Network Forensics 101

The links and content in this presentation are meant to be informational only and do not imply endorsement of the content, sources, organizations, or authors
Network Forensics
"...is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection. Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. Network traffic is transmitted and then lost, so network forensics is often a pro-active investigation." -wikipedia



The Basics
The minimum knowledge needed is understanding how computers communicate to each other!
- OSI Model
- TCP vs UDP
- HTTP(S) & DNS
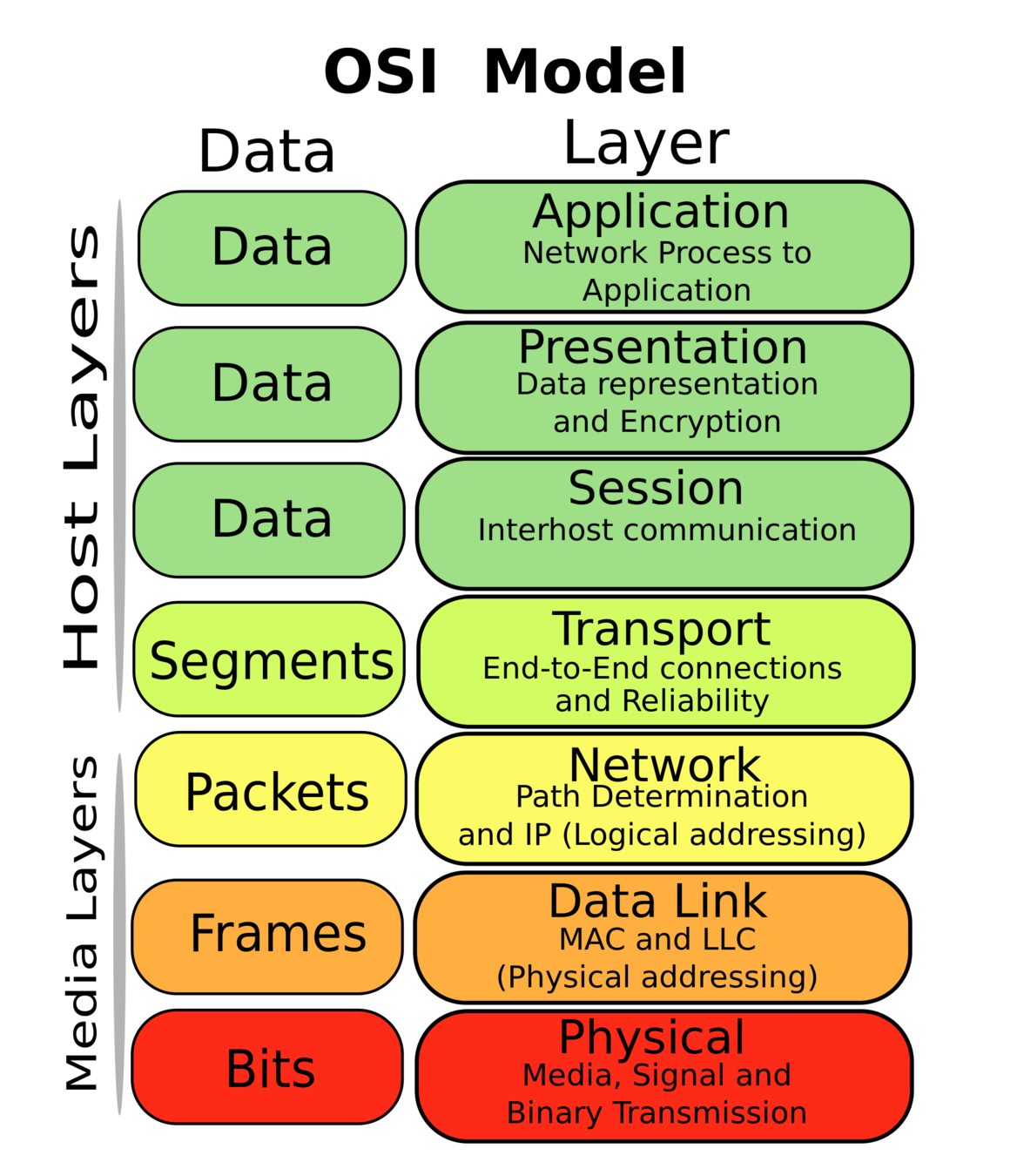
OSI Model
All communications between computers over the internet follow this abstraction. Usually, we can group the Data layers together (Layers 5-7).
Layer 1 - Physical layer is the literal transmission of bits, wired or wireless
Layer 2 - Data Link is the physical addressing of devices, what bits were meant for whom?

OSI Model
Layer 3 - Network is where IP addresses help get our packets around the world
Layer 4 - Transport is how we decide data is reconstructed on the destination end of communication
Layer 5+ - Application data is sent in any format here and left to be interpreted by an application like a browser

OSI Model
Layer 2 - Usually:
Ethernet frames on wired nets
802.11 frames on wireless nets
Layer 3 - Usually:
IP header datagrams
Layer 4 - Usually:
TCP segments
UDP datagrams
Layer 5 - all sorts of things!

Internet Protocol - Layer 3
IPv4 uses 4 octets as addresses, ex: 127.0.0.1 or 192.168.0.1
Those are both reserved private addresses, the former being localhost for your computer to address itself. The latter is usually your home router on the local area network (LAN)
Public IPs are used to address servers across the internet outside your home.
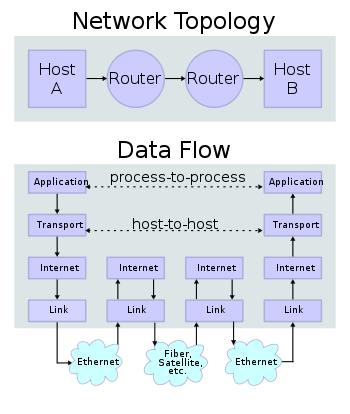
Much more to talk about here, but is omitted for simplicity's sake
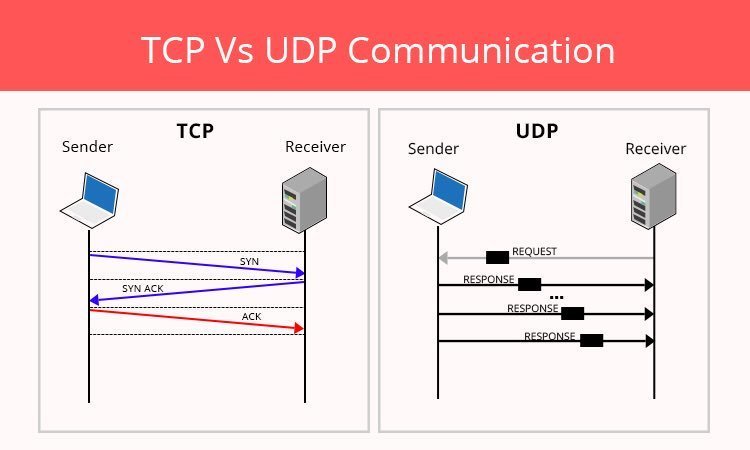
TCP vs UDP - Layer 4
UDP is a simple protocol, where packets are sent on best effort and are not ordered. This can be problematic sometimes, but is used often in video games. TCP is a reliable and ordered stream based communication. Below is an example of a TCP handshake to establish a new connection for sending data.
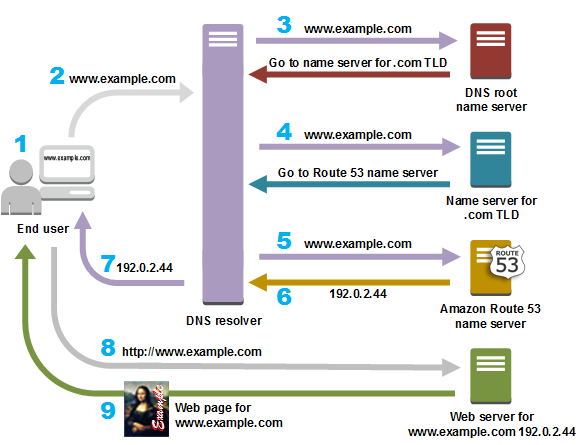
HTTP(S) & DNS - Layer 5
How does your computer know how to reach 'Google.com'?
Wireshark

Wireshark
"...is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions." -Wireshark.org
Wireshark is free and open source, with many many contributors!

Wireshark
Download for Windows & Mac: https://www.wireshark.org/#download
Linux users either compile from source or install via package manager (apt, yum, pacman)
Promiscuous mode is not needed at all in these challenges since all the examples are static.
Download pcap from MalwareTrafficAnalysis: CATBOMBER
password: infected
WARNING: these pcaps CONTAIN malware, do NOT execute any programs/binary files on your computer found in these pcaps.


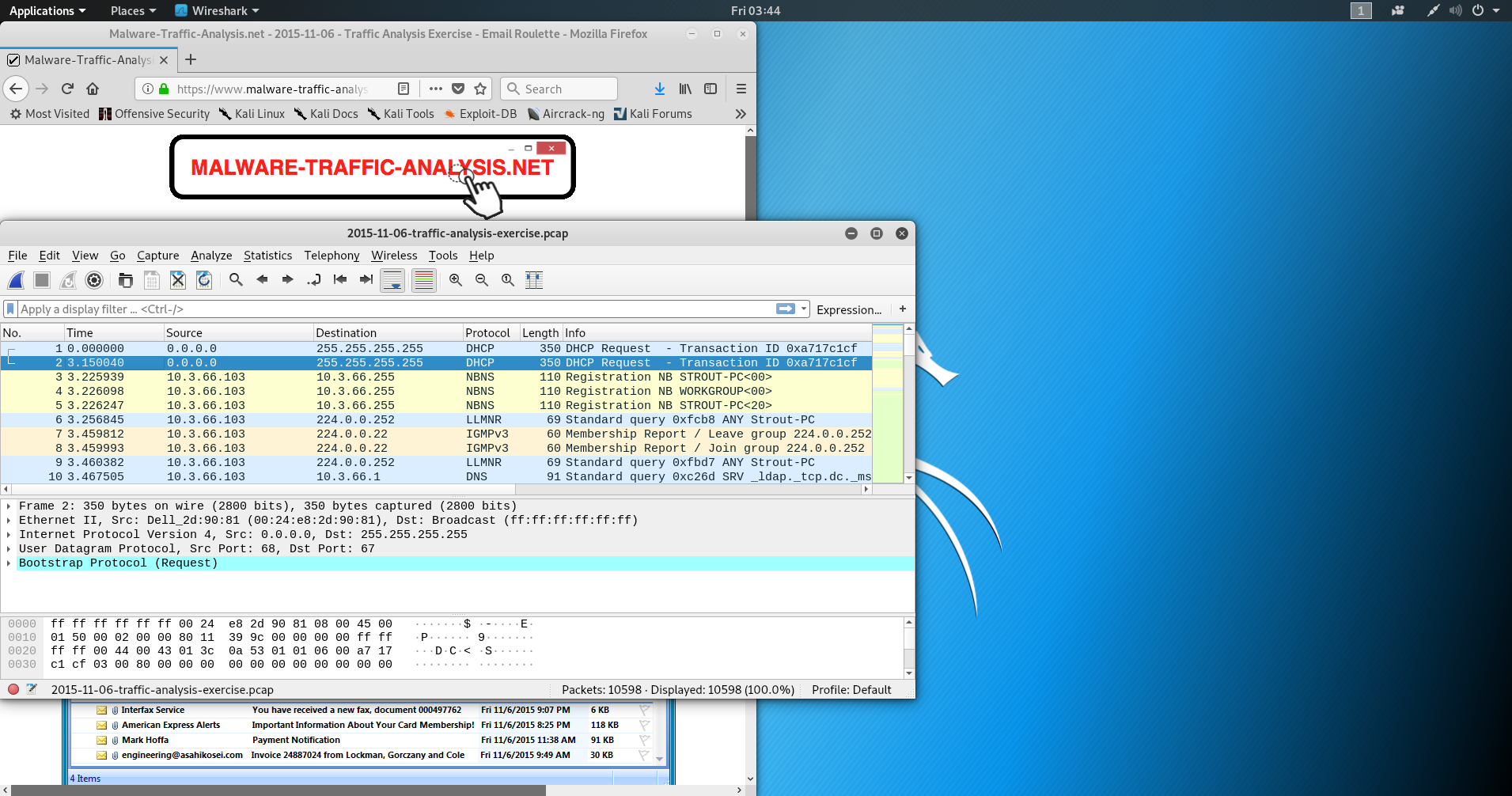
First Analysis!
Packet number
First Analysis!
Source IPs

First Analysis!
Destination IPs

First Analysis!
Top level Protocol in packet

First Analysis!
Extra useful information

First Analysis!
Expression filter bar

First Analysis!
Packet preview (all layers)

First Analysis!
Hex dump (all layers)

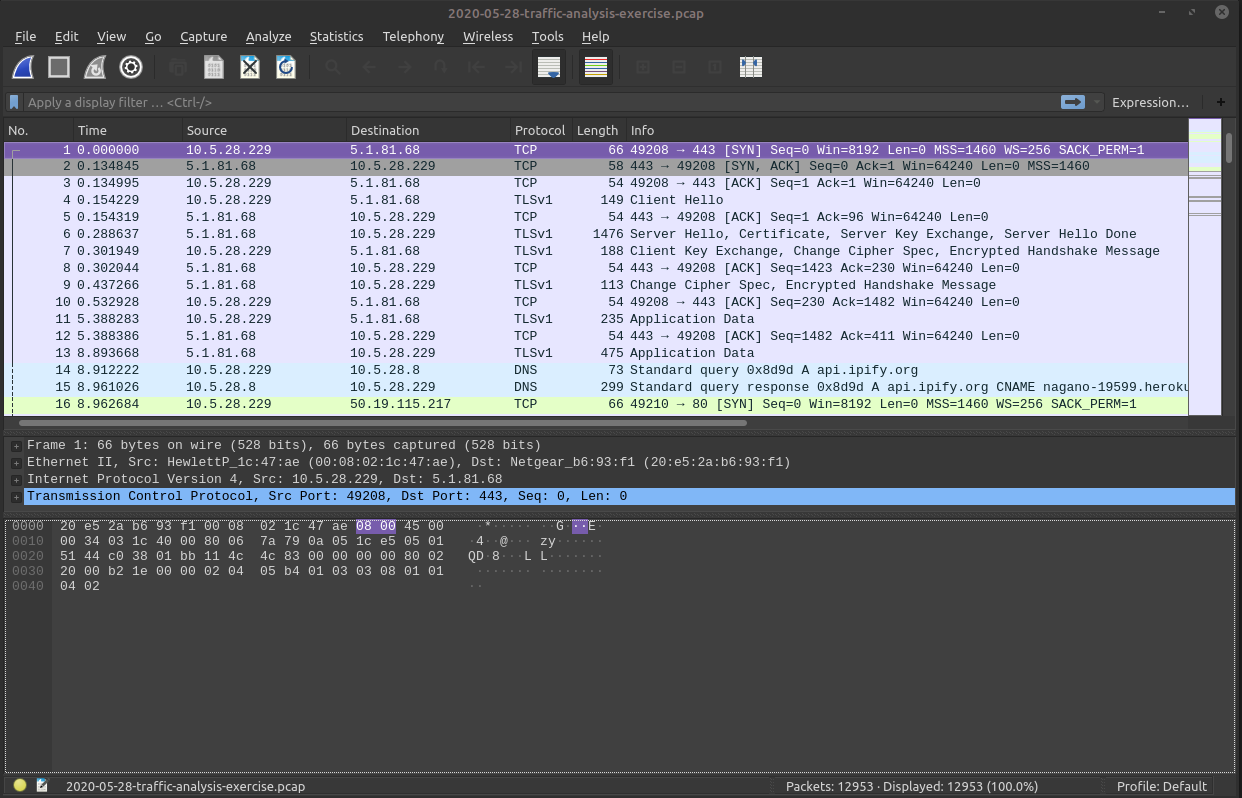
First Filter!
Filter for DNS
First Filter!
DNS Results

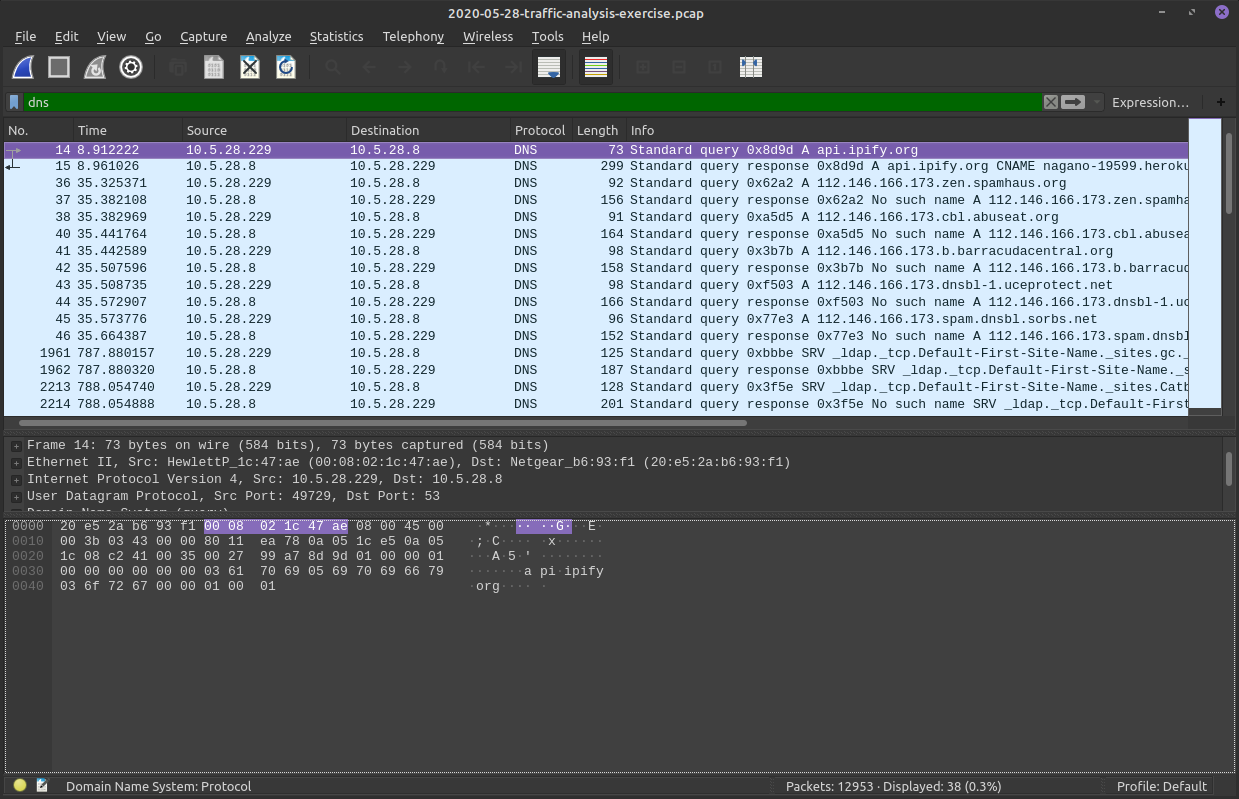
First Filter!
Inspect individual DNS packet and all the frames
First Filter!
We can see this packet was delivered with UDP

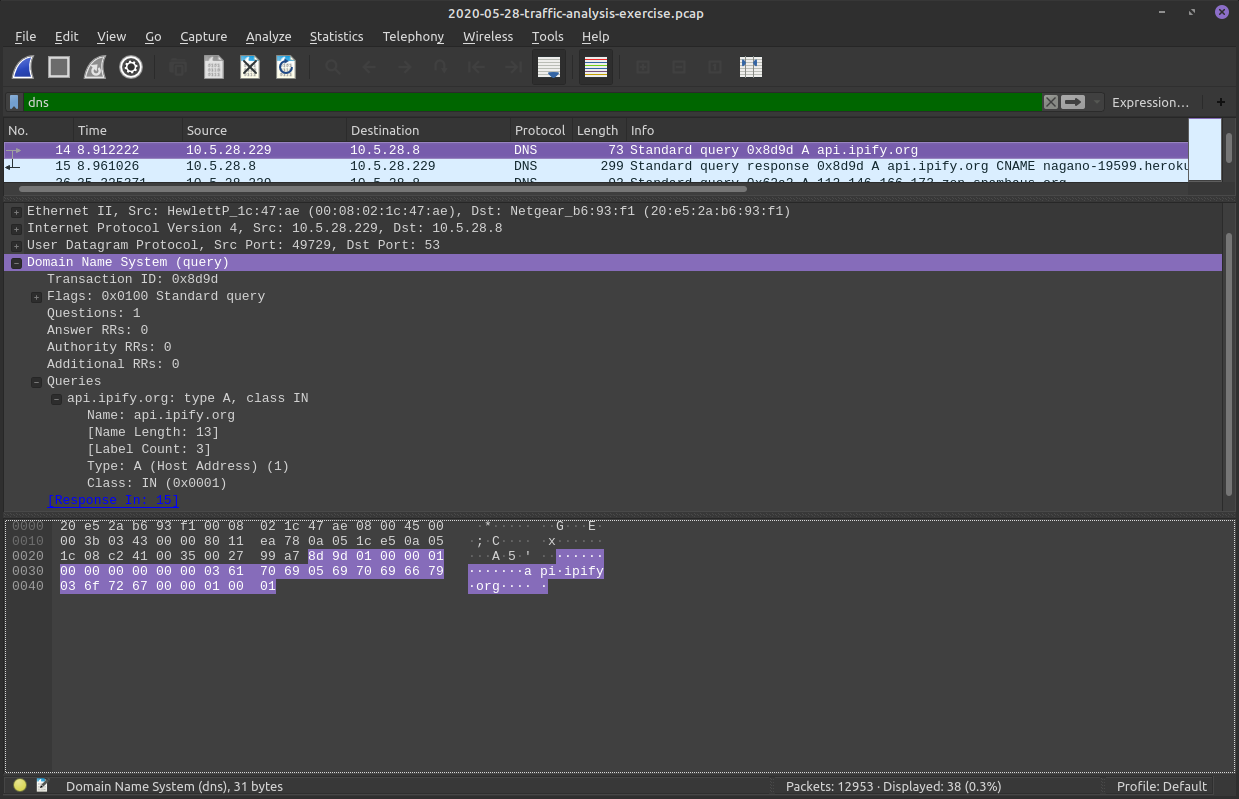
First Filter!
Notice the header we select is highlighted in the hex dump as well!

First Filter!
Same thing for the Fields of a frame!
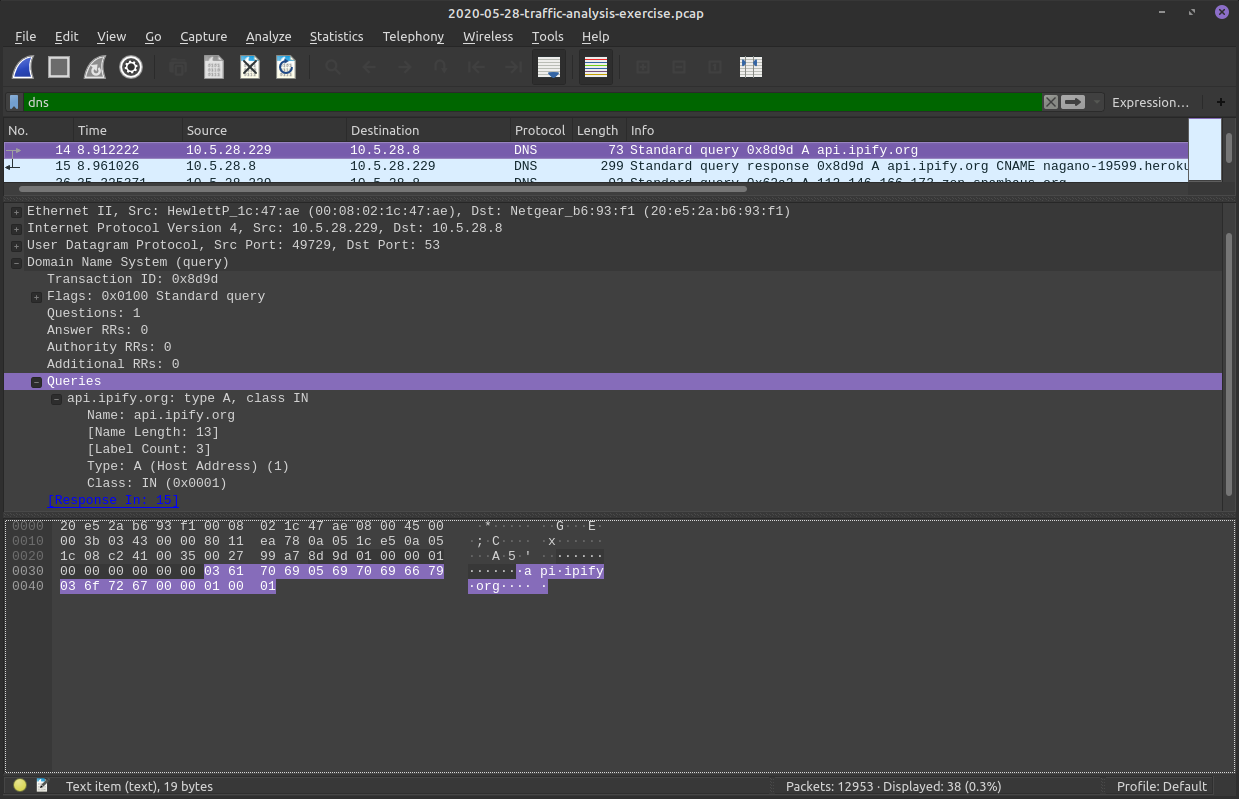
First TCP Stream filter!
Lets look as some HTTP data in isolation
First TCP Stream filter!
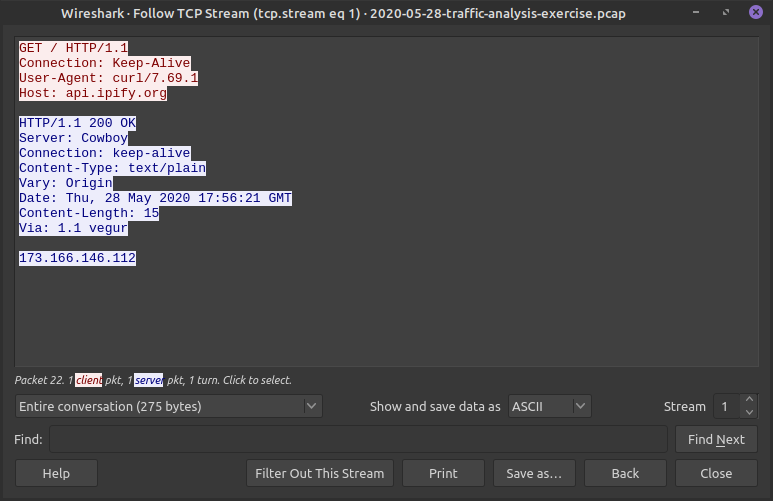
Here we can see the whole HTTP conversation in plaintext (from the TCP filter we made)
The client sent the red HTTP messages
The server respsonded in blue
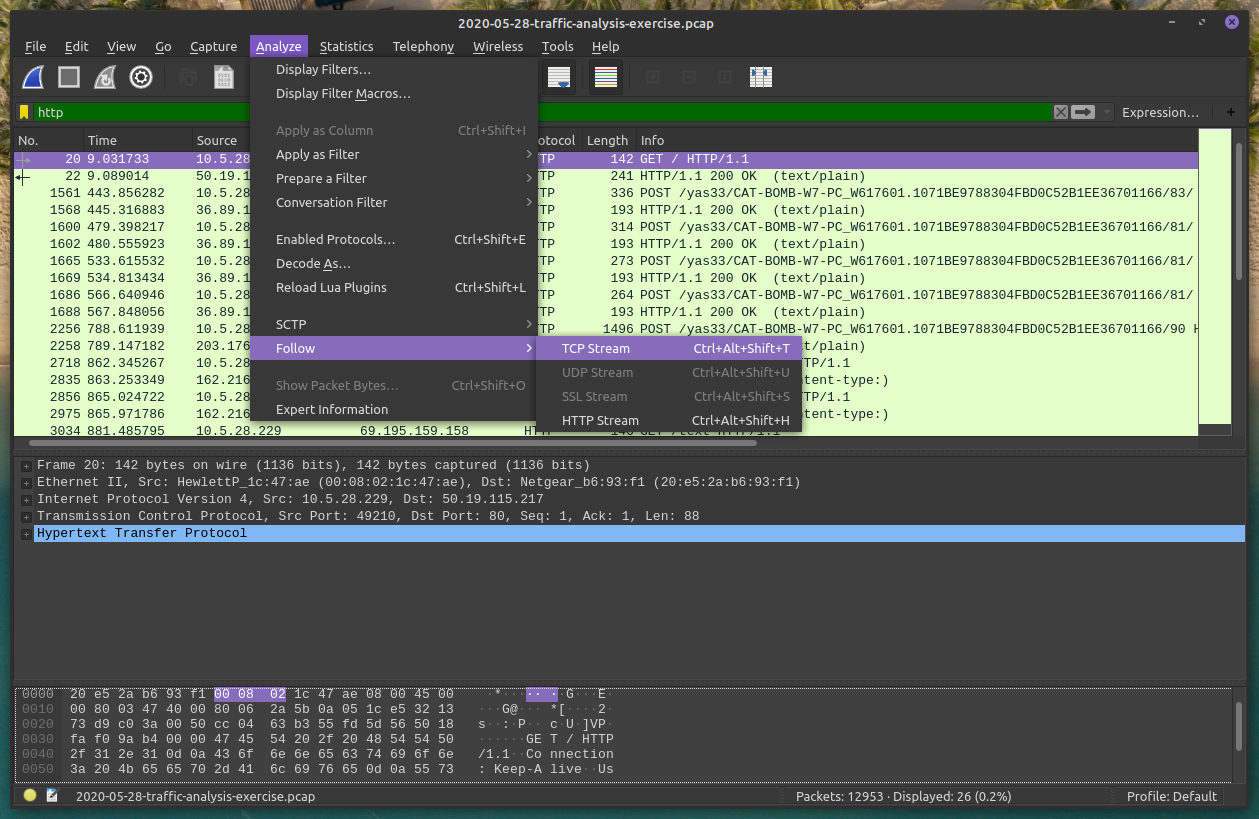
First TCP Stream filter!
We can look at other TCP streams (not just the HTTP ones) in this window as well!

First TCP Stream filter!
We can look at other TCP streams (not just the HTTP ones) in this window as well!
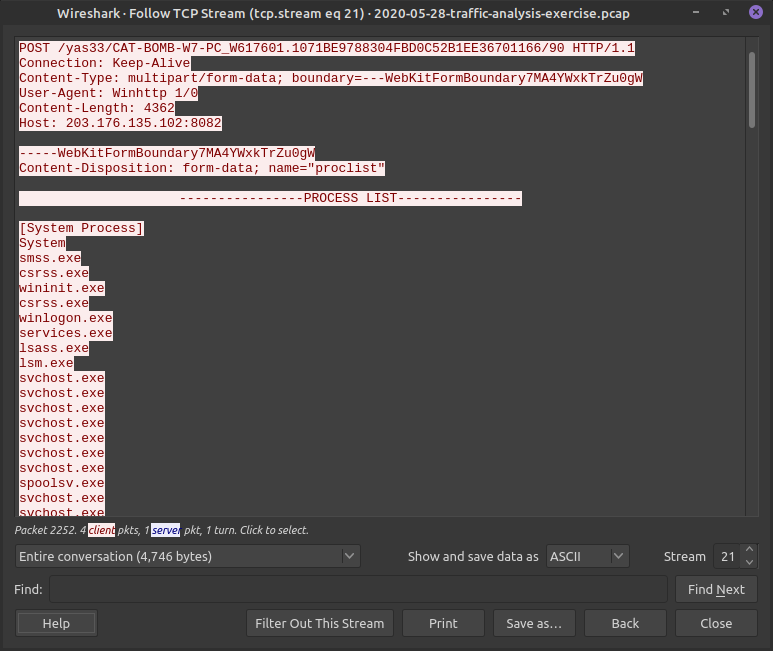
First TCP Stream filter!
Just flipping through streams we might find something, but if there are a lot of streams we might need to narrow our search

First TCP Stream filter!
This stream looks odd?
Looks like a process list from the client is being send to back! That's not normal!

Malware Traffic Analysis


Today we are looking at Catbomber!
CATBOMBER
This network uses Active Directory, basically the domain controller here "authenticates and authorizes all users and computers in a Windows domain type network." This is pretty common in these types of challenges.
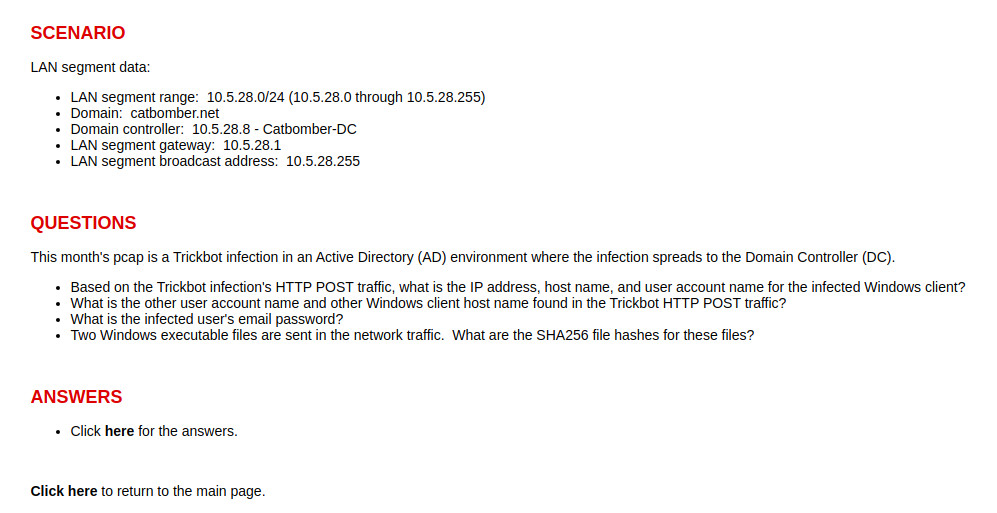
CATBOMBER
We want to know:
- Which computer and user was infected first and their password
- What other users and computers were found by the Trickbot
- The executables that were sent

CATBOMBER
"Based on the Trickbot infection's HTTP POST traffic..."
Lets filter on HTTP POST first with:
http.request.method == "POST"

CATBOMBER
We know 10.5.28.8 is the DC and not the initial infected client, because the prompt said "where the infection spreads to the Domain Controller (DC)"

CATBOMBER
That leaves 10.5.28.229 to be the initial infected computer here.
Lets take a deeper look!

CATBOMBER
Can we see some sort of MIME data encapsulated here? We want to look at the Data in plaintext so lets right click and Show Packet Bytes. We'll do this for each of these POST packets
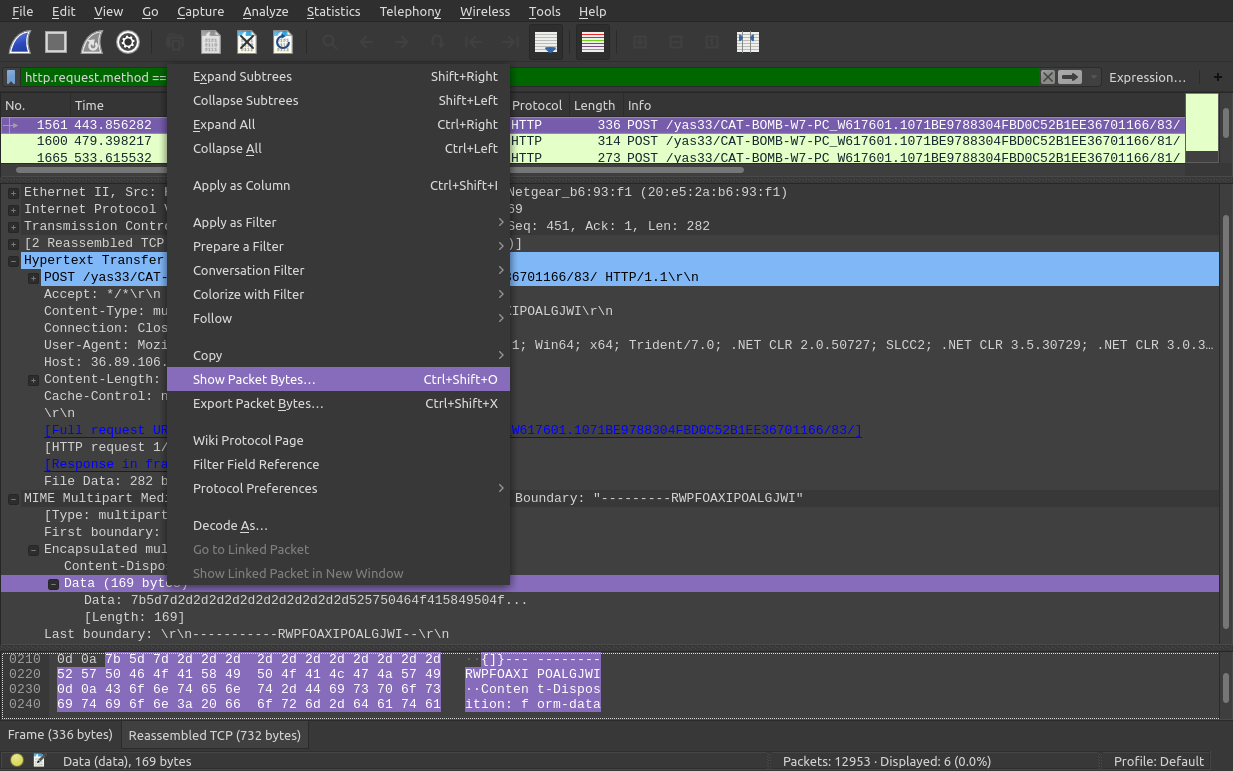
CATBOMBER
Packet 1561- nothing interesting...
CATBOMBER
Packet 1600 - This looks interesting! we got the username and password!
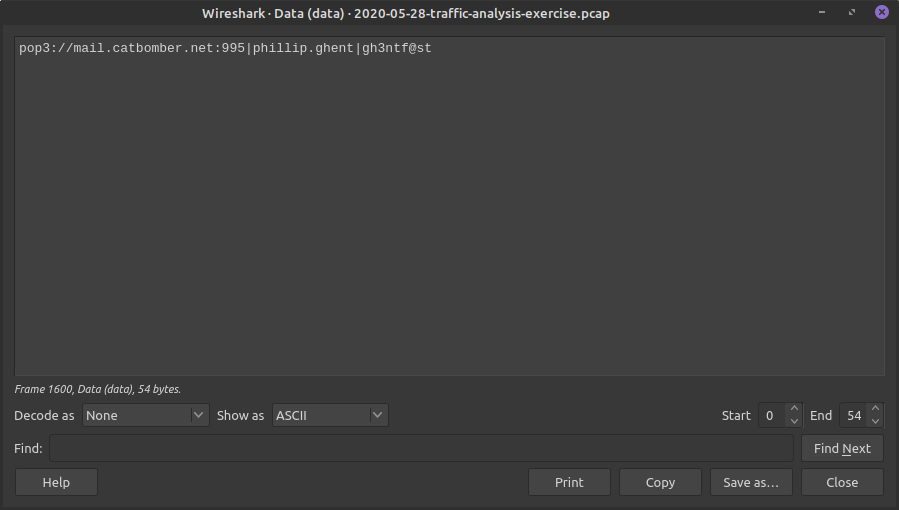
CATBOMBER
Packet 2256 - Has two Encapsulated parts, if we look at both we can see the Process list and ipconfig info!
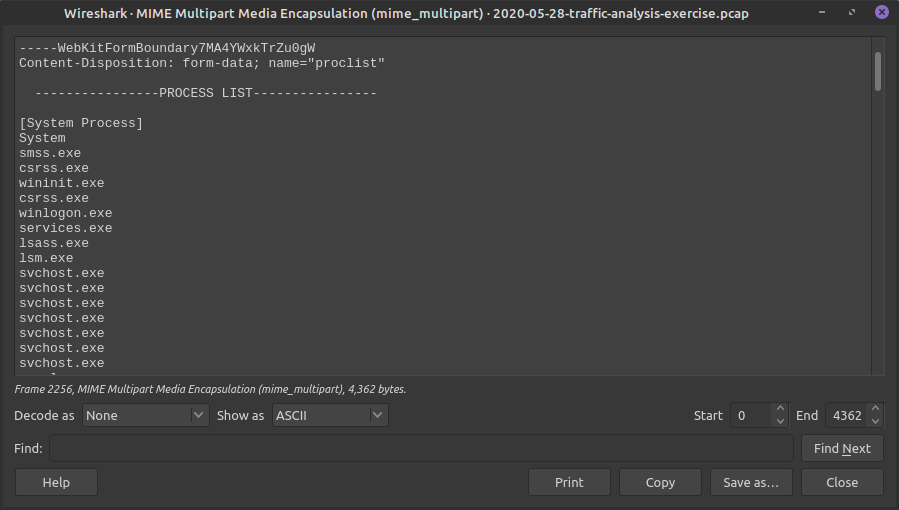
CATBOMBER
Packet 2256 - Has two Encapsulated parts, if we look at both we can see the Process list and ipconfig info!
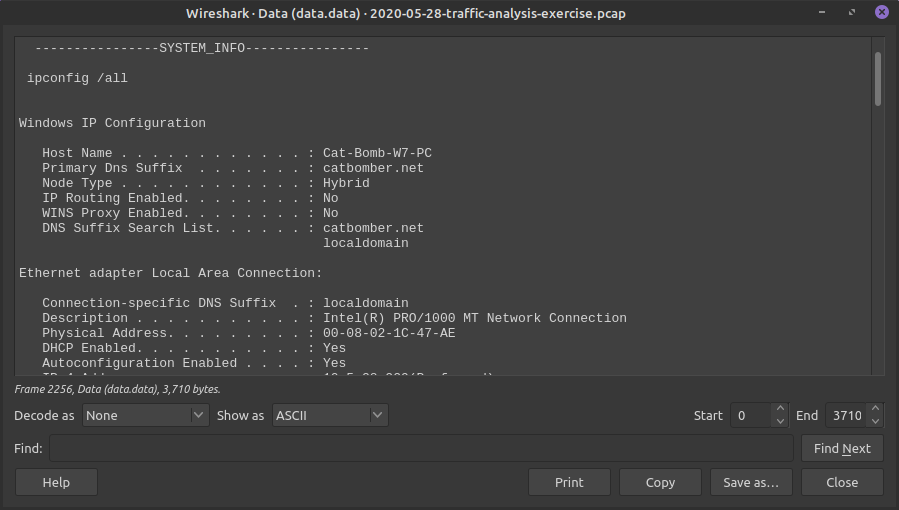
CATBOMBER
Can you find the last pieces of information now?
- Other username on Domain Controller
- Other machine host name
- PE executables sent over network

CATBOMBER

Thank you!
Network Forensics 101
By Drake P
Network Forensics 101
This deck is meant to guide beginners through how network forensics is conducted and how to use tools like wireshark. Resources in this deck come from Malware-Traffic-Analysis.net and highly recommend visiting their website!
- 630



