Malware homelab & analysis automation
@xanhacks - Hack2G2 workshop
October 2023
https://slides.com/xanhacks/workshop-malware-hack2g2/
https://github.com/xanhacks/workshop-malware-hack2g2
Prerequisites
1
- docker & docker-compose installed
- Bash shell (or equivalent)
- 5GB of disk storage
- Basic knowledge in a programming language
Exercises
2
- Setup MWDB & Karton using docker-compose
- Create a Python script to add samples on MWDB from a well-known database (like MalwareBazaar)
- Reverse the given malware using dnSpy or ILSpy
- Create a Python script to extract the malware's configuration with dnlib
- Embed the Python script to a Karton task to auto-extract the malware's configuration on new upload
Do not hesitate to ask for help!
Glossary
3
- Malware: Software specifically designed to disrupt, damage, or gain unauthorized access to computer systems.
- Sample: A file representative of a malware.
- Malware's configuration: Settings of the malware (C2 IP address/port, version, persistence mechanism...).
- Command & Control server (C&C or C2): A server controlled by an attacker which is used to communicate with the malware.
- Malware types: Ransomware, RAT, Wiper, Worm...
- Hash: A unique cryptographic identifier generated from a malware file.
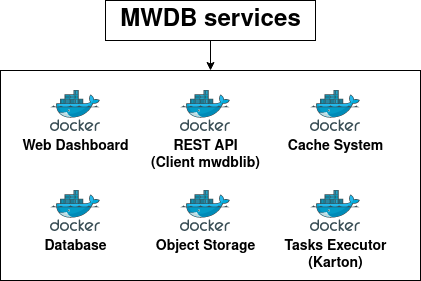
Features
4
-
Database of samples
-
Web API & Interface to view/edit information
-
Automation of :
- Download samples from well-known malware databases to fill our database
- Simple tasks on samples (strings, unzip, exif...)
-
Extraction of malware's configuration
- Easy to deploy and update
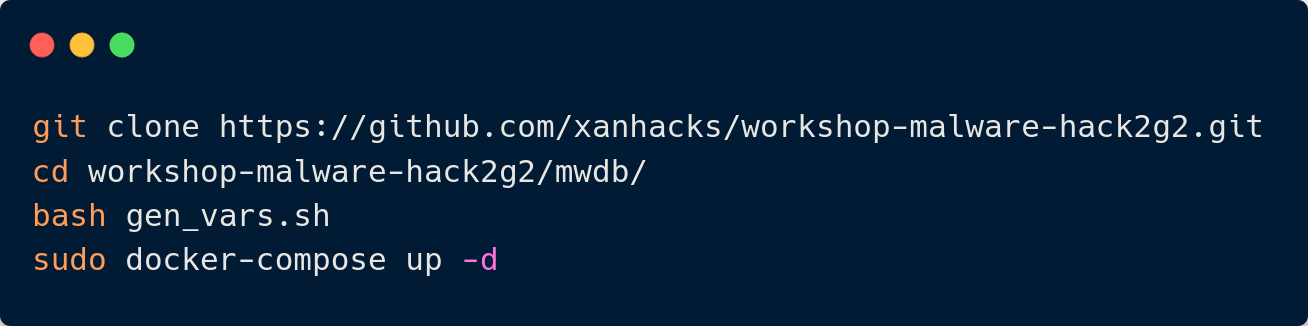
MWDB - Malware Database
5
- Project name: MWDB (Malware Database)
- Github: https://github.com/CERT-Polska/mwdb-core
- Description: Malware repository component for samples & static configuration with REST API interface.
MWDB - Architecture & Docs
6
Documentation
- https://mwdb.readthedocs.io
- https://karton-core.readthedocs.io
- https://mwdblib.readthedocs.io
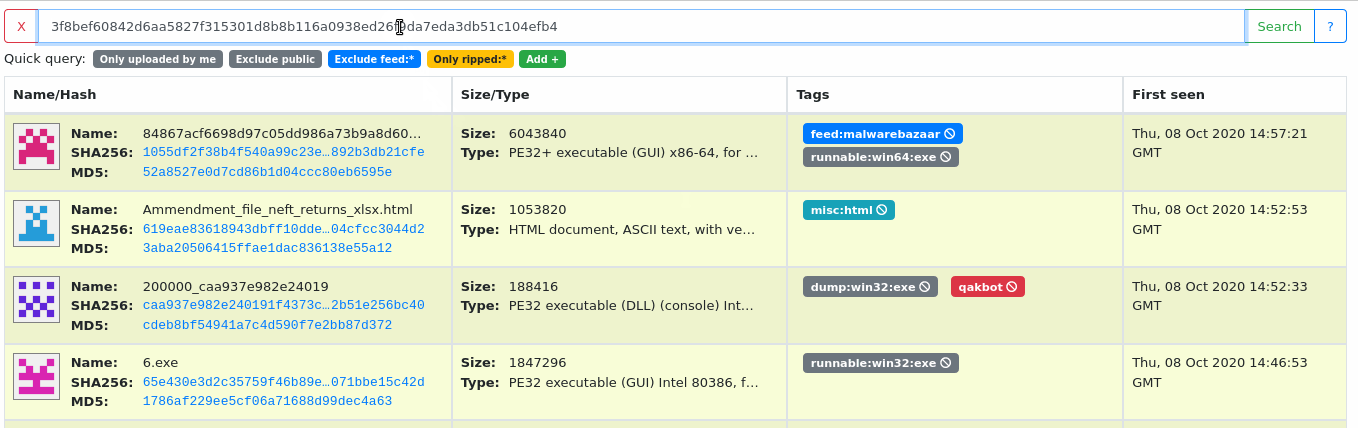
Download samples from Internet
7
-
Well-known malware databases:
- VirusTotal (enterprise account)
- Tria.ge (free - account needed)
- MalwareBazaar (free - no account)
- ...
- Python script to download samples from well-known malware database and upload it to our MWDB.
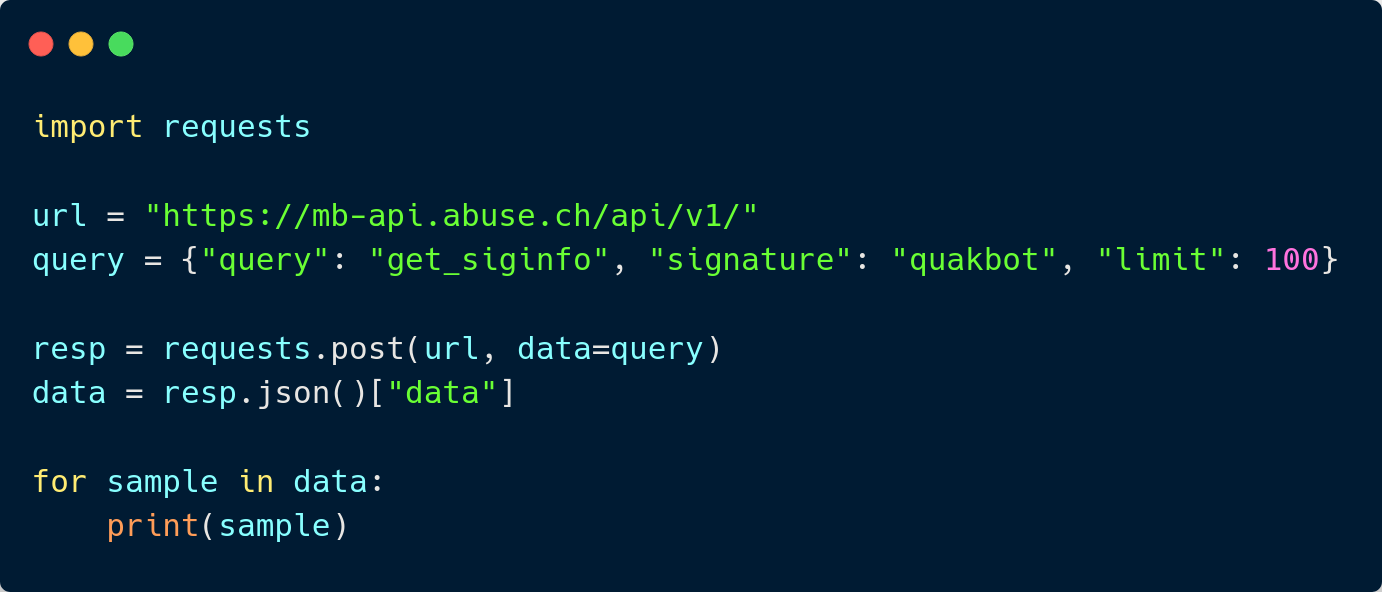
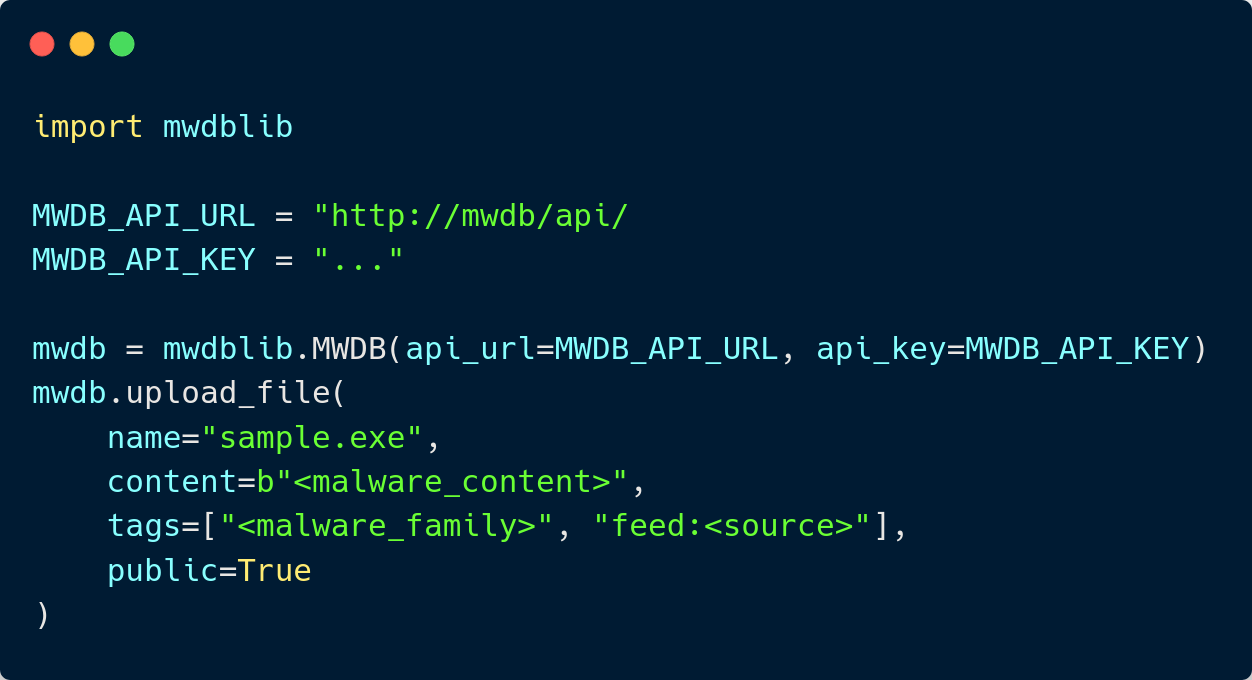
MWDBLIB - Client Python Library
8
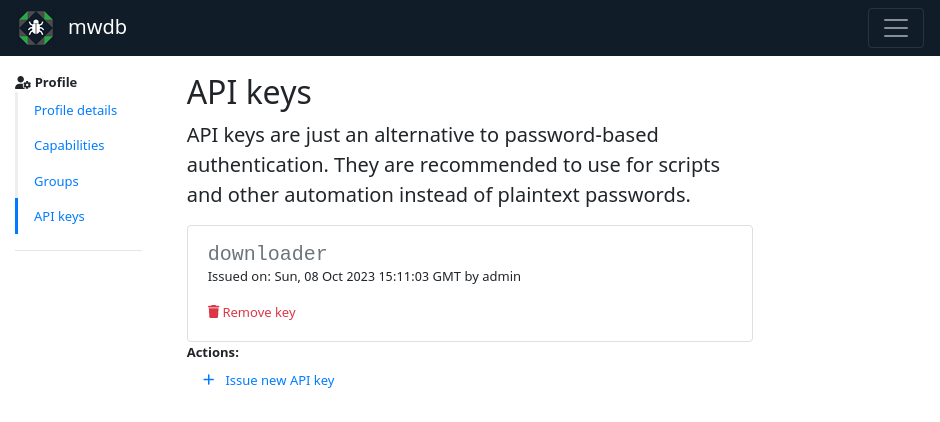
http://mwdb/profile/api-keys
Upload a sample to MWDB using mwdblib
Karton - Tasks executor
9
- Project name: Karton
- Github: https://github.com/CERT-Polska/karton
- Description: Execute tasks on new uploaded samples (integration with MWDB)
New sample
Malware Configuration
Extractor
MWDB
Karton
Success
Fail
Upload
Malware
Configuration
Nothing
Karton - Example of task
10
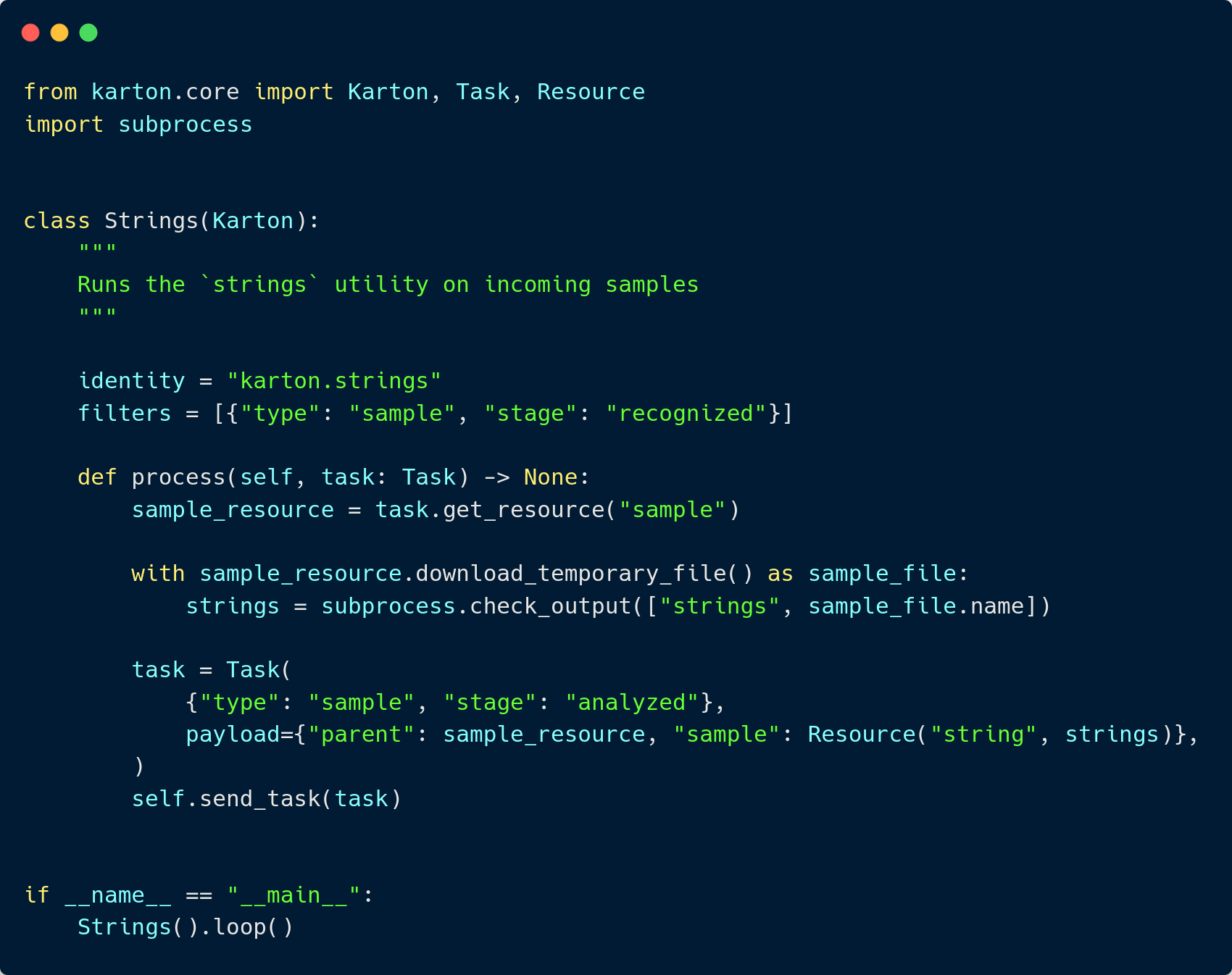
https://github.com/CERT-Polska/karton-playground/
dnSpy - Reversing .NET binaries
11
- Project name: dnSpy
- Github: https://github.com/dnSpy/dnSpy
- Description: .NET debugger and assembly editor
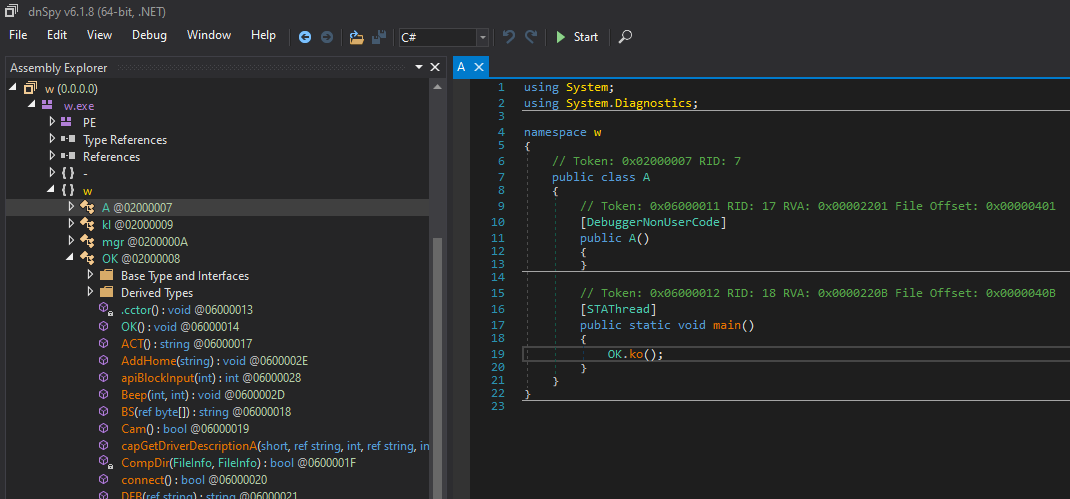
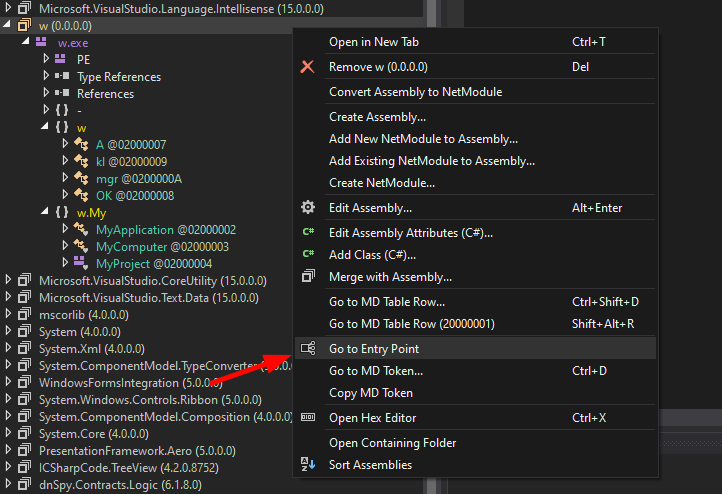
dnSpy - Finding the Entrypoint
12
Right click on the binary -> Go to Entry Point
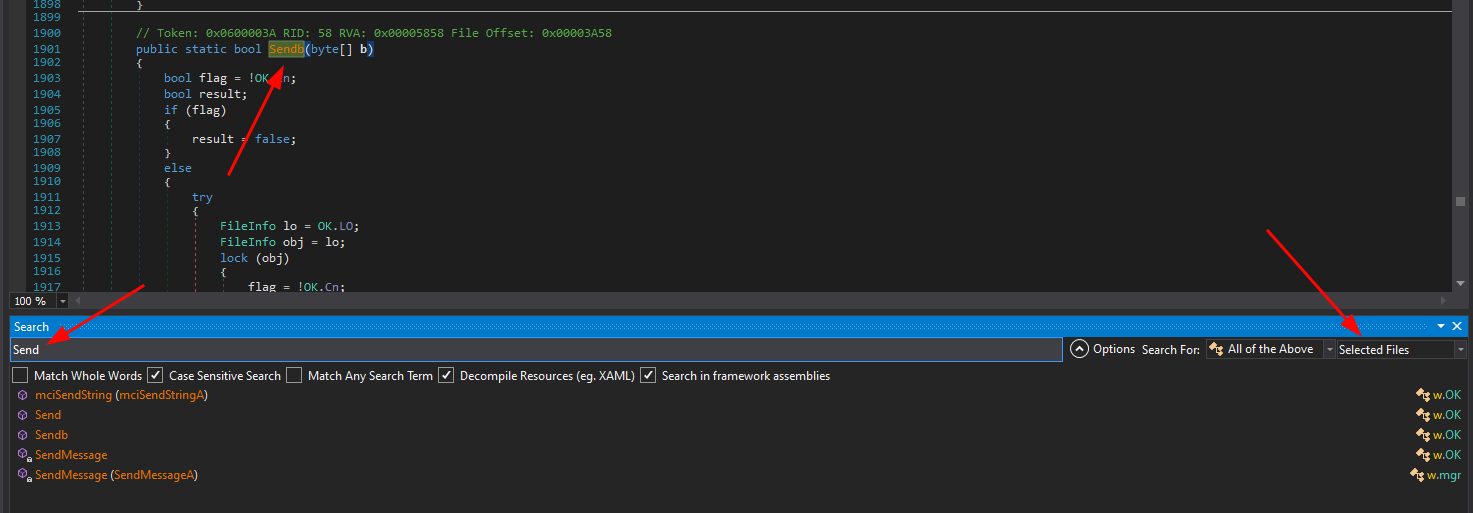
dnSpy - Code search
13
CTRL+F
dnSpy - Usage analysis
14
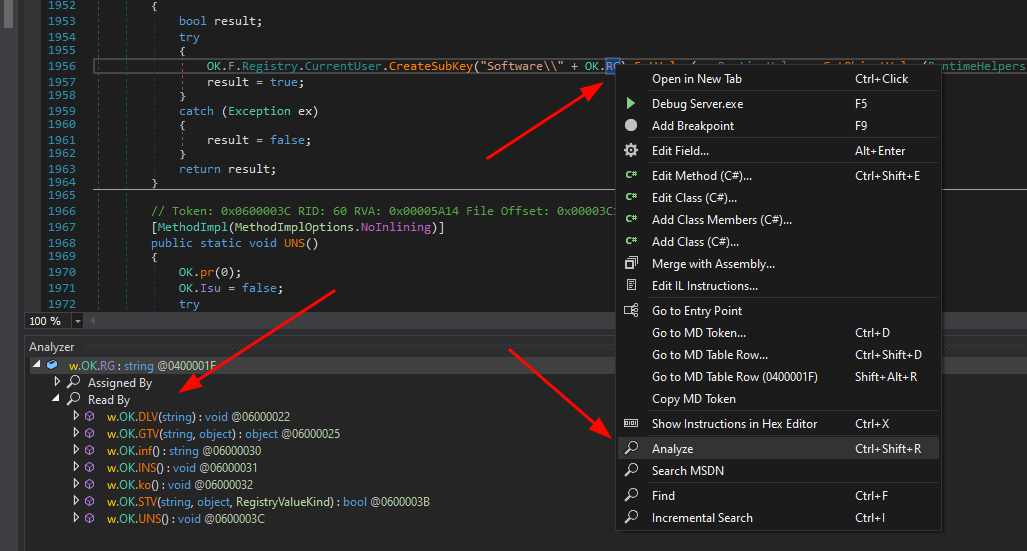
Right click on the symbol -> Analyze
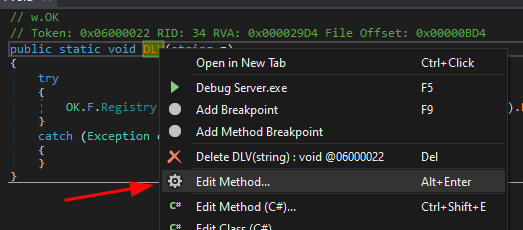
dnSpy - Rename symbols
15
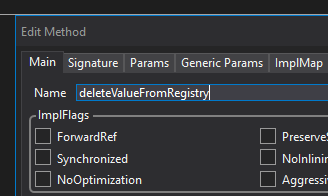
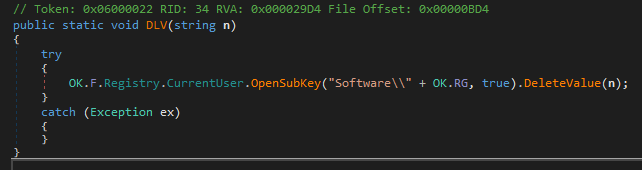
Right click on the symbol -> Edit Field... / Edit Method...
Let's begin!
16
workshop-malware-hack2g2
By xanhacks
workshop-malware-hack2g2
- 673



