
Introduction to Namespaces


BC = Before Container
The Monolith
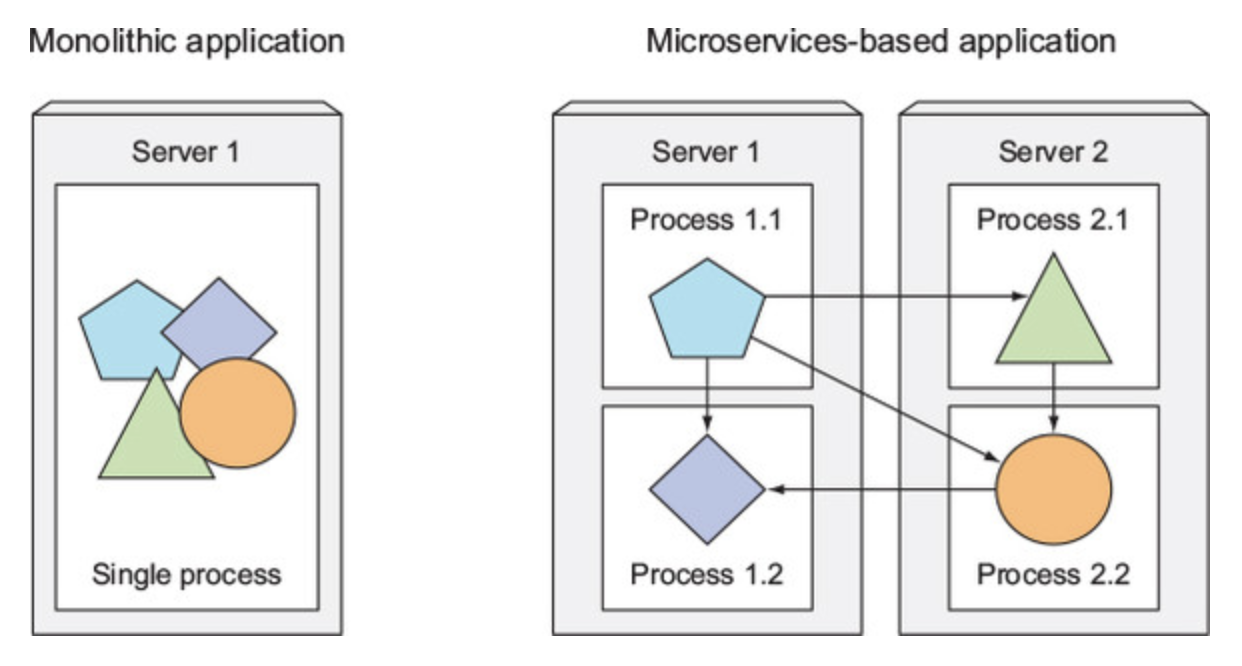
Monolithic vs Microservices
As Uncle Ben Once Said
With great numbers of components comes great responsibility, Peter...

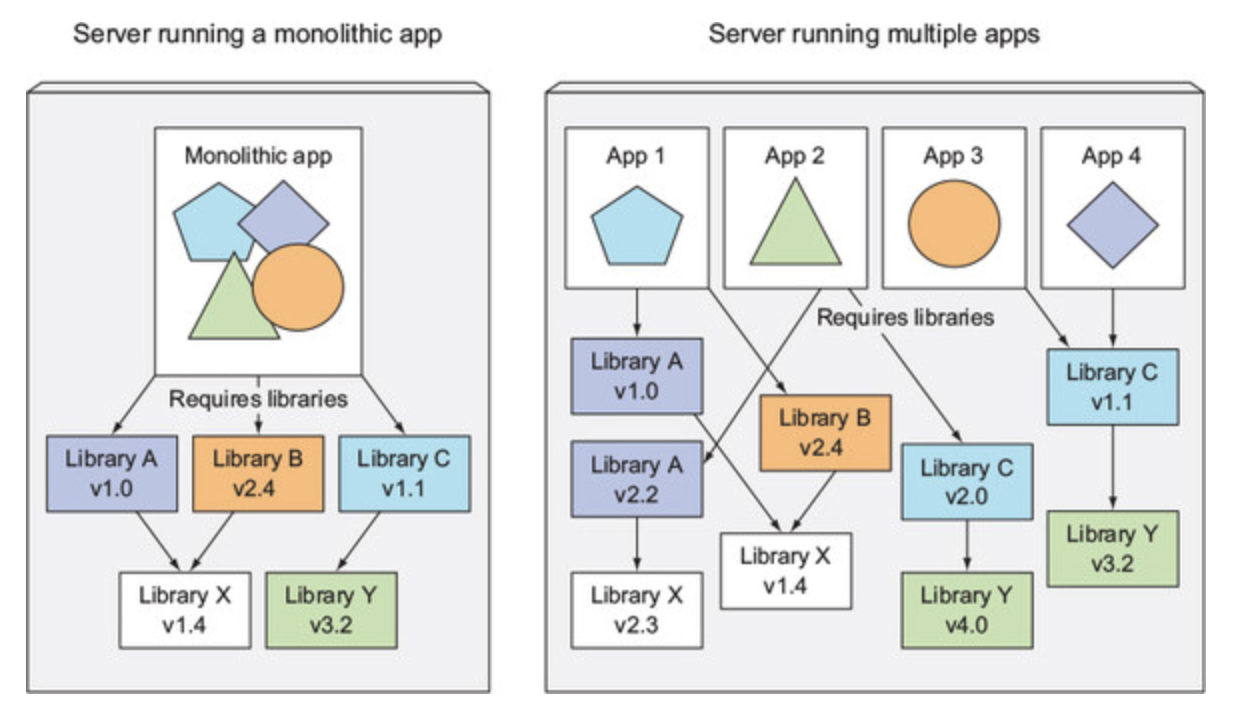
Dependencies Madness
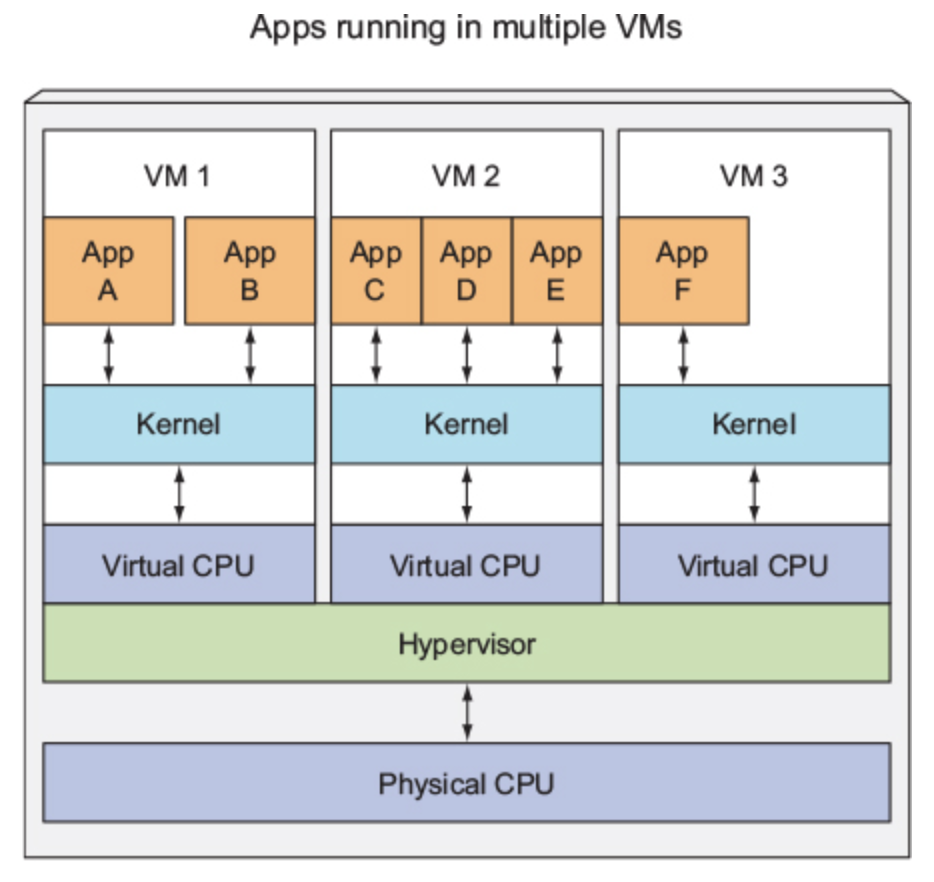
Virtual Machine
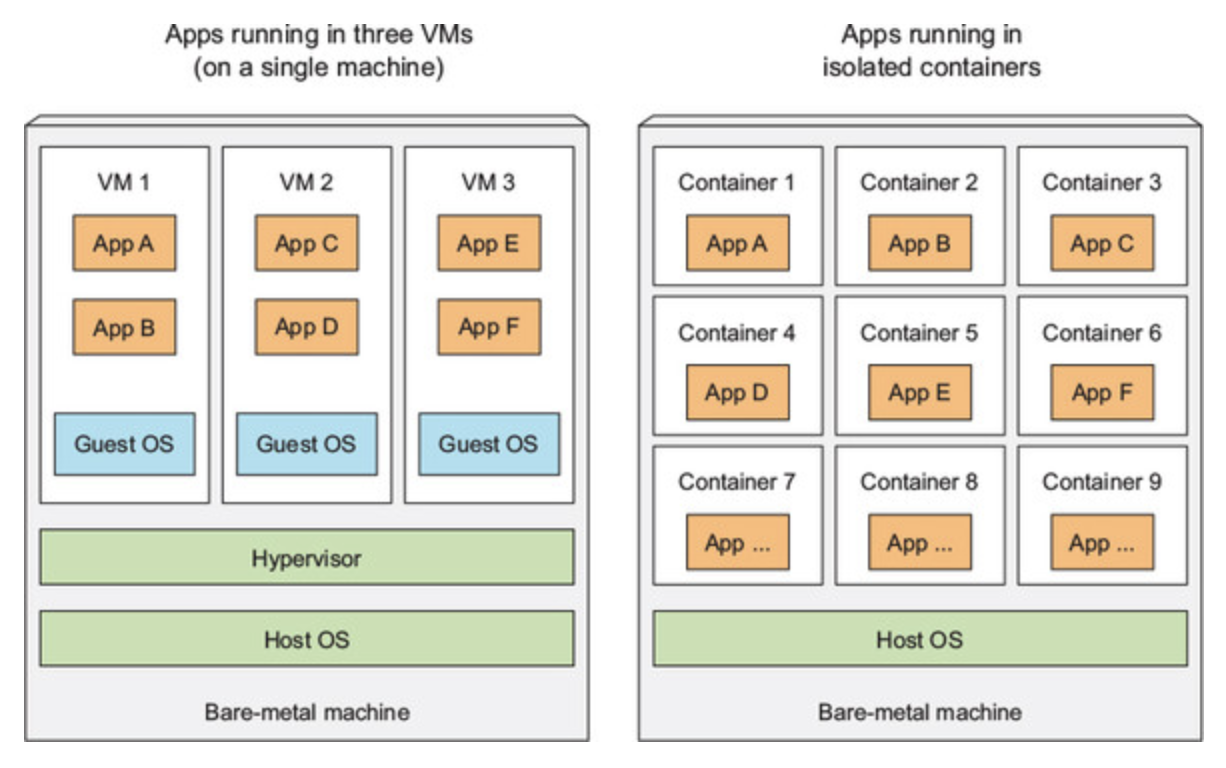
Before containers went mainstream, we isolate components using Virtual Machine (VM). This way, each components can have their own dependencies satisfied without getting in the way of each other.
The problem with VM is that it takes a lot of hardware resources, therefore not ideal for microservices architecture with large number of services.
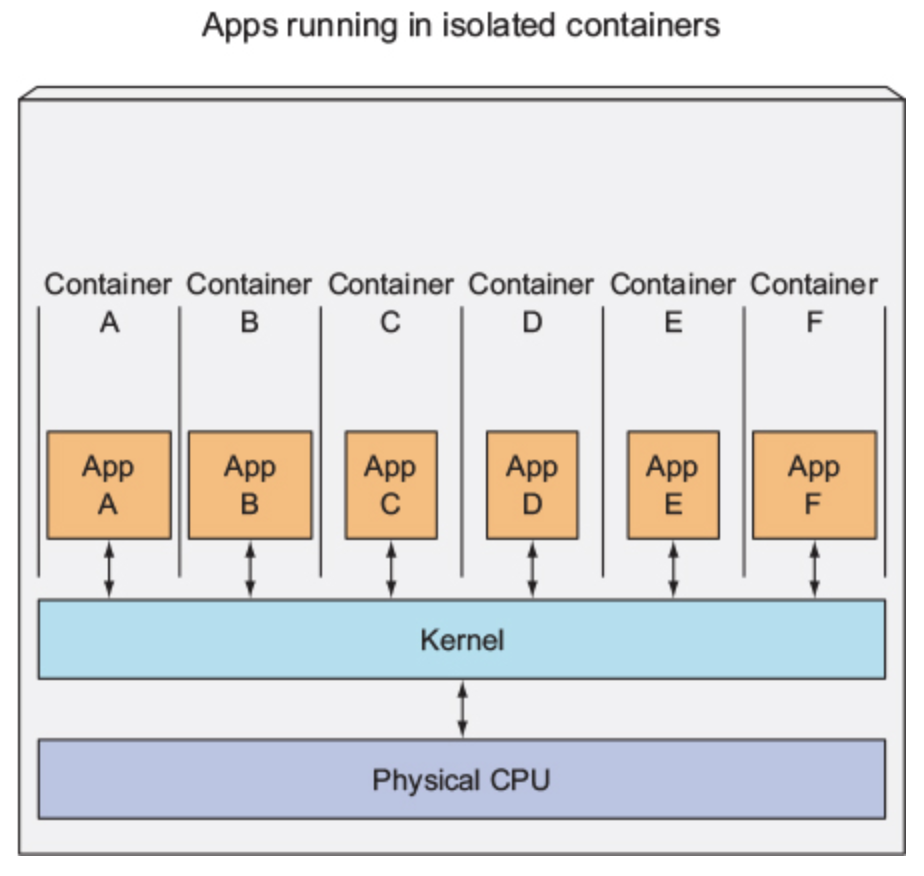
Along Comes Container
VMs:
- Run own OS
- Run own system processes
Containers:
- Run on host OS
- Run as isolated processes in host OS
VM vs Container (1)
VM vs Container (2)
But How is That Possible?
What is Linux Namespace?
A namespace wraps a global system resource in an abstraction that makes it appear to the processes within the namespace that they have their own isolated instance of the global resource.
- Linux Programmer's Manual
Types of Linux Namespaces
- Cgroup - isolates cgroup root directory
- Interprocess Communications (IPC) - isolates system V IPC, POSIX message queues
- Network - isolates network devices, stacks, ports, etc.
- Mount - isolates mount points
- PID - isolates process IDs
- User - isolates user and group IDs
- Unix Timesharing System (UTS) - hostname and NIS domain name
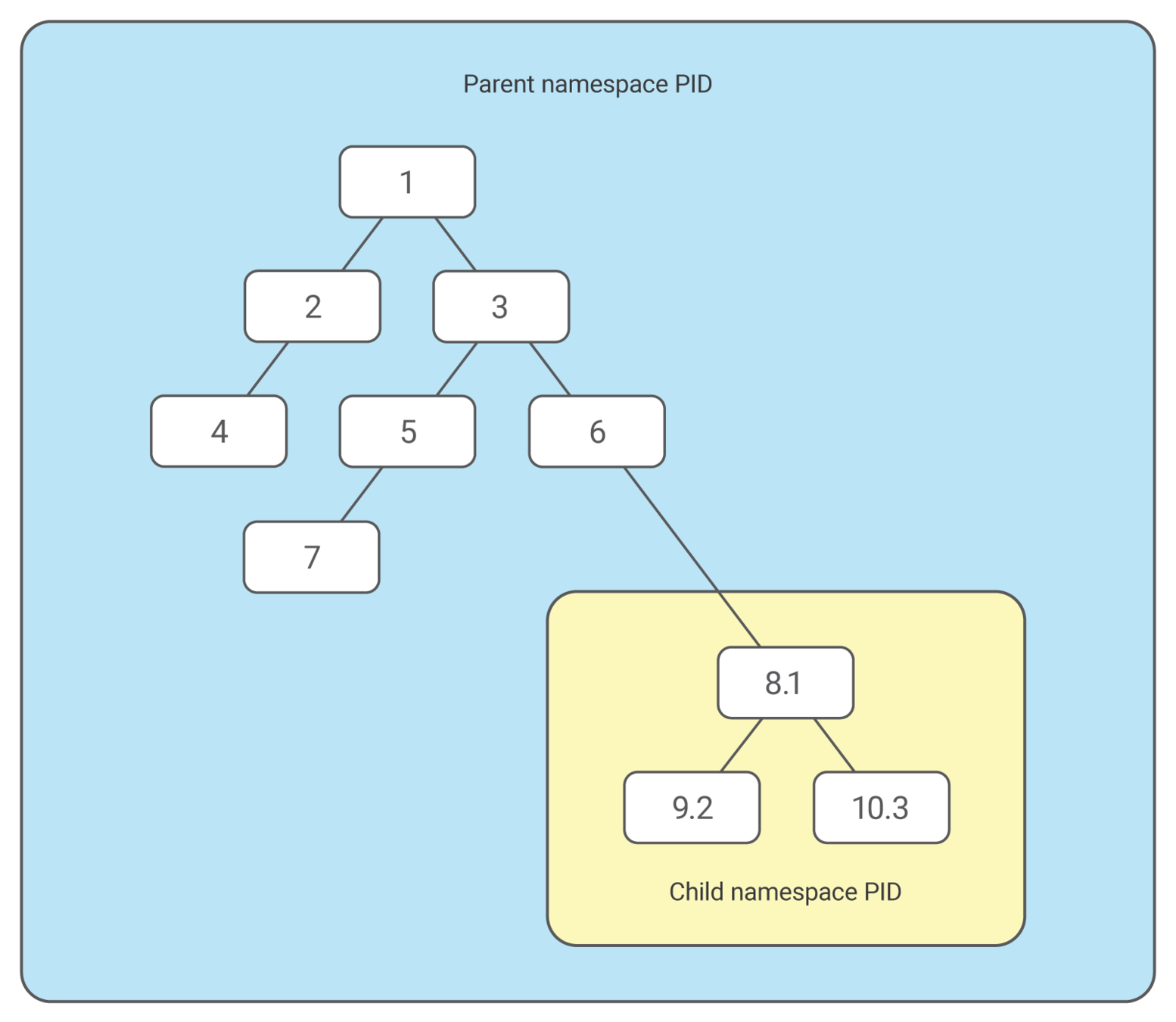
Process Namespace (1)
Historically, the Linux kernel maintained a single process tree. The tree contains a reference to every process currently running in a parent-child hierarchy. A process, given sufficient privileges and certain conditions, can inspect another process by attaching a tracer to it or may even be able to kill it.
Process Namespace (2)
With the introduction of Linux namespaces, it became possible to have multiple “nested” process trees. Each process tree can have an entirely isolated set of processes. This can ensure that processes belonging to one process tree cannot inspect or kill - in fact cannot even know of the existence of - processes in other sibling or parent process trees.
Process Namespace (3)
Network Namespace (1)
A network namespace allows each of these processes to see an entirely different set of networking interfaces. Even the loopback interface is different for each network namespace.
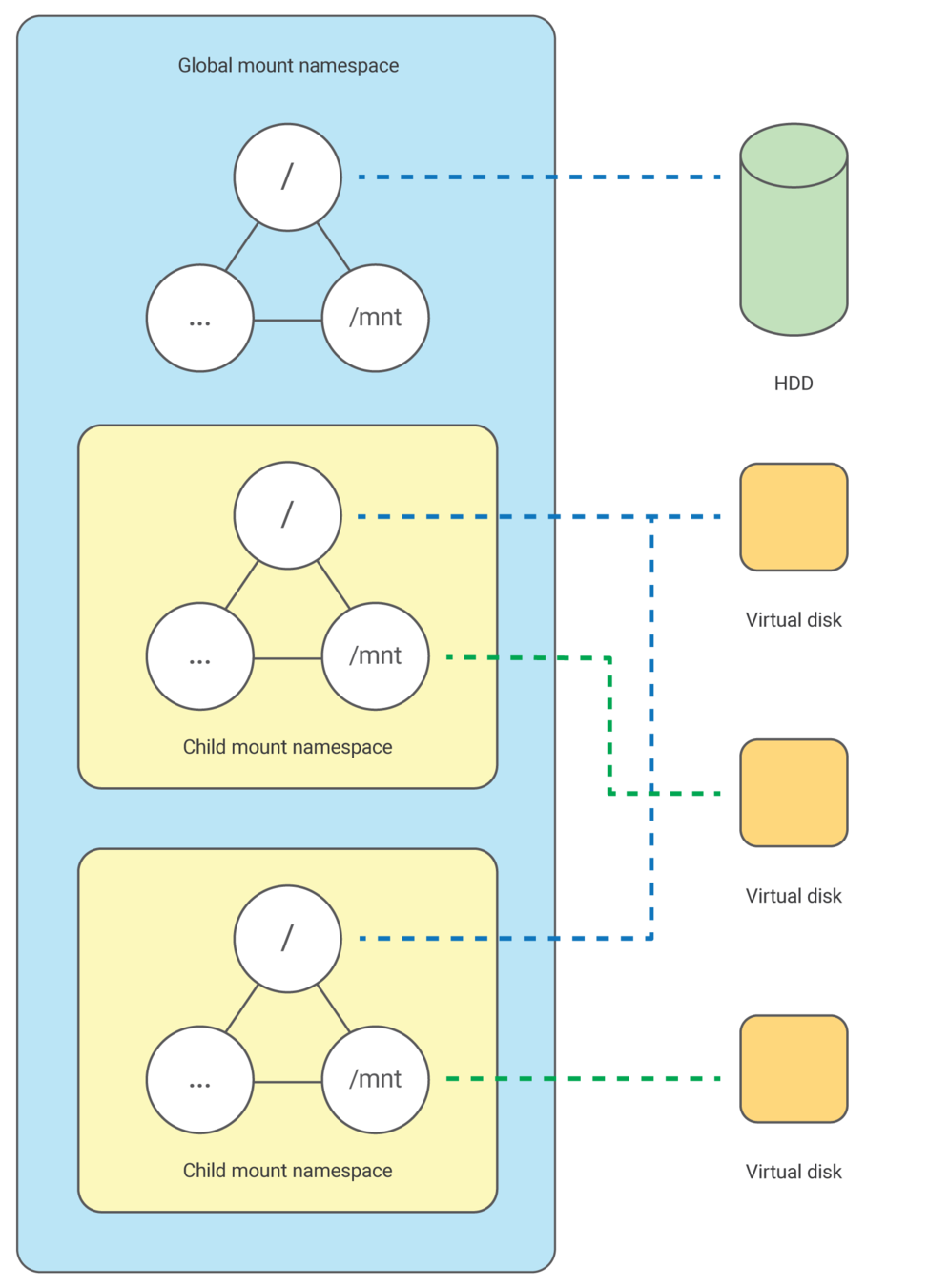
Mount Namespace (1)
Linux maintains a data structure for all the mount points of the system. It includes information like what disk partitions are mounted, where they are mounted, whether they are readonly, etc. With Linux namespaces, one can have this data structure cloned, so that processes under different namespaces can change the mount points without affecting each other.
Mount Namespace (2)
Other Namespaces
There are other namespaces that these processes can be isolated into, namely user, IPC, and UTS.
The user namespace allows a process to have root privileges within the namespace, without giving it that access to processes outside of the namespace.
Isolating a process by the IPC namespace gives it its own interprocess communication resources, for example, System V IPC and POSIX messages.
The UTS namespace isolates two specific identifiers of the system: nodename and domainname.
Demo!
Source Code
If you want to replicate what we do in this session, take a look at this repository.
References
- Kubernetes in Action, Mario Luksa
- Linux Programmer's Manual
- LWN [1][2]
- Isolating Your System with Linux Namespaces, Mahmud Ridwan
- Container from Scratch, Liz Rice
Introduction to Namespaces
By qblfrb
Introduction to Namespaces
- 560



