Week 9
Agenda
- Malware
- Volatility
Malware
What is Malware?
"...any program or file that is harmful to a computer user. Malware includes computer viruses, worms, Trojan horses and spyware. These malicious programs can perform a variety of functions, including stealing, encrypting or deleting sensitive data, altering or hijacking core computing functions and monitoring users' computer activity without their permission."

Types of Malware
- Virus
- Worm
- Trojan
- Adware
- Ransomware
- Rootkit
- Spyware
- Greyware
- Botnet
Types of Behavior


- Virus
- Worm
- Trojan
- Adware
- Ransomware
- Rootkit
- Spyware
- Greyware
- Botnet
Combinations of Malware
There is no universally agreed way to classify malware beyond the types mentioned. This is because malware tends to be hybrids of the the above types.
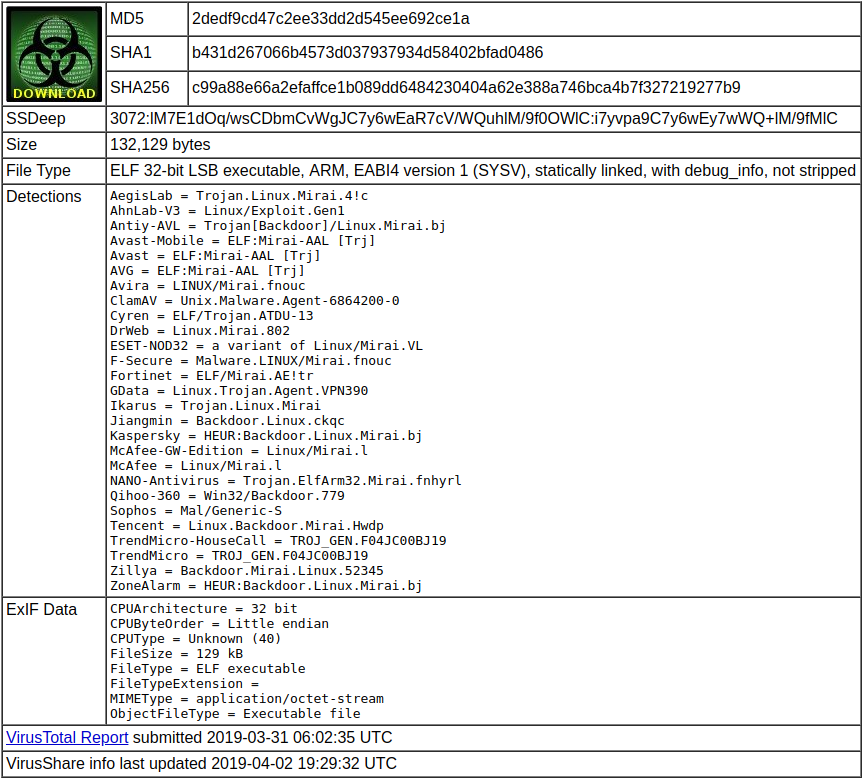
Hashes
File Type Info.
File Type Info.
Detections:
Anti-Virus tools that try to indicate features of the sample

Half of your HW
Research and describe some famous malware and classify them on how they work.
Volatility
What is Volatility?
Volatility is a Memory Forensics CLI tool. Volatility reconstructs the virtual memory from a memory sample (RAM dump) to allow a user to see the running processes, network connections, etc.
We could teach a class on this alone, but for now...

Getting a Memory Sample
There are many situations for making a sample from a computer
- Kernel module
- Firewire
- Crashdumps

Virtual machines are easiest, Snapshots contain memory dumps.
https://tunnelix.com/linux-memory-analysis-with-lime-and-volatility/
Acquiring the memory sample needs to be atomic, this is difficult over a wired connection.
Forensics
Volatility needs a profile for the operating system and architecture. There are many built-in profiles for Windows; other operating systems need profiles built when conducting memory forensics
Yes we are using Windows for this!
$ volatility -f wcry.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/drakemp/Dropbox/projects/vol/wcry.raw)
PAE type : No PAE
DTB : 0x39000L
KDBG : 0x8054cf60L
Number of Processors : 1
Image Type (Service Pack) : 3
KPCR for CPU 0 : 0xffdff000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2017-05-12 21:26:32 UTC+0000
Image local date and time : 2017-05-13 02:56:32 +0530
Now we can look for things!
$ volatility -f wcry.raw --profile=WinXPSP2x86 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0x823c8830 System 4 0 51 244 ------ 0
0x82169020 smss.exe 348 4 3 19 ------ 0 2017-05-12 21:21:55 UTC+0000
0x82161da0 csrss.exe 596 348 12 352 0 0 2017-05-12 21:22:00 UTC+0000
0x8216e020 winlogon.exe 620 348 23 536 0 0 2017-05-12 21:22:01 UTC+0000
0x821937f0 services.exe 664 620 15 265 0 0 2017-05-12 21:22:01 UTC+0000
0x82191658 lsass.exe 676 620 23 353 0 0 2017-05-12 21:22:01 UTC+0000
0x8221a2c0 svchost.exe 836 664 19 211 0 0 2017-05-12 21:22:02 UTC+0000
0x821b5230 svchost.exe 904 664 9 227 0 0 2017-05-12 21:22:03 UTC+0000
0x821af7e8 svchost.exe 1024 664 79 1366 0 0 2017-05-12 21:22:03 UTC+0000
0x8203b7a8 svchost.exe 1084 664 6 72 0 0 2017-05-12 21:22:03 UTC+0000
0x821bea78 svchost.exe 1152 664 10 173 0 0 2017-05-12 21:22:06 UTC+0000
0x821e2da0 spoolsv.exe 1484 664 14 124 0 0 2017-05-12 21:22:09 UTC+0000
0x821d9da0 explorer.exe 1636 1608 11 331 0 0 2017-05-12 21:22:10 UTC+0000
0x82218da0 tasksche.exe 1940 1636 7 51 0 0 2017-05-12 21:22:14 UTC+0000
0x82231da0 ctfmon.exe 1956 1636 1 86 0 0 2017-05-12 21:22:14 UTC+0000
0x81fb95d8 svchost.exe 260 664 5 105 0 0 2017-05-12 21:22:18 UTC+0000
0x81fde308 @WanaDecryptor@ 740 1940 2 70 0 0 2017-05-12 21:22:22 UTC+0000
0x81f747c0 wuauclt.exe 1768 1024 7 132 0 0 2017-05-12 21:22:52 UTC+0000
0x82010020 alg.exe 544 664 6 101 0 0 2017-05-12 21:22:55 UTC+0000
0x81fea8a0 wscntfy.exe 1168 1024 1 37 0 0 2017-05-12 21:22:56 UTC+0000 pslist - Process list
Demo
Sample can be downloaded from here!
https://mega.nz/#!Au5xlCAS!KX5ZJKYzQgDHSa72lPFwqKL6CsZS7oQGbyyQrMTH9XY
Week 9
By Drake P
Week 9
Malware, Volatility
- 380



