DOM Clobbering
from HTML injection to controlling JS variables

xanhacks - HitchHack 2023
https://slides.com/xanhacks/dom-clobbering/
image: https://portswigger.net/research/dom-clobbering-strikes-back
Definition
Define (and occasionally manipulates)
Javascript variables from HTML

You do not write JS code, you can only manipulate a variable that has not been defined.

HTML Injection != Javascript Injection

- Rich text input
-
Can be found in:
- Forum post
- Discord message
-
You can define:
- title, bold, italic, link, images...
- but obviously no JS script
index.html
script.js

HTML Injection
Vulnerable JS (sink)
Attack scenarios
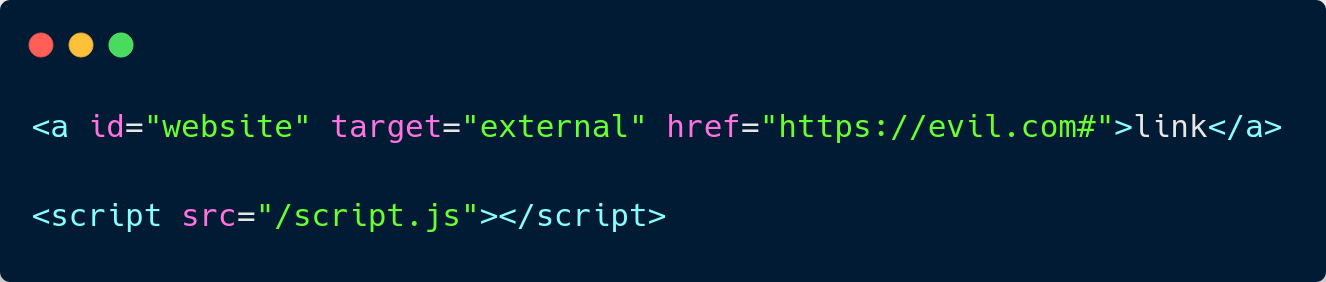
Example n°1 - Redirection
Text
Attack scenarios
index.html
script.js

HTML Injection
Vulnerable JS (sink)

Example n°2 - JS Execution
Attack scenarios
Prerequisites : HTML Injection & JS Sink
Goal : JavaScript execution
Advantages
- Often bypass CSP (Content-Security-Policy)
- DOM Clobbering attacks are almost unknown
Disadvantage
- Very rare to get an HTML injection AND a sink
Theory
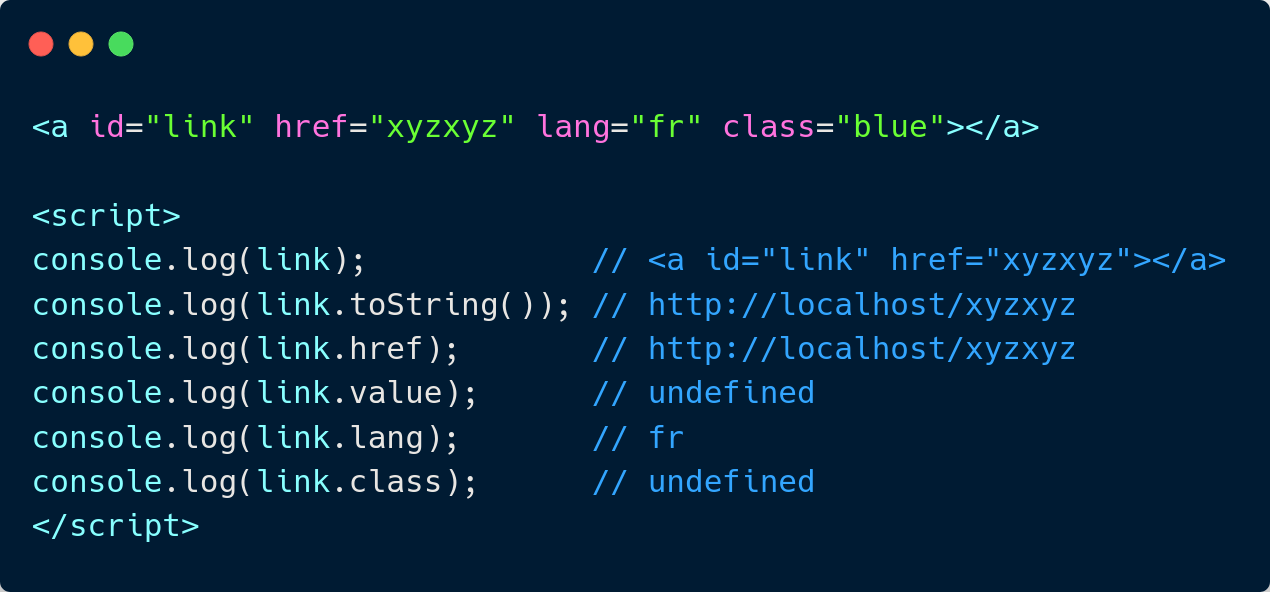
What to clobber?
Some HTML attributes
https://github.com/xanhacks/DOM-Clobbering-Generator/
What to clobber?
id or name

We can also create a variable using the name property, but this works only for:
-
embed,form,iframe,image,img,object
What to clobber?
Three levels
We can use form to clobber variables at a depth of 3
first.second.third

What to clobber?
More than three levels
We can use iframe to clobber variables at a depth of 4 and more
first.second.third.fourth first.second.third.fourth.fifth...


Real world use-case
[html-janitor] Arbitrary HTML can bypass the sanitization process
https://hackerone.com/reports/308158


Practice DOM Clobbering attacks
- https://portswigger.net/web-security/dom-based/dom-clobbering
- https://www.root-me.org/fr/Challenges/Web-Client/DOM-Clobbering
Challenges

Whoami
@xanhacks






https://www.offensiveweb.com/
End! Question?
DOM Clobbering
By xanhacks
DOM Clobbering
- 1,540



