Cyber101 - Getting into Cyber as a Student

These are our own views/thoughts and do not reflect the views/thoughts of our employer.
Who are we?
We graduated from UMD in '19 with our BS in CS. We were involved in CSEC and helped create challenges for UMDCTF-2018/19.
Now we have to be adults and work our lives away, but still love CTFs and connecting with the community! (And we love our jobs! #cyberroolz)
Mike - WittsEnd2
Drake - drakemp
Researcher
Reverse Engineer
Hobbyist - DIY electrionics
- RF
- MISC.
Foodie

Software Engineer - C, Python, & Web
Reverse Engineer
Graduate Student - M. Eng. Cyber Sec.
Hobbies: CTFs/Dev Projects, Entrepreneurship, Baseball, Music, Stocks
How to reach us
#!/usr/bin/env python3
user = 'drakemp'
sites = {
"discord: ": "#3083",
"gitlab: ": "",
"email: ": "@terpmail.umd.edu",
"spotify: ": "",
"itch.io: ": ".itch.io",
"duolingo: ": ""
}
for site,ext in sites:
print(site + user + ext)





#include <stdlib.h>
typedef struct Contact {
char discord[15];
char twitter[15];
char github[10];
} Contact;
int main() {
Contact *contactInfo = malloc(sizeof(struct Contact));
contactInfo->discord = "WittsEnd2#9274";
contactInfo->twitter = "@RagnarSecurity"
contactInfo->github = "WittsEnd2";
return 0;
}General Resources
(The good stuff)
Reddit:
- r/ReverseEngineering
- r/ghidra
- r/hacking
- r/HowToHack
- r/humblebundles
- r/memoryforensics
- r/RTLSDR
- r/securityCTF
- r/netsec
- r/netsecstudents
- r/LiveOverflow
- r/linux
- r/linuxmemes
- r/linuxmasterrace
- r/unixporn #getricingYoutube:
- LiveOverflow
- Hak5
- pwn.college
- RTL Engineering
- Guided Hacking
- Ben Eater
- Computerphile
- DEFCONConference
- Aerospace Village
- Car Hacking Village
- Cheat The Game
- LockPickingLawer
- Suckerpinch
- John HammondWebsites:
- vx-underground.org
- index-of.es
- repnz.github.io
- www.corelan.be
- github.com/RPISEC/MBE
- pwn.college
- exploit.education
- hockthebox.eu
- hackthissite.org
- www.overthewire.org
- tryhackme.com
- ringzer0ctf.com
- ctftime.org
- picoctf.com
- lobste.rs
Your friends are just as (if not more imporant) than these resources!
Roles/Positions in Cyber
Offensive - RED Team
- Exploitation
- Social Engineering
- Penetration Testing
- Cryptography (Cracking)
Black Hat vs White Hat
DON'T Hack anything you're not allowed to!


Mindset: Offensive
Defensive - BLUE Team
Mindset: Defensive
- Secure programming
- Network Security
- Cryptography (encryption)
- Incident Response
- Digital Forensics
Law Enforcement is huge on hiring Incident Response specialist/Digital Forensics Analyst/etc.

drakemp@mojito:~$ r2 - #Neat trick with radare2
-- There are 5 minutes from WTF to FIX in r2land
[0x00000000]> w https://youtu.be/LhF_56SxrGk
[0x00000000]> pqs
▄▄▄▄▄▄▄ ▄ ▄▄▄▄ ▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄
█ ▄▄▄ █ ▄ ██▀▄▀▄▄█▀▄██▄▄█ █ ▄▄▄ █
█ ███ █ ▀▀█ █▀▀▄█ █ █▄ █ ███ █
█▄▄▄▄▄█ ▄▀▄▀█▀█▀█▀█ █▀█▀▄ █▄▄▄▄▄█
▄▄ ▄▄ ▄▀▀▄ ▀▀ ▀▄ ▀ ▀ ▄▄
▄▄▄▀██▄▄█▀▄▄ ▄▀█ ▄ ▀█▀▄▄▄█▄█▀█▄▄▄
▄█▄▀▀█▄█▄█▀▄▀ ██▄▄▀█▀▄▄ ▄██▄▀█
▄▀▀▄▄█▄█▄█ ▄▄▄▀▄▄ ▄▄▀ ▀▄ ▄█▀█▀▀
▀▄▄█ █▄ ██ ▀▄ █▄ ▀ ▀▄▀ █▀▄▀
▄▄ █▀▄█ ██▄▀▀▄▀█▄ ▀▀▄▀▄▀███▀█▄ ▄
▀▄ ▄▄▀ ▀▄█▀▄▀▀▄▄ ▀█ █▀█▄▀▀ █▀█
█▀▄▄ ▄▄▄ ▄▄██▄ █▄▄▄▄█▀ ▄▀█▀▀▀ ▄█
█▄█▄██▄██ ▄▀▀█▀▄ ▄ ▀ ▄▄▄██ ▀▀▀
▄▄▄▄▄▄▄ █▀█▀█ ▄ ▀▄▀▄ ▄███ ▄ █ ▄
█ ▄▄▄ █ ▄▀█ ▀ █ ▄▀▀█▄ ▄█▄▄▄████
█ ███ █ ▀▄ ▀▀██ ▄█▀ ▄▀▄ █▀ ▀▄▀ █▄
█▄▄▄▄▄█ █▀ ▄ ▄█▄ ██ ▀ ▄ ▀ ▄ █▀▀
[0x00000000]>
Hybrid - PURPLE Team
- Security Research (generally)
- Reverse Engineering
- Bug Bounties
- Vulnerability Research
- Developers
#PURPLETeamizb3st



Mindset: Both Offensive and Defensive
Genres (topics) in Cyber
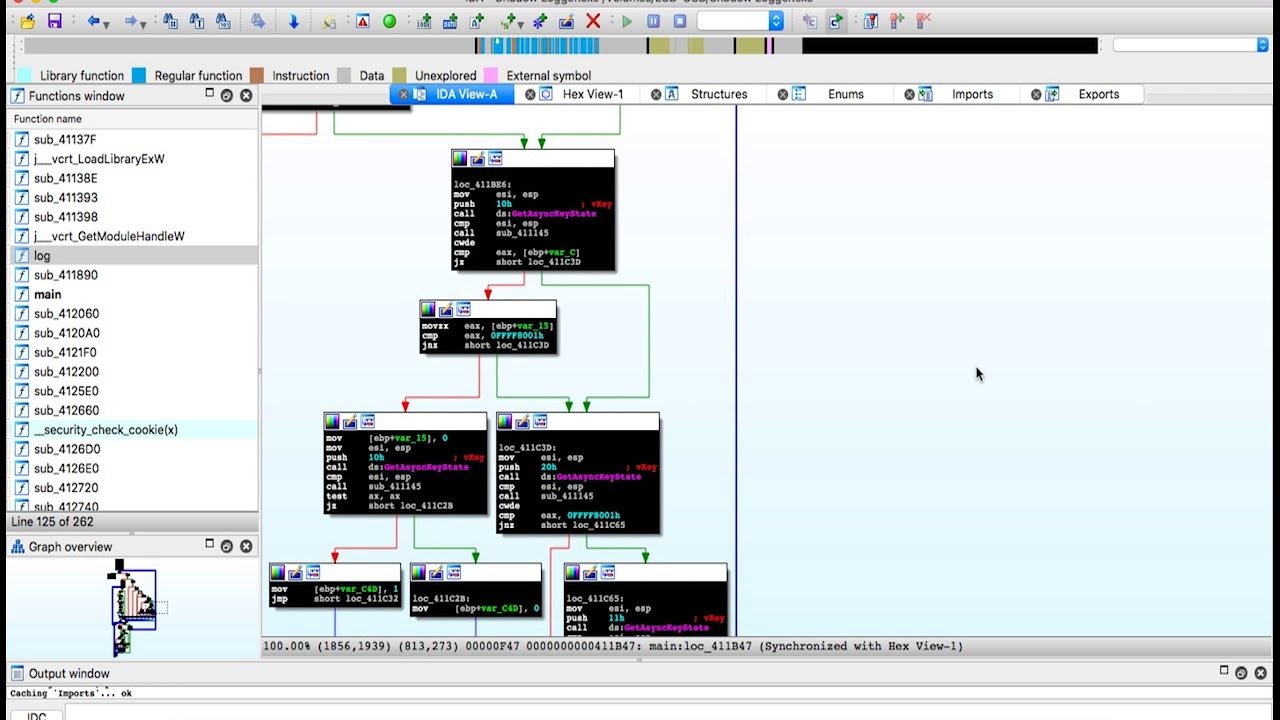
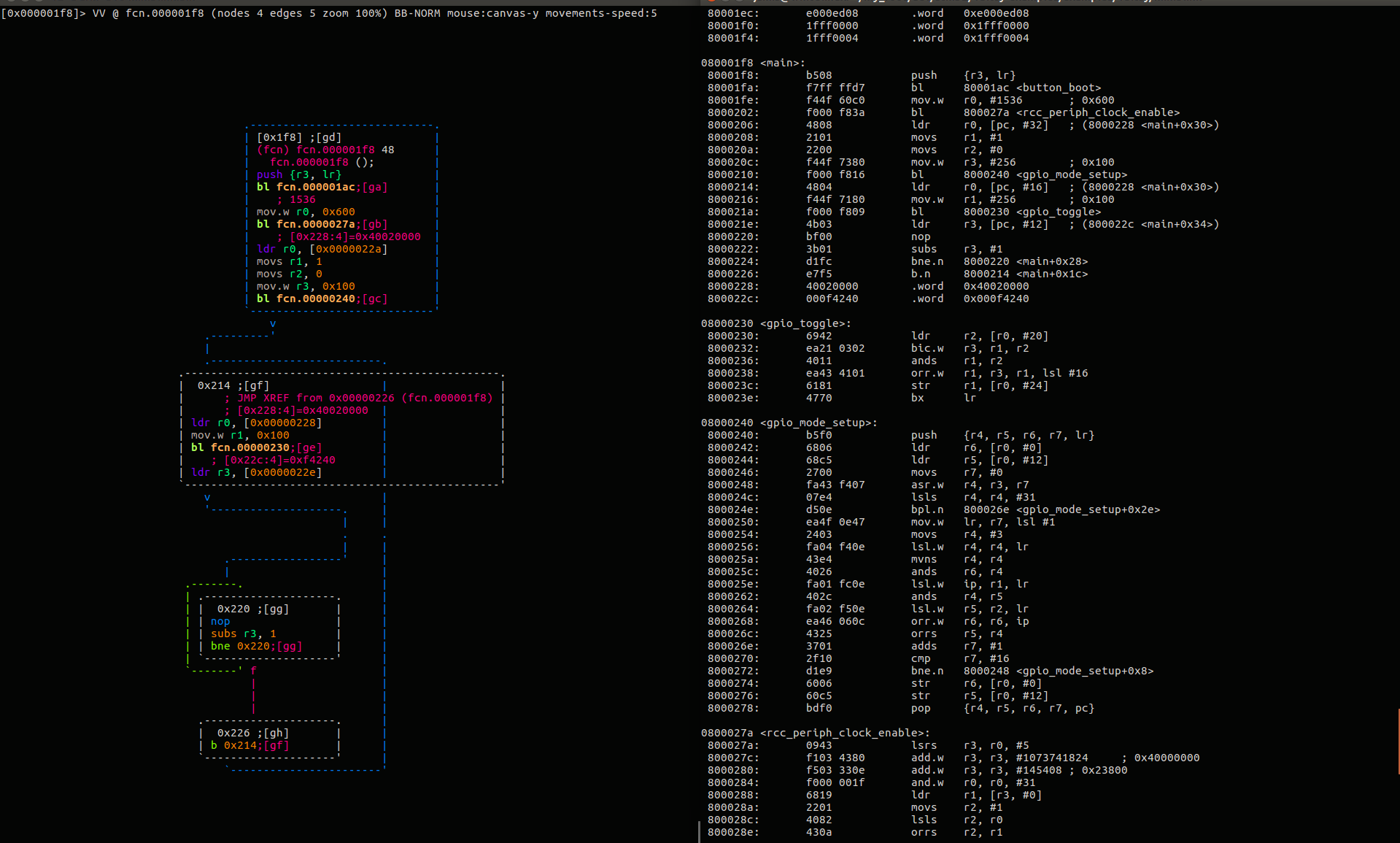
Reverse Engineering
Understanding how something works, whether its software, hardware, or anything else.
Ghidra
IDA Pro
Binary Ninja
Radare2
ptrace/strace
Sysinternals Suite
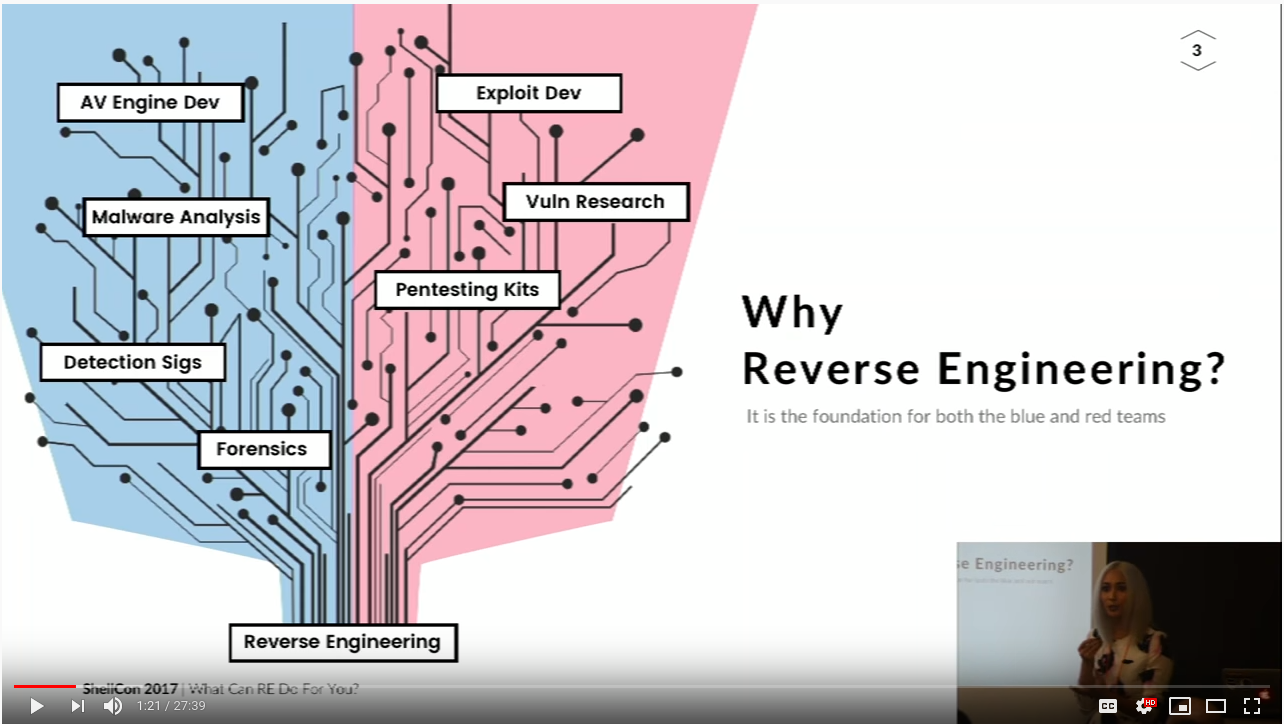
Tools (Software):


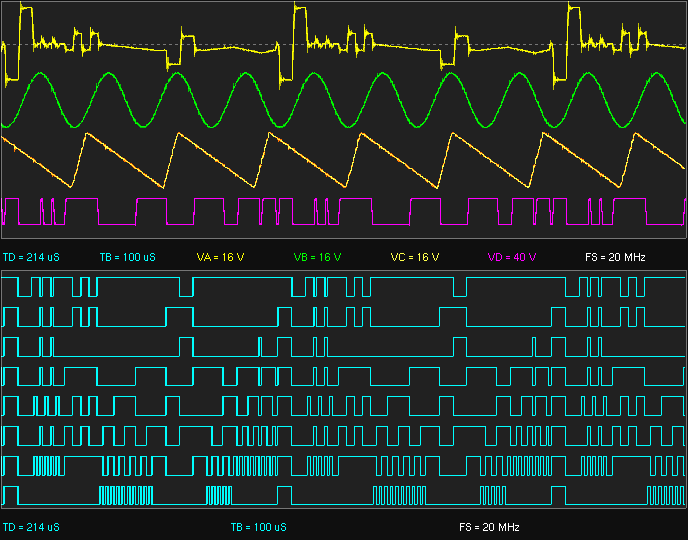

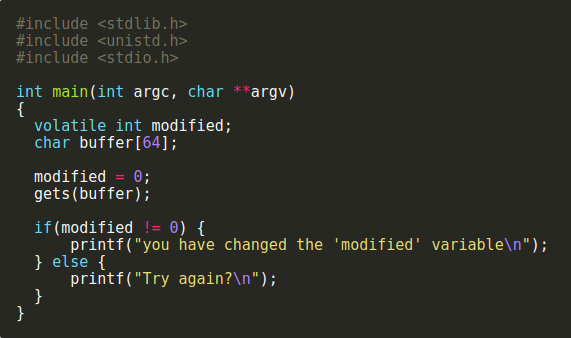
Exploit
Taking advantage of an unintended bugs features

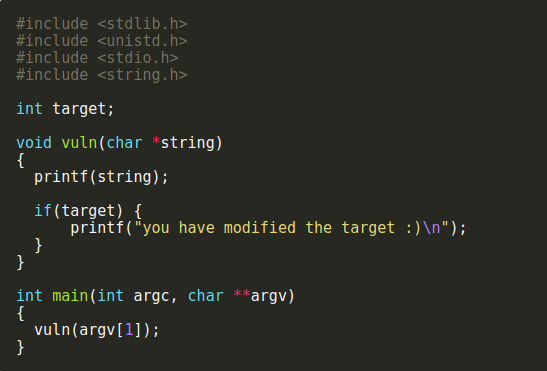
Binary -
Buffer Overflow
String Format
Return Oriented Programming (ROP)
Timing Attacks
Side channel
Web -
SQL Injections
XSS/CSRF
Can require some RE to do successfully.
Examples
Whats the exploit here?
Digital Forensics
Data Analysis - Aggregated Data investigations
Disk - Storage Drive forensics
Memory - RAM/Snapshot forensics
Network - IP traffic forensics
Mobile/Embedded - Niche technology based forensics

Popular Areas
Forensics is uncovering evidence and artifacts like a detective solving a crime scene.
Criminal Investigations
Malware / Intrusion Detection


Volatility
Autopsy
Hardware
Embedded Systems - Internet of Things
Software Defined Radio - RF Hacking
Hardware Hacks - Side channel
Tools/Resources:
- GNU Radio
- Hak5
- HackRF
- Architecture Manuals
- etc

Hardware covers a variety of topics, and as Software folk we generally don't get to play with this stuff.

Cryptography
Secure communications in an adversarial setting. In CTFs, usually breaking uses of crypto or broken crypto. (there's a difference!)
Broadly speaking, unless you become an expert in Cryptography, uses of crypto are limited to consulting and designing with secure crypto primitives. (secure primitives does not imply secure communications!)
data = 'CAPTURETHEFLAG'
key = 'A'
encrypted = ''.join([chr(ord(x) ^ ord(key)) for x in data])
print(encrypted)
# '\x02\x00\x11\x15\x14\x13\x04\x15\t\x04\x07\r\x00\x06'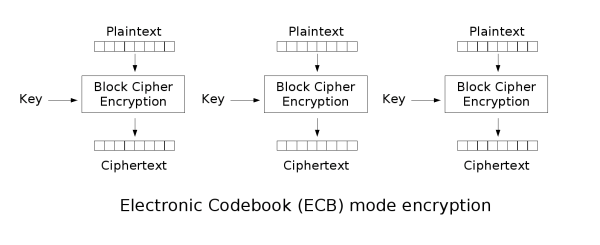



Networks/Web
- Web applications
- Industrial Control Systems
- Open Source Intelligence
Extremely broad, often see exploit development, cryptography, and forensics in web.
Tools:
- Burp Suite
- Kali Linux
- WireShark
- OWASP Zap





[0x00000000]> w https://www.destroyallsoftware.com/talks/wat
[0x00000000]> pqs
▄▄▄▄▄▄▄ ▄ ▄ ▄▄ ▄▄▄▄▄▄▄
█ ▄▄▄ █ █▀▄▄▄█▄ ██▄ ▀▄▄▀█▄ ▀ █ ▄▄▄ █
█ ███ █ █▄▀ █ ▀█▄▀▀▀▀██ ▄▀█▀▄ █ ███ █
█▄▄▄▄▄█ █▀▄ ▄▀▄ ▄▀▄ █ █ ▄▀█ █ █▄▄▄▄▄█
▄ ▄▄▄▄ ▀▄ ▄ ▀▄▀ ▀▀ ▀ ▀▀█▄ ▄▄▄▄▄
▀▀ ▀██▄▀█▀█▄█▄███▀▀ ▄▀▀ ▄▀▀█ ▄█▀▄▀█▀█
██▄▄█ ▄█ ▀██▀▄ ▄█▄▀ ▀▄▀▀ ▀█ ▄ ▄
▀▀█ ▄▄▄▄▀███▄ █ ██▄█▄█ █ ███▀███ ▄█▄█
█ █▄▀▄ ▀█▀ ▄▀ ▄▀█▀█▄▀█▄ ▀▄▄▀█▀ ▀ ▀█
█▀ ▀▄▄▄▄▀▀█ ▄ ▄█▄▄ ▀ ▀█▄ ██▀█▀▄█▀ █
█▄ ▄▄▄██▄▄ █▄▄ ▄▄█▄ ▀▀█ ██▄ ▄▀ █
█ ▀██ ▄███▀▄▄ ██▄▀▀▀▄▀▀██ █▄▀▀█▄ █
▄▀ ▀▄▄▄ ▀▀▄ ▄▄█▄ ▄▄ ▀█ ▀▀ ▄█ █ ▀▀
▄▄█ ▄▄▄▀▄█▄▄ ▀ ▄▄█ ▀▀▀▄▄ █▀▄██▄▀▀ █
▄▄ ▀██▄▄▄██▀▄▀█▄█▄██▀▄█▄█ ▀▀▄███▄▀
▄▄▄▄▄▄▄ █▄▀█▀▄ ▀█▄█ ▄██▀▄█ █ ▄ ██▄▀█
█ ▄▄▄ █ ▀█▄ ▄ ██ █▀█▄▀█ ▀██▄▄▄█▀ ▀█
█ ███ █ ▄ █▀ █ ▄█▄ ▀█ ▄█▀▀ ▀█ ██▄▄█
█▄▄▄▄▄█ ██▄▀ ▀▄▄▀▄▄█▀█▄▄ ▀██▄▀▀█ ▄
[0x00000000]>
POP CTF CHALLENGE
// What is the value of this in JavaScript?
{} - []result: -0
Resources
Programming
- Python : Useful for everything
- C/C++ & ASM : Exploit & RE
- Golang & Rust
- Web - JavaScript, PHP, etc.
- Machine Learning: For working with data
Little reason to write in assembly, Lots of reasons to read assembly
- Hackerrank - Great for learning languages fast and practicing your understanding of algorithms. Ex. functional programming, Regex, ML, Bash, C/C++, etc.)
- Side Projects - Websites, Hardware, SDR, IOT, etc.


CTFs
CTFs are a great way to learn and apply skills!

- ctftime.org - Following and keeping up with CTFs
- UMDCTF past challenges - Jeopardy
- HackTheBox - Pen. Testing / Jeopardy
- RingZer0 - Jeopardy
- Malware-Traffic-Analysis - Forensics based (Wireshark :D)
- Exploit.Education - VMs for learning exploits and privilege escalation
- TryHackMe - Pen. Testing / Jeopardy
Where to start!

Classes
Cybrary - Red Team and Blue Team Cyber
RPISEC-MBE - Intro to Exploit Dev.
ACES-Minor @UMD
pwn.college - Intro to cyber (and ctfs)
Graduate Degree: M. ENG and Computer Science
CMSC389R - Intro to Ethical Hacking
CMSC389J - Intro to Reverse Engineering
Certifications:


Open Source
Git____ is your friend!
CTF Writeups/Source Code
Metasploit
Wireshark
Nikto
NMap
Volatility
angr
Capstone - (not a school project)
BAP - Binary Analysis Platform
Many many more!




Books
-
Ghidra Book - Reverse Engineering
-
Practical Reverse Engineering
-
Practical Malware Analysis
-
Programming Linux Anti-Reversing Techniques
-
Black Hat Python - Development (Pen. Testing)
-
The Hacker Playbook 2 & 3 (Pen. Testing)
-
PoC || GTFO
-
Hacking the Art of Exploitation
-
Shellcoders Handbook
-
Grey Hat Hacking
-
Open Source Intelligence Techniques



Academia
- Research (Network with professors/faculty)
- ACES
- Cyber Security Specialization
- Lots of open source projects are being run by universities as research projects. You can easily get involved by contributing to these projects. Features/Bug Fixes/Documentation are all encouraged!

Internships
NETWORK NETWORK NETWORK
Go to CSEC meetings & meet recruiters (they are here for you)
Pro tips -
Open conversation with... "I'm taking <some class title> and I really enjoyed this project on <topic like bufferoverflows>. Do you guys do stuff like that on the job?"
Ask... "What kind of training/learning opportunities do you have? I love to learn!"
Ask... "Whats the office culture like?" (You'll love your job if you love your coworkers)



Questions/Comments/Random
Thank you!
Getting into Cybersecurity
By Drake P
Getting into Cybersecurity
This slide deck is introduce people who are interested in cybersecurity, but don't know where to start.
- 993



