Malwares
What are Malwares?
Malware is a set of instructions that run on a victim's computer. The attacker can practically craft malwares to do anything they like to do with the victims computer.
What are they used for?
- DDOS attacks. Lulzsec anyone?
- Stealing of information.
- Including: browser history
- private files
- passwords
- anything present on your harddrive and ram.
- Use your computer.
Types
- Worms (my favorite)
- Virus
- Trojan/Backdoor
- Rootkit
- Adware/Spyware/Ransomware/...ware.
Worms
On November 2, 1988, Robert Tappan Morris, a Cornell University computer science graduate student, unleashed what became known as the Morris worm.
- 2010 - Stuxnet - first worm to attack SCADA systems.
- 2011 - Duqu
- worms are rare. These days Ransomwares/Trojans are the most popular.







Stuxnet
- Four 0-day vulnerabilities
- Root-kits - advanced techniques to hide itself from users and anti malware software.
- But it only infected systems very specific in nature.
-
The ultimate destination of Stuxnet is the computers that control the centrifuges. These are called PLCs (Programmable Logic Controllers), and are special-purpose computers, used for controlling electronic devices or systems, such as industrial systems.
-
PLCs are connected to computers that monitor them and usually aren't connected to the internet.
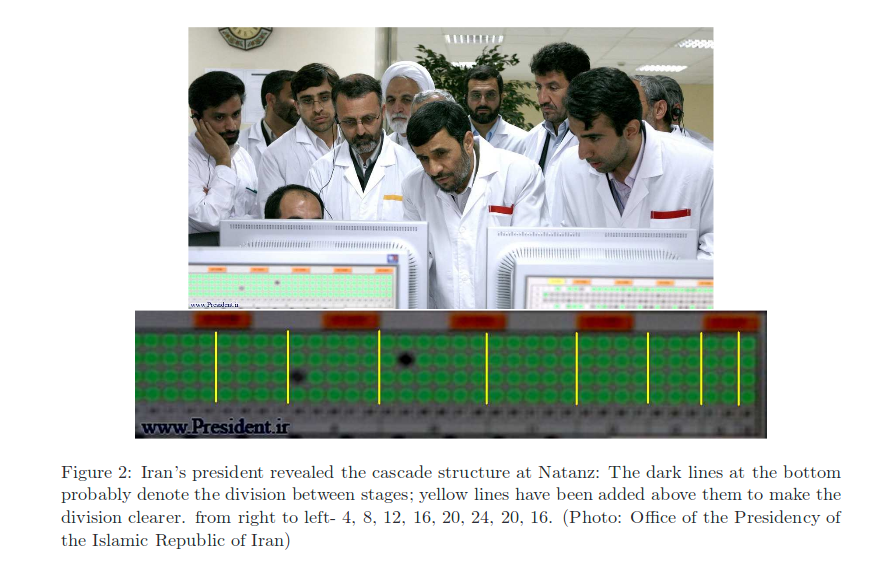
Iranian President lul
Iranian President visited Natanz on April 8, 2008, and photos of the visit were published on his website as a photo-op. The attackers
Spreading
- Via USB devices (simple and works best)
- Via WinCC
- Via network shares
- Via the MS10-061 print spooler 0-day vulnerability
- Via the MS08-067 SMB vulnerability
USB Drives
- USB Drives: recent versions use an Windows LNK vulnerability and older versions use an autorun.in file vulnerability.
-
The USB contains the Stuxnet DLL and a loader for it, the malware creates four .lnk files on the removable drive. These are used to execute the loader when a user views the drive.
- Autorun.inf: Remember the time when windows just blindly ran any command in autorun.inf as soon as you enter an external device? yeah that!
WinCC
Stuxnet searches for computers running Siemens WinCC, an interface to their SCADA systems. It connects using a password hardcoded into WinCC, and attacks its database using SQL commands to upload and start a copy of itself on the W
inCC computer.
Network Shares
Uses Windows shared folders to propagate itself over a local network. It places a dropper file on any shares on remote computers, and schedules a task to execute it.
Infection
- inject it into a chosen process - add its own code into a running process.
-
check for the appropriate platform
-
escalate privileges
-
install two kernel-mode drivers, one for running Stuxnet after reboot and the other as a rootkit to hide its files.
Attack
- Step7 programs, which control and monitor these PLCs, use a library named s7otbxdx.dll to communicate with the actual PLC to read or modify its contents (codes). Stuxnet gets control over all requests sent to the PLC by wrapping this library.
- runs the centrifuge rotors at too-low and too-
high frequencies (as low and high as 2 and 1410 Hz, respectively)
-
The slow speeds are sufficient to result in inefficiently pro-cessed uranium, and the high speeds are probably sufficient to result in centrifuges actually being destroyed, as they are at the centrifuges’ maximum speed limit.
Well that was years ago
- Sonic Screwdriver
- DerStarke
- Trition
- DarkSeaSkies

Sonic Screwdriver
- Sonic Screwdriver is a mechanism for executing code on peripheral devices while a Mac laptop or desktop is booting.
- The code for Sonic Screwdriver is stored on the firmware of an Apple Thunderbolt-to-Ethernet
adapter. The implant code will scan all internal and external media devices for a device
with a specific volume name. It later executes a UEFI boot of that device.

Affected Devices
- MBA5,1 (Mid 2012 - 11”)
- MBA5,2 (Mid 2012 - 13”)
- MBA4,1 (Mid 2011 - 11”)
- MBA4,2 (Mid 2011 - 13”)
- MBP10,1 (Mid 2012 - 15” Retina)
- MBP10,2 (Late 2012 - 13” Retina)
- MBP9,1 (Mid 2012 - 15”)
- MBP9,2 (Mid 2012 - 13”)
- MBP8,1 (Late 2011 - 13”)
- MBP8,2 (Late 2011 - 15”)
Trition
Triton is an automated implant for Mac OS X.
Mac OS X 10.7 or 10.8 + lxml♦
Supported Target Systems: Mac OS X 10.7 or 10.8
Its way for CIA to execute tasks on your mac. They have a neatly written API for automated and manual tasks that they can perform on your systems at will.
Trition
####### IMMEDIATE TASKS ########
# GET: recursively get the specified files/folders, regardless of size
get:/some path/here
get:/a/file:/another file/here:/some/directory/
# PUT: put the source file on the target system at the specified location
# - file will be root owned and executable by root
# - directory containing dest file must exist
put:/sourcefile:/destfile
# EXEC: execute something with the specified parameters
# - arg 1 is the executable on target
# - if arg2 and 3 are present, and arg 2 is "stdin" then arg3 is piped to stdin
# - all other parameters are passed to the executable
exec:/some/file
exec:/some/file:args:moreargs:etc
exec:/some/file:stdin:/some/stdin/file:args:moreargs
# UNINSTALL: uninstall, optionally removing the specified files
# - Triton will remove it's files and stop running
# - Der Starke will set an NVRAM variable to indicate uninstall on next reboot
# - The update bundle will also be removed
Malwares
By Aneesh Dogra
Malwares
- 826



