Dynamic Analysis
GDB
Gnu Debugger -- Very powerful and is the most popular dynamic analysis tool!
What do we want from gdb?
- Disassembly
- Register contents
- Memory contents
- Step debug
I wish it could step backwards...
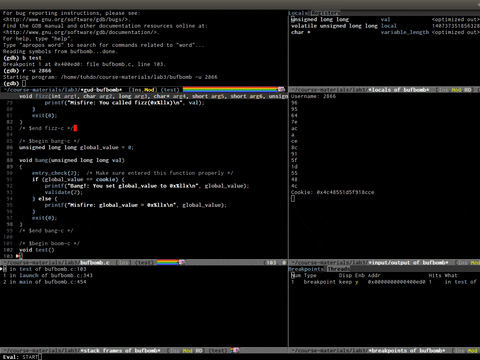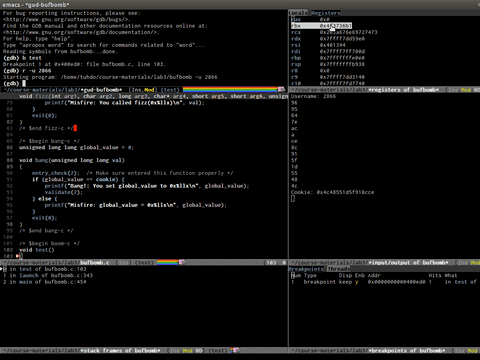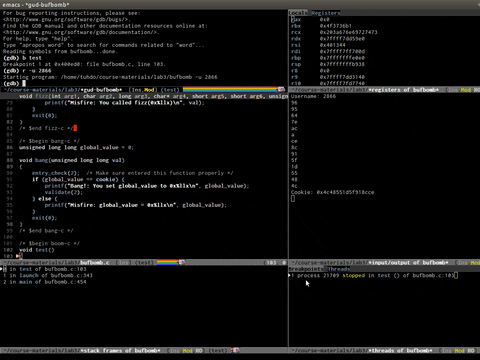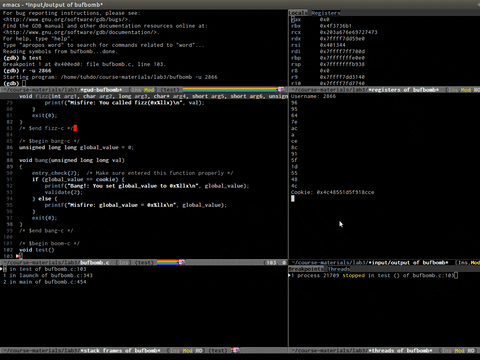
Emacs in GDB mode, Pretty cool, not good for RE.

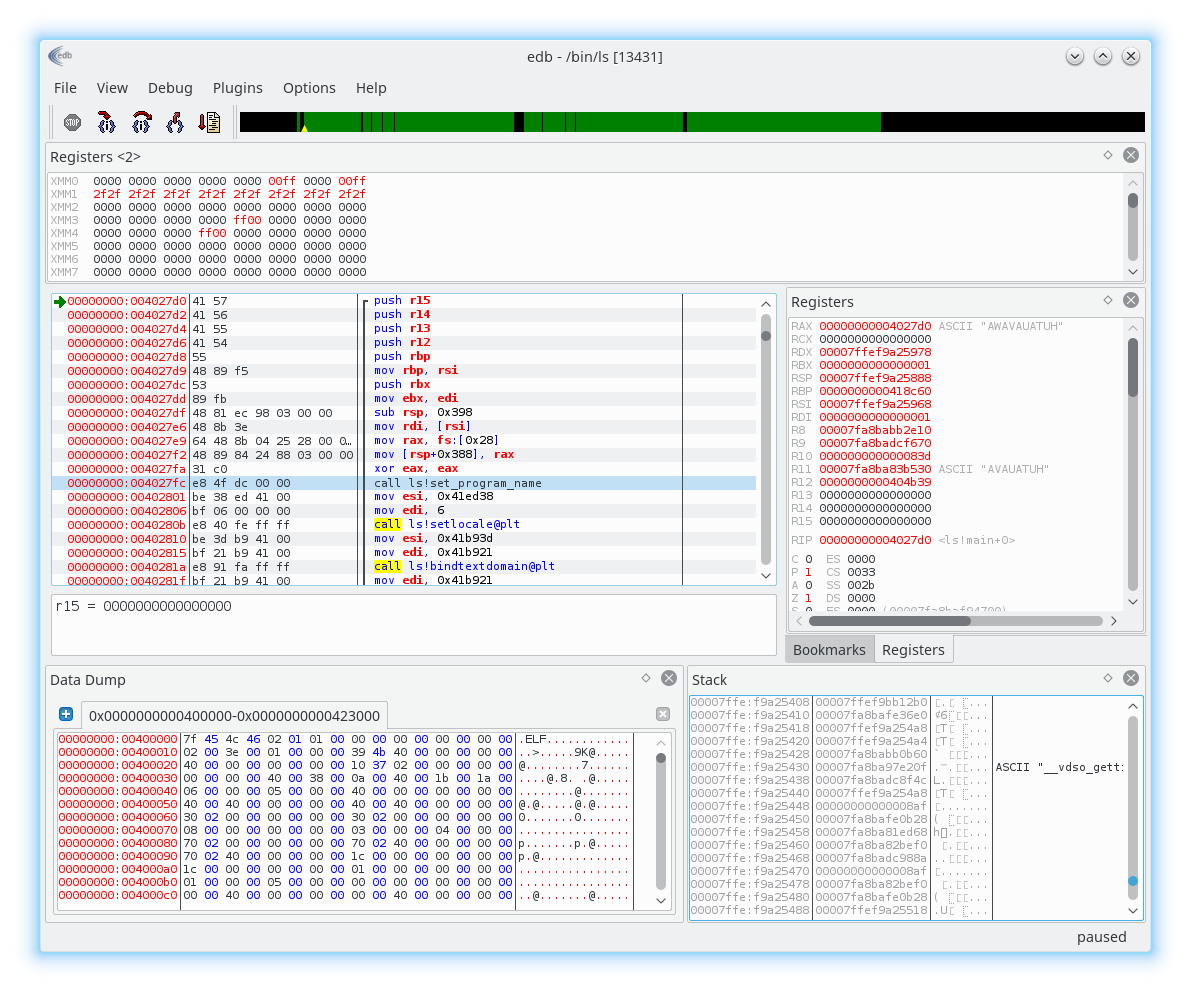
EDB
gdb GUI makes life so much easier for us! (sort of)
I love CLI, but here GUI is so much less struggle!
There are still quirks, but we get much more!
Lets look at an example!
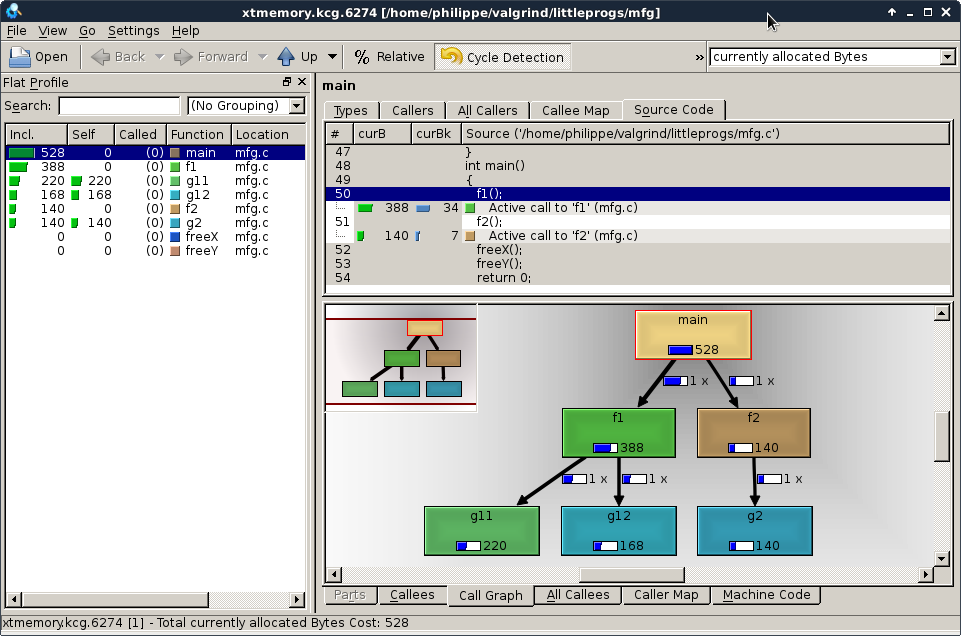
Valgrind
Dynamic analysis instrumentation framework (more on this later) for building dynamic tools.
You've likely used this for detected memory management bugs (Memcheck).
Interesting tools:
- Helgrind
- DRD
- DHAT
Packers
What is a packer?
Why might a program be packed?
What about this makes our job hard?
Packers change/hide the original binary code by compressing or operating on the bytes
Company trying to hide their product, Malware trying to stay undetected,
Trying to make Reverse engineers hate life
No static analysis, need to learn how the packer works/tools to unpack.
Detecting packers?
Can we detect these nasty things?
/usr/bin/yes
upx yes
Yes, we can run it and see that is unpacking, but that can take time!
Visual Binary Analysis makes all the difference!!
UPX
UPX - Ultimate Packer for Executables
What does this packer do?

Relocates sections!
Removes section table
Packs all sections with UCL
All imports become statically linked
Adds stub code

Lets Step through yesupx and see what this looks like!
What issues did we have with Static Analysis?
Function detection was not complete
Useless against packers and Obfuscators (next week :D )
Difficult to reason about everything at the same time
Stripped binaries are difficult to work with

Ltrace
Library Trace -
Allows us to see the libc calls in the order they are called, as well as arguments to each call
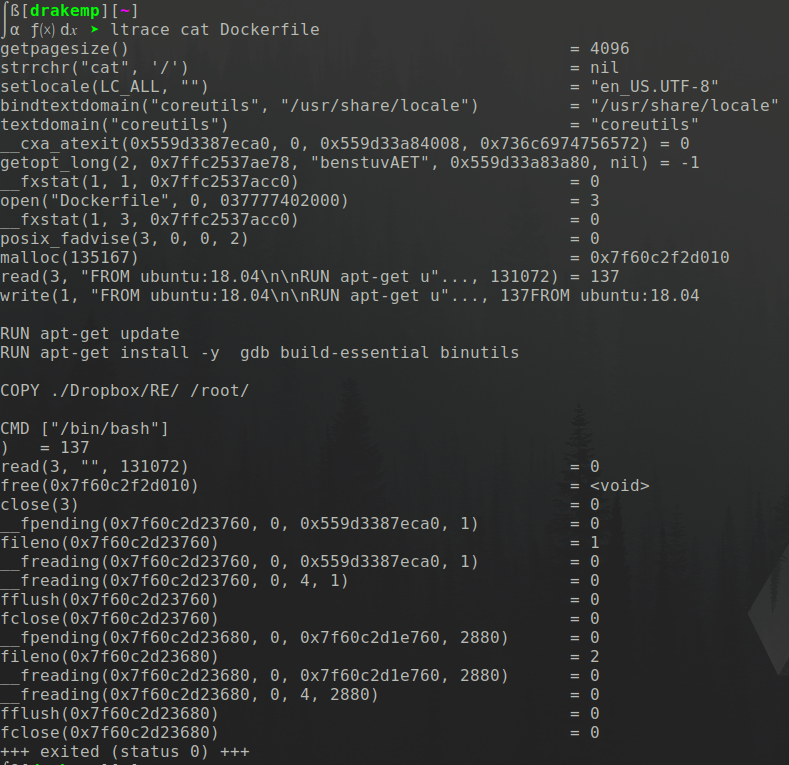

Opening
Malloc
Output
Return values
Strace
System trace -
Similar to ltrace, shows all system calls made by the process in the order they occur and arguments to them.
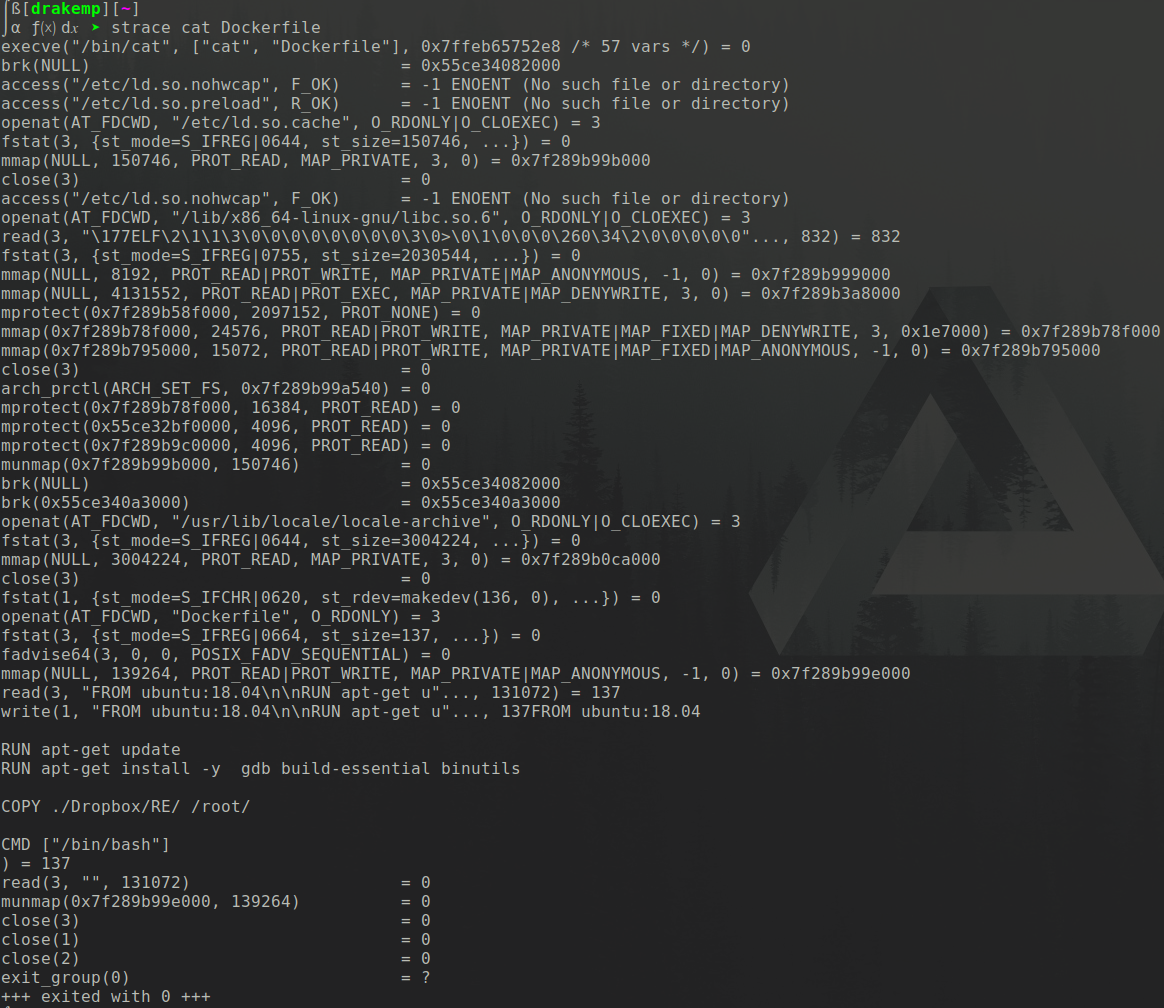

What is all of this?
What about these?
Syscalls that set up the running process
Syscalls from our process
Ptrace
How does strace and ltrace work?
What can ptrace do?
And a lot more!
$ man ptrace
Why Obfuscation?
- Hide intent
- Avoid detection
- Cause pain to Reverse Engineers
- Obfuscating is fun!

How can we obfuscate?
- Write compilers that do weird stuff
- Abuse Language Syntax
- Write VMs for esoteric languages (really fun actually)

Why Self-modification?
- Avoid detection
- Make static analysis much much harder

- Slower
- Hard to write
- Hard to read
- Better than Obfuscation when avoiding detection
Pros/Cons
What does a binary need to self modify?
- Write access to Executable segments/sections
- Stub code for modification

Types of Self modifications:
- Unpack-able - At some point in execution all of the code that is hidden is visible at the same time.
- Non-unpack-able - At no point in execution is all hidden code unpacked at the same time.
Dynamic Analysis
By Drake P
Dynamic Analysis
- 388



