Heimdall
Ivan Zlatanov - NTBHS
Yavor Papazov - CyResLab
The problem
- USB mass storage devices are utilized in cyberattacks
- The problem is weakly addressed
- There is a lack of proper detection and therefore prevention methods
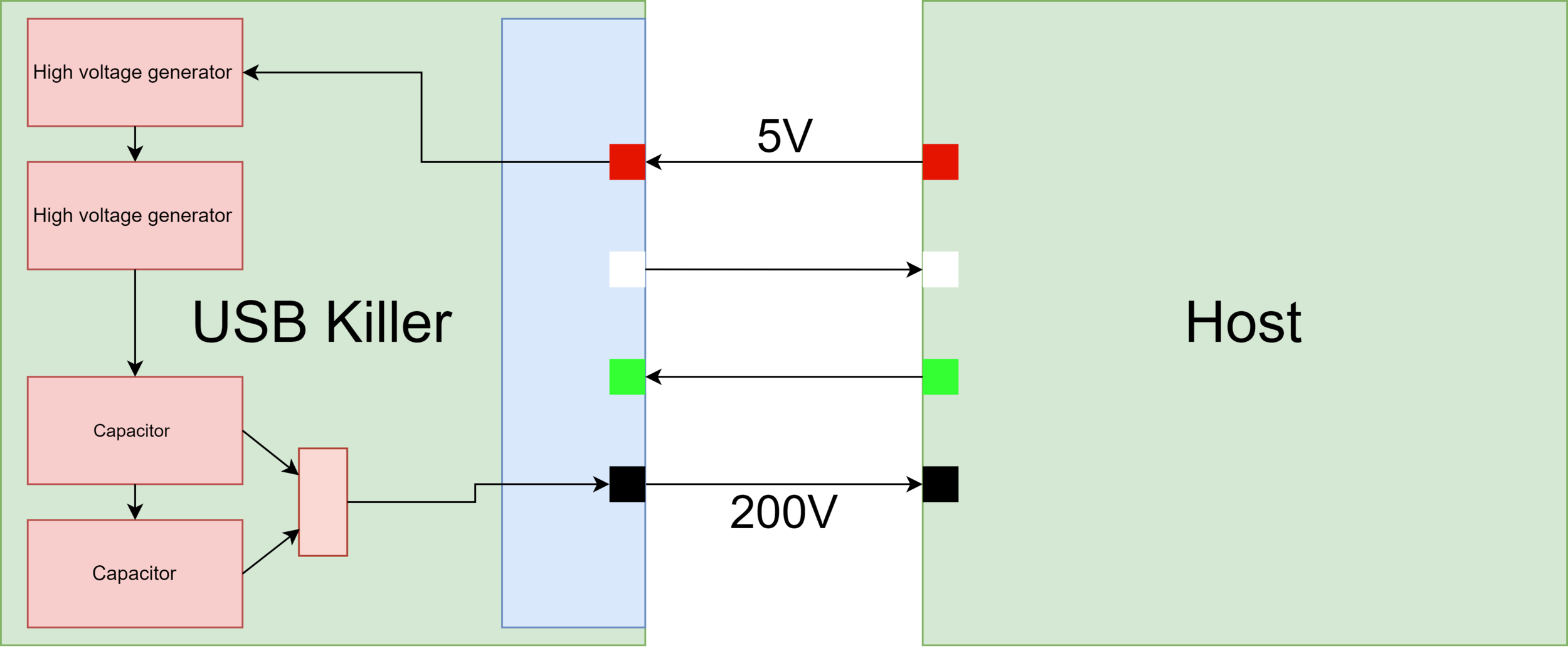
Attacks: USB killer
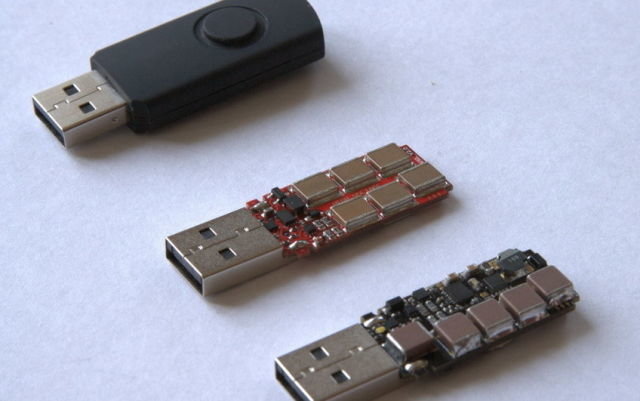
Attacks: USB killer
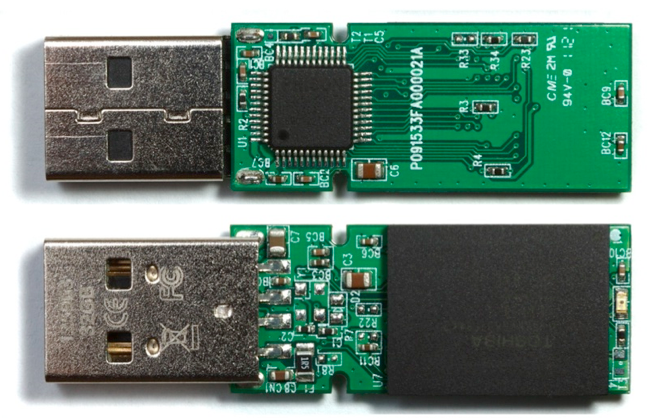
Attacks: Alternated firmware
Attacks: Backdoored live-boot OS

Attacks: Malwares


Our approach
- Framework on an embedded system
- Can detect software and theoretically hardware attacks
- Allows developing custom tests for edge cases
- Verifies the integrity of live-boot distributions of Tails
The tests we developed
- Unplugging simulation
- Device type validation
- Vendor information validation
- Antivirus engine scanning
- Input/Output tests
- Live-boot validation
- OS emulation
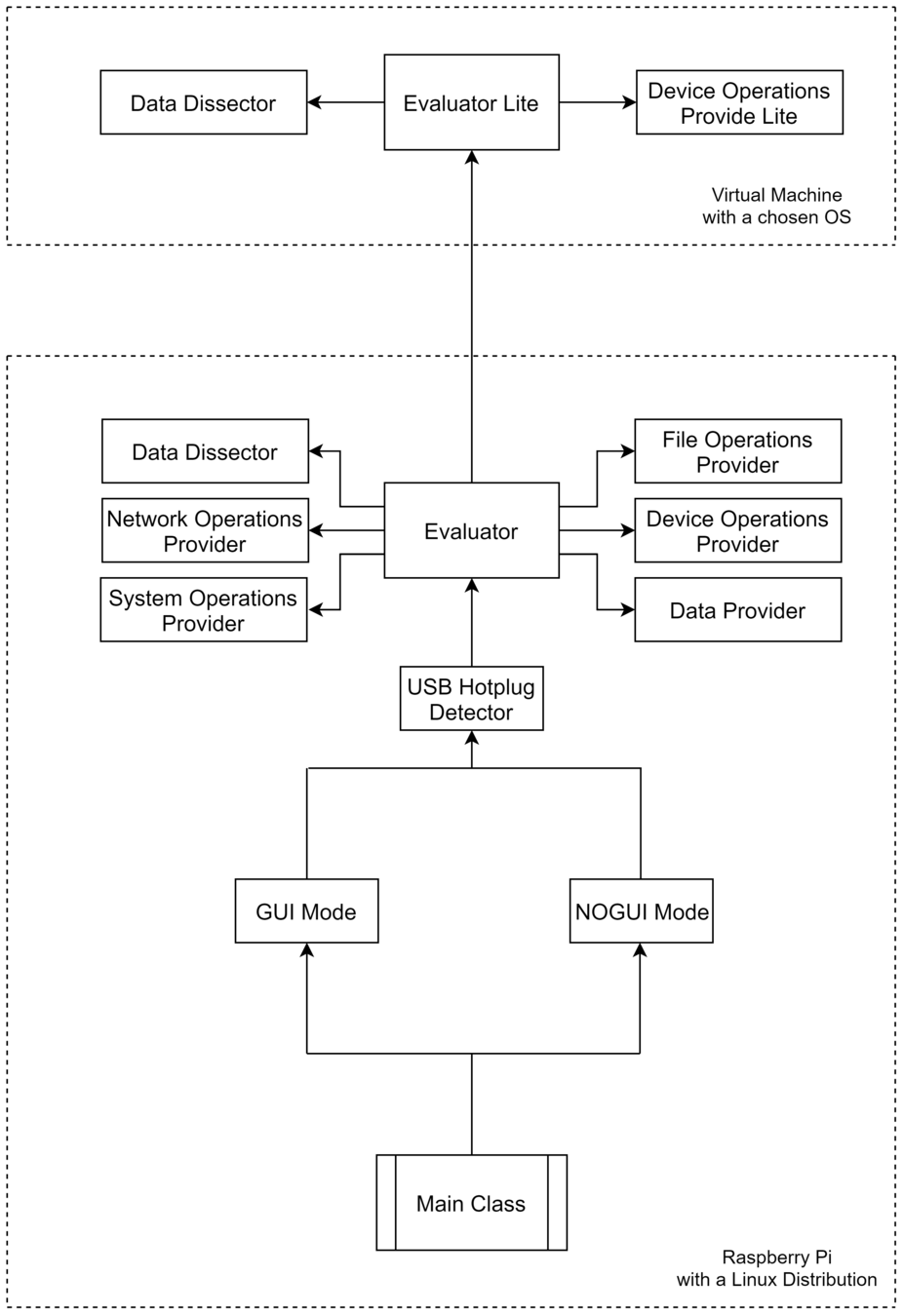
Software architecture
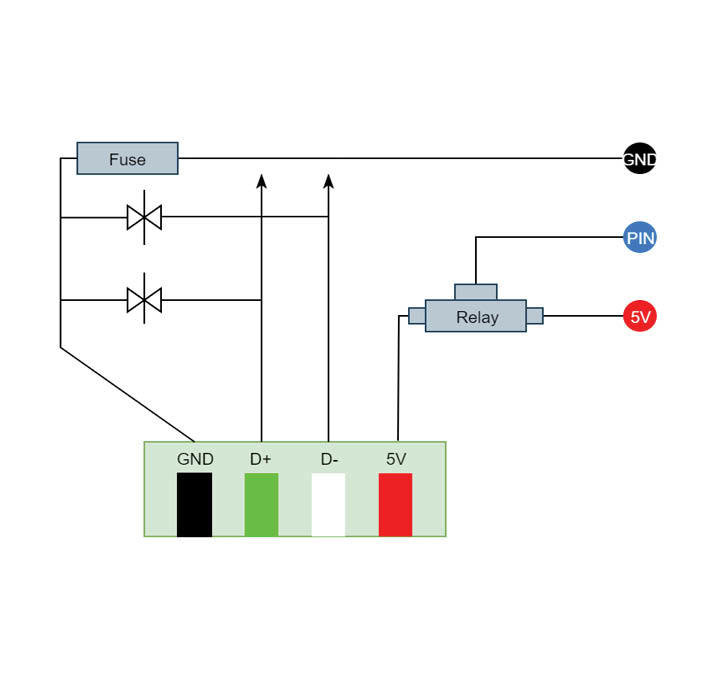
Hardware modifications
- Port Extender
- USB Killer Detector
- Port Power Controller
Port Extender
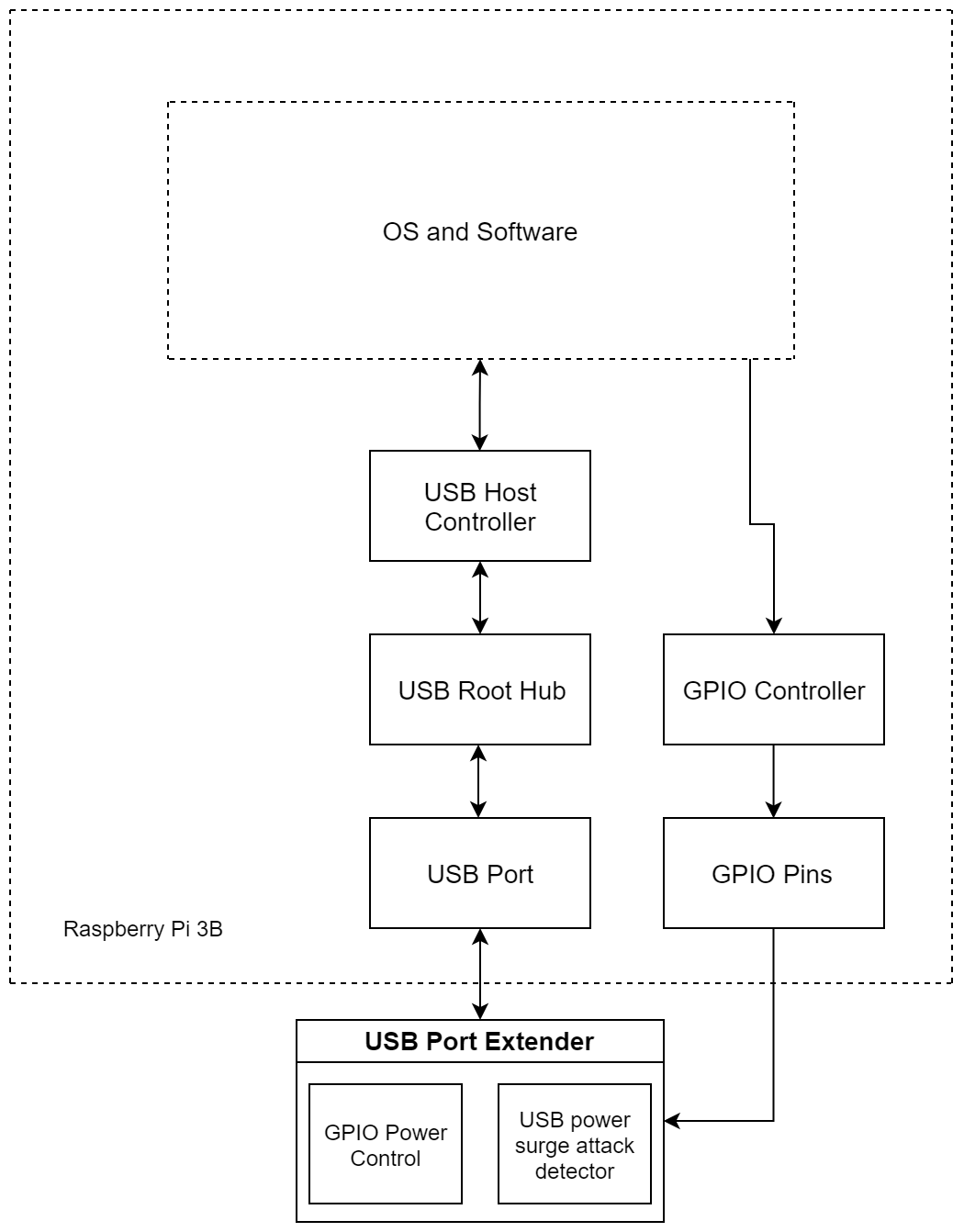
Hardware architecture
Conclusion
Check it out:
Acknoledgments
- To Yavor Papazvo and Konstantin Delchev., for the help of the choice of research topic and guidance during the development process.
- To the team of SAP Labs GK, for the valuable feedback.
- Georgi Sharkov, for providing me test devices.

Heimdall [ENG]
By Ivan Zlatanov
Heimdall [ENG]
- 167



