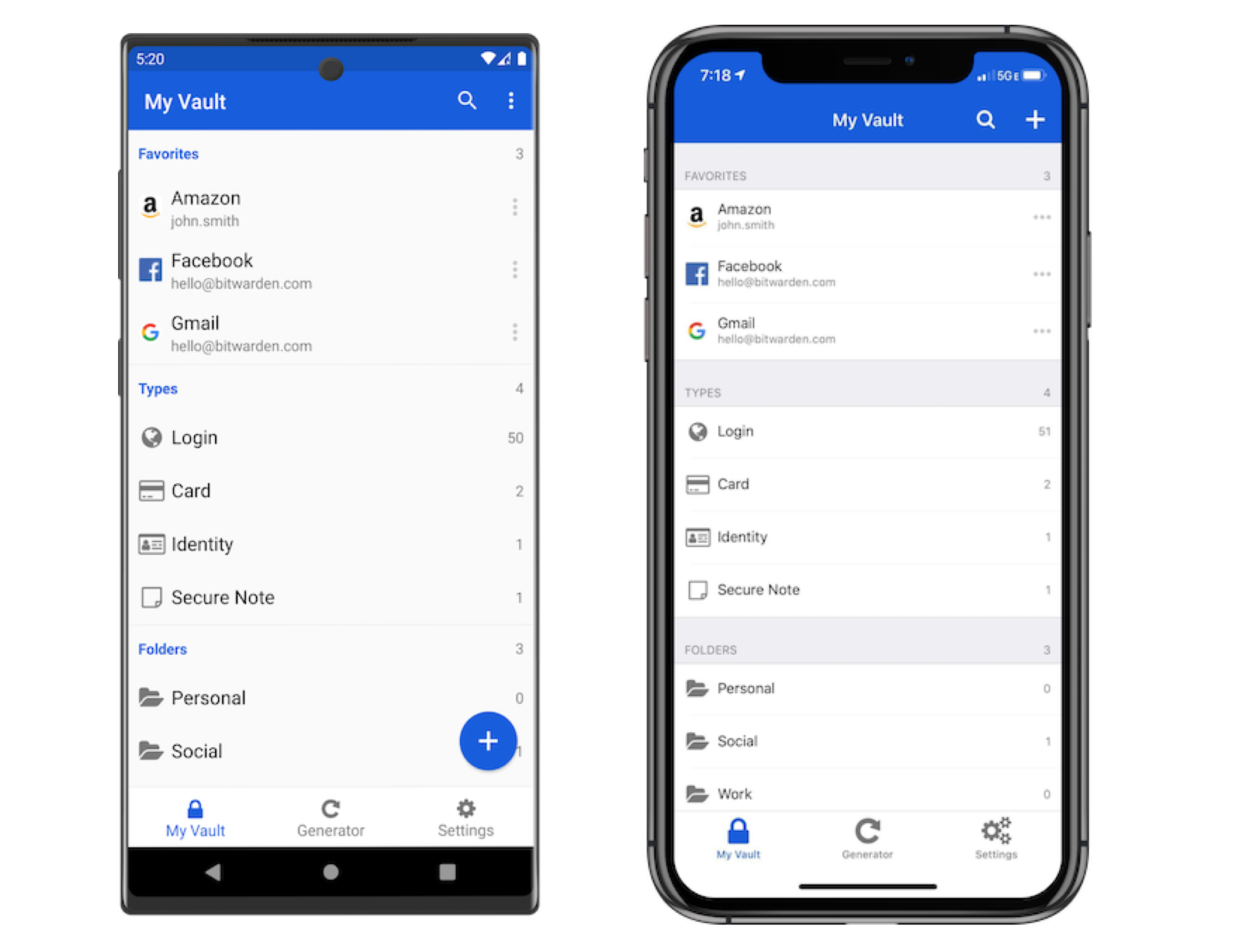
HOW TO USE BITWARDEN?
Web Vault
Browser Extension
Mobile App

Web Vault
Let's get you setup with
Invite People to Organization
BitWarden Admin
Create Organization
1
3
Create Collection for Shared Passwords
2
Grant access to Collections
4
Use Passphrase generated with Diceware
BitWarden Users
Accept invitation
5
7
Click "Create Account"
6
Login to your Vault
8

ACCOUNT SETUP

Accept invitation
5

Click "Create Account"
6
"Get Started" to sign up
https://bitwarden.com/
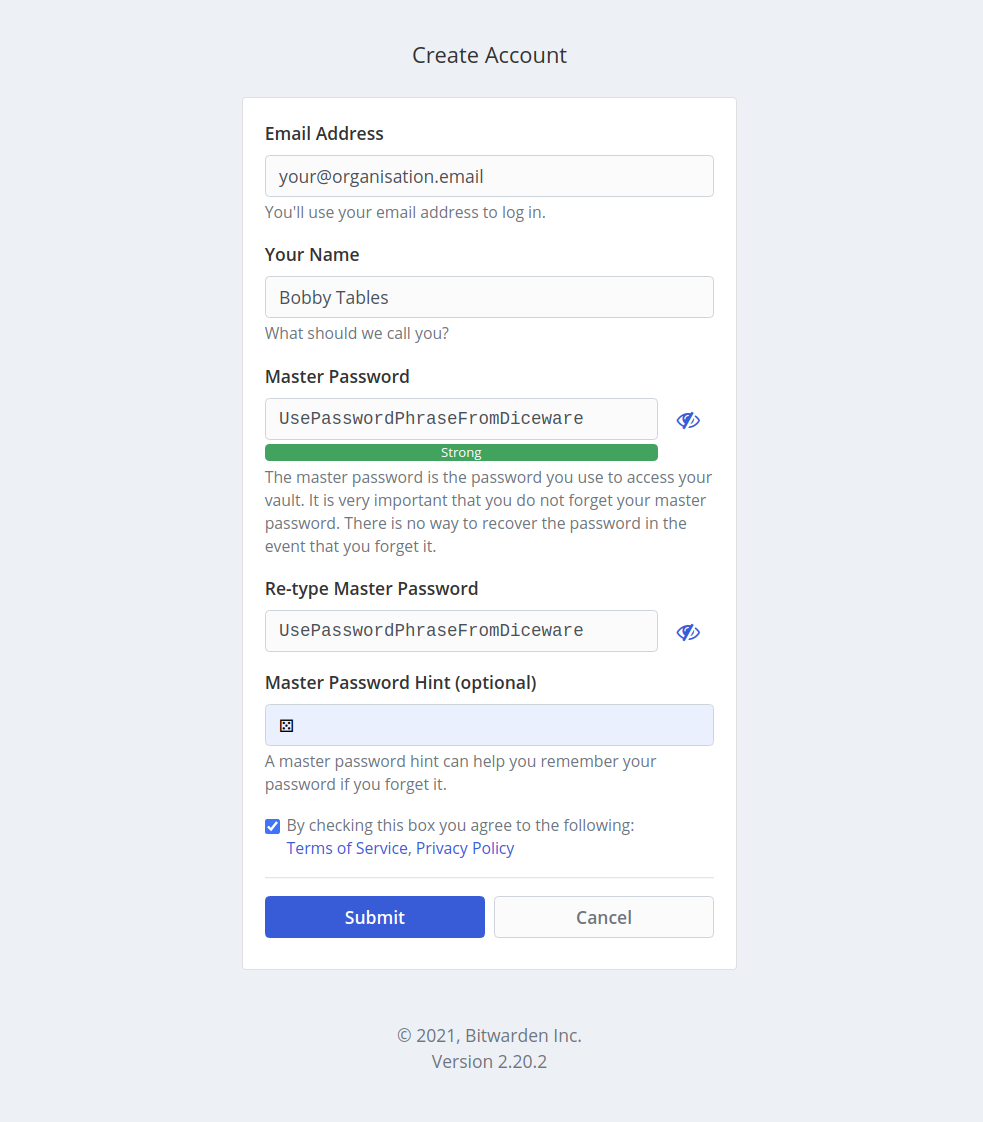
Use Passphrase generated with Diceware
7
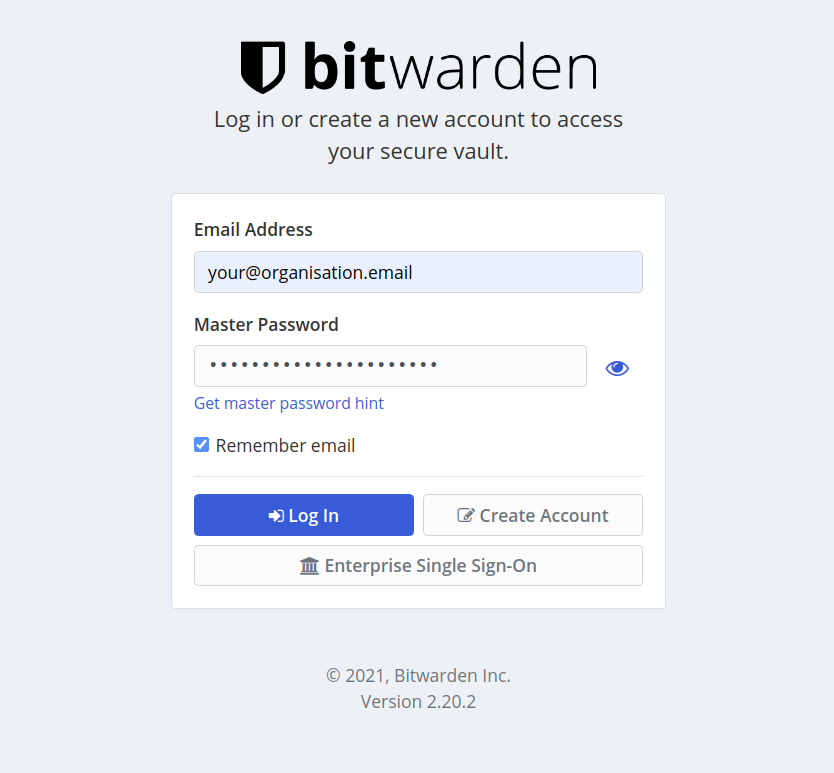
Login to your Vault
8
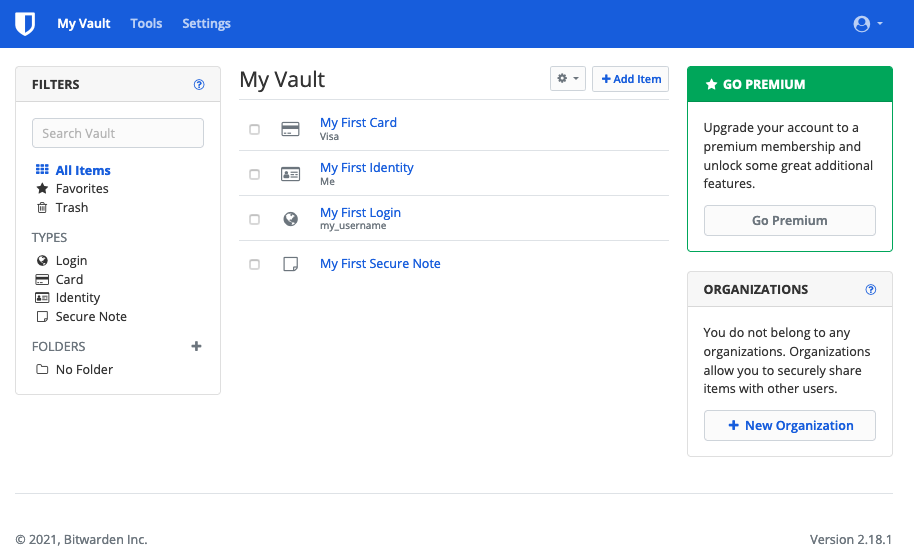
Welcome to your Vault

EMERGENCY ACCESS
Admin
Users
Add emergency contact
2
Follow Emergency Policy
3
Accept emergency contact
4
Define Emergency Protocol
1
point person
trigger conditions
access control
automatic grant
Confirm emergency contact
5
Confirm account fingerprint
6
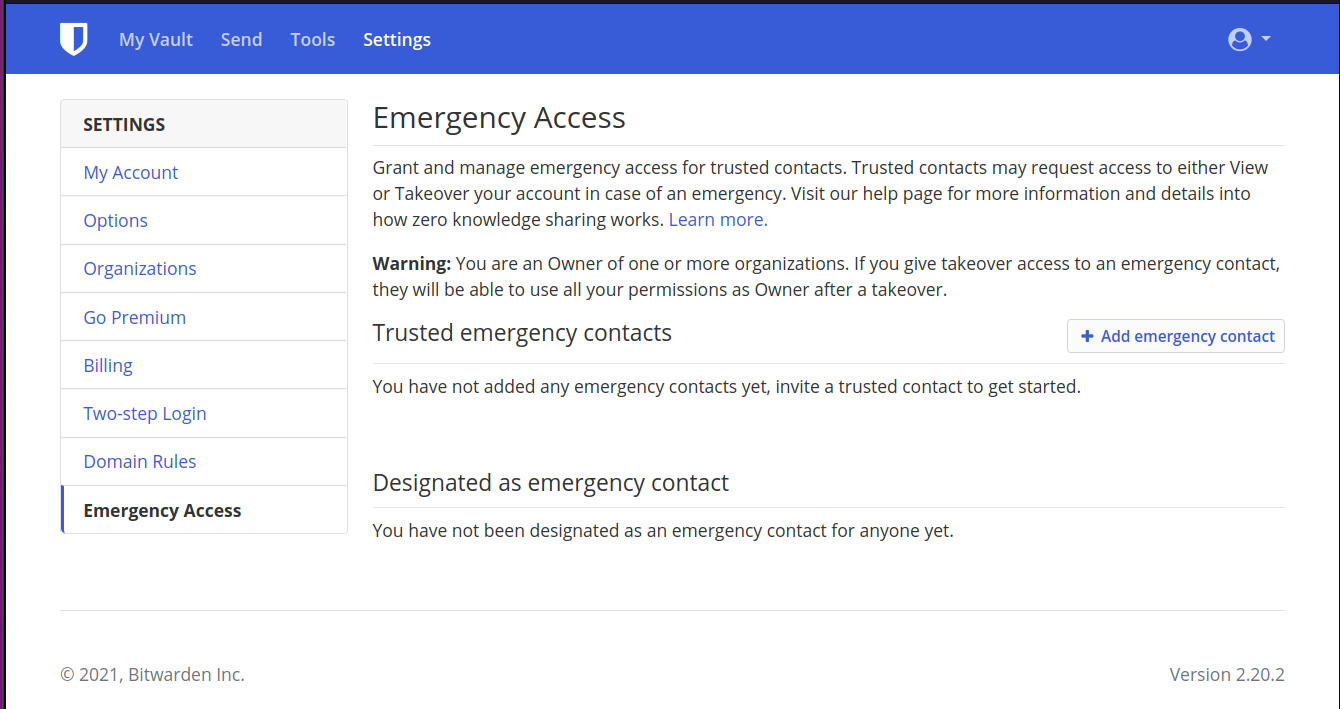
Add emergency contact
2
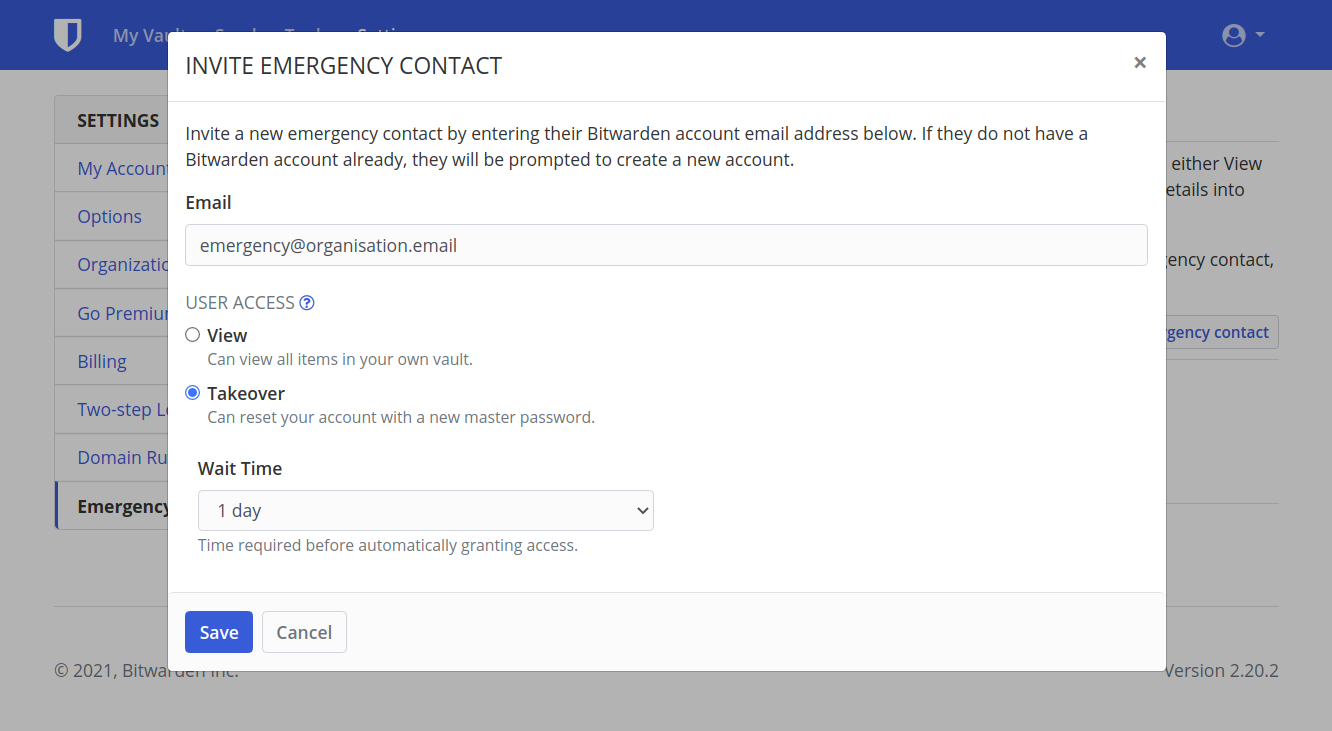
Follow Emergency Policy
3

You've succesfully invited your Emergency Contact ...
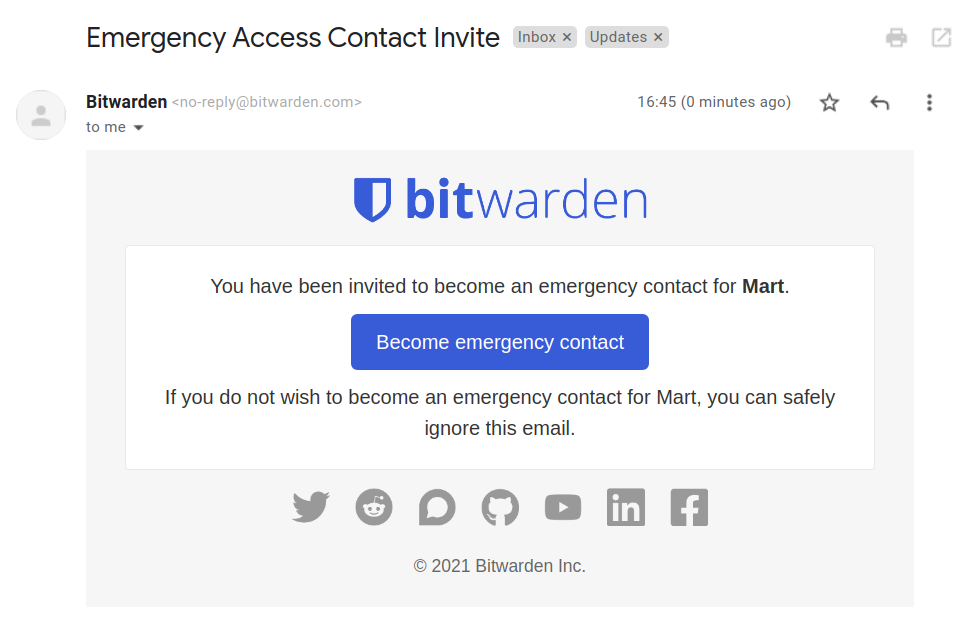
Accept emergency contact
4
Accept emergency contact
4
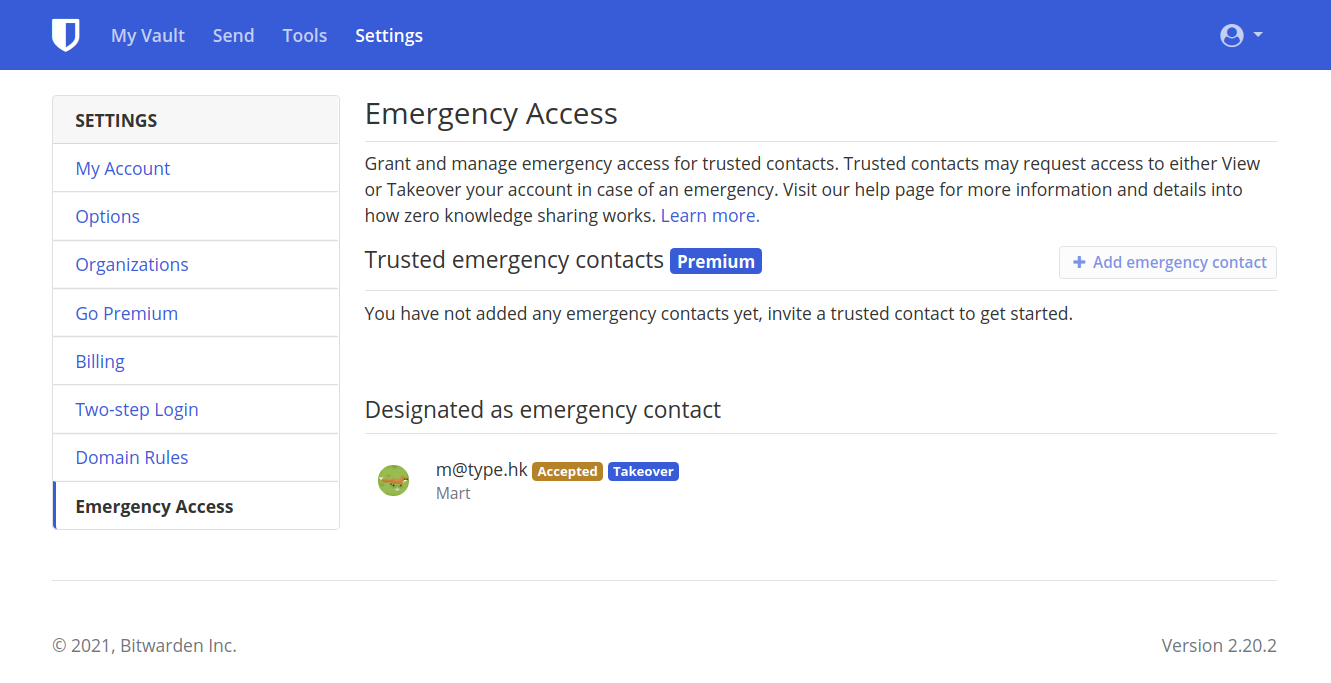
You've succesfully accepted your Emergency Contact ...
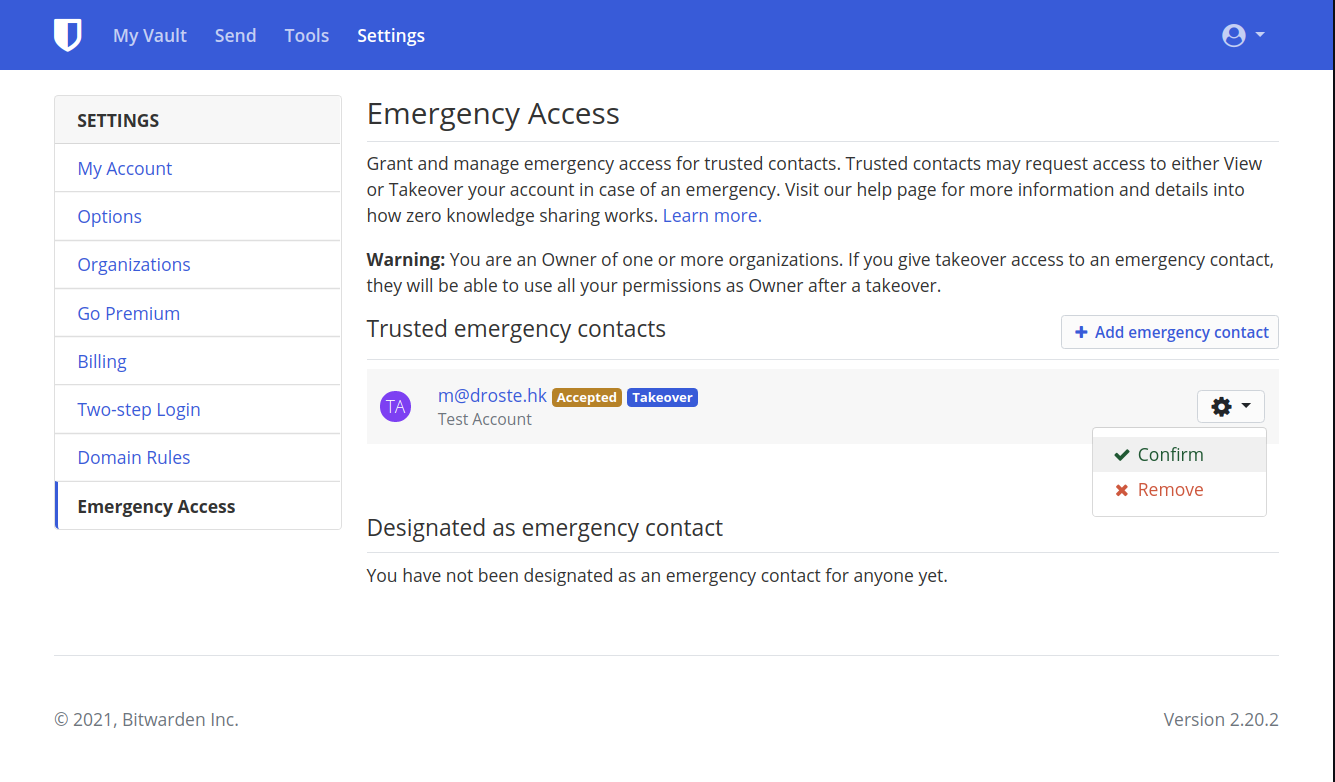
Confirm emergency contact
5
Accept emergency contact
4
You've succesfully accepted your Emergency Contact ...
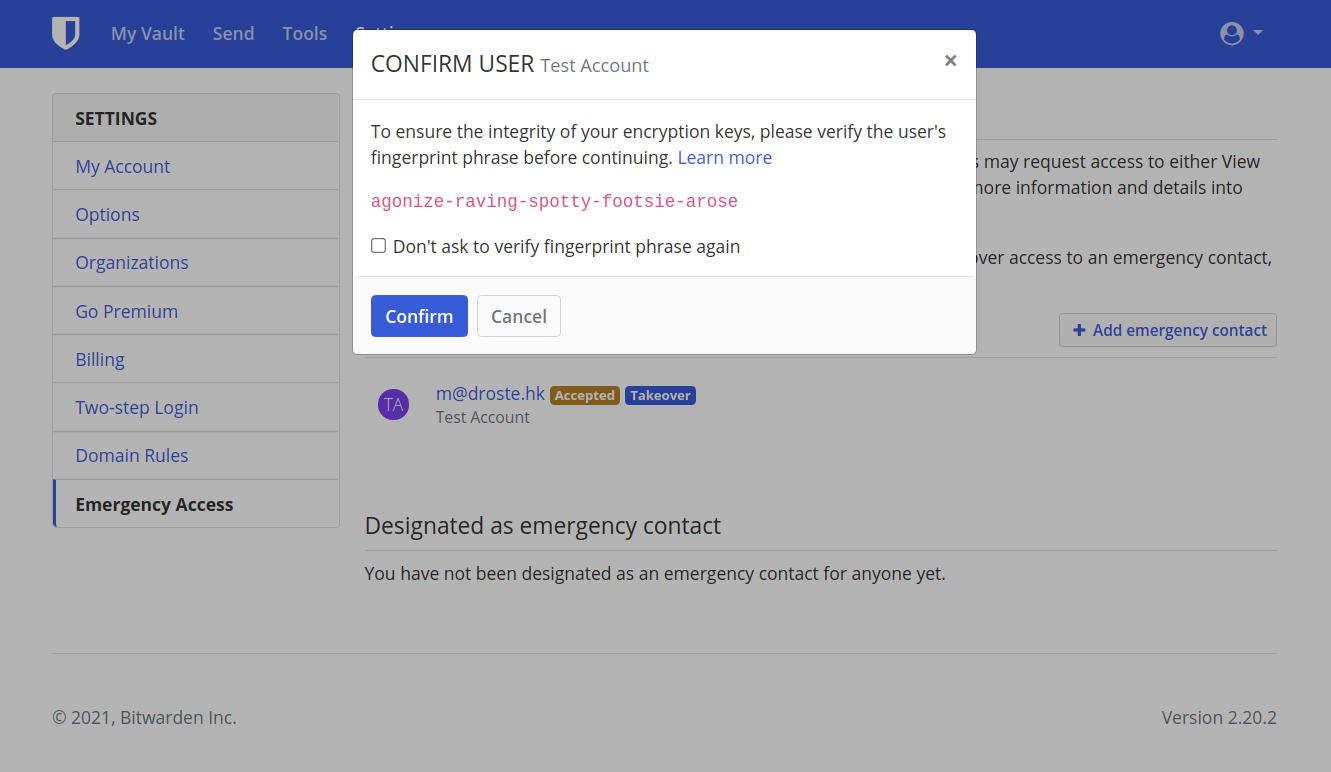

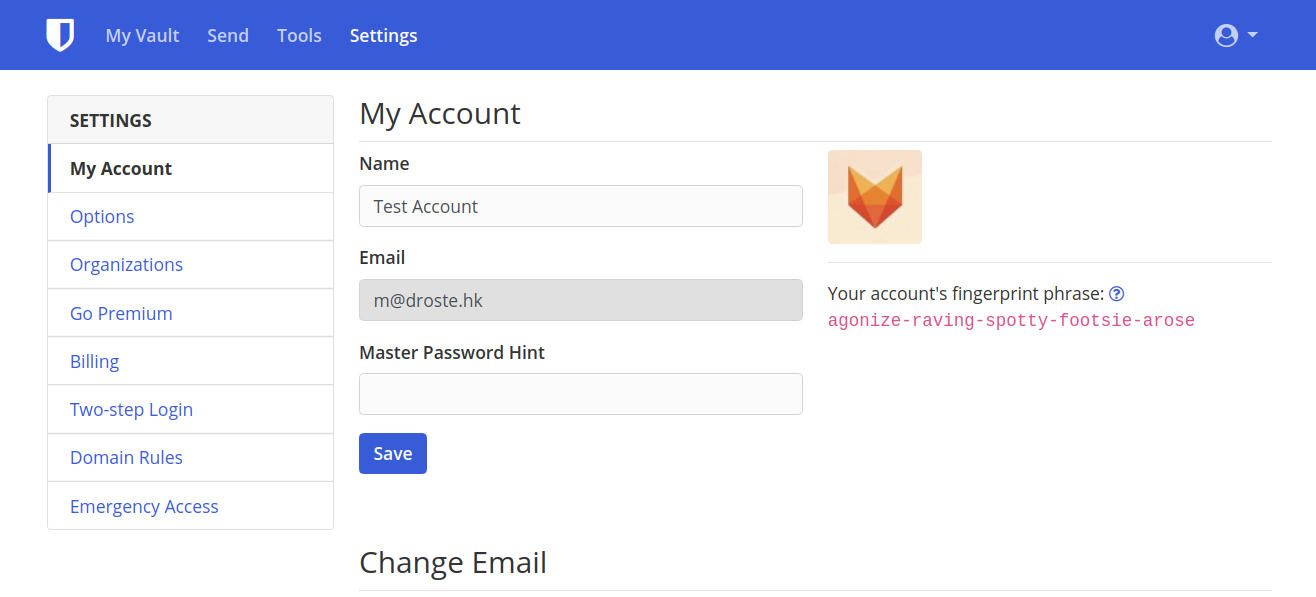
Confirm account fingerprint
6

VAULT SETTINGS
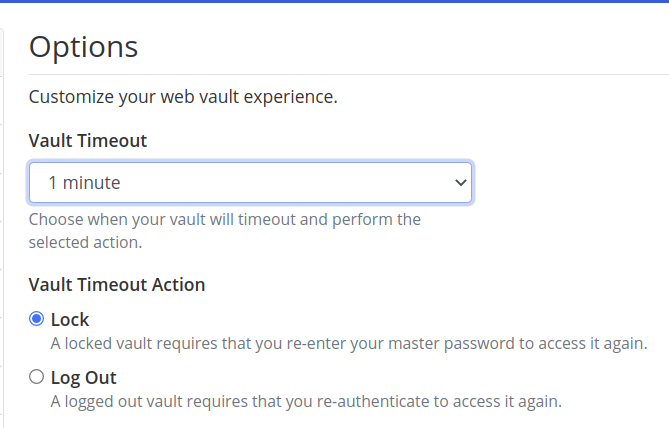
Vault Timeout
1
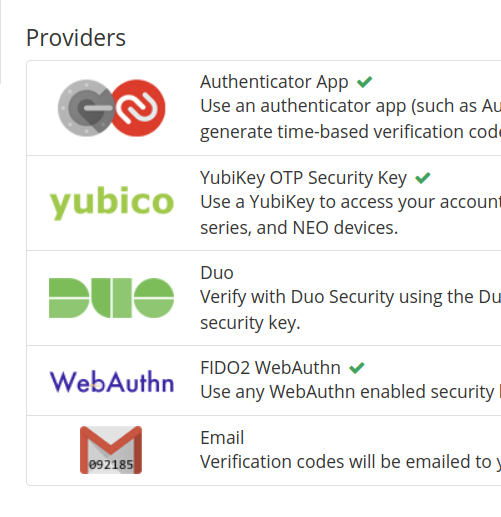
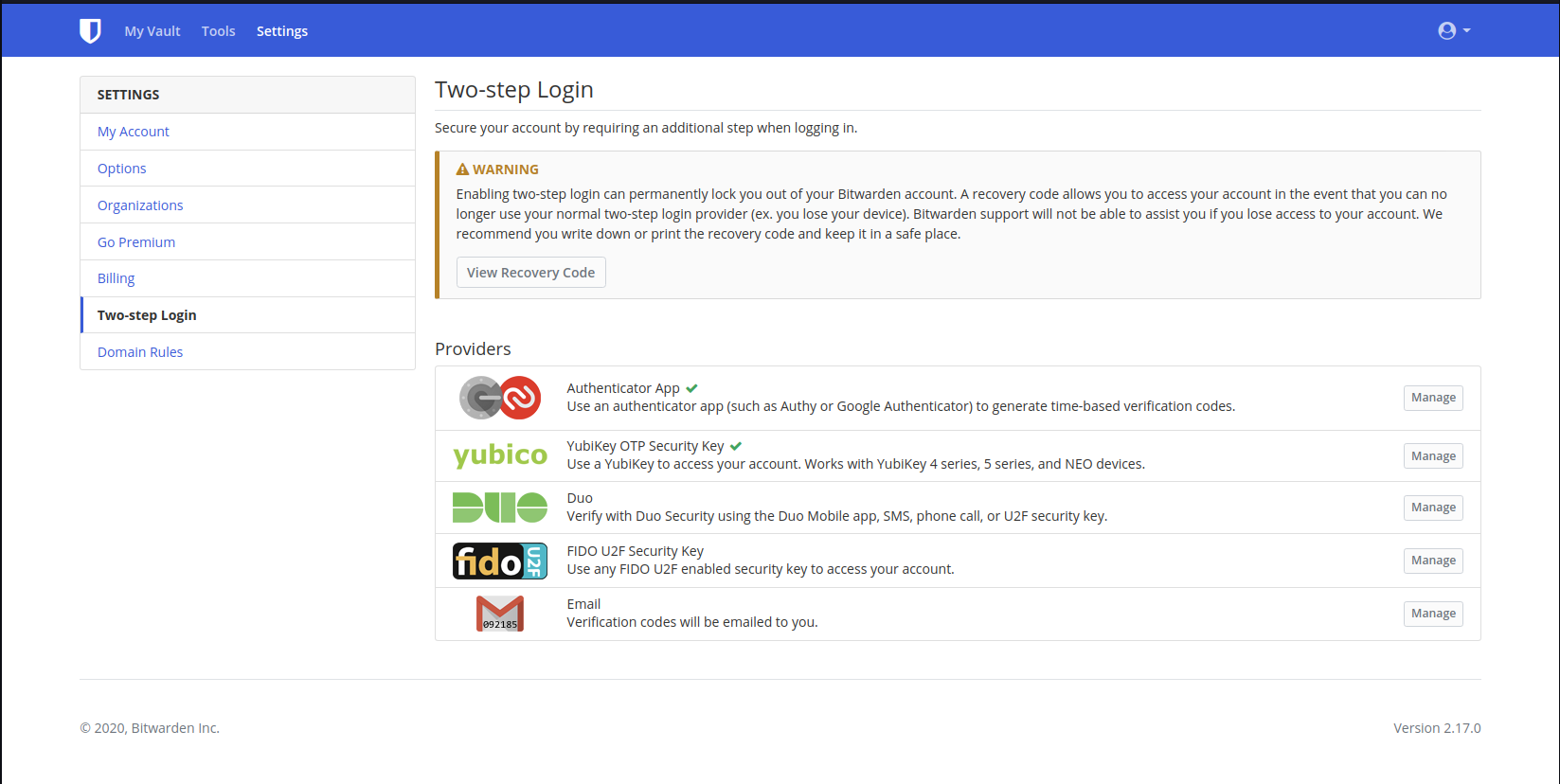
Two-step Login
2
Browser Extensions

Let's get you setup with
Set Timeout Settings
Install Browser Extension
1
3
Login and Pop out
2
Set Options
4

BASIC SETUP
Install extension & pin it
1
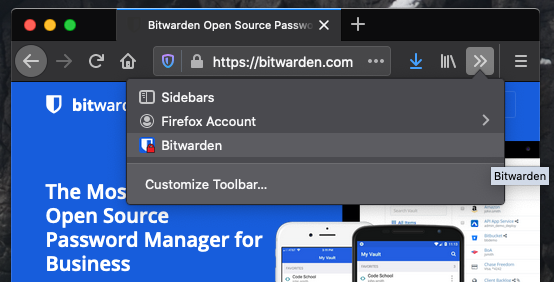
Login and Pop out
2

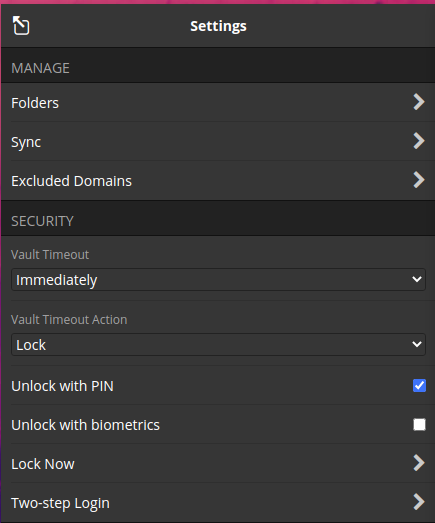
Set Timeout Settings
3
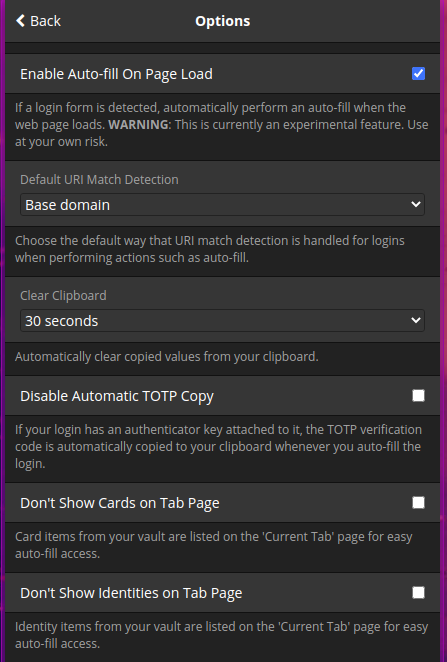
Set options to what your are comfortable with
4
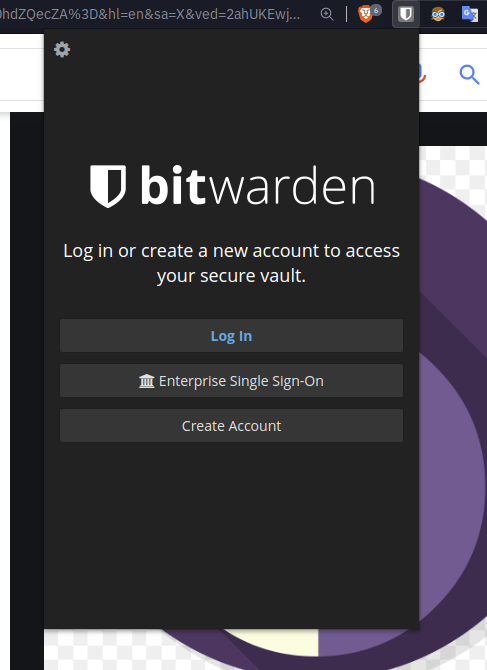
Log in to BitWarden extension
1
3
Existing account : login and store password
2
Login flow with BitWarden
4

DAILY USE
New account : generate and store password
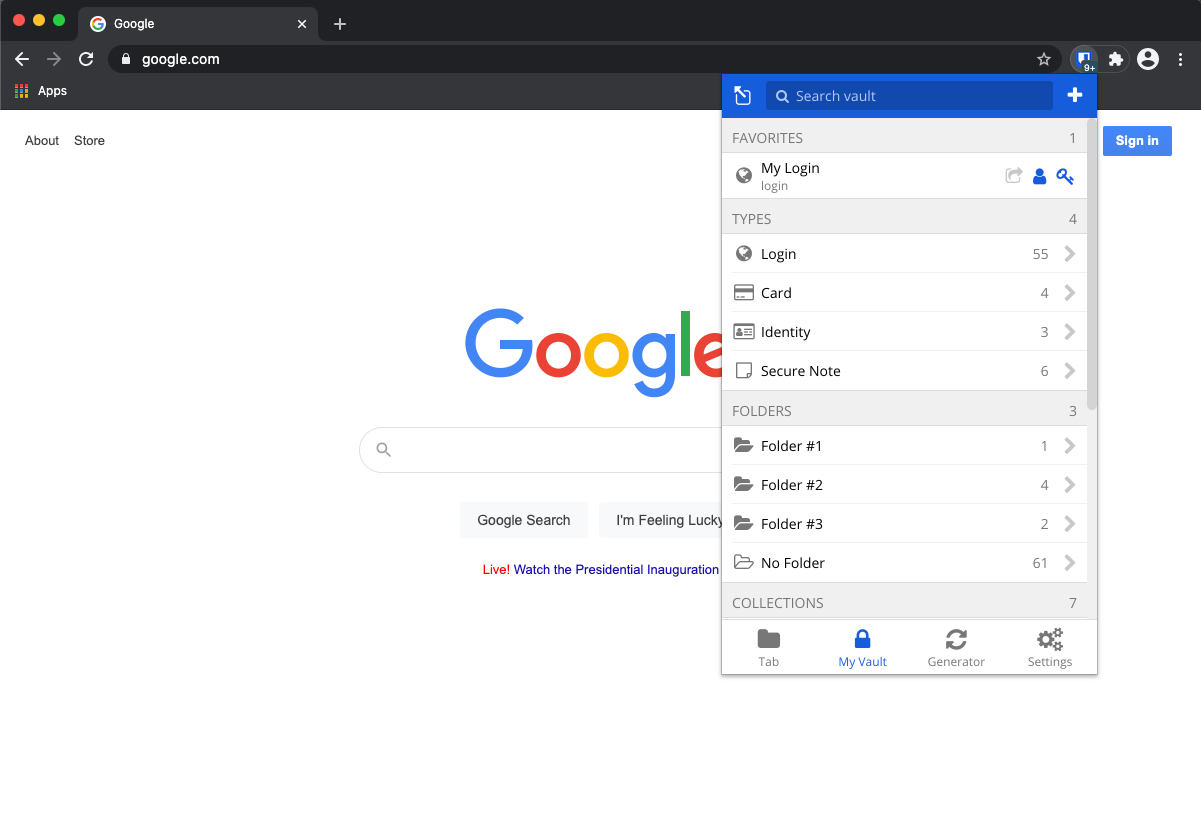
Log in to BitWarden extension
1
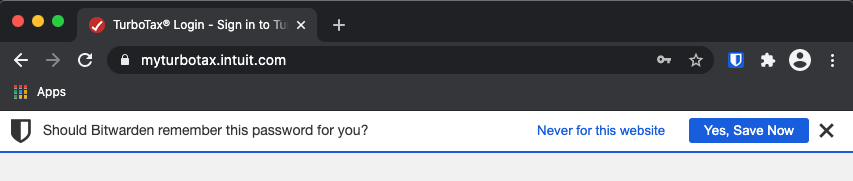
Existing account : login and store password
2
New accounts : generate and store password
3
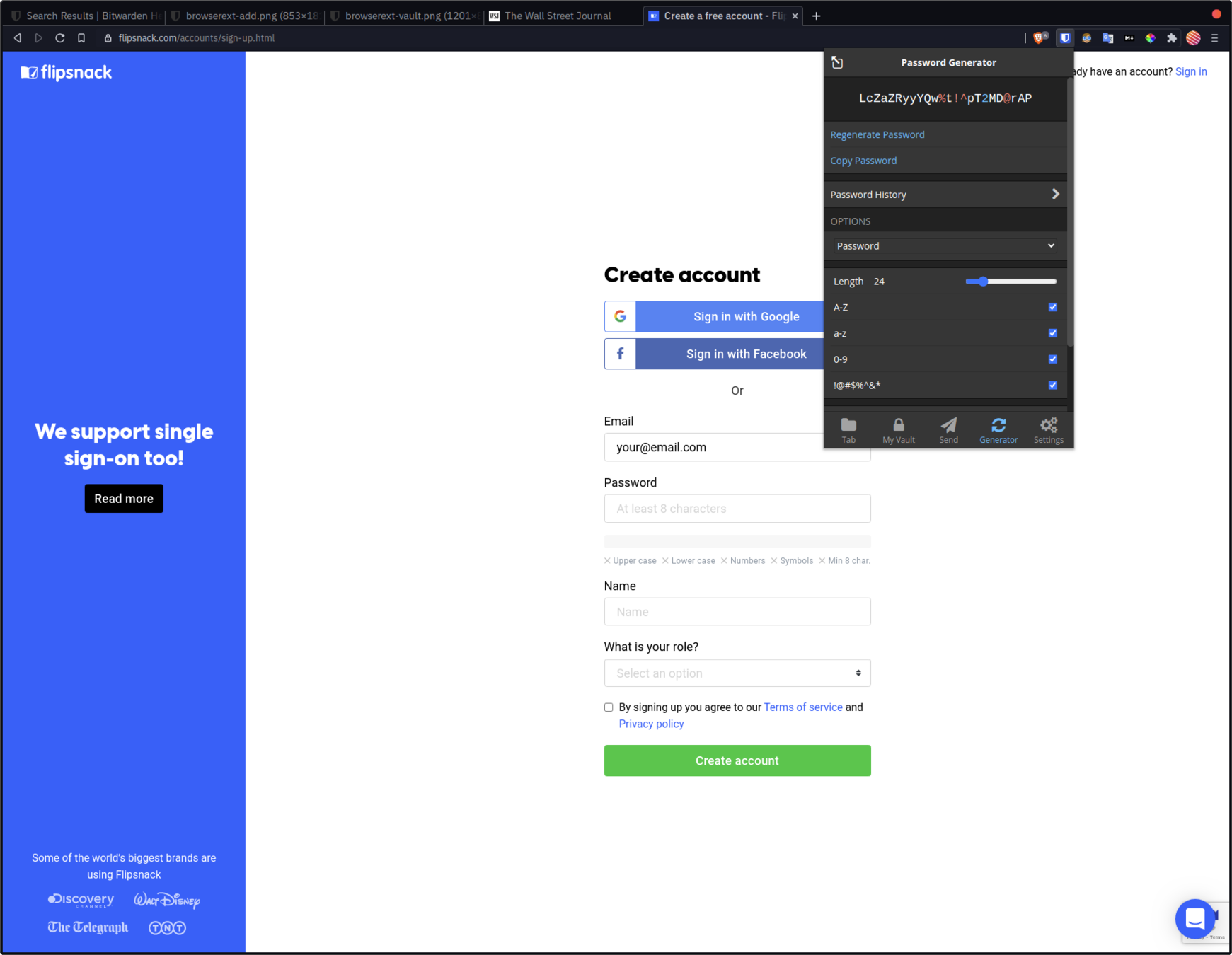
Login flow with BitWarden
4
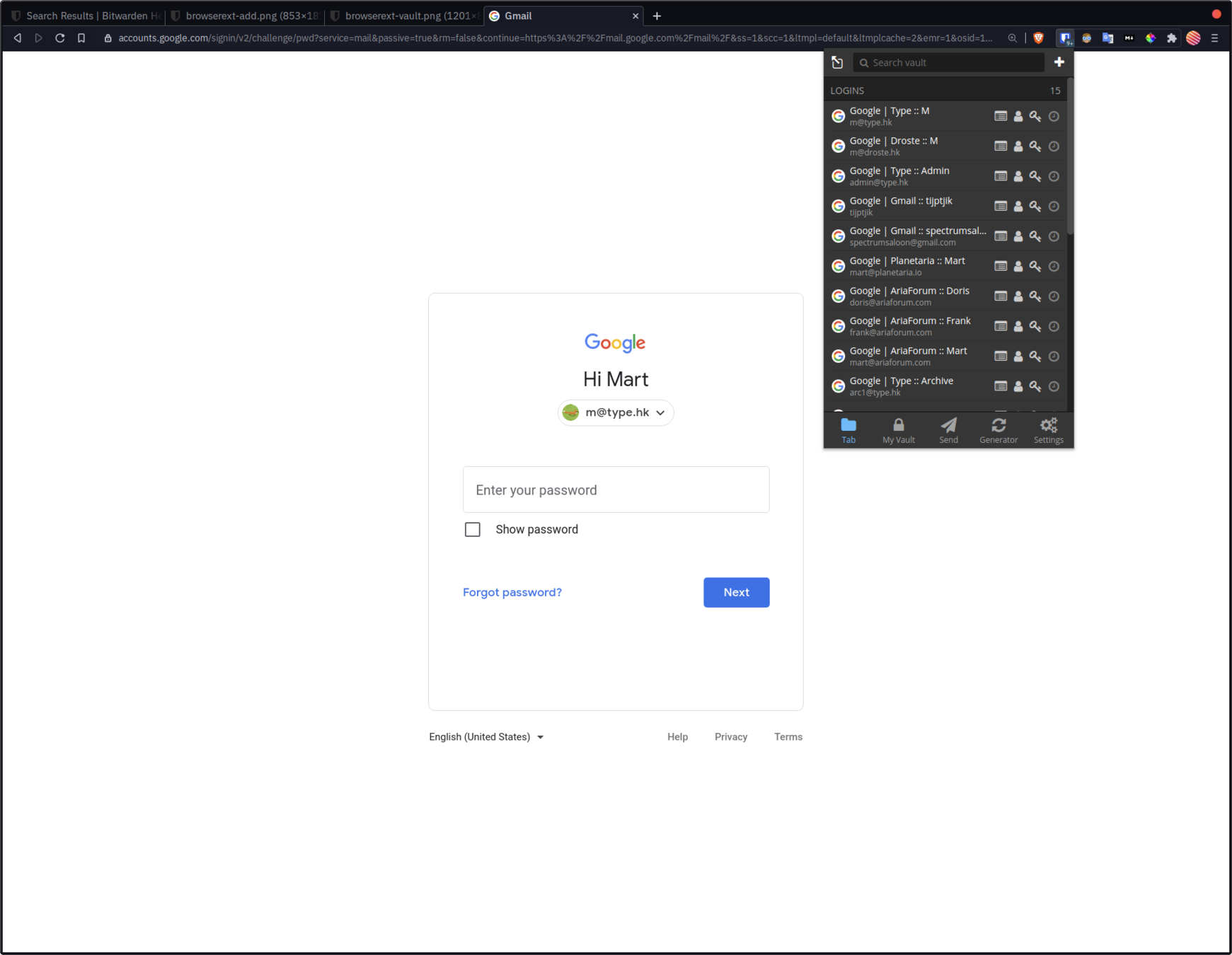

Let's get you setup with
Select matching logins from keyboard
Install Mobile App
1
3
Setup Auto-fill
2
Set Options
4

BASIC SETUP & USE
- Open the iOS Settings app on your device.
- Tap Passwords.
- Tap AutoFill Passwords.
- Toggle AutoFill Passwords on and tap Bitwarden in the Allow Filling From list:
- Disable any other Auto-fill service (like Keychain)
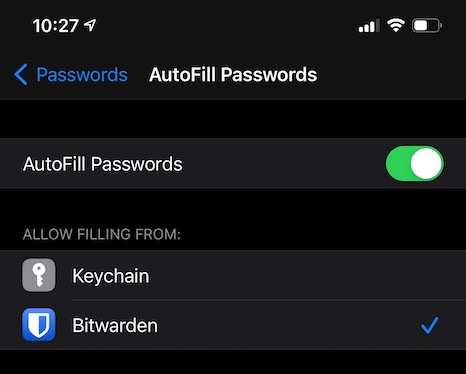
Setup Auto-fill
2
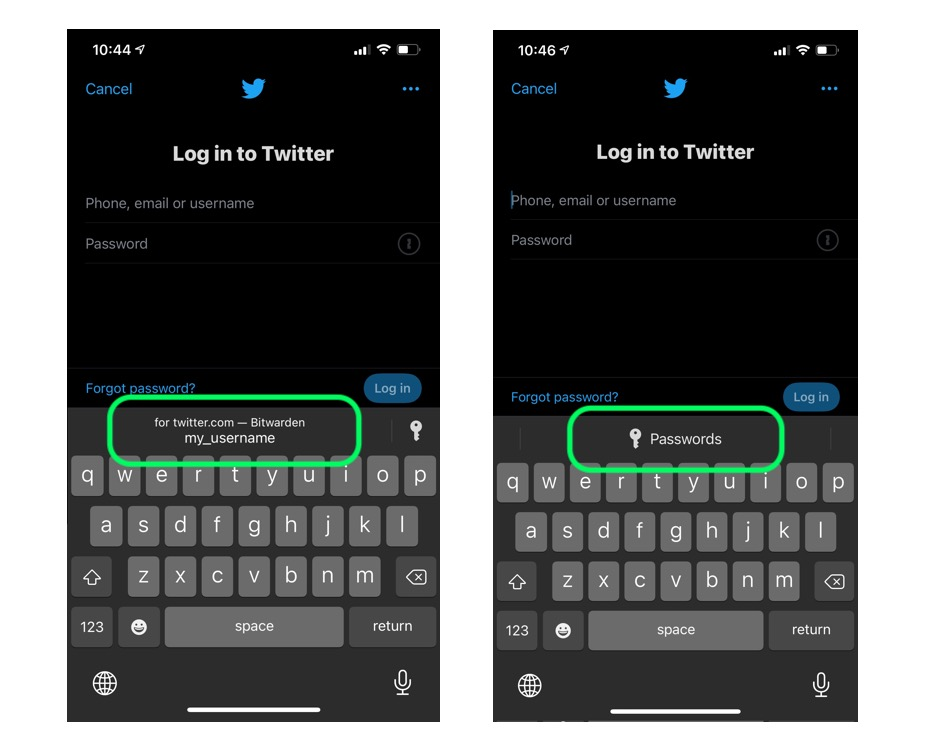
USE : Select matching logins from keyboard
3
Set Options
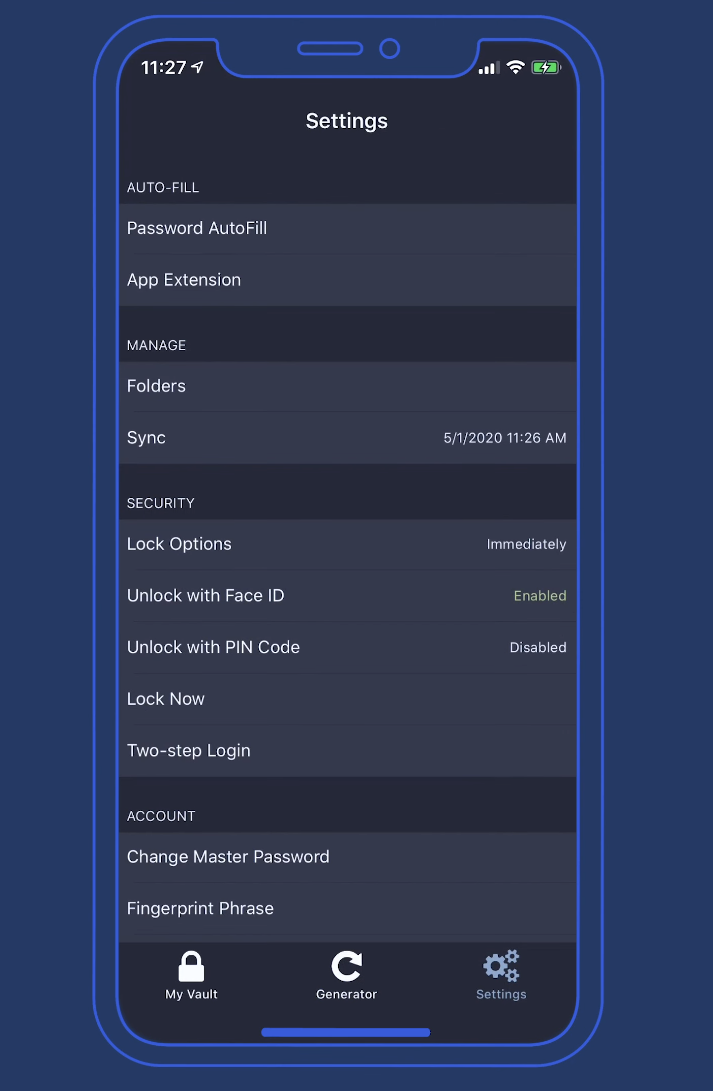
4
- Lock Options : Immediately
- Unlock with FACE ID : Disabled
- Unlock with PIN Code : Enabled
- Two-Step Login : Enabled
HTTPS / 2FA Reports
Import passwords from other managers
1
3
Password Reports
2
Data Breach Reports
4

... THERE'S MORE
Support for Timed - One Time Passwords
5
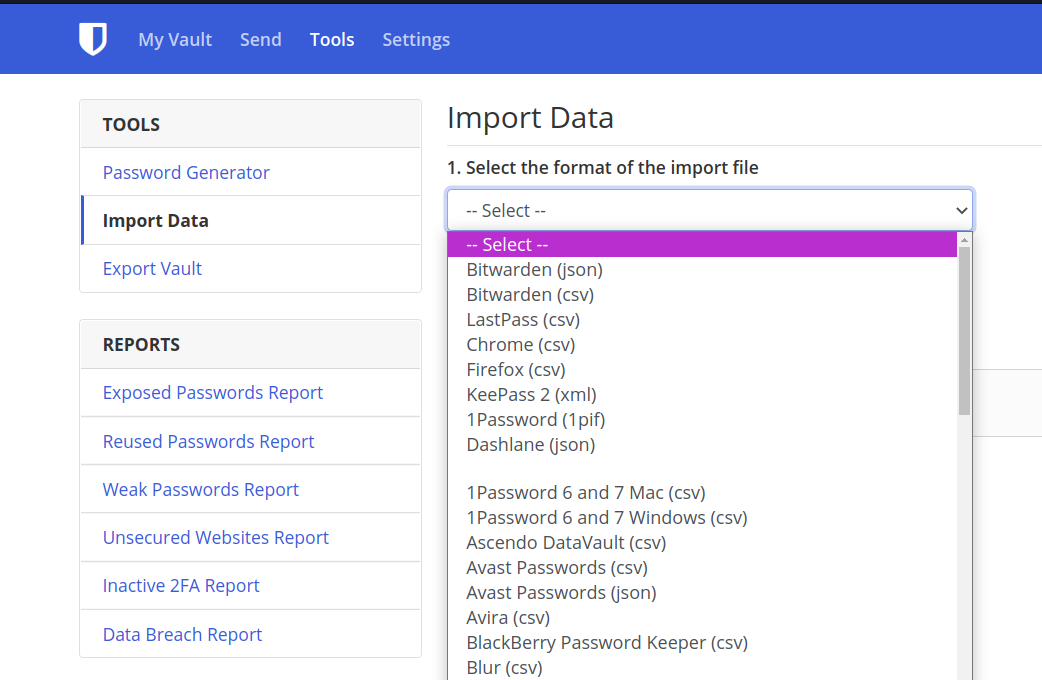
Import passwords from other managers
1
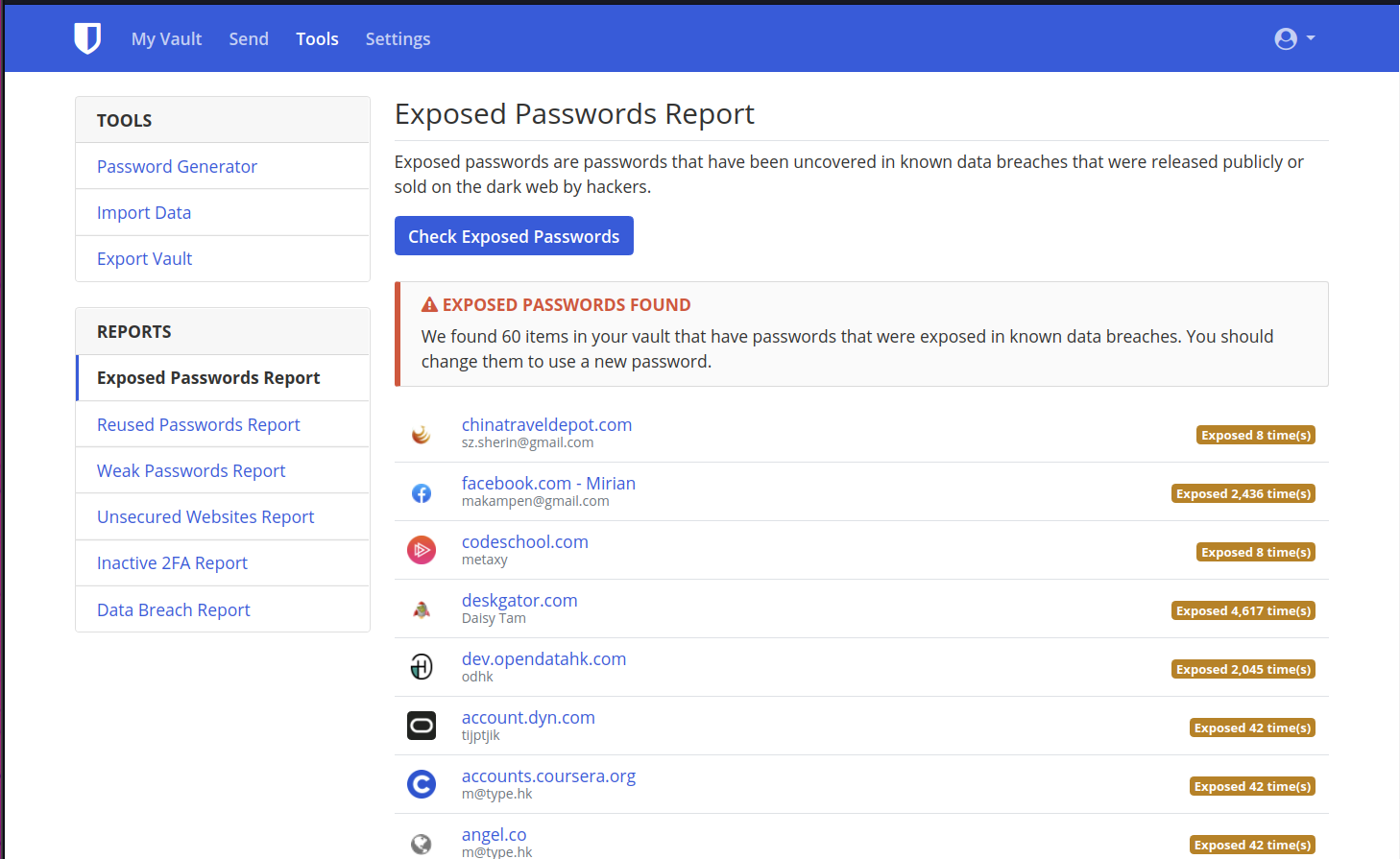
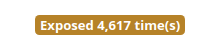
Password Reports
2
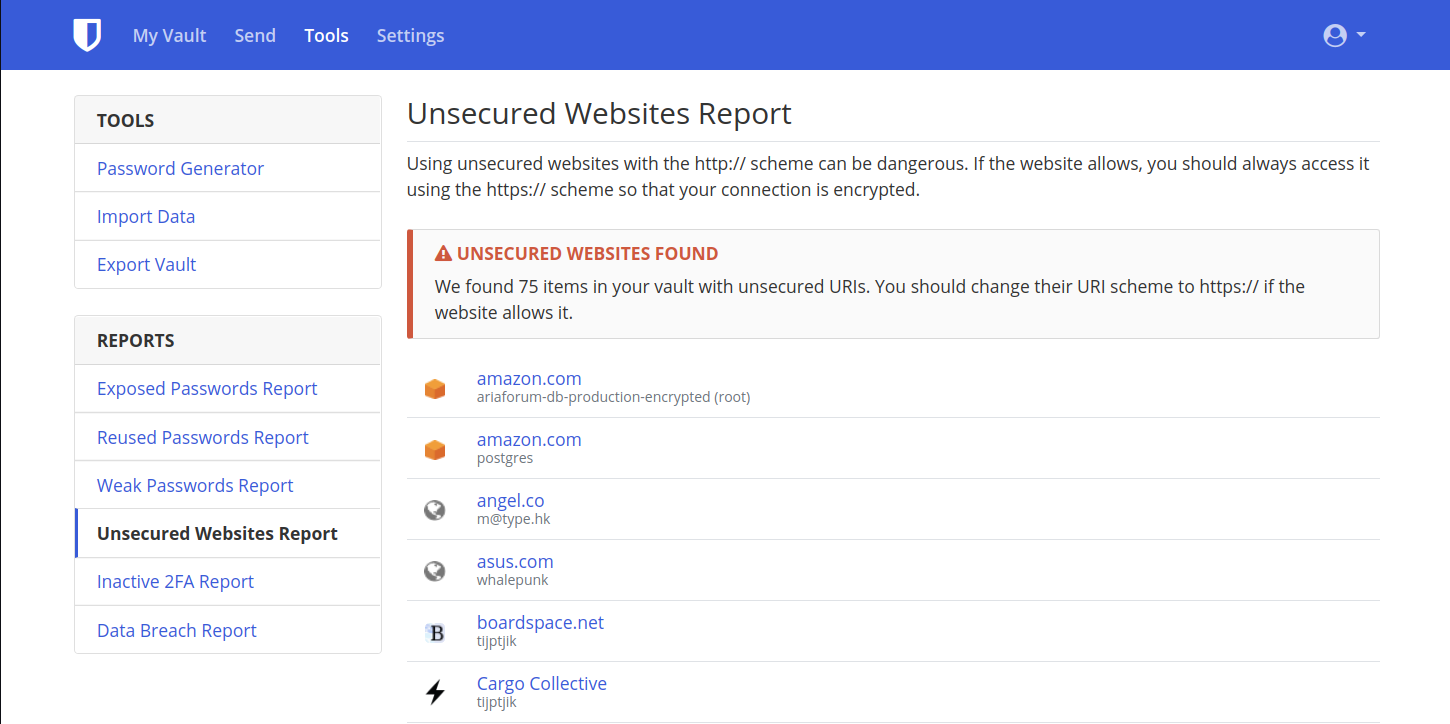
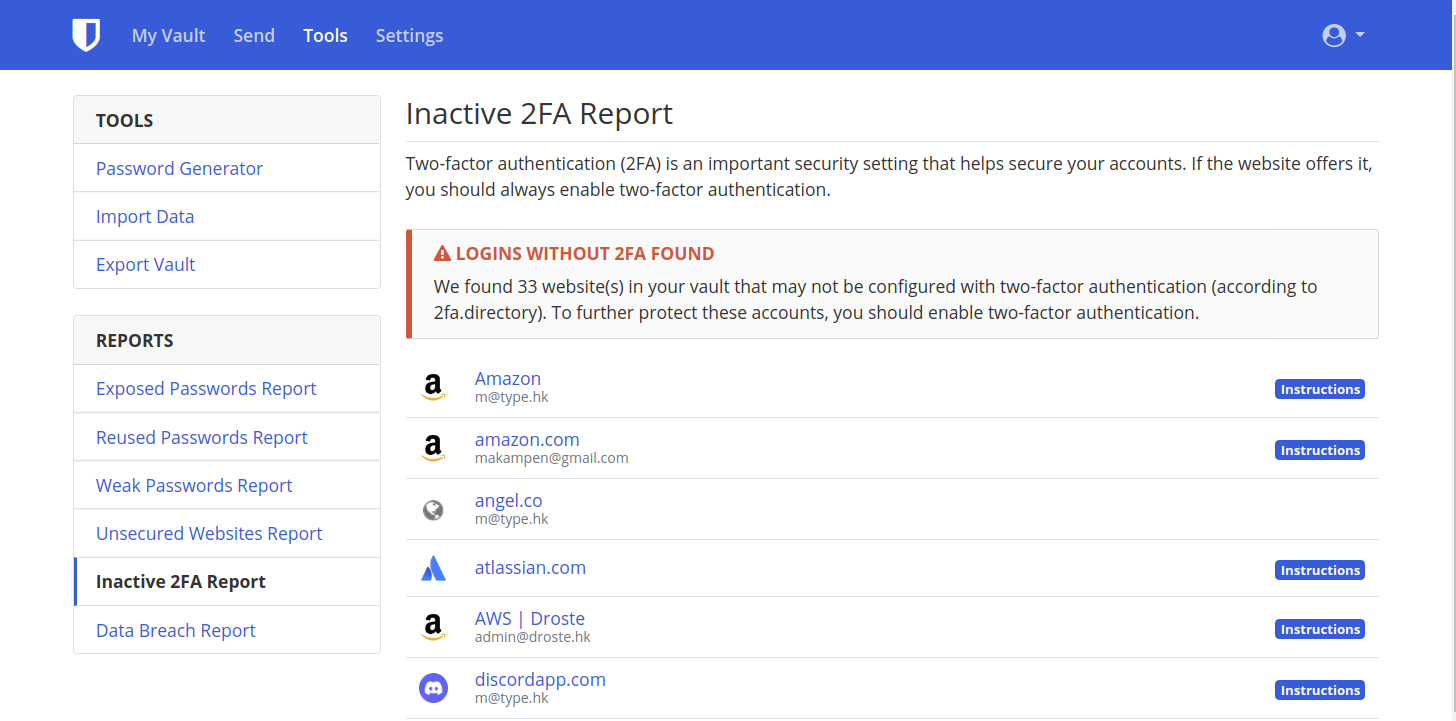
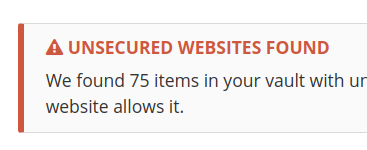
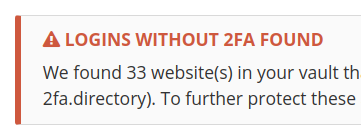
HTTPS / 2FA Reports
3
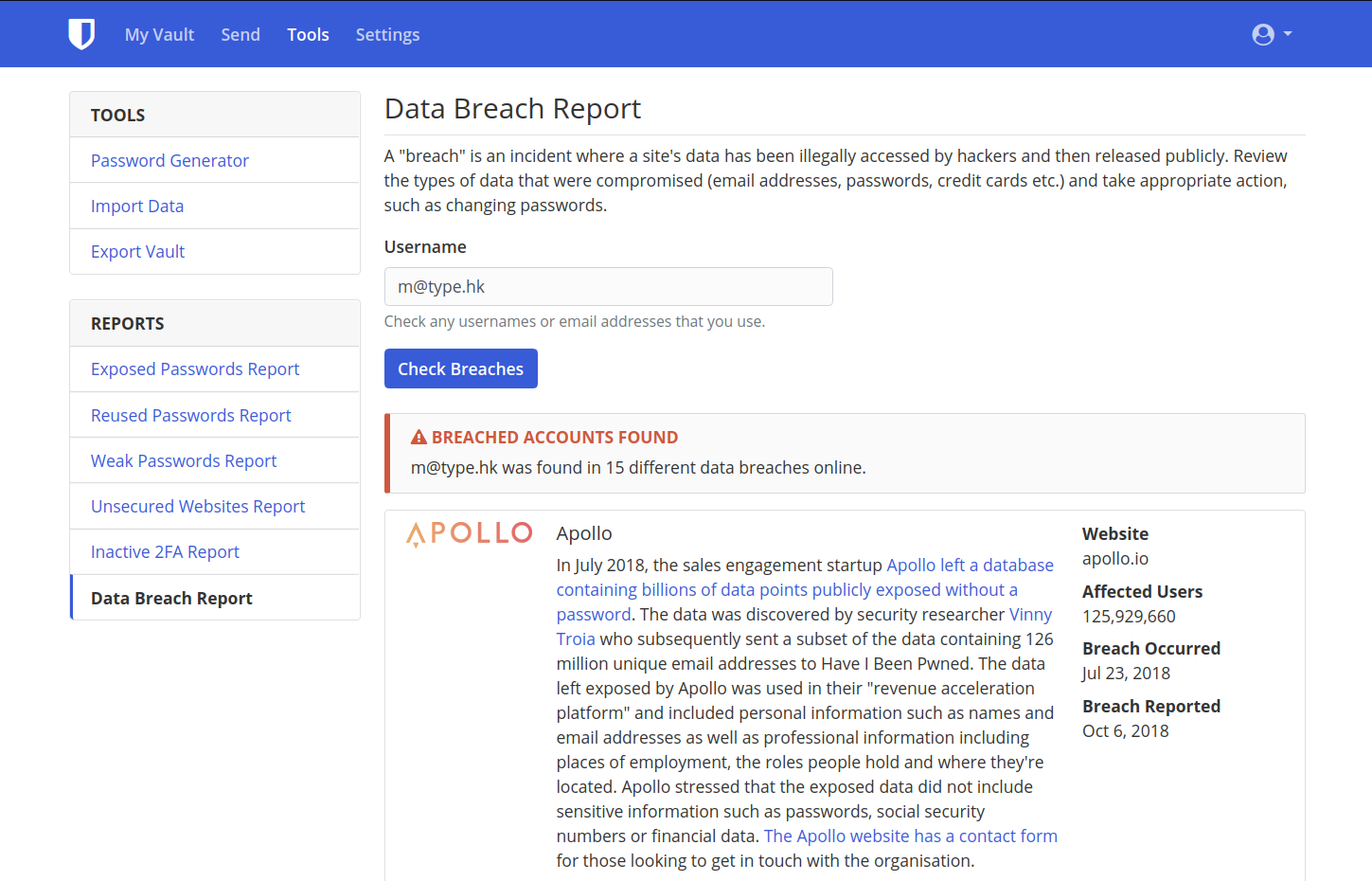
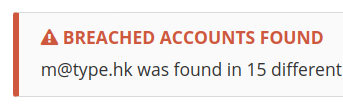
Data Breach Reports
4
BitWarden Authenticator (TOTP)
5
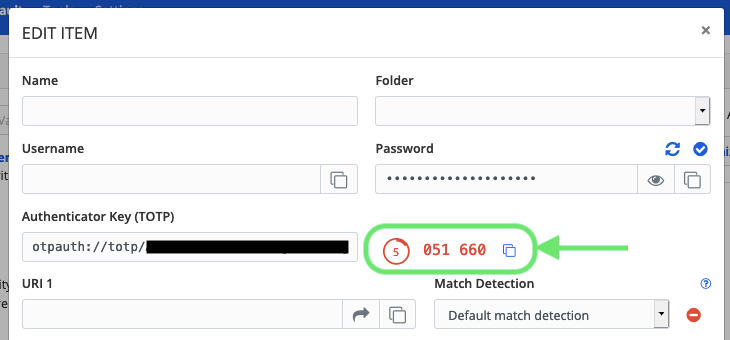
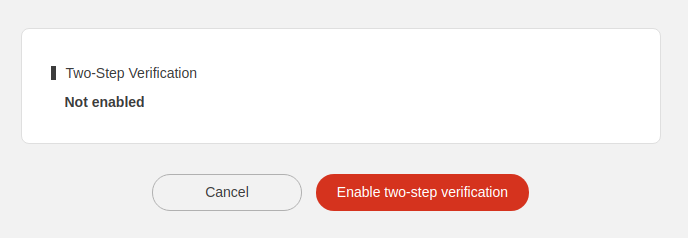
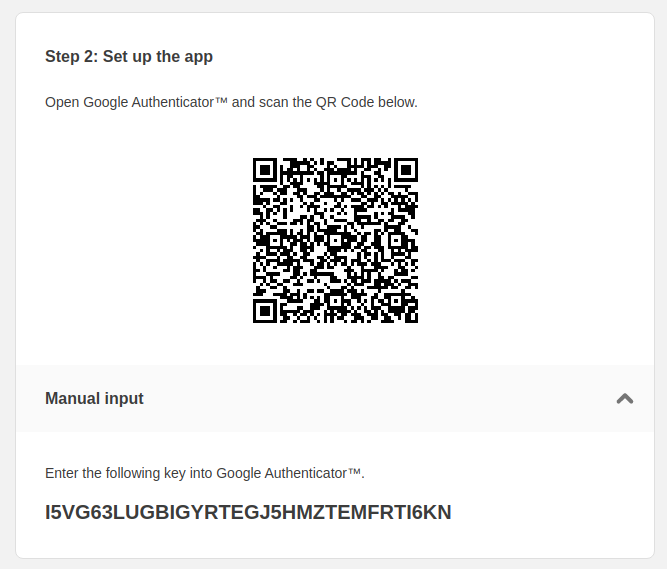
KEYS

FIDO U2F

No Software
Second Factor
1
6
Touch based
2
3

FIDO |
U2F |
Universal
Two
Factor
Fast
IDentity
Online
Durable
FIDO U2F KEY
Phishing protection
4
Privacy by design
5


Log in to supported service
1
How to setup
Indicate you
wish to use a
"U2F" key as
another factor
2
Tap the metal
circle 🔑 pad when prompted
3
Your account is
now tied to your
FIDO U2F key
🎉


Log in to a supported service
1
How to use
2
Tap the 🔑 pad when prompted
🎉


Supported Services













Let's set you up!

Let's set you up!
Let's set you up!
with
Let's set you up!

Let's set you up!
Let's set you up!
with

1. Store your Recovery Code
in a secure location

2. Link this BitWarden account to
your personal FIDO U2F Key
3. Enter your Master Password
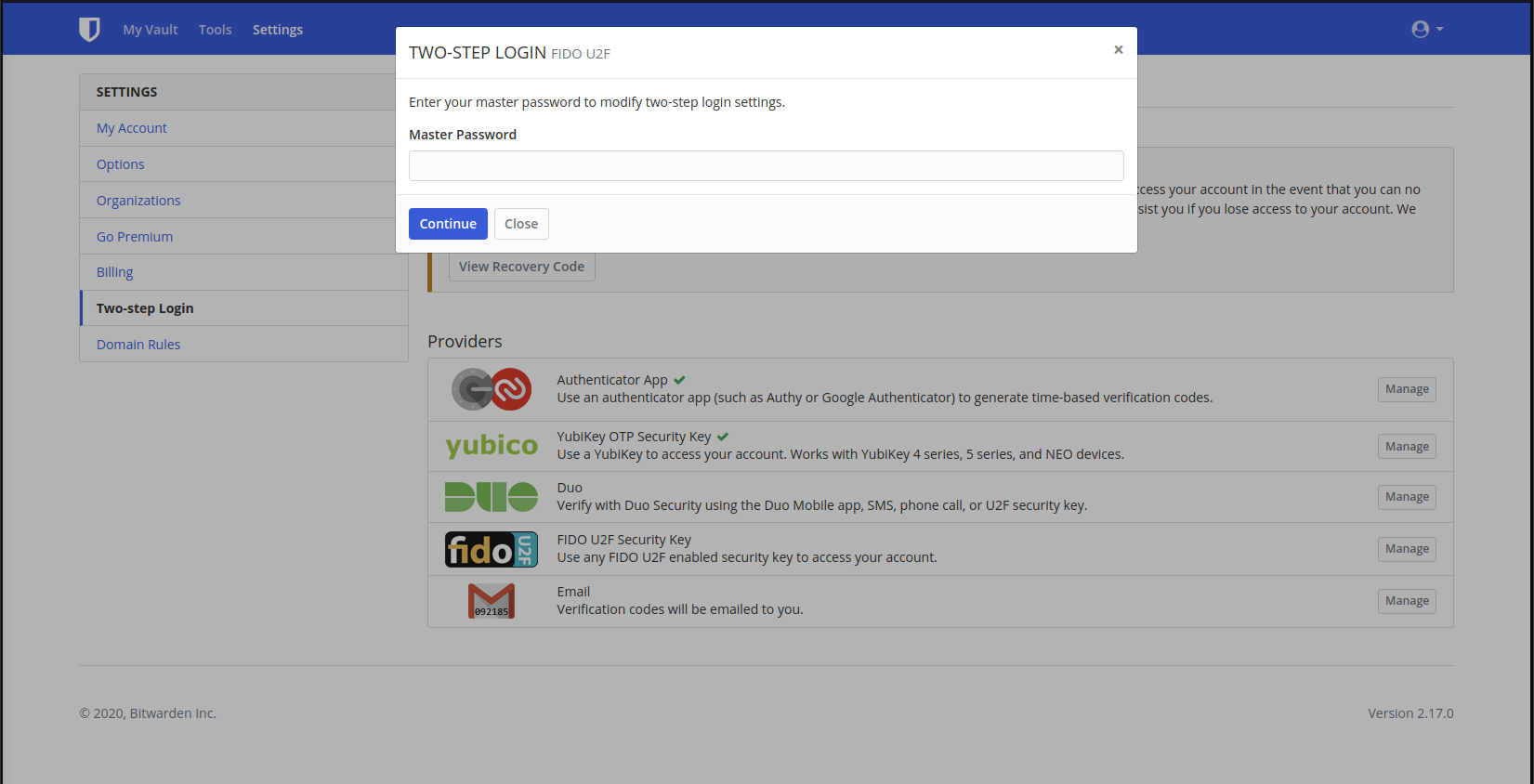
4. Provide a Name - e.g. "Office Key" and click "Read Key" when you're ready to touch the key pad
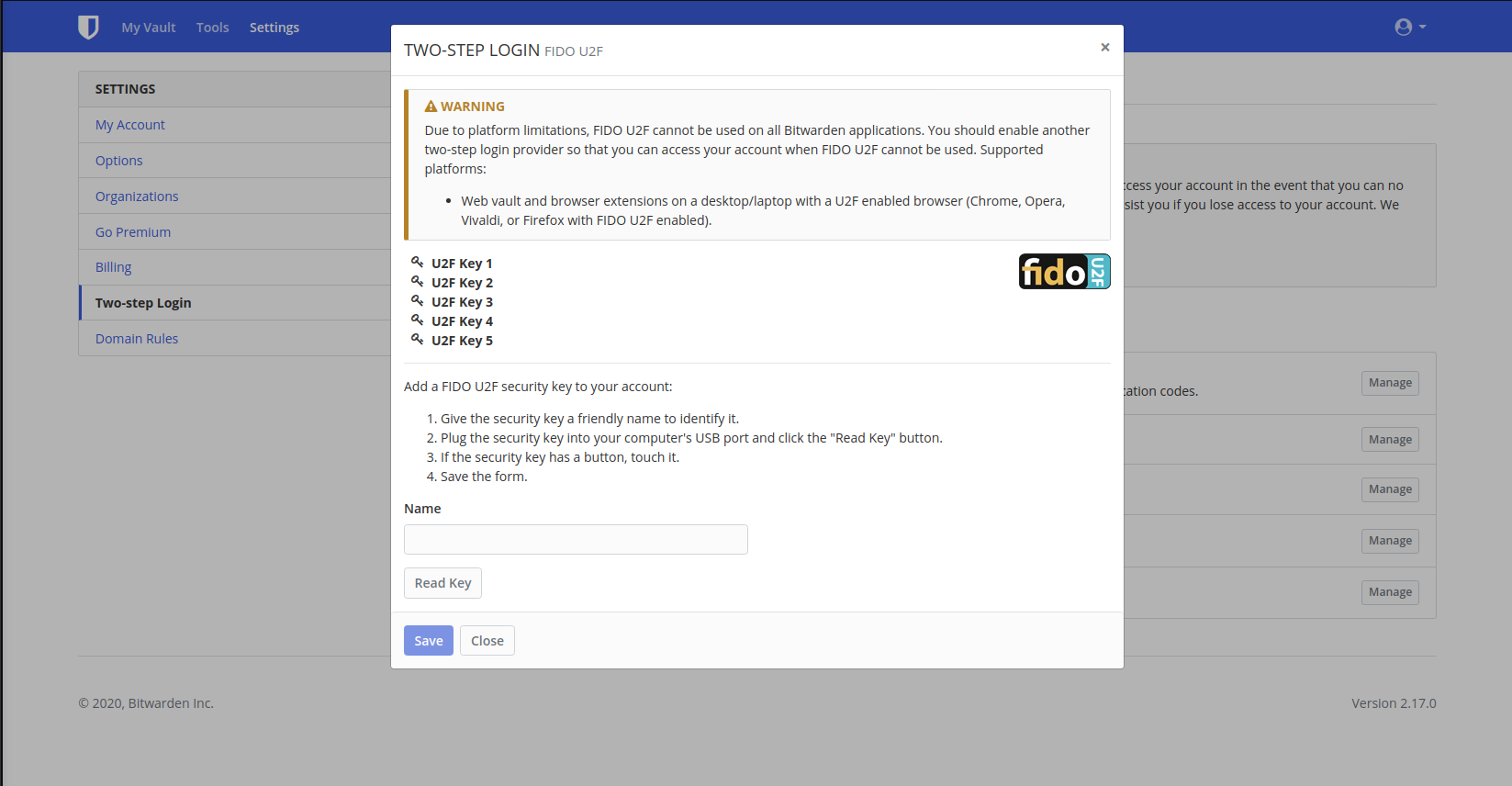
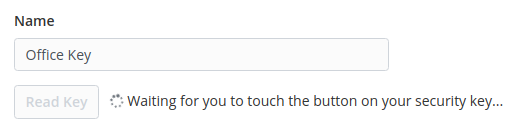
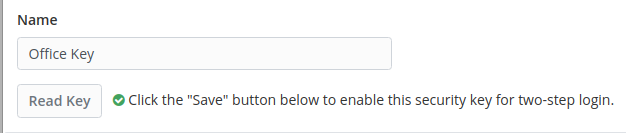
5. After clicking save,
your key is now registered
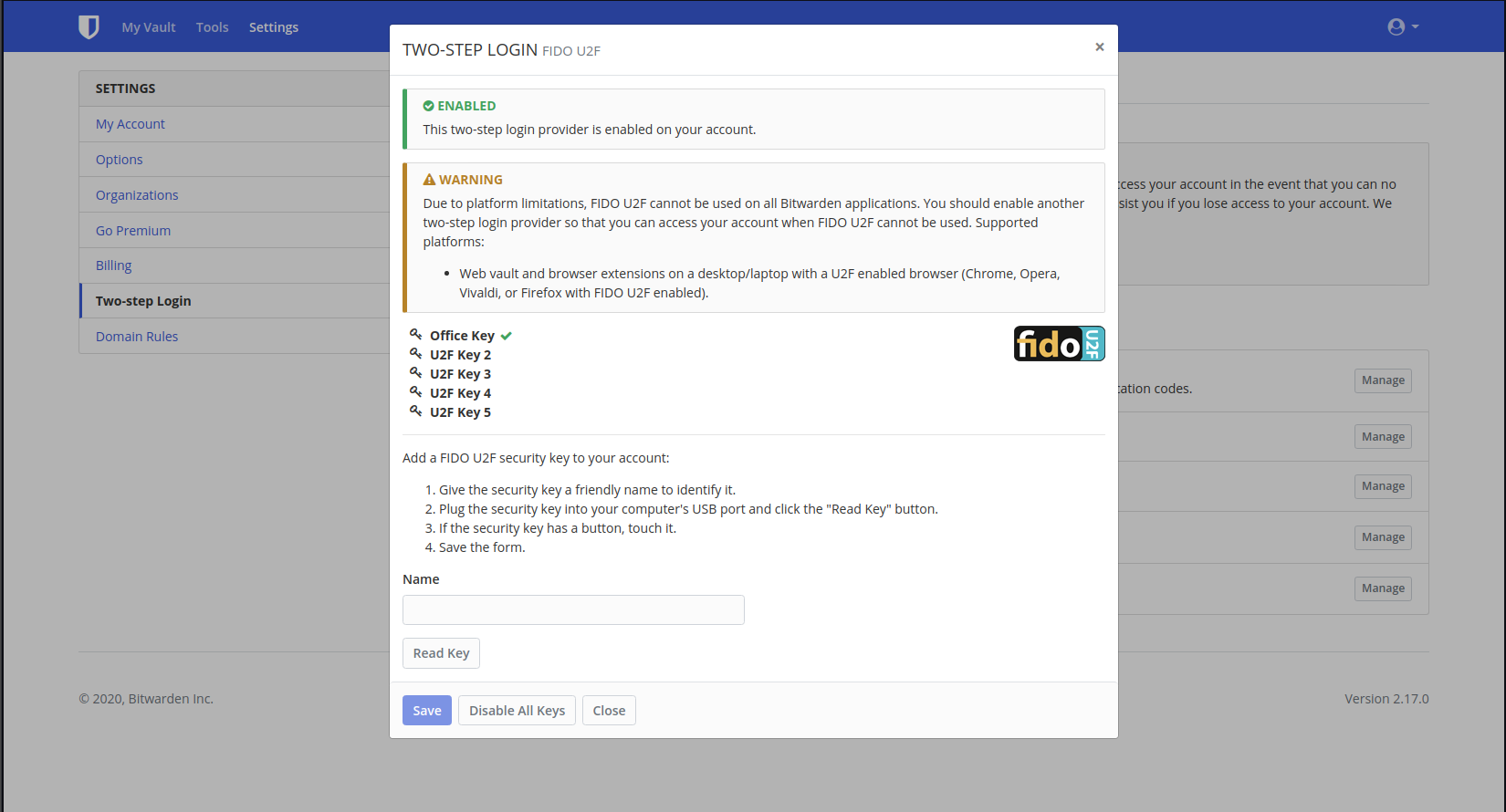


Let's set you up!

Let's set you up!
with
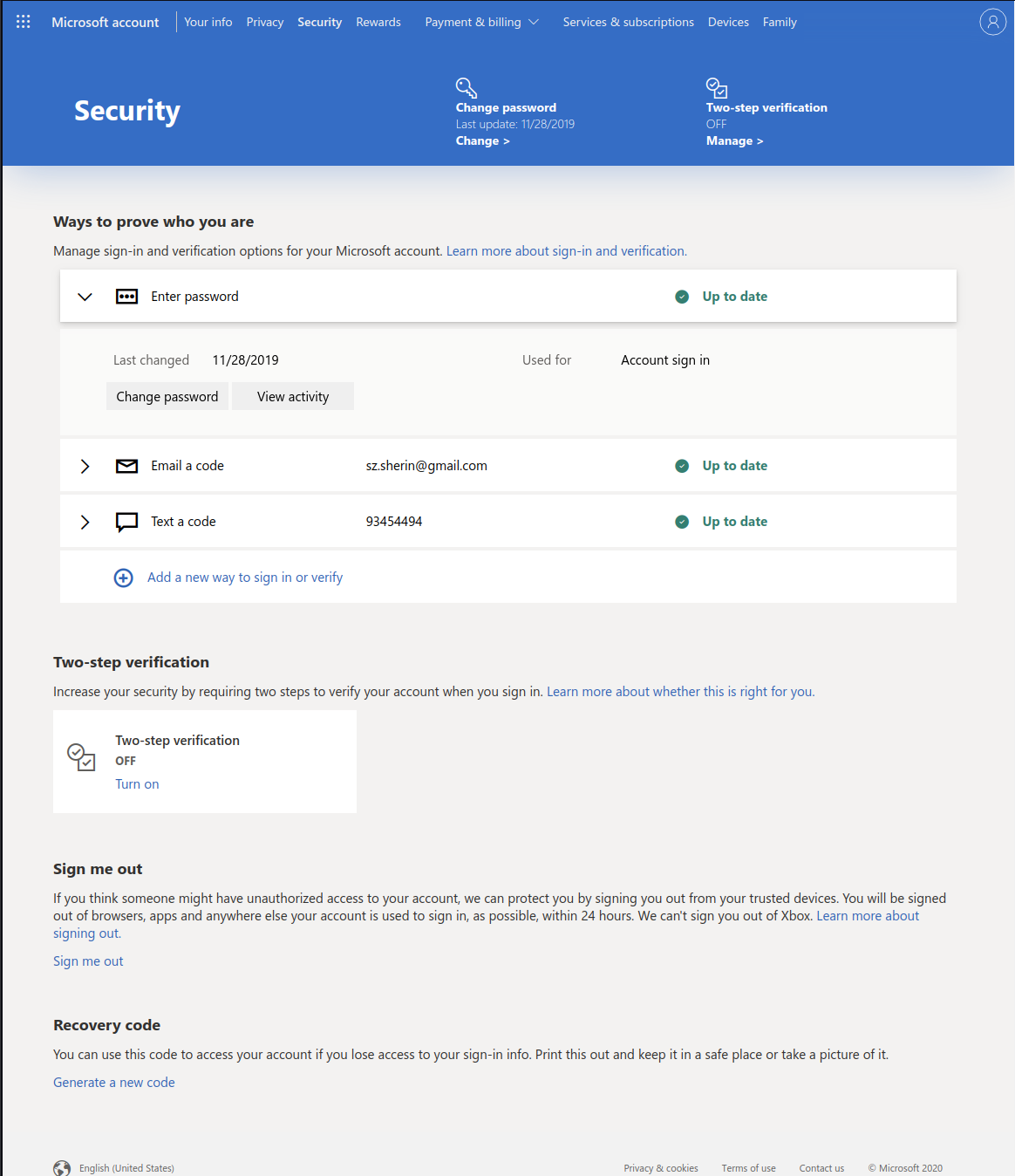
U2F
2FA

1. Store your Recovery Code
in a secure location

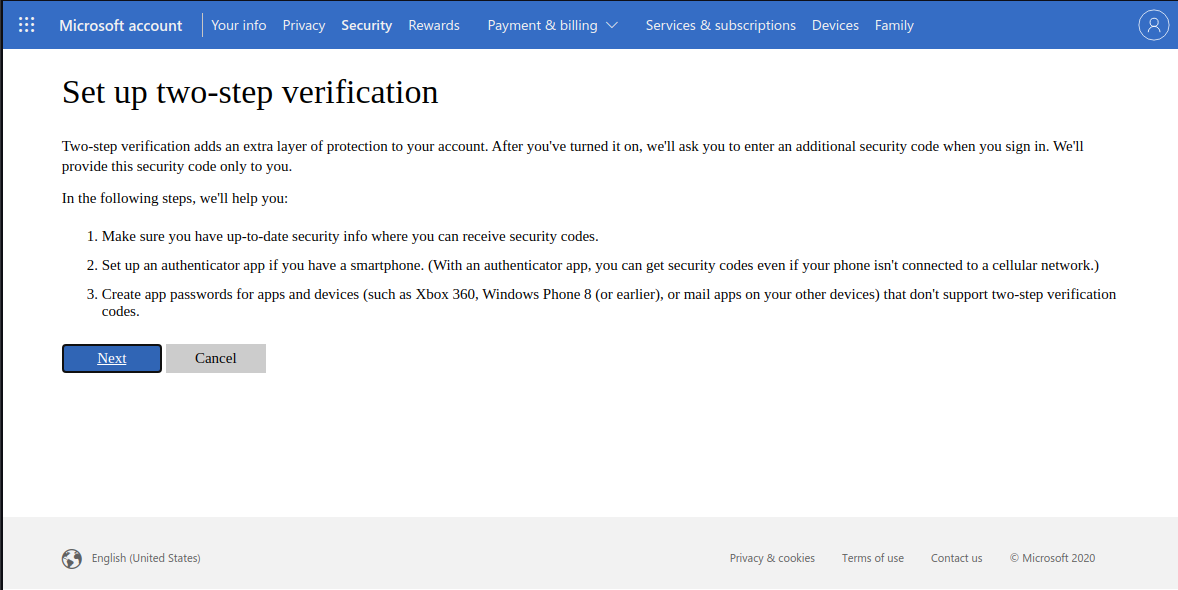
2. Turn on two-step
verification
3. OK, Microsoft
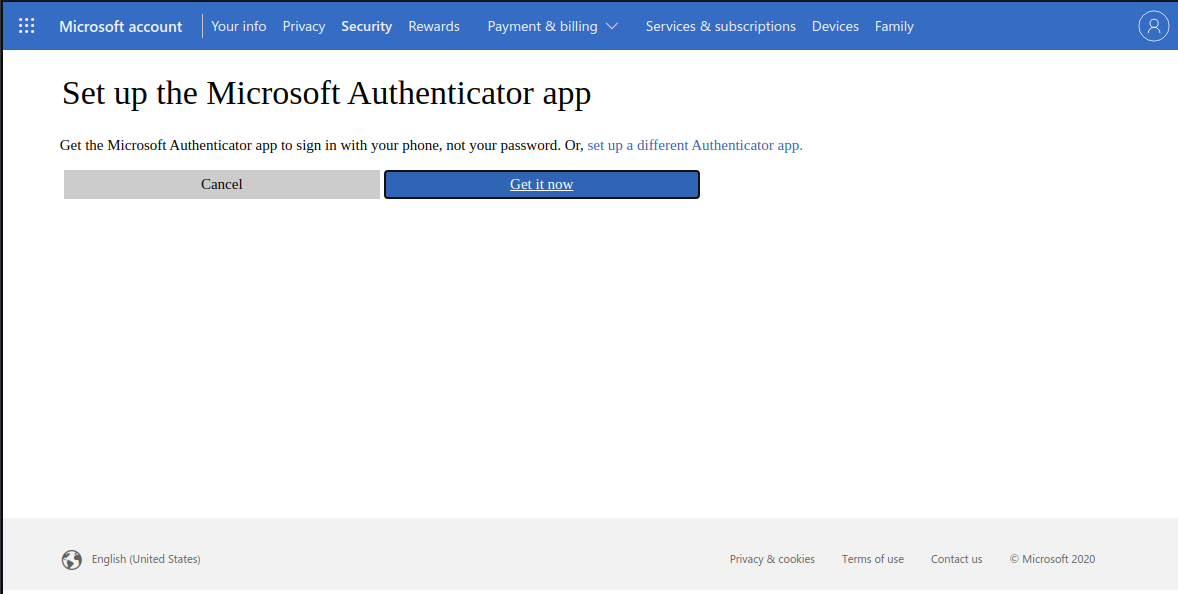
4. We will use Authy or BitWarden's built-in authenticator
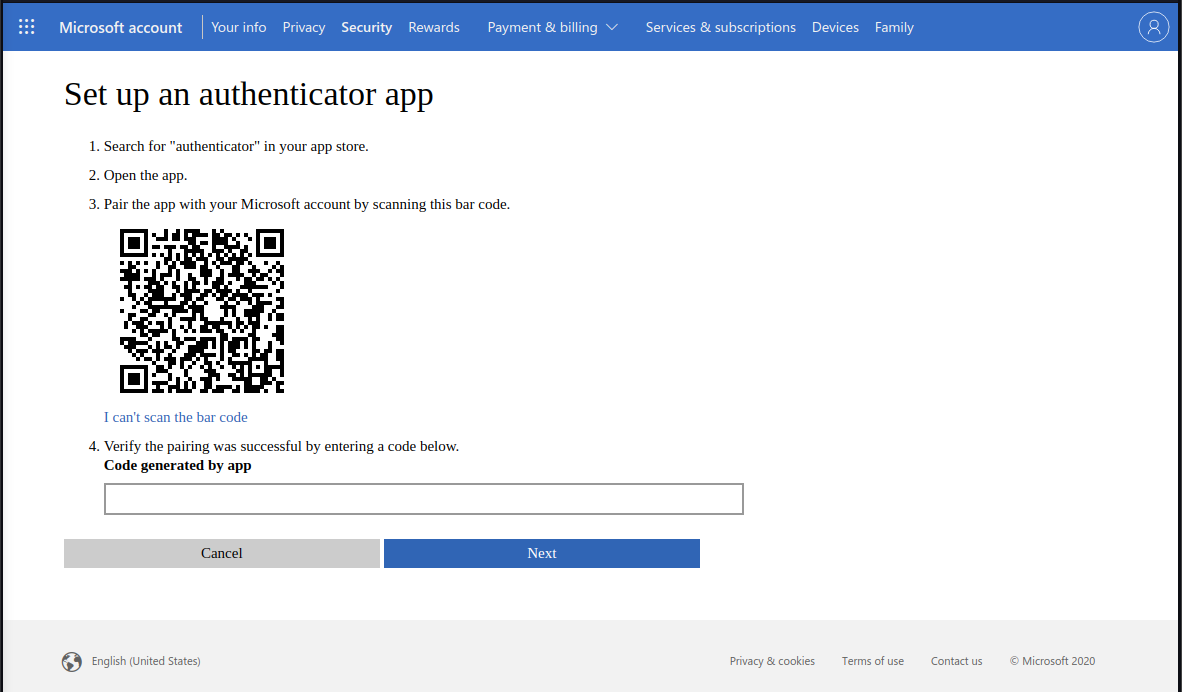
5a. Authy : Scan the QR code with the
authy app installed on your phone, and provide the generated code (TOPT)
5b. BitWarden : Click "I can't scan the bar code" and provide the Secret Key
to the OTP section in the login profile
6. If you are syncing your Outlook.com
email to your phone, follow the
respective instructions for your OS
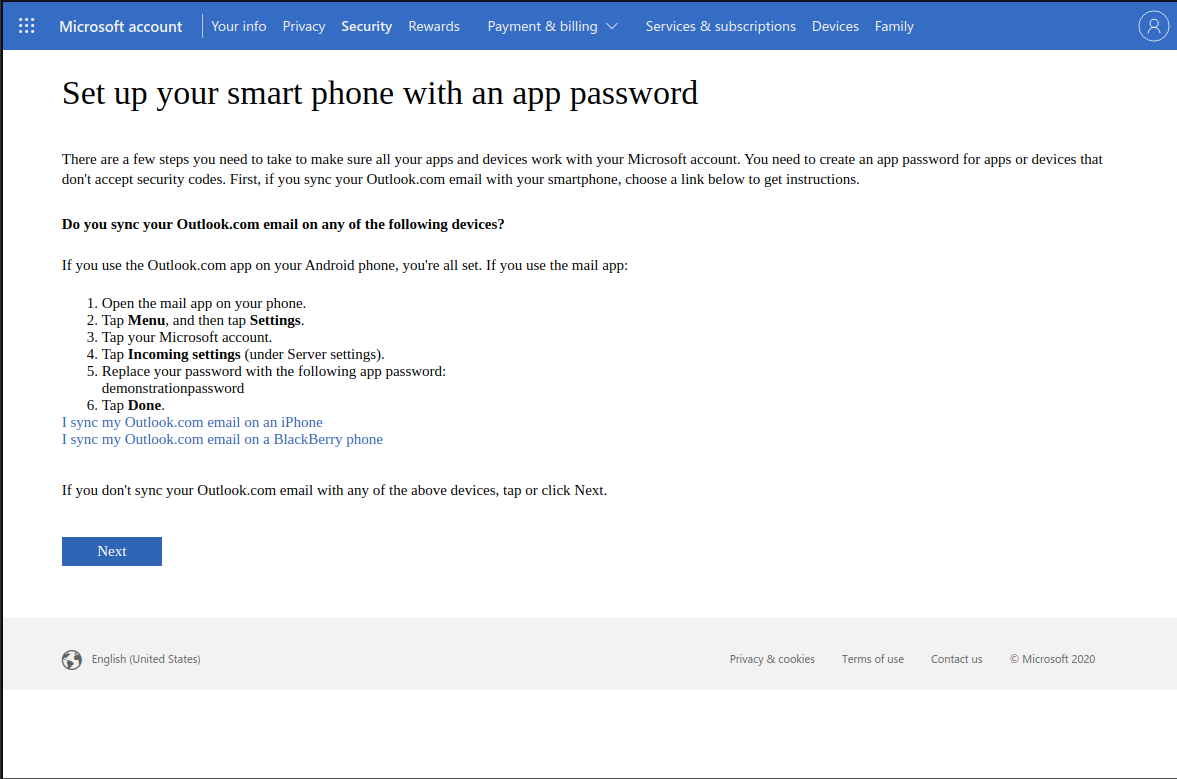
Click "Next" when done, and "Finish" on the next page.
You'll be logged out and required to log in again.
Two Factor Authentication is now
turned on for your Microsoft account
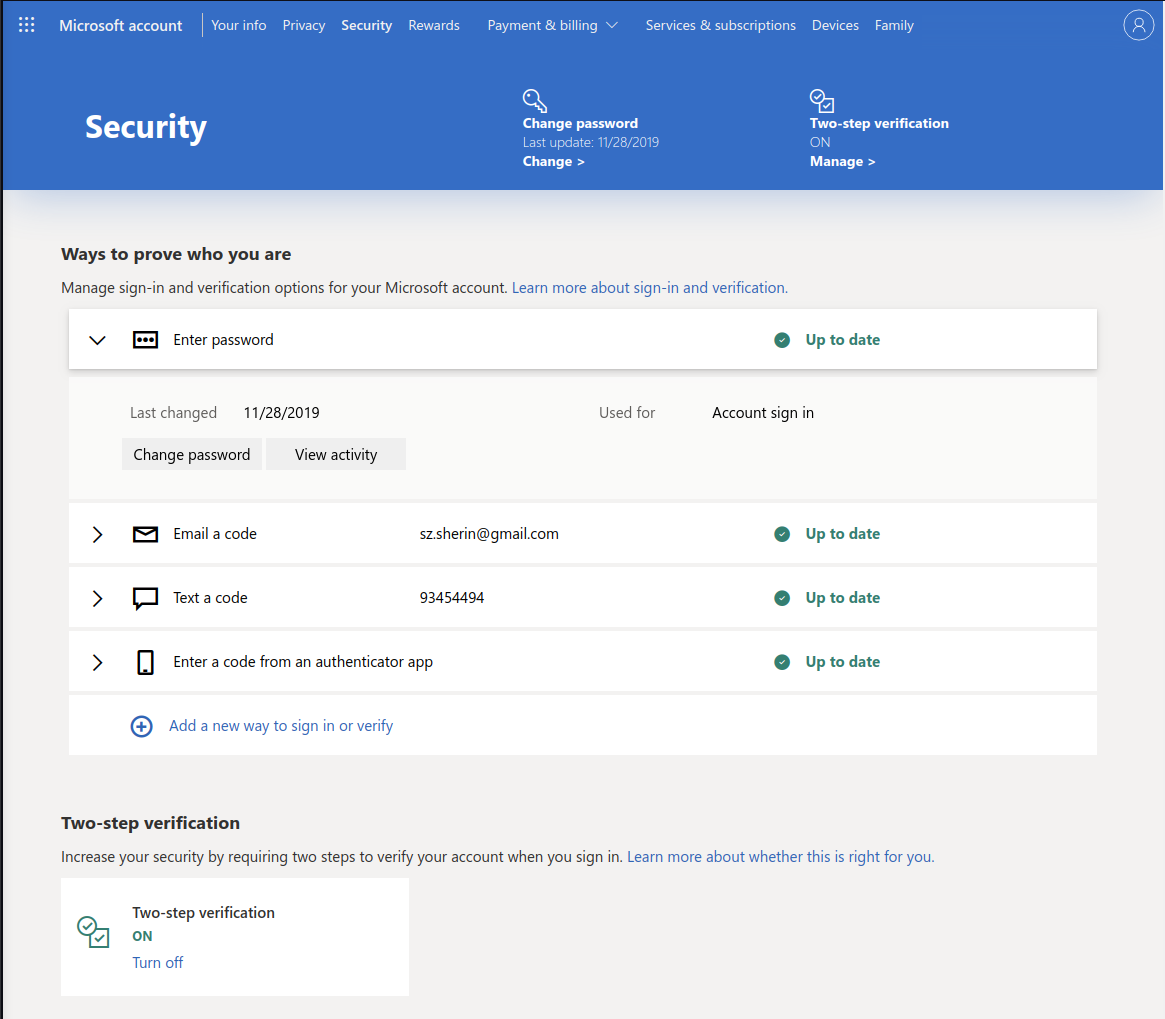
ENCRYPTION
share secrets
confidentiality
... in transit
confidentiality
... at rest

trust sources
How can we encrypt files on MacOS?
Use VeraCrypt on MacOS
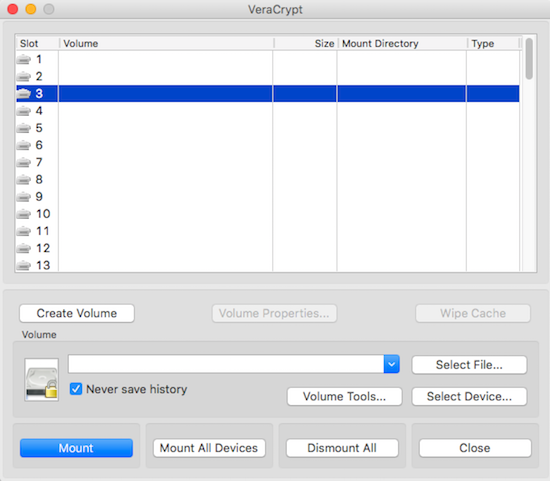
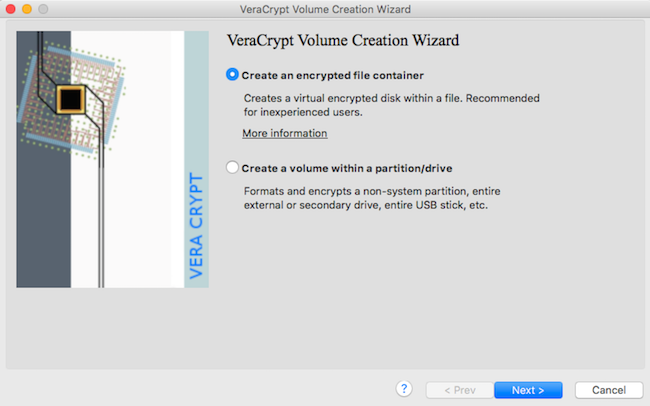
Launch VeraCrypt app
1
Create Volume
2
Use VeraCrypt on MacOS
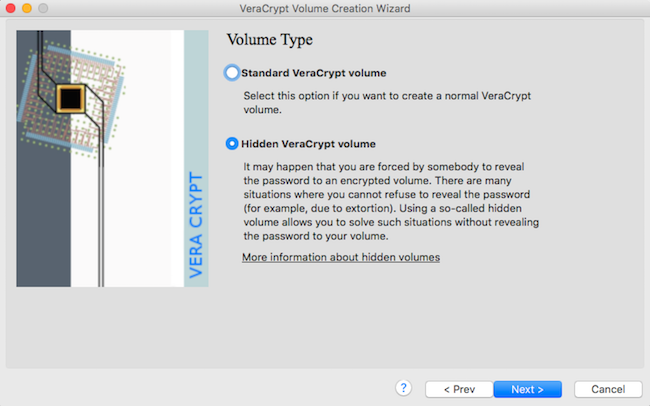
Select the "Hidden" option
3
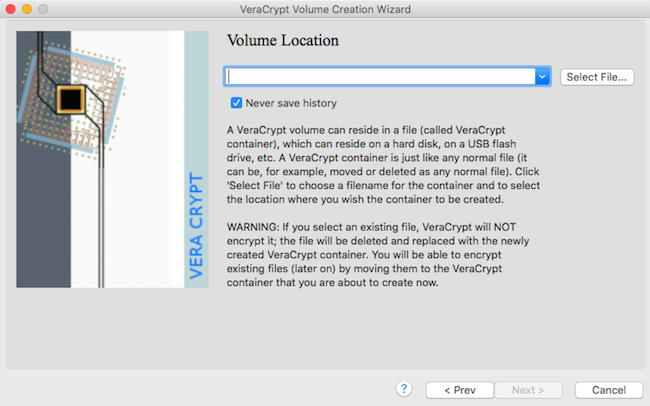
Select any location for the Volume and use any name
4
Use VeraCrypt on MacOS
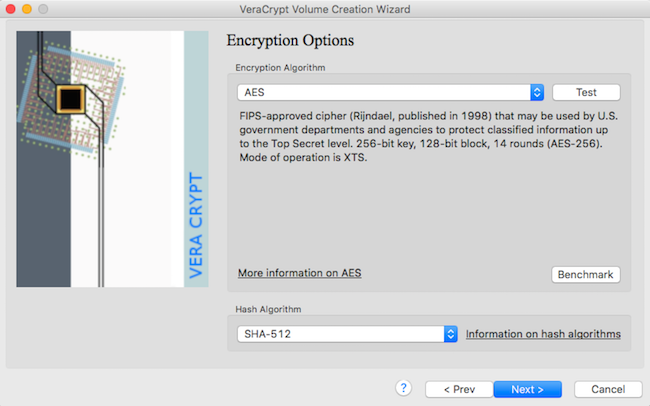
Leave the default algorithm
5
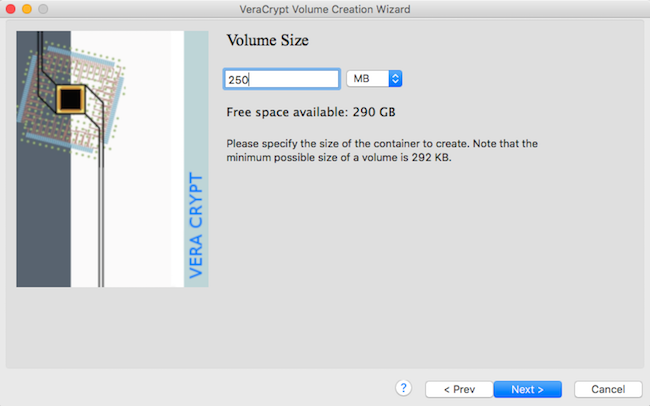
Choose size that can contain both presumed and true sensitive files
6
Use VeraCrypt on MacOS
Create a memorable password - not a BitWarden generated one
7
Select "exFat" as format Option, then move the mouse until half the bar is green, then Format
8
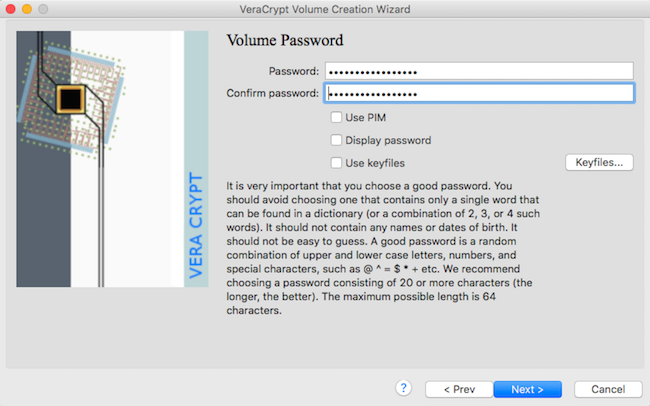
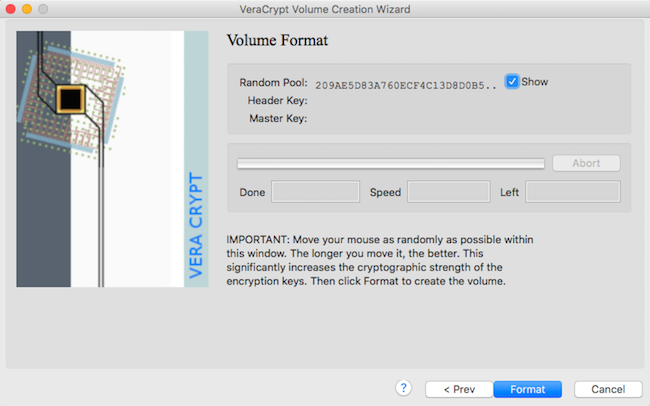
Use VeraCrypt on MacOS
Click next to repeat steps for the hidden volume, and choose a size for sensitive files
9
Generate secure password with BitWarden and use it
10
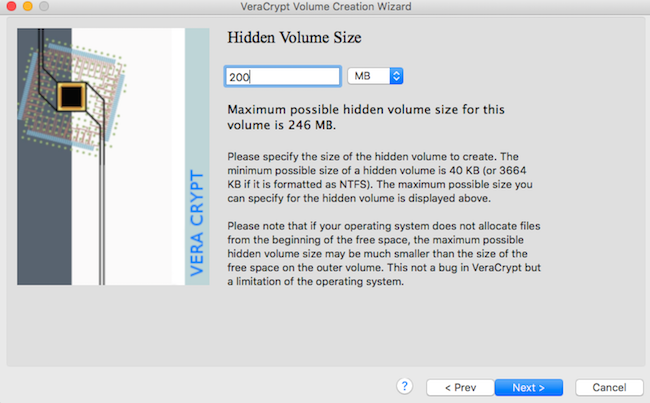
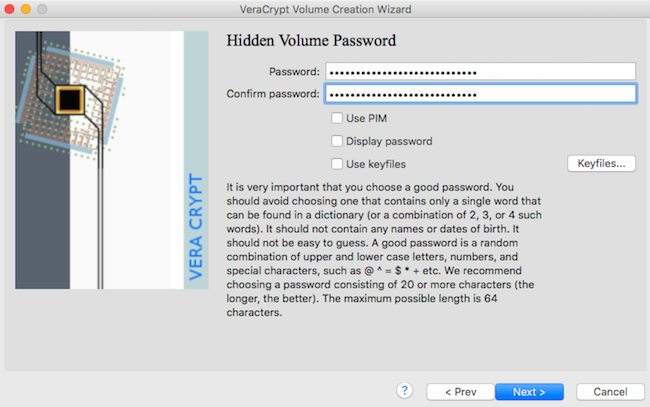
max size is incorrect !!
Use VeraCrypt on MacOS
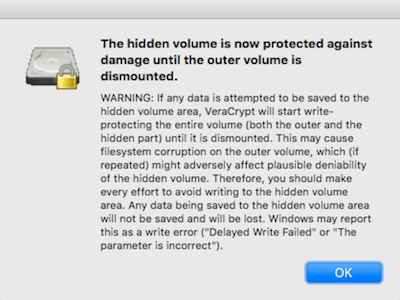
If you were successful, you should see this modal with a warning message
11
Click "next" and "exit" - you're ready to mount your volume!
12
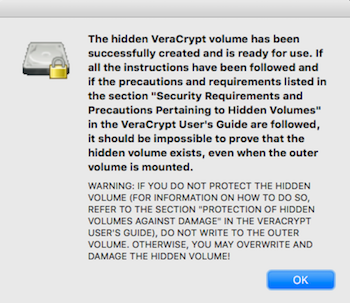
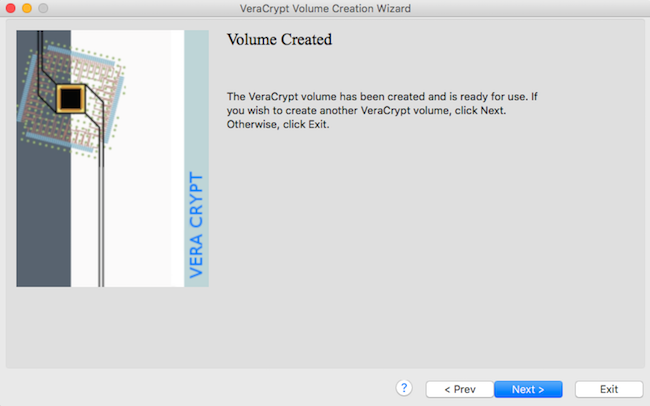
don't damage hidden volume !!
Use VeraCrypt on MacOS
Launch VC app, select a slot ,"Select File" to locate your volume, and mount it
13
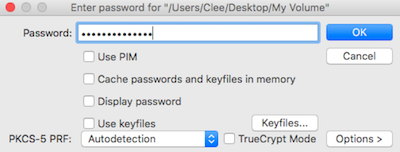
Enter your 'memorable' password for the decoy volume, and your BW pass for the hidden volume
14
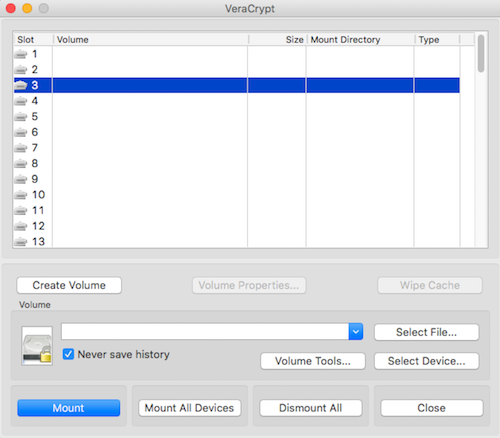
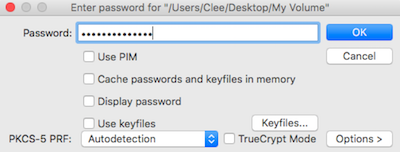
Use VeraCrypt on MacOS
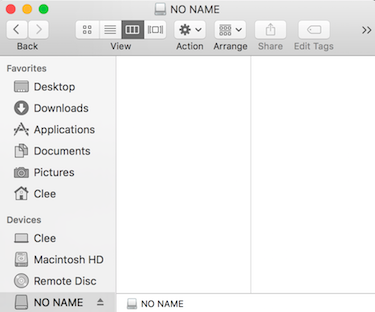
If successful, it will show up as mounted - double click to open in Finder
13
Place your decoy / sensitive files into the volume with it's mounted
14
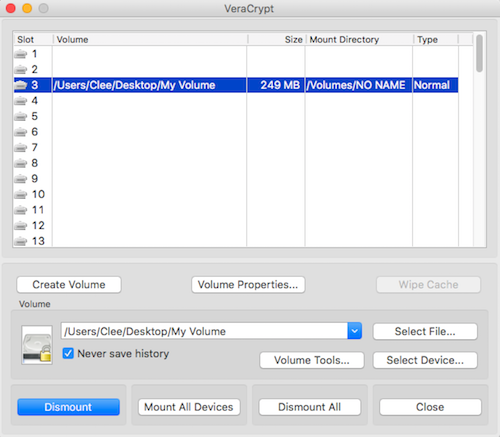
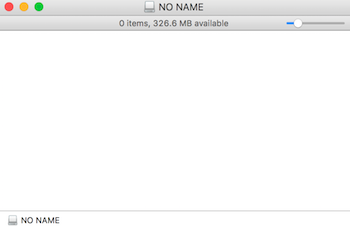
Use VeraCrypt on MacOS
Once you're finished working on the files, "Dismount" it.
15
Quit VeraCrypt when no longer in use
16

FINDER EJECT IS NOT ENOUGH !!
Use VeraCrypt on MacOS
Once you're finished working on the files, "Dismount" it.
15
Quit VeraCrypt when no longer in use
16

FINDER EJECT IS NOT ENOUGH !!

1
Delete files,
unless your cannot
2
When not in use, unmount VC volumes
3
Do not automount VC volumes
6
Create Traveler disks
for USB drives (WIN only)
5
practice quick dismounting
4
Uninstall VeraCrypt if moving through sophisticated security
1
volume equivalent in size to a 4K movie
2
name volume as movie
3
store it next to other real movie rips
6
disable recent file function
5
no shortcuts to hidden volumes
4
add "decoy" volume password to BitWarden
the.phantom.2018.x265.NAHOM.mkv
6
disable recent file function
disable recent file function
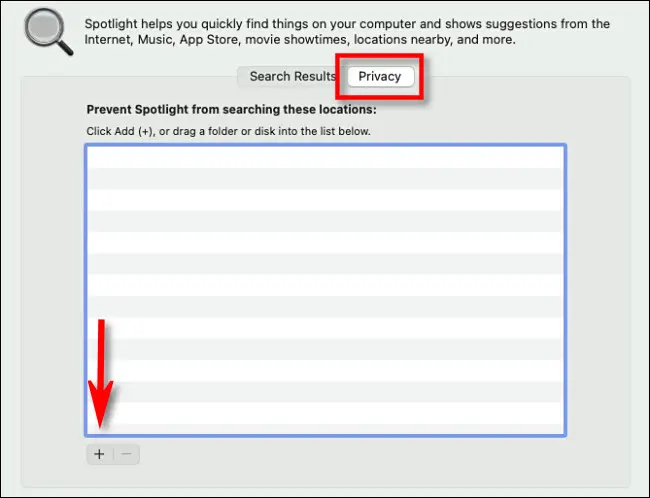
Spotlight settings
Add "Macintosh HD" to the list
pro tip: disable spotlight
6
disable recent file function
disable recent file function
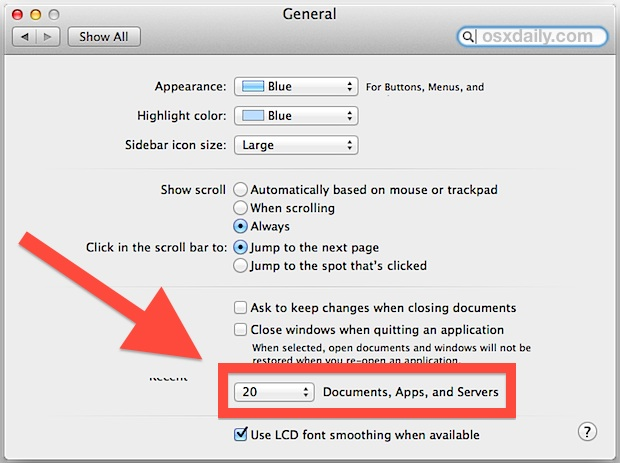
Setting to zero Finder's menu recent items count (via System Preferences > General) also sets to zero all Office applications' Open Recent... items count.
1
Be prepared to lose
your data instead
of revealing it
2
If cloud-based, use
differential sync
3
Backup your
volume
6
The passphrase can be changed if necessary
5
Dismount volume, before backing up
4
"protect hidden volume against damage"
4
"protect hidden volume against damage"
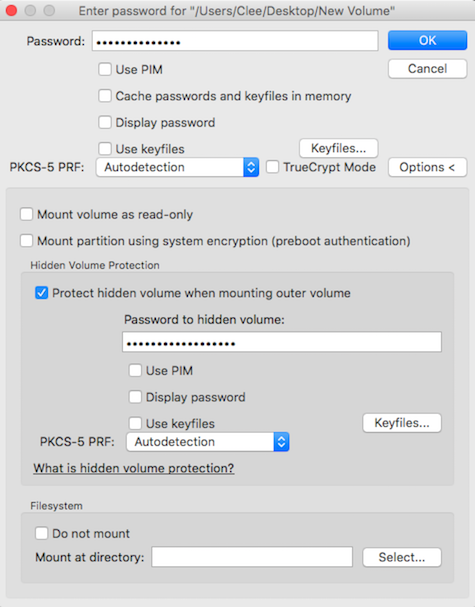
When mounting, enter decoy volume password, and select "Options"
select "When mounting, select "Options" and enter hidden volume password
4
"protect hidden volume against damage"
Read the warning carefully - TL;DR do not write to the hidden volume while both volumes are mounted
double click on the volume to open the decoy volume, you can now safely modify files


DIGITAL FOOTPRINT
identifiers
monitoring & tracking


1
IP address
4
WiFi / BT
devices
3
RFID devices
2
dns requests
NETWORK
1
IP address
1
public WiFi ... carefully
2
connect over TOR
3
connect over VPN
SOLUTIONS
2
dns requests
1
Use TOR
2
Use TOR + VPN
SOLUTIONS
3
RFID devices

1
dont use
them
2
store inside RIFD blocker
SOLUTIONS
4
WiFi / BT
sensors

1
dont carry /
take our batteries
2
meet in
"faraday cages"
1
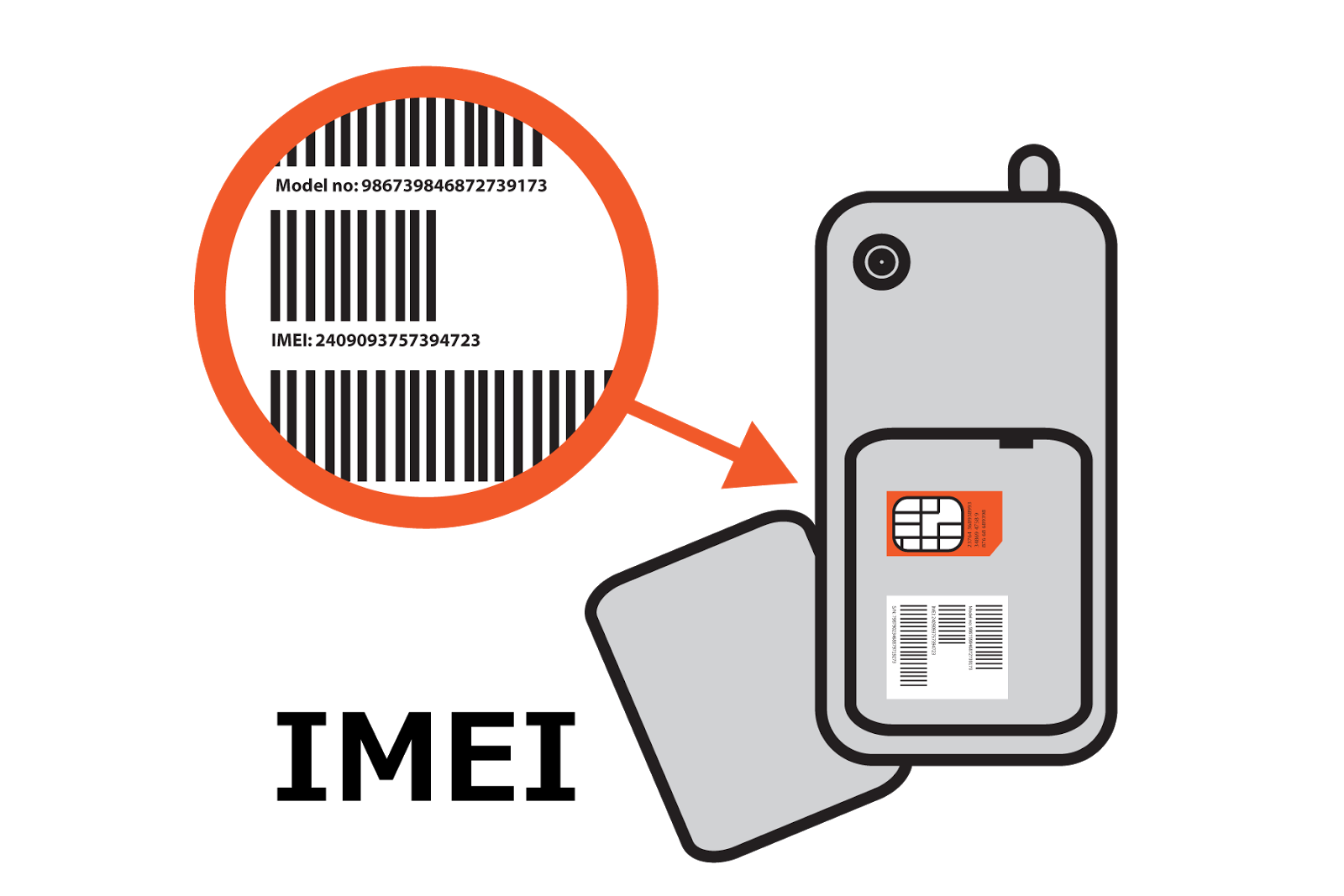
IMEI / IMSI
3
BT MAC
address
2
WiFi / Eth
MAC address

HARD
WARE
1
IMEI + IMSI
subscription pairs are recorded
3
IMEI tracked at
Point of Sale
2
IMEI + IMSI
pairs are tracked at antenna
HARD
WARE
4
IMSI tracked
at Point of Sale
5
Apple & Google track IMEI
2
Eth / WiFi
Mac Address

1
Turn off Telemetry
2
Replace the G with DuckDuckGo
3
Private and Secure DNS
6
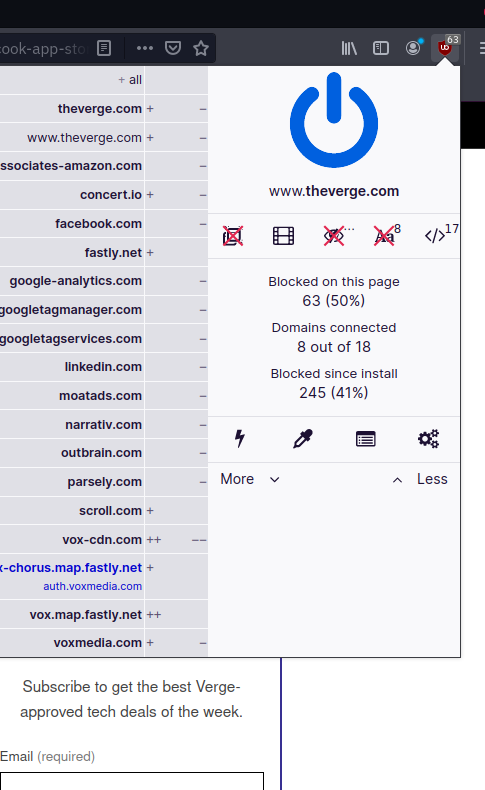
Security Extensions
5
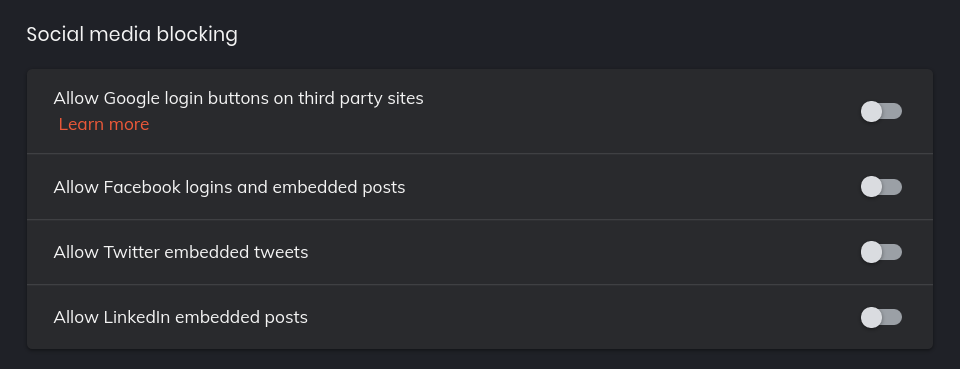
Rip out Social Media
4
Shields Up!

1
Turn off Telemetry
about:telemetry
2
Private and Secure DNS
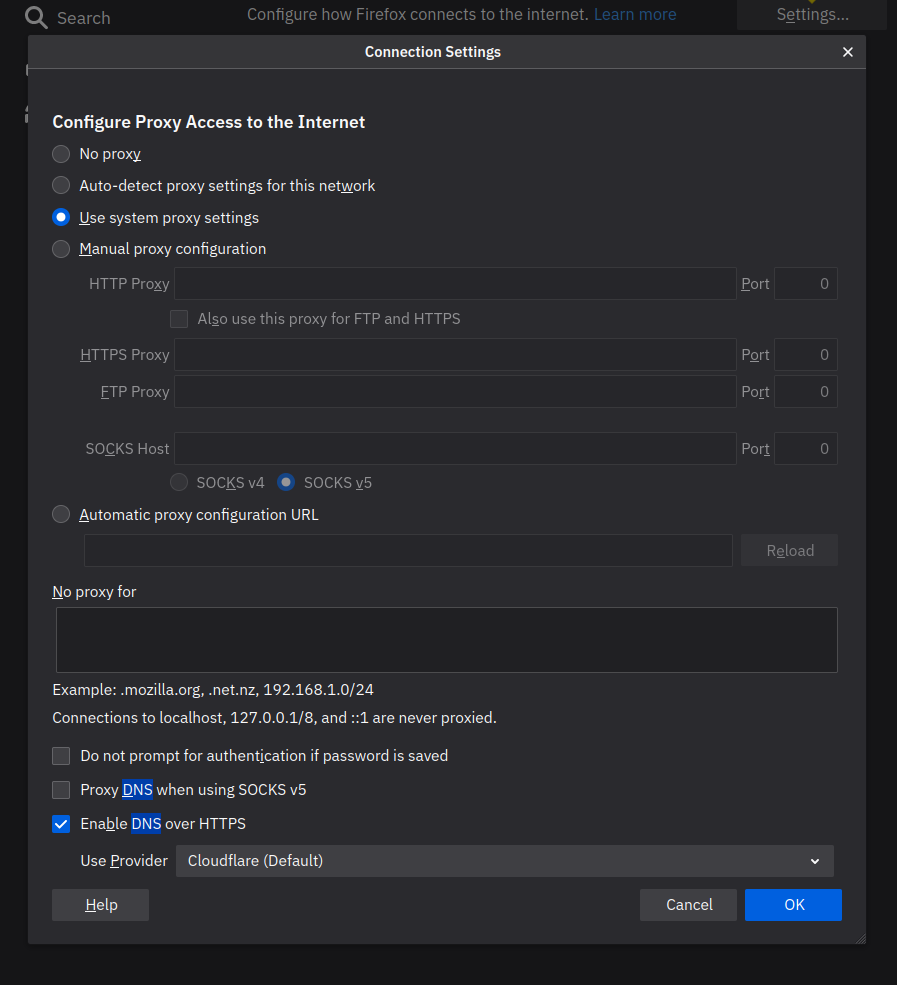
Preferences > General Tab > Network Settings > Settings > Enable Enable DNS over HTTPS.
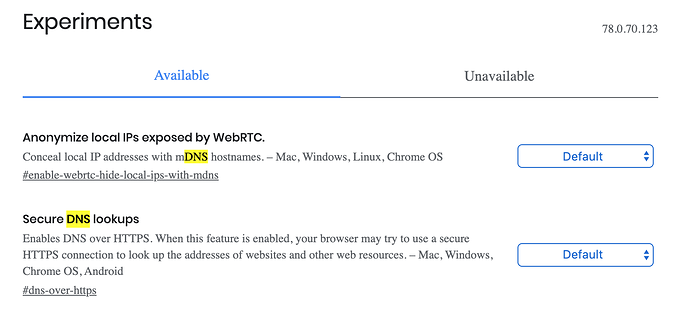
Replace the G with DuckDuckGo
3
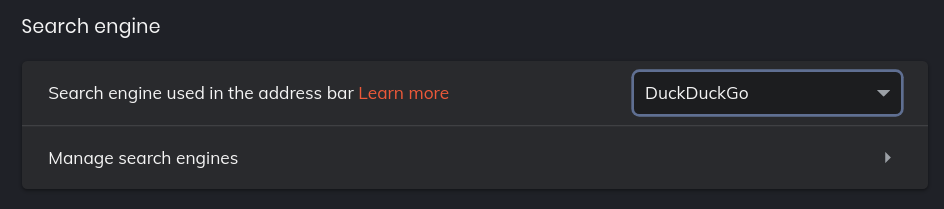
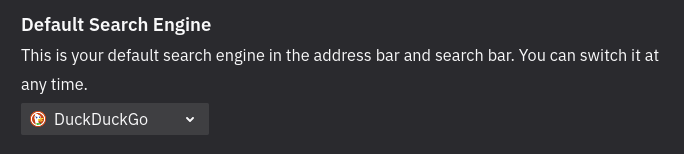
PRO TIP : turn off search suggestions
4
Shields Up!
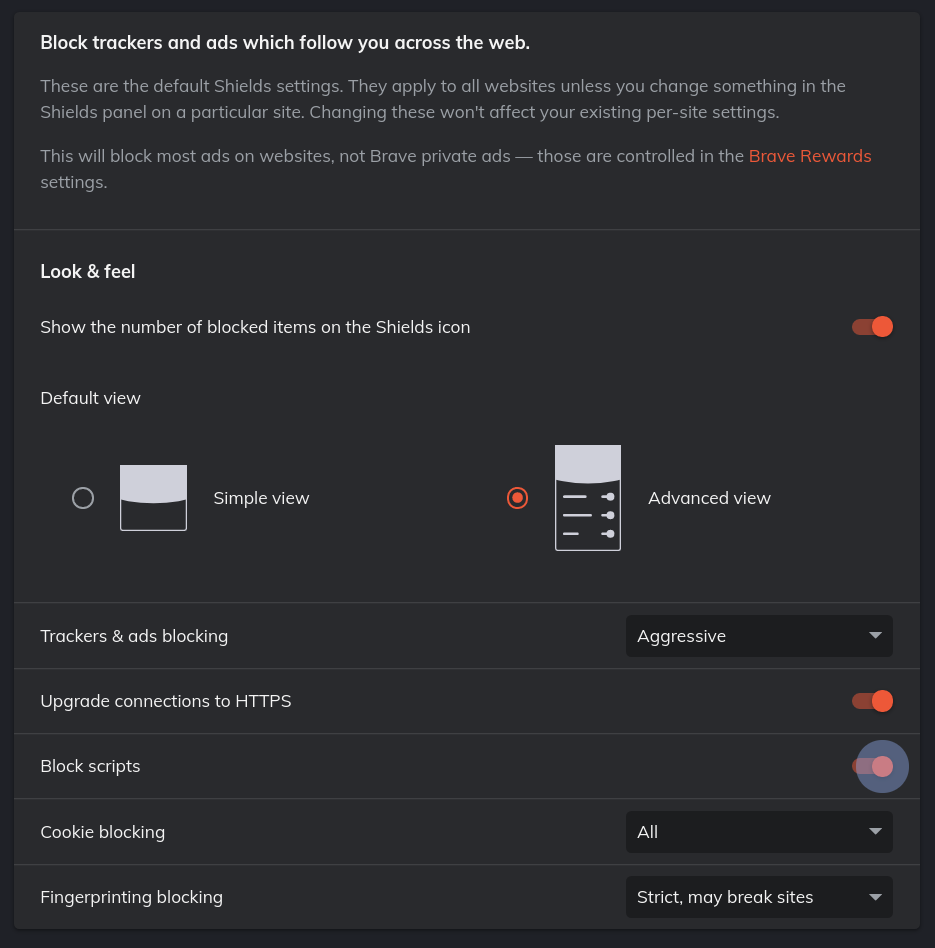
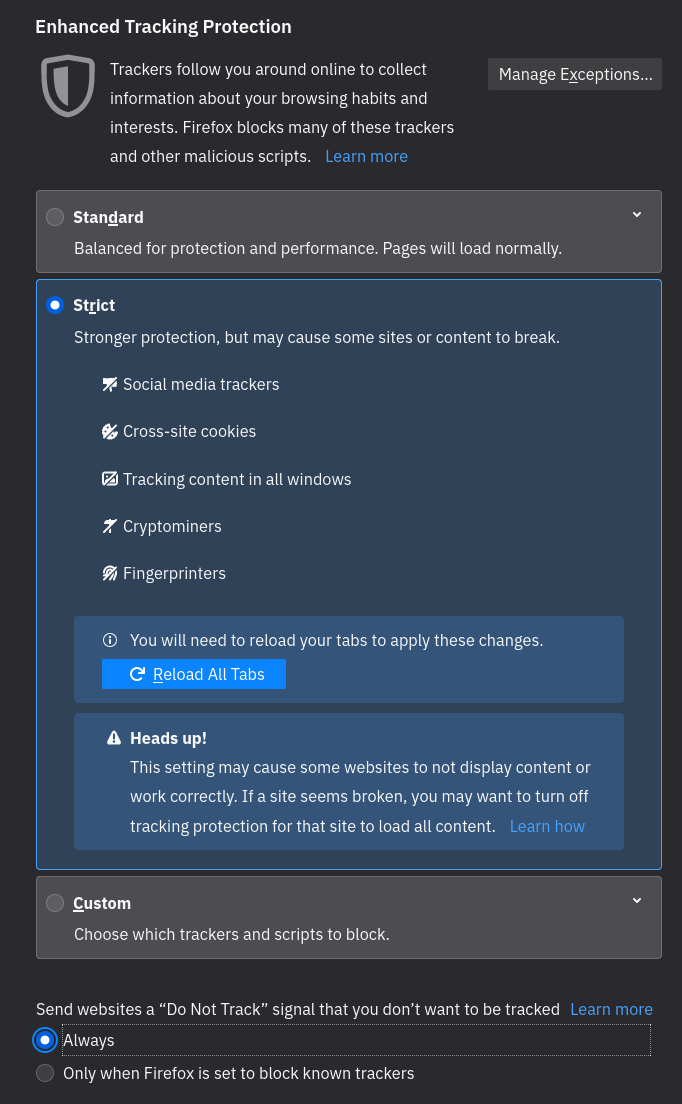
5
Rip out Social Media
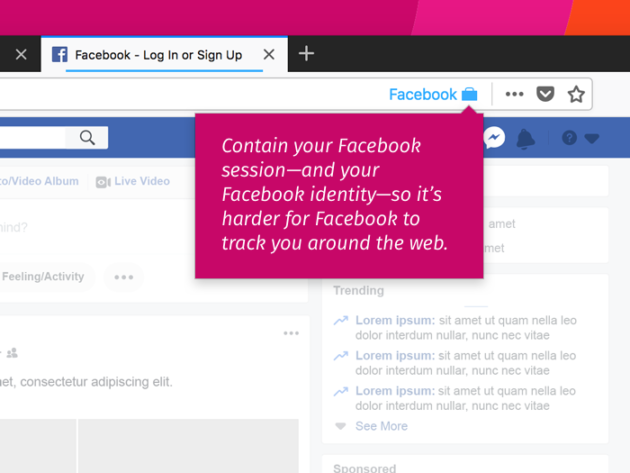
6
Security Extensions

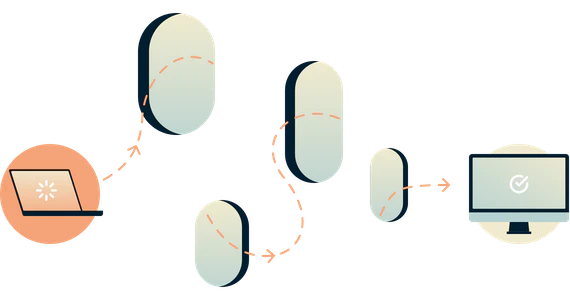
TOR
1
anonymous browsing through layer of proxy servers
2
prevents browser fingerprinting
3
be default, only protects browser; not apps
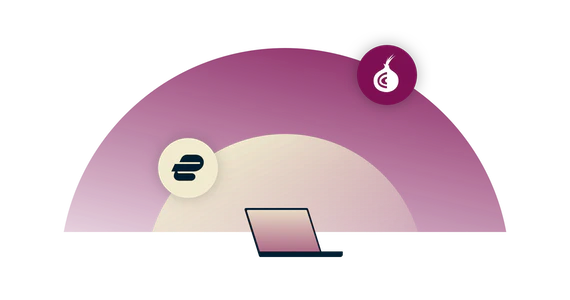
TOR over VPN
1
all the privacy
benefits of TOR
2
Home network cannot see TOR connection
3
TOR entry nodes cannot see your IP
Mart
GIVEN NAME
vs
PSEUDONYM
vs
ANONYM
tijptjik
?

revealing
GIVEN NAME
PSEUDONYM
vs
ANONYM
obscuring

Mart
tijptjik
?
persistent
GIVEN NAME
PSEUDONYM
vs
ANONYM

ephemeral
Mart
tijptjik
?
What you can do
to stay secure
Keep them up to date!
1
Don't share device
Make sure they auto-lock
2
3
Avoid connecting external devices
4
Encrypt drives and USB sticks
5

Your Devices
1
2
3
4
5
Only install apps from trusted sources (Google Play, official sites)

Your Apps
Keep apps up to date!
Avoid pirated software
Turn off sharing / back up features
1
2
3
4
1
2
3
4
Always use the password manager
Your Accounts

Set accounts up properly ... or delete them
Set reminders to review security settings
(3x per year)
1
1
2
2
3
3

Communicate
Allow for healthy distrust
Verify each other's identity
Avoid stress, allow for slow pace
Avoid clicking on links from strangers (use bookmarks)
1
1
2
2
3
3
4
4
QUESTIONS?!
QUESTIONS?!

Title Text
BROUGHT FOOD?!
BROUGHT FOOD?!

Digital Security with Raccoons
By Mart van de Ven
Digital Security with Raccoons
- 1,510