

Why do we care about anonymity on the Internet?

Source
Dest


M1
M2
M1 and M2 knows who are you talking to
Question: Is encryption going to help?
Why proxies don't work?



Proxy
User
Server
- Once the proxy IP is known, its easy to block
- If the adversary can monitor the traffic between proxy and the user and the proxy and server. He can trace the user.
Things to know
- Encryption
- IP address
- Packet
- Public/Private Keys
- Asymmetric Encryption
- Symmetric Encryption
- Integrity check
- Perfect Forward Secrecy
- Diffie Hellman Handshake
Diffie Hellman
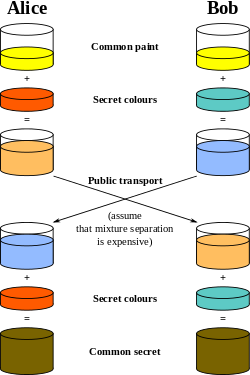
-
Alice and Bob agree to use a modulus p = 23 and base g = 5 (which is a primitive root modulo 23).
-
Alice chooses a secret integer a = 6, then sends Bob A = g^a mod p
A = 5^6 mod 23 = 8 -
Bob chooses a secret integer b = 15, then sends Alice B = g^b mod p
B = 5^15 mod 23 = 19 -
Alice computes s = B^a mod p
s = 19^6 mod 23 = 2 -
Bob computes s = A^b mod p
s = 8^15 mod 23 = 2 -
Alice and Bob now share a secret (the number 2).
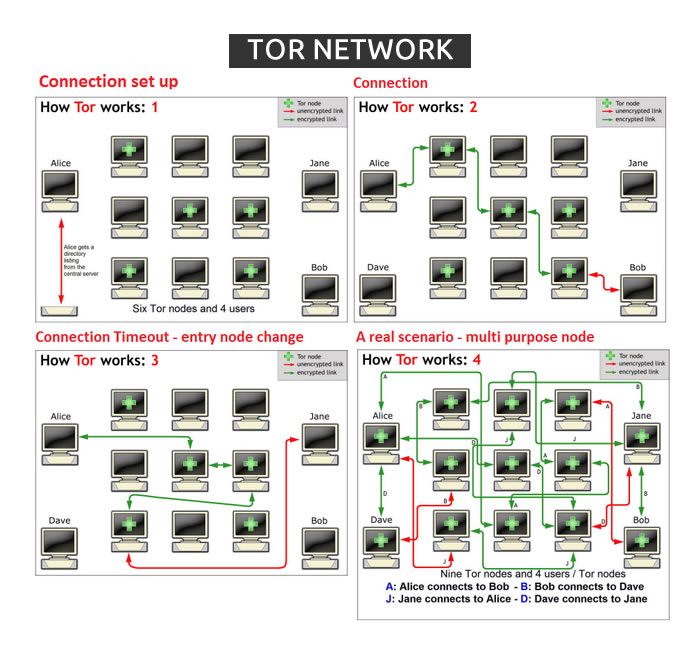
How does it work?
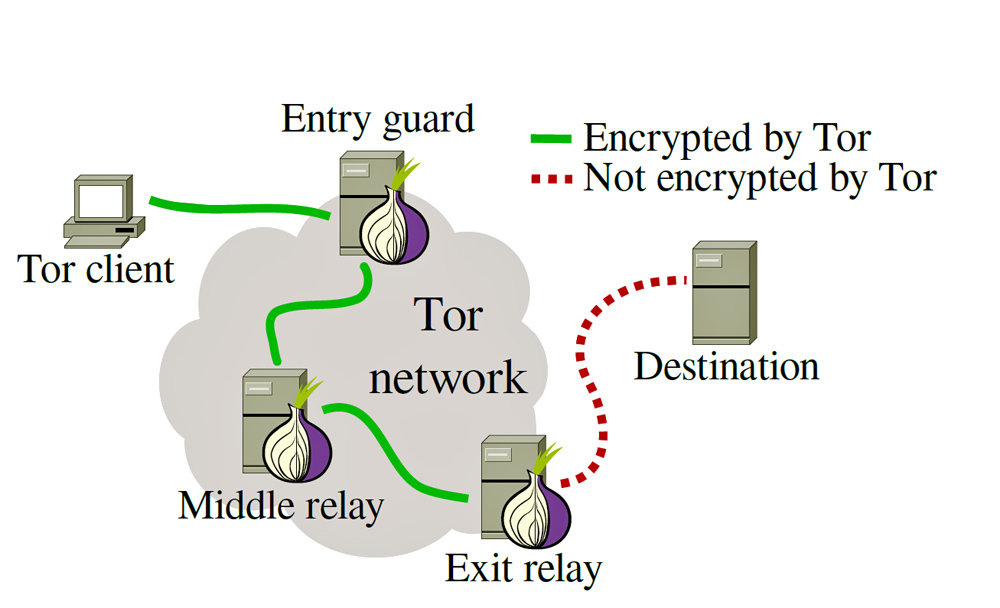
...
- The user first requests the directory server for a list of relays. This also contains information about their public keys.
- The user then starts talking to the guard relay (using asymmetric encryption)
- Then it iteratively builds a circuit one-hop at a time.
- Each hop associates a unique CircID.
- To extend the circuit to a third node or beyond, Alice proceeds as above, always telling the last node in the circuit to extend one hop further
- Symmetric keys are shared between each OR in the circuit. To ensure Private forward Secrecy.
- To extend the circuit to a third node or beyond, Alice proceeds as above, always telling the last node in the circuit to extend one hop further
- Each hop associates a unique CircID.
- To extend the circuit further, Alice sends a relay extend cell to Bob, specifying the address of the next OR (call her Carol), and an encrypted g x2 for her.
How does it work?
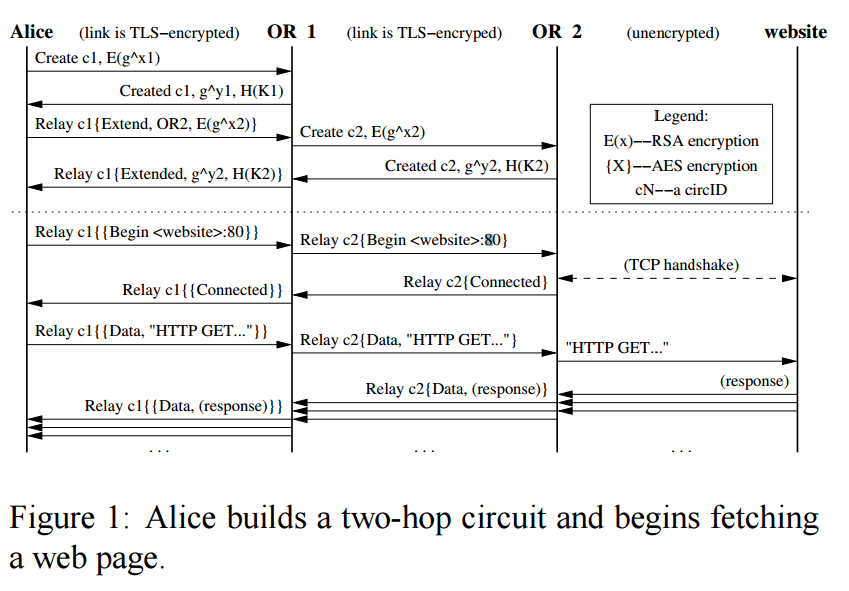
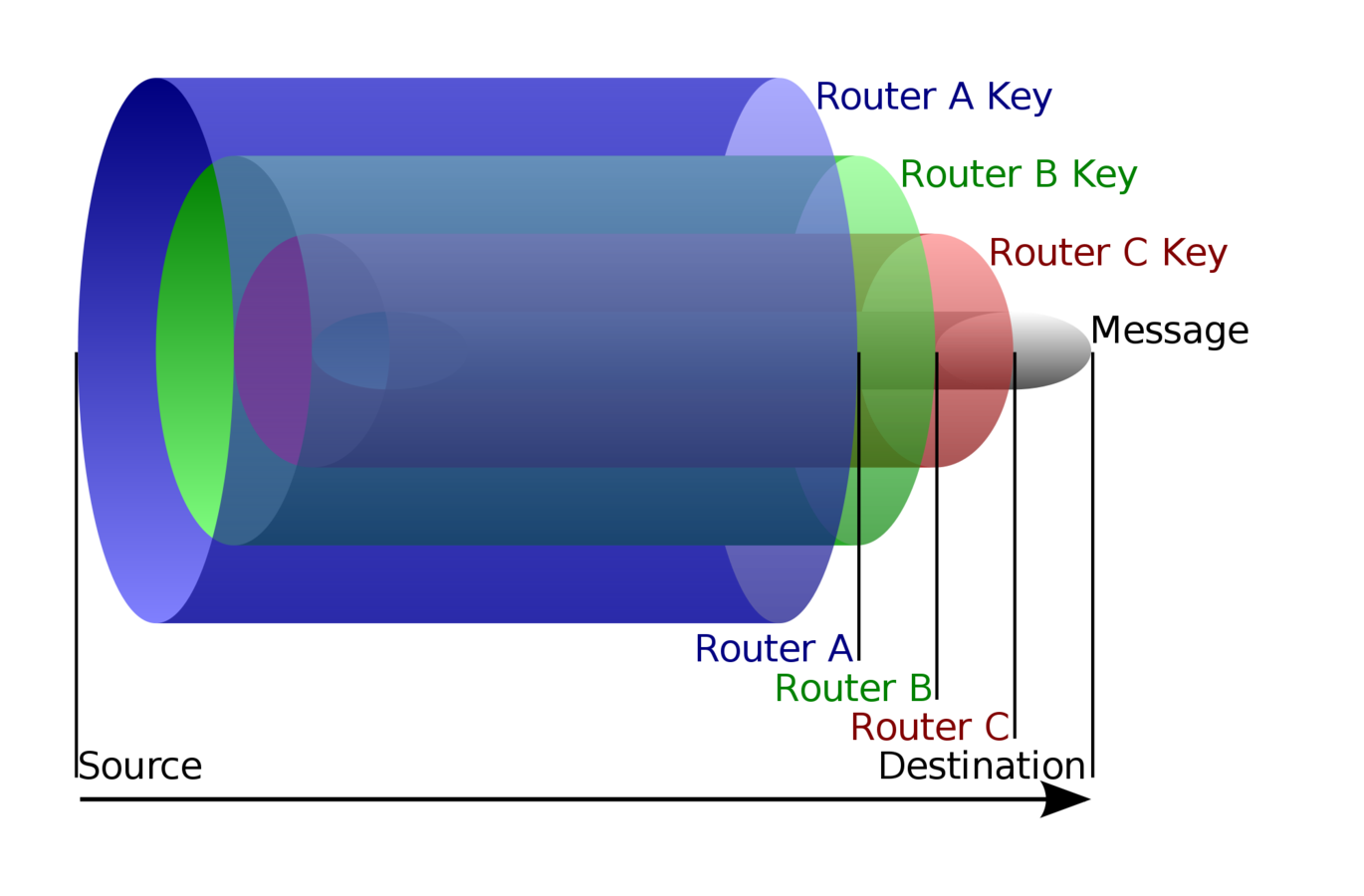
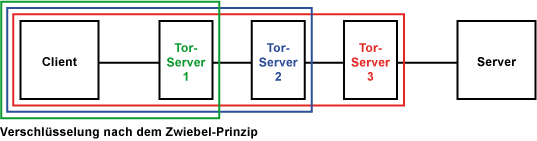
How do we transmit messages?
How are the governments around the world trying to block Tor?
- Iran
- block "/tor/"
- liberation number "p"
- block if SSL certificate expires within 2 hours
- Tunisia - only port 80
-
China
- block public relays
- block public bridges
- follow up on connections, say hello, check what he says
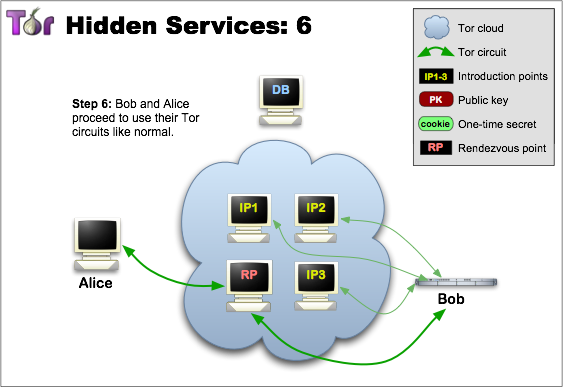
Rendezvous Points
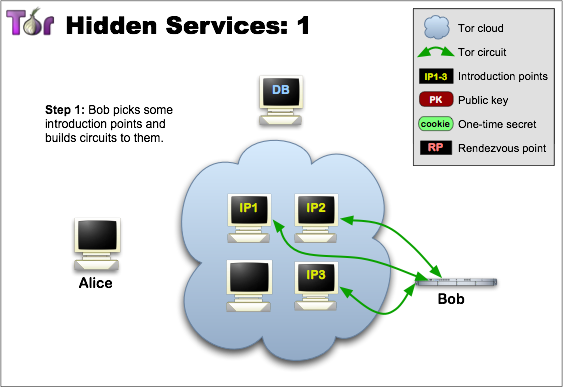
Bob builds circuits to Introduction Points and share his public key with them.
Rendezvous Points
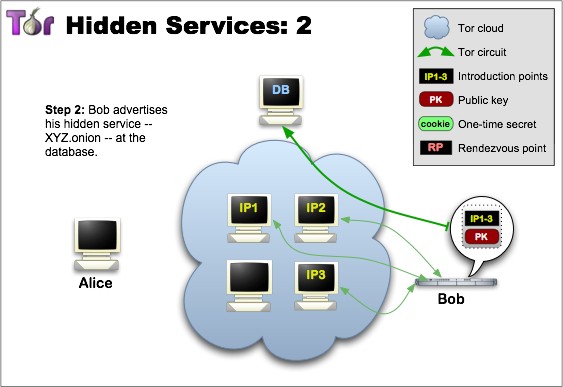
Rendezvous Points
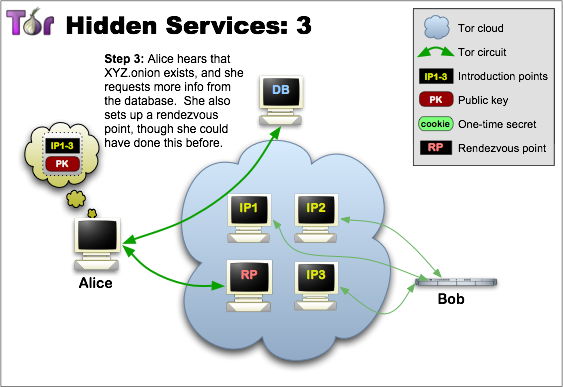
Rendezvous Points
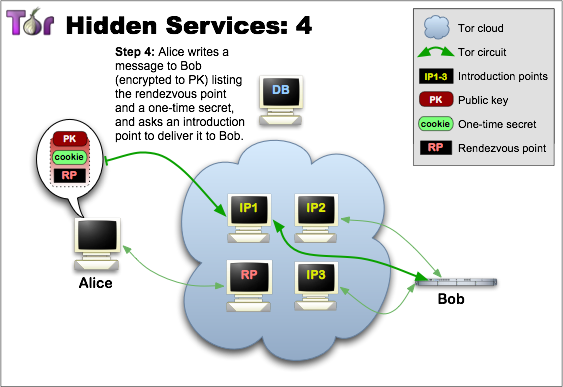
Rendezvous Points
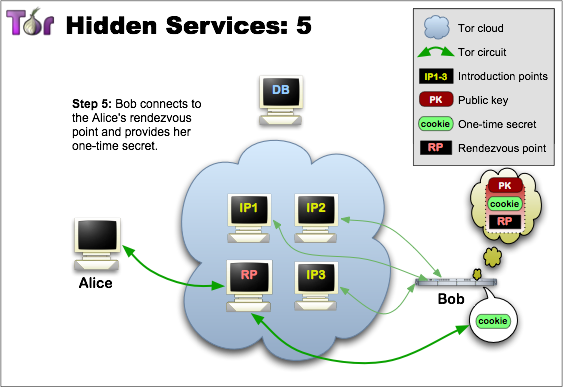
Rendezvous Points
Tor
By Aneesh Dogra
Tor
- 693



